From big companies to individuals, phishing affects everyone in today's digital world.
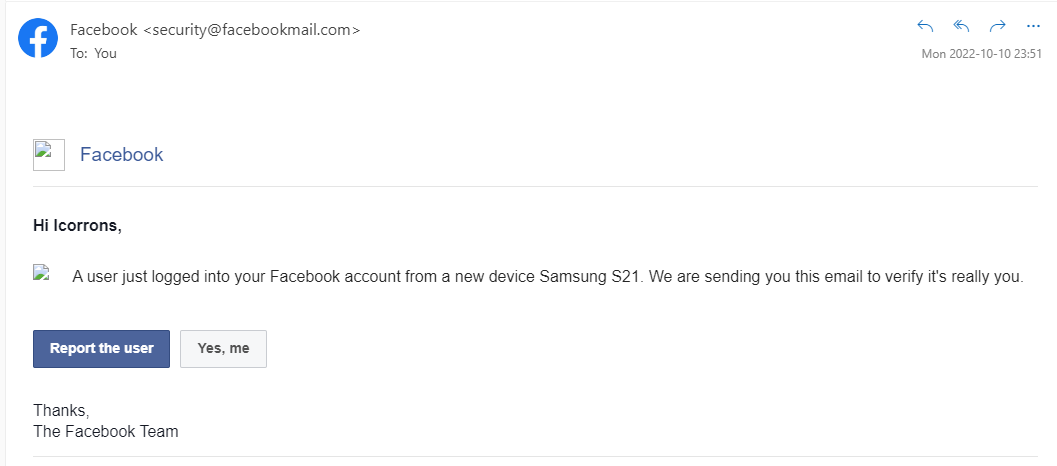
Day after day, we see news about new cyberattacks: Data breaches, yet another ransomware attack, and so on. From big companies to individuals, all of us are affected by these threats. A fact that isn’t that well known is that the first vector of a majority of these attacks takes the form of a simple phishing message. Phishing is one of the most popular attack vectors, and its use has only increased over time. According to a recent report published by the Anti-Phishing Working Group, which Avast is a sponsor of, Q2 2022 was the worst quarter for phishing ever observed. Essentially, phishing is when someone sends you a link or an email that looks like it comes from a legitimate source but actually leads to a fake website. Phishing sites look very convincing and are designed to trick people. They can be hosted on a real website and even look like an official message from a bank, social network, or other organization. The person who sends you the phishing link or email wants you to trust them and enter your personal information. This information is then used by the person sending the phishy message to commit identity theft. Once attackers have obtained the victim’s identity, they have an open field of abuse: They can lock you out of your online accounts, target your contacts, or pretend to be you to commit further crimes. As seen in the image above, cybercriminals use fear and urgency to force users to make rash decisions, that’s why many phishing emails usually refer to some threat – a claim that your account will be blocked or deleted or an unauthorized access has been detected. Attackers are getting more sophisticated, with different players specialized in different tasks, from stealing credentials to laundering money. Having phishing kits for sale has become a reality, and this trend is similar to what we’ve seen in other areas such as ransomware, where there are groups that create a platform in exchange for a percentage of the ransoms obtained. Recently, our team has been studying EvilProxy, a phishing service that allows untrained cybercriminals to run phishing campaigns capable of bypassing two-factor authentication. From the social engineering perspective, the improvements are also evident. Even for a trained eye, it’s sometimes truly difficult to distinguish a phishing message from a real one. On top of that, these attacks target the victim, using his native language on various platforms. For instance, phishing by SMS (also known as smishing) has become quite popular and works in the same way. Below, we can see a fraudulent SMS targeting customers of Spanish bank Banco Santander: Fortunately, protection against phishing attempts have increased due to increased awareness of these scams. However, not all users are aware of how to spot phishing sites and thus aren’t equipped to avoid giving away sensitive information. While browsers and security solutions include phishing protection, their effectiveness may vary and there are not many independent testing labs running phishing tests, being AV-Comparatives one of the few running comprehensive Anti-Phishing Certification Tests. Here are a few key tips to keep in mind:Cybercrime has become a mature industry
Phishing affects everyone in today's digital world
Tips for protecting yourself against phishing scams
如有侵权请联系:admin#unsafe.sh