2022-10-26 23:32:16 Author: lab.wallarm.com(查看原文) 阅读量:34 收藏
The kind of API security scenarios we witnessed today were never like this from the beginning of time. It has gone to extra lengths to become responsive and productive as it’s now.
How was it in the beginning?
What changes has it faced?
What more can we expect in the future?
If this is what bothers you, let’s have a look at this post as it explains the evolution of API security through the years.
API Is Omnipresent
Before we delve deeper into API evolution, let’s understand how it’s prevailing. A recent report revealed that nearly 1.7 billion active APIs will be there by the end of 2030. Be it web or mobile, apps are going to be fully dependent on APIs.

See how APIs are distributed across the industry. Private and customized APIs have the largest market share as they lead to need-based development.
As APIs are everywhere, related risks are not less. With the rise of API, API threats and vulnerabilities also increased. This is what we meant.

API Security – What Rests In History
Let’s begin with understanding the beginning of API protection. The concern about improved API security was always there. But, it got accelerated when the official API vulnerability was announced. It all began in 1998 with the identification of CVE-1999-0270 vulnerability. It existed in the Performer API Search Tool and permitted attackers to gain access to random files.

It was the beginning and the world witnessed many more API threats including CVE-2022-29464, which is the latest addition to the list. A handful of WSO2 products permit unrestricted file upload that aids further in RCE.

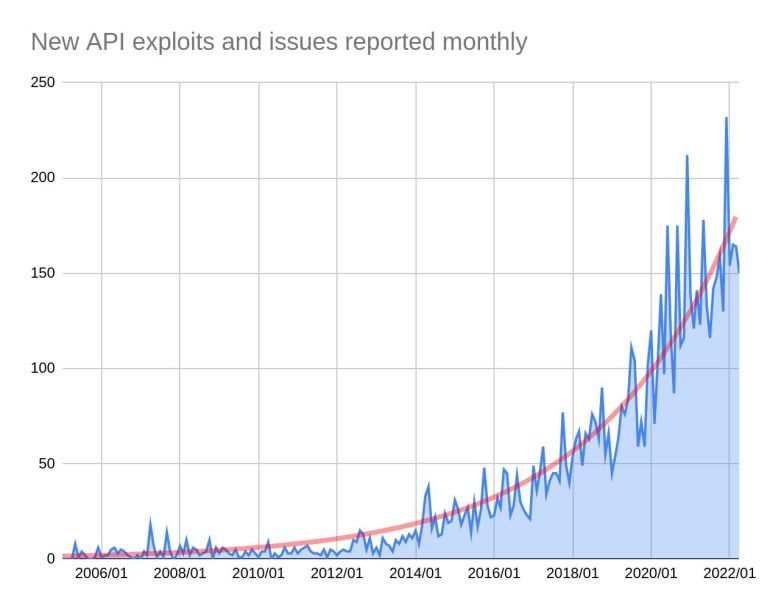
In an era driven by API, it’s not wise to let these loopholes create a rucksack. Presently, 5 novel exploits are coming into the picture every day.
What We Had Until Now
Presently, we have solutions like WAF, API gateway management, and API security to protect the APIs. Are they useful? Yes. Are they perfect? No. Let’s explain what made us say this.
API Gateway management is great as it provides rate limiting; we can’t expect much as there is no access control and threat discovery. API security sounds impressive on paper but lacks hugely when it comes to protecting APIs in real time.
What Is Wrong With Legacy WAF Solutions?
WAF came into being a viable solution to protect web apps and APIs and we must admit that it was doing a great job until today. With the evolution of API and its related threats, legacy WAFs are falling short with a huge margin and are not able to match the pace of your developer.
They lack API protocol support, real-time API threat detection, keep API endpoints unprotected, and lack PII discovery abilities. Let’s understand it in a better way. Also, don’t forget to check out how cutting-edge Wallarm WAF is filling its caveats.
First, we need to mention that its usage is too labor extensive as it demands constant configuration and will require API specs upload for protection. On the contrary to this, modern Wallarm has everything that requires API protection. While legacy WAF fails to process API calls, Wallarm WAF can process any kind of API. REST or SOAP, GraphQL, or gRPC, you name it and Wallarm WAF will be able to handle it.
The cherry on the cake is that it won’t bog you down with specs and configurations. It demands almost zero API specs.
Present-day API handling scenario demands a wide range of protocols. Sadly, there is hardly anything impressive offered with legacy WAF. This keeps your API development sluggish. Wallarm WAF does a great job on this front. For over 5 years, this WAF is receiving the best API protocols support and updates.
Recently, it supports Websockets, gRPC, and GraphQL API protocols and support for other API protocols is possible in near future. With this option, you enjoy the soundest protection against recent threats.
Have we discussed how poor auto-scaling is with legacy WAF? Yes, auto-scaling is at its worst with this option. The lack of proper threat detection techniques also caused high false positives.
These troubles are easily fixed with Wallarm WAF which scales up and down in a blink of an eye. As it comes with native Kubernetes support scaling is possible in K8 services and ecosystem.
To deal with the false positives issue, Wallarm has used the RegExp-free attack detection technique, which is known for the least possible false positive incidences.
Try installing a classic WAF as an inline solution and it’ll start working as a reverse proxy. Wallarm WAF is not like this. It comes with native inline support and is easy to be installed as an out-of-the box deployment.
This is just the tip of the iceberg. The more you know a legacy WAF, the more issues will come to the surface. In short, the traditional WAFs are not capable to handle what modern-era API security demands.
Thankfully, Wallarm WAF is there that seamlessly fixes all these loopholes of legacy WAF and shows up as a viable and workable WAF tool that modern-day API users can adopt.

Set Your Eyes On These For Future API Security
What we have today is already a bit flawed and will fail to address future API concerns. Be ready for the future by adopting these practices.
- Do extensive API discovery
Make sure you know what APIs you have and need protection. Zombie API, Shadow API, Rogue API, or any other API should be in your knowledge. If you are aware of every single API then only can protect it.
- Classify data and do constant risk assessment
Discovery every single sensitive data and tag them. Use a tool like Wallarm to spot the risks such data have. Assess without fail. The early detection, the better the protection.
- Have full security control
Make sure you know your API portfolio, can easily detect common threats, mitigate threats early, and provide the best protection.
The future is going to be API-driven.
You can’t remain functional with old-school API security practices. Become proactive and have the aid of a futuristic API security tool like Wallarm. As an ideal replacement for legacy WAF, Wallarm is laced with every cutting edge feature like:
- Easy tuning
- RegExp-free attack detection
- Support for in-line deployment
- Perfect integration with AWS/GCP/Azure
- Kubernetes native support
- Support for best protocols like Websockets, gRPC, and GraphQL.
By all means possible, it’s easy for the future and is here to empower the current API security strategy of all sorts of organizations.
Many Are Enjoying Leveraged API Security. What Are You Waiting For?
Wallarm, because of its inventive features, grabbed the attention of many. Already many Fortune 500 companies have replaced their outdated WAFs with Wallarm.
For Fintech businesses, this modern WAF tool has become imperative as this industry is at the eye of an API vulnerability storm. As per the FinCEN report, this industry lost nearly $416 million due to cyberattacks. With time, this number has only increased.
Tipalti and Rappi, two future unicorns of this industry, have adopted Wallarm and managed to shrink the attack surface. The tool is protecting nearly 180 billion API requests daily and helping these two and many other businesses to sigh in relief as mission-critical APIs are now protected and ready to deal with unforeseen threats.
Learn more about API Security through this video.
如有侵权请联系:admin#unsafe.sh