
Hello World! You can jump start your 802.11 journey in cyber security with your existing knowledge of the Ethernet standard. However, there are some situations in which you will require more in-depth knowledge. For example, despite being unbounded in its surroundings, providing security to prevent known network attacks.
The more you understand about how wireless networking actually functions, the easier it will be for you to grasp changes made to the technology. The MAC frame is crucial to the 802.11 specification. It travels across all physical layers and regulates the airborne transmission of user data. Due to the different physical layer mediums used by Ethernet and WiFi, their MAC frame structures are essentially identical with some differences.
The MAC was forced to adopt several unique features in order to meet the challenges posed by a wireless data link. Some classic Ethernet frame features, most notably the type/length field and the preamble, are absent from 802.11 MAC frames.
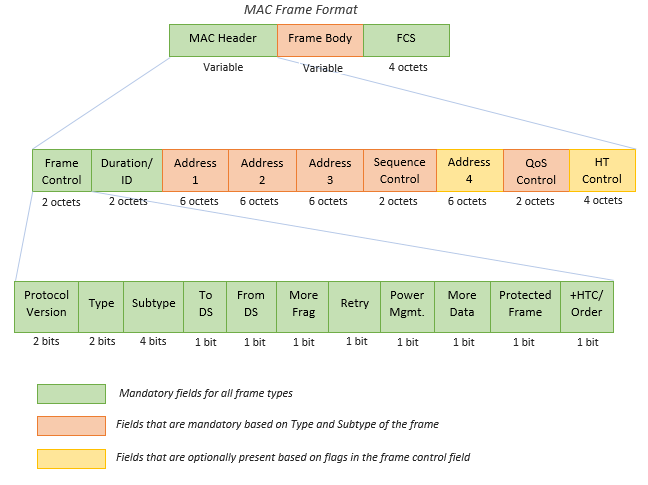
Note: Octect also means 8 bits, aka byte.
Each frame begins with two bytes of meta information, which is then subdivided into eleven parts. Let's go over each subpart individually to learn more about it.
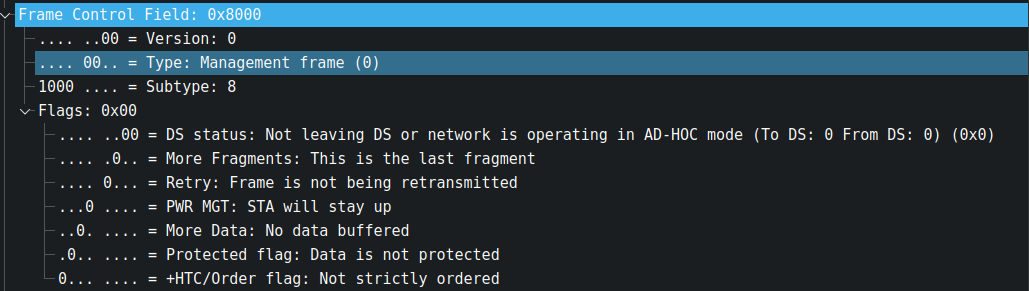
Protocol Version
The protocol version is assigned the first two bits. At the moment, only one version has been developed, with protocol number 0. Other values will be added as the IEEE standardises changes to the MAC that make it incompatible with the original specification. This value is associated with the wlan.fc.version field in the IEEE 802.11 protocol capture in wireshark.
Type and Subtype
This is used to categorize the frame into Management, Control or Data types of the frame. Based on the certain values defined in the specificiation the WiFi device behaves differently.
Do you ever wonder how your phone learns about a new WiFi access point nearby? It's thanks to Beacon frames, which are broadcasted on a regular basis by the access point. This frame's type and subtype will be 0x00 and 0x08, respectively.
There is a Wikipedia article that lists all of the available frame types as well as their names.
802.11 Frame Types - Wikipedia
 Wikimedia Foundation, Inc.Contributors to Wikimedia projects
Wikimedia Foundation, Inc.Contributors to Wikimedia projects

In the wireshark, you have 3 different fields for querying
wlan.fc.typewill only be used to query the frame's type.wlan.fc.subtypewill only be used to query the frame's subtype.wlan.fc.type_subtypewill be used to query the frame's type and subtype. For example, this value would be 0x0008 for all beacon frames.
Other Details
In the wireshark, these details are grouped under Flags section. They are used to provide additional information about the frame.
ToDS and FromDS
The first two bits are used for ToDS and FromDS flags, which indicate whether the frame is directed to or coming from a distribution system.
If both of these values are set to zero, it indicates that the frames are not directed to or coming from any distribution centre in relation to the station. If the receiver address matches the bssid address, it is routed to the access point; otherwise, some station-to-station communication occurs. If both of these values are set to 1, all four addresses in the frame will be used.
Retry Bit
Because of the very flexible boundary, there is a possibility that the transmitting device does not receive acknowledgement whether the frame is delivered or not. As a result, frames may be retransmitted from time to time. To avoid duplicate frames at the receiver end, any retransmitted frames will have the retry bit set to 1.
Power Management
Because the station's devices are powered by batteries to provide mobility, there is a chance that in order to save power, some of the transmitters will be disabled. To notify other devices of this information, the power management flag will be set to 1. If this is 0, the power save is disabled; otherwise, it is enabled.
Because access points perform a variety of critical management functions and are not permitted to save power, this bit is always set to 0 in frames transmitted by
More Data
When the client is associated with the access point's network, you will find the association id in the Association Response frame ( wlan.fc.type_subtype == 0x1 ) in the fixed parameter section.
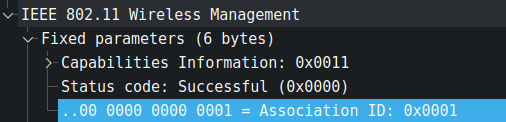
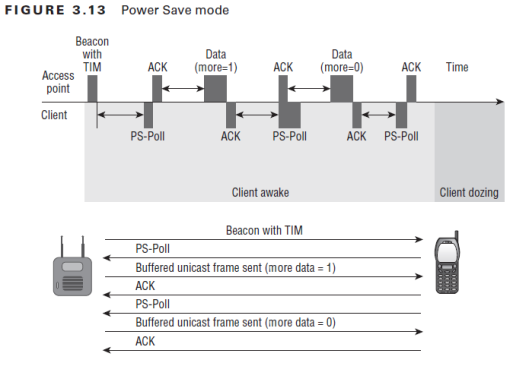
When the station is in power-saving mode, the access point frequently transmits unicast data in chunks (buffers) that are associated with this association id (to keep track of data sent). To indicate that there are more frames, the AP will set the "More Data" field to 1, allowing the station to wake up and receive all of those frames.
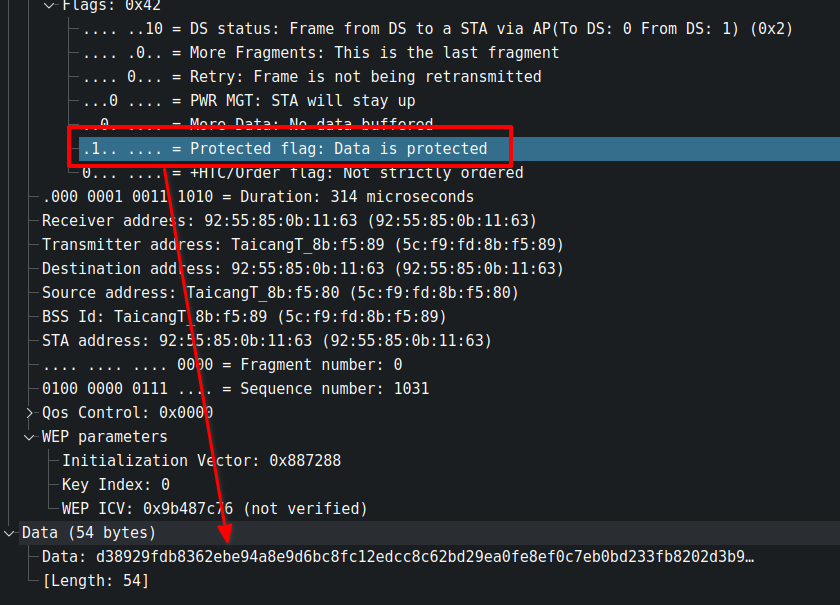
Protected
If frames are transmitted in encrypted form, this flag is set, indicating that the receiver device must first decrypt based on the encryption algorithm provided in the packet before processing the data. This will always be set to 0 in an open WiFi network.
These fields in the frame header are frequently used to direct frames to a specific station or access point. Because I have worked in an environment with direct communication between stations and access points rather than through distribution systems, these fields will be explained solely on that basis.
The first address field is reserved for the destination address, which is followed by the source address and finally the bssid. If the BSSID address and the source address are the same, and the destination address is FF:FF:FF:FF:FF:FF, it means that access point is broadcasting the packets: This is a common occurrence in beacon frames.
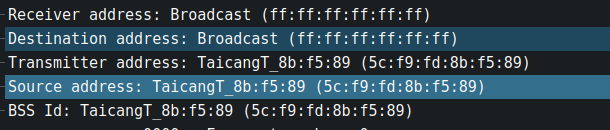
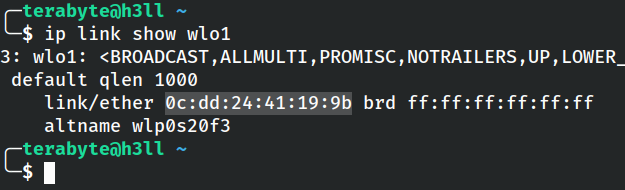
These addresses, like Ethernet addresses, are 48-bit IEEE MAC identifier that are associated with the device. The ip link command can be used to obtain the mac address of your WiFi card.
💡
These values should not be regarded as constants for your device. This is easily changed using the macchanger tool. I've written a blog post about it – Bypass MAC Filtering using MAC-Changer
- https://www.tutorialspoint.com/the-802-11-frame-structure
- https://en.wikipedia.org/wiki/802.11_Frame_Types
- https://www.wifi-professionals.com/2019/03/wireshark-display-filters
- https://mrncciew.com/2014/09/27/cwap-mac-header-frame-control/
- https://mrncciew.com/2014/09/29/cwap-802-11-mgmt-frame-types/
- https://en.wikipedia.org/wiki/Wireless_distribution_system
- https://dalewifisec.wordpress.com/2014/05/17/the-to-ds-and-from-ds-fields/
- https://mrncciew.com/2014/11/01/cwap-mac-header-sequence-control/
- https://mrncciew.com/2014/11/01/cwap-mac-header-sequence-control/
- https://mrncciew.com/2014/10/03/cwap-mac-header-qos-control/
如有侵权请联系:admin#unsafe.sh