2022-11-16 08:0:0 Author: www.trustwave.com(查看原文) 阅读量:15 收藏
The National Institute of Standards and Technology’s (NIST) Cybersecurity Framework (CSF) is one of several “gold level” standards used by public and private organizations as the basis for their cybersecurity protocols. It is also the benchmark utilized by Trustwave to protect our clients.
NIST rolled out the CSF in 2014 as a set of guidelines for mitigating organizational cybersecurity risks. NIST designed the Framework to be continuously updated to keep pace with technology, threat trends, and to integrate lessons learned.
Trustwave is a firm believer in the NIST CSF. All of Trustwave’s products and services overlap with at least one of the NIST CSF functionalities that the government agency has stated are core to any proper cybersecurity program. In addition, Trustwave believes the five NIST CSR functions are of significant value to organizations that are relatively immature or new to cybersecurity as it provides a simple lens through which to understand the field and the areas in which the organization is likely to require investment.
The five NIST functions are:
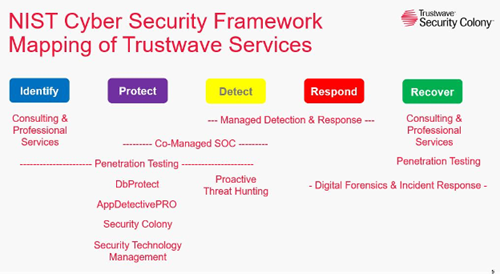
- Identify - Develop a strong understanding of your key systems and information assets.
- Protect - Develop and implement appropriate safeguards to prevent or at least contain the impact of a potential cyber security event.
- Detect - Develop and implement technology and processes for detecting cyber security incidents.
- Respond - Develop and implement processes for responding to a cyber security incident that occurs.
- Recover - Develop and implement processes for recovering from a cyber security incident that occurs.
How Trustwave Works Within the NIST Framework
There are two ways to better understand how Trustwave intersects with the NIST CSF priorities. First, by mapping it against Trustwave’s services, which can be visualized below:
Secondly, by comparing it to Trustwave’s product portfolio.
As can be seen, Trustwave has all aspects of the NIST CSF covered.
This is no accident. Trustwave has been deeply involved with NIST in the continuous development of the Framework, and as part of this cooperation, earlier this year, Trustwave submitted its thoughts on how it can be updated and improved.
The new version, dubbed CSF 2.0, follows the initial version adopted in 2014, and then updated in April 2018 when NIST issued CSF 1.1.
NIST began pulling together what would become CSF 2.0 in February 2022 when it put out a request for information (RFI) to obtain public input on how to improve the Framework, which is formally known as the Framework for Improving Critical Infrastructure Cybersecurity. The RFI contained six areas to explore, along with asking for information on cybersecurity supply chain risk management
The latest NIST update is not driven by any specific cybersecurity issue, the agency said, but is part of the agency’s planned update to keep the CSF current and ensure that it is aligned with other tools that are commonly used. In addition, the CSF is intended to be a living document that can be refined, improved, and evolve over time. These updates help the Framework keep pace with technology and threat trends, integrate lessons learned, and move best practices to common practice.
Trustwave and NIST
In response to the RFI, Trustwave, through Trustwave Government Services, forwarded a list of recommendations to help improve the Framework.
These included:
- The five functions do not clearly correspond to groups of risk, and a clearer connection between the ISO27001 risk-based approach would be valuable for organizations seeking to use both frameworks (and/or indeed, that are effectively mandated to use both frameworks by different groups of stakeholders).
- We believe the Framework should add a clear and comprehensive database security program with proactive database security measures that include continuous vulnerability assessment and remediation, database privileged access visibility and control, and continuous database activity monitoring to alert and respond to anomalous database activity.
- The main challenge organizations currently face from using NIST CSF is the typical marketplace challenge of needing the demand-side and supply-side to agree on an approach. Currently, there are a myriad of certifications and reports requested, such as ISO27001, SOC2, etc. Many organizations are using whatever security framework they see the best commercial returns on, and until greater consistency exists in the market, it will be hard for a single framework to get overall traction.
- Strengthen vulnerability management posture. Vulnerability management is considered a fundamental security operational process recommended by standards like the NIST and is performed by nearly every industry. There are, however, important differences in the toolsets and what they are designed to do.
如有侵权请联系:admin#unsafe.sh





