2022-1-31 22:58:59 Author: sandflysecurity.com(查看原文) 阅读量:22 收藏
Sandfly 3.2 features new threat detection modules for suspicious base64 payloads, suspicious processes and suspicious systemd behaviors. Plus, version 3.2 has new host and alert views along with rapid view of key Linux forensic data details.
New Checks for Base64 Payload, Process and Systemd Attacks
This latest release adds new sandfly checks for:
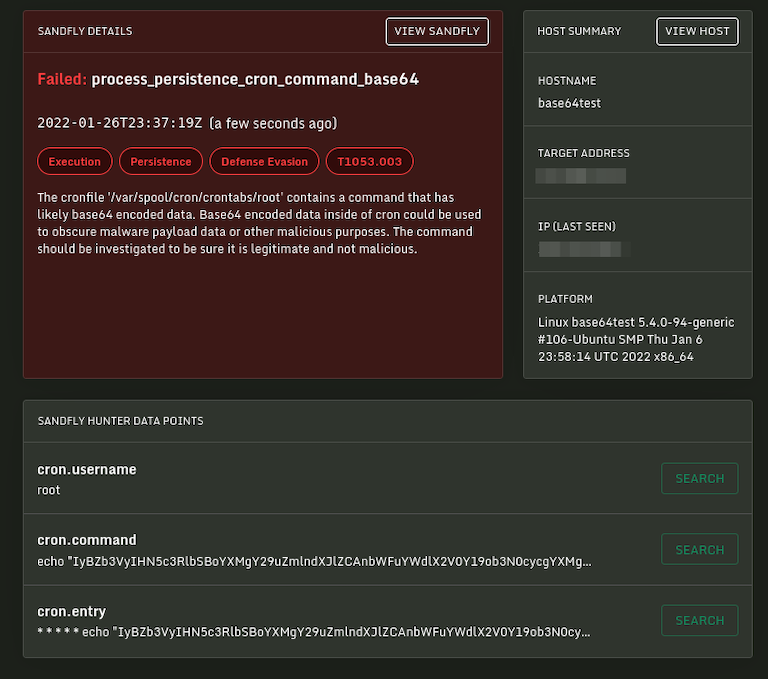
Base64 encoded Linux malware payload data inside critical system areas such as cron, system init scripts, login/logout scripts and more. These checks find payload data often hidden as base64 obfuscation for malware persistence.
Detection of empty command sequences to find masquerading process names and process names trying to masquerade as a PID value.
More systemd attack detection around suspicious timers and events.
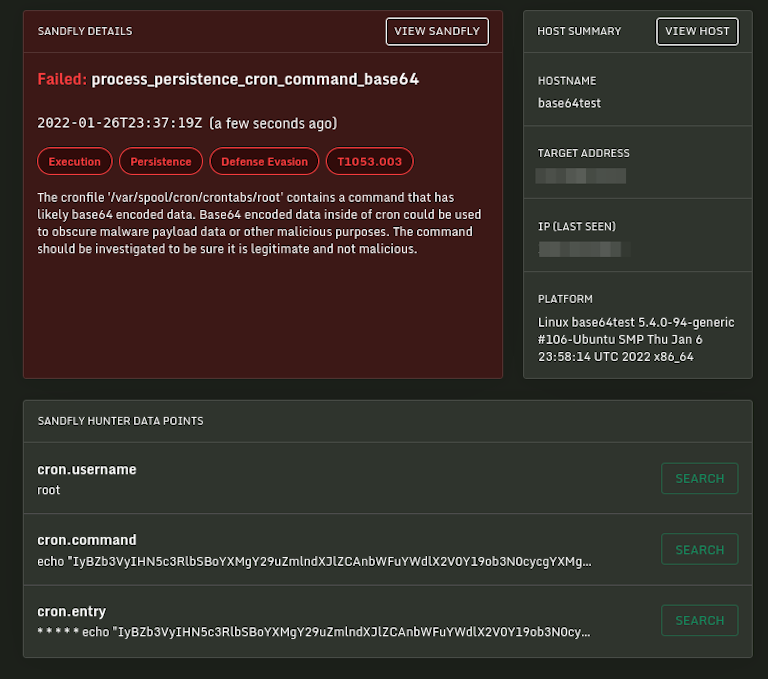
New Host Views
We’ve improved several elements to increase your insight into your hosts, including: More information on core operating system data such as kernel versions, CPU type and architecture in the host status view (Detailed operating system information is still available under the raw host data tab).
Quick access buttons to results available directly from the host screen.
Status icons that show the current state of the host such as Passing, Alerts, Errors or Offline.
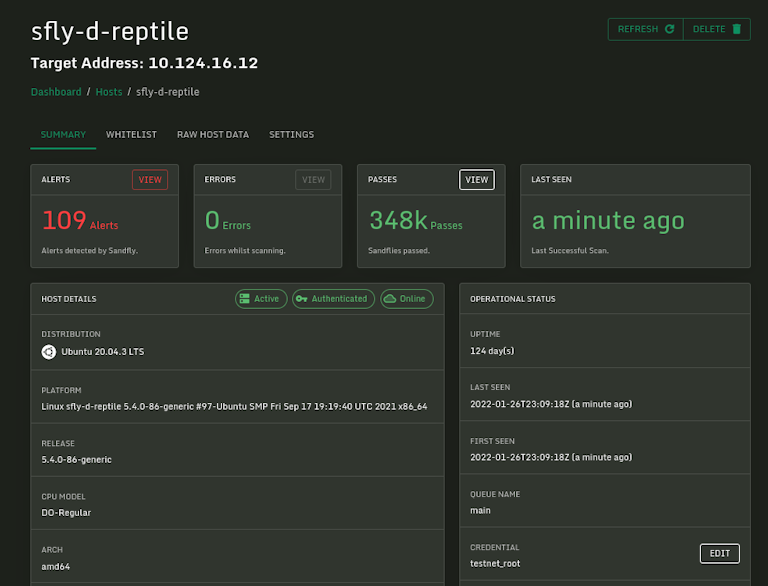
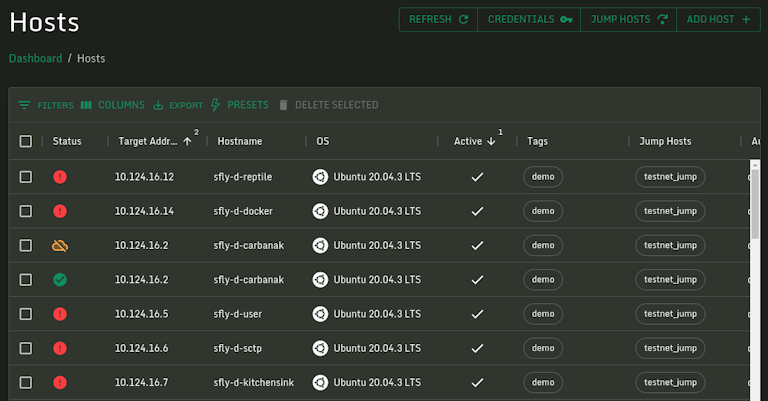
Offline Detection
Our new offline detection feature lets you know when we haven't seen a host within 24 hours so you know it is no longer being monitored. The top bar under the host status shows time elapsed since the host was last seen with quick access to any alerts if present.
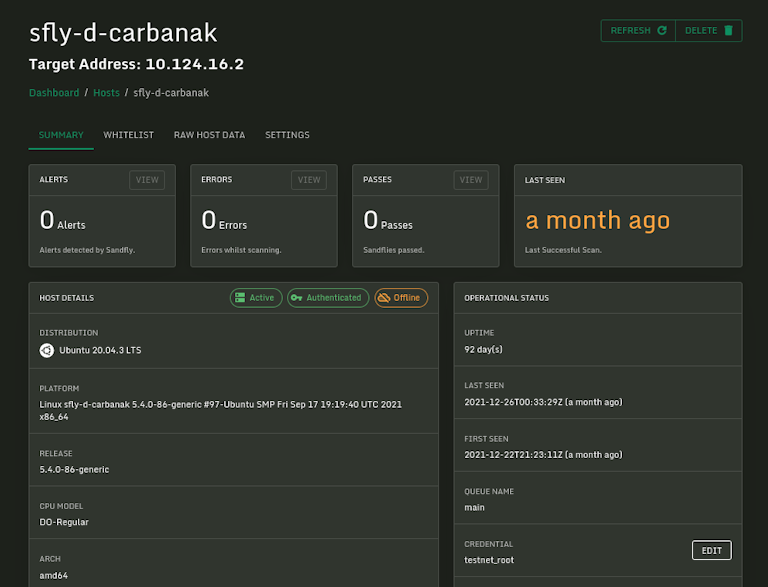
Results Grouped by Hosts
The new host alert view gives you a total alert count for all hosts and allows you to quickly explore alerts just for the affected system by a simple click.
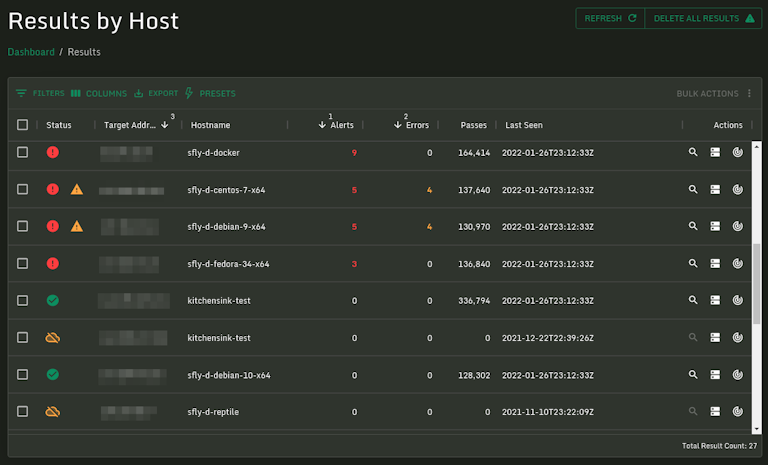
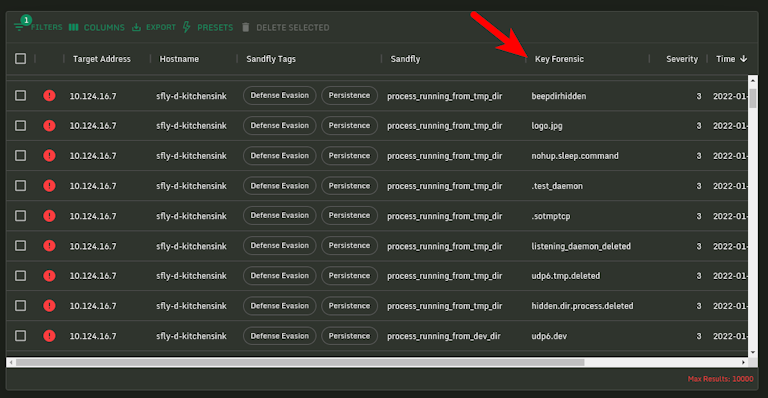
Key Forensic in Results
The master results list has a new column called "Key Forensic." This column shows you the primary element of the alert to help you quickly see critical forensic data. For instance, a process alert will show you the process name flagged and suspicious users will have the username shown. This allows analysts to browse their alerts and prioritize what is most important with a quick glance.
Seamless, Free Upgrade to 3.2
All free and paid customers can upgrade today. Please see the upgrade documentation for instructions on how to quickly and easily upgrade.
Protect 500 Linux Systems Now for Free
Sandfly v3.2 is still offered for free to help you immediately start monitoring and protecting your Linux fleet. Get it online now with an instant no-obligation license.
如有侵权请联系:admin#unsafe.sh