
2022-12-6 19:0:2 Author: unit42.paloaltonetworks.com(查看原文) 阅读量:24 收藏
By
Category: Ransomware
Tags: Cortex, Cortex XDR, CVE-2021-1675, CVE-2021-34527, HelloKitty, incident response, NGFW, PrintNightmare, Vice Society, WildFire

Executive Summary
Vice Society is a ransomware gang that has been involved in high-profile activity against schools this year. Unlike many other ransomware groups such as LockBit that follow a typical ransomware-as-a-service (RaaS) model, Vice Society’s operations are different in that they’ve been known for using forks of pre-existing ransomware families in their attack chain that are sold on DarkWeb marketplaces. These include the HelloKitty (aka FiveHands) and Zeppelin strains of ransomware as opposed to Vice Society developing their own custom payload.
In September 2022, a joint Cybersecurity Advisory (CSA) from the FBI, CISA and the MS-ISAC declared they had recently observed Vice Society actors disproportionately targeting the education sector with ransomware attacks. The CSA continued that attacks could increase as the 2022-23 school year begins and criminal ransomware groups perceive opportunities for successful attacks.
Vice Society first surfaced in the summer of 2021, and in that time frame it was seen exploiting the CVE-2021-34527 (aka PrintNightmare) vulnerability as part of their attack chain. The gang is also known to target backups and exfiltrate data from compromised systems to be leveraged for the purpose of double extortion, a common ransomware operation tactic where victims are pressured to pay a specified ransom amount in exchange for decryption and to avoid having sensitive data published on the attacker’s dedicated leak site.
Palo Alto Networks customers receive protections against ransomware used by Vice Society from Cortex XDR, as well as from the WildFire cloud-delivered security service for the Next-Generation Firewall. The Unit 42 Incident Response team can also be engaged to help with a compromise or to provide a proactive assessment to lower your risk.
Table of Contents
Vice Society Activity Timeline
Study of Vice Society’s Victims
Geographical Impact
Impacted Industry Verticals
Leak Site Metric Comparisons
Unit 42 Incident Response Data on Vice Society
Vice Society Technical Details
Leak Site Synopsis
HelloKitty Usage
Zeppelin Usage
Conclusion
Tactics, Techniques and Procedures (TTPs)
Indicators of Compromise (IoCs)
Additional Resources
Vice Society Activity Timeline
Early reports of the extortion group Vice Society were shared on Twitter by malware researchers such as Michael Gillespie. These tweets depicted HelloKitty ransomware payloads appending a .v-society extension to encrypted files on June 10, 2021.
Since then, Vice Society has used a variety of different ransomware strains including the following notable examples:
- In June 2021, Vice Society infected victims with HelloKitty.
- In 2021 and 2022, Vice Society used Zeppelin to target Windows hosts.
- During their 2021 infections, these attackers also exploited vulnerabilities such as PrintNightmare to escalate privileges and spread laterally across targeted networks.
Based on leak site activity we’ve observed in recent months, as shown in Figure 1, we saw a subtle spike at the turning point from 2021 to 2022. This was followed by one large spike of activity at the end of spring 2022.
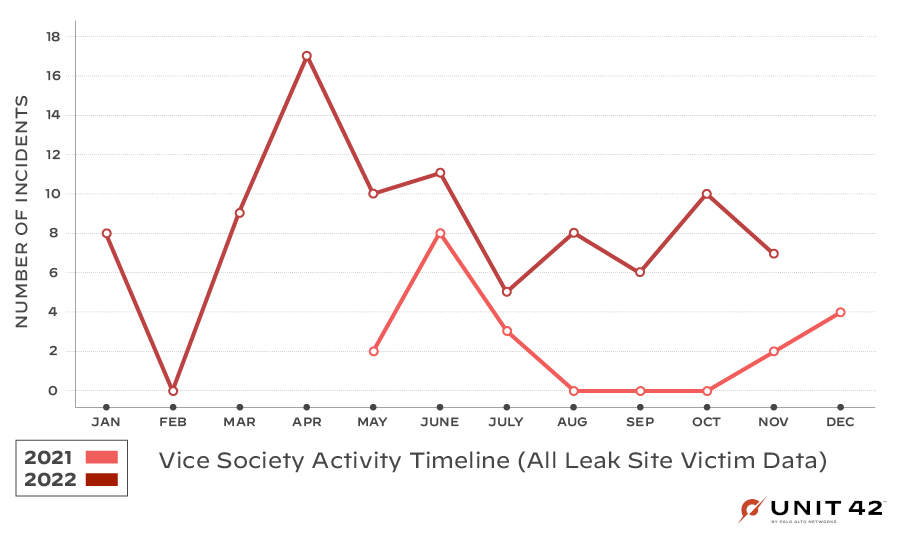
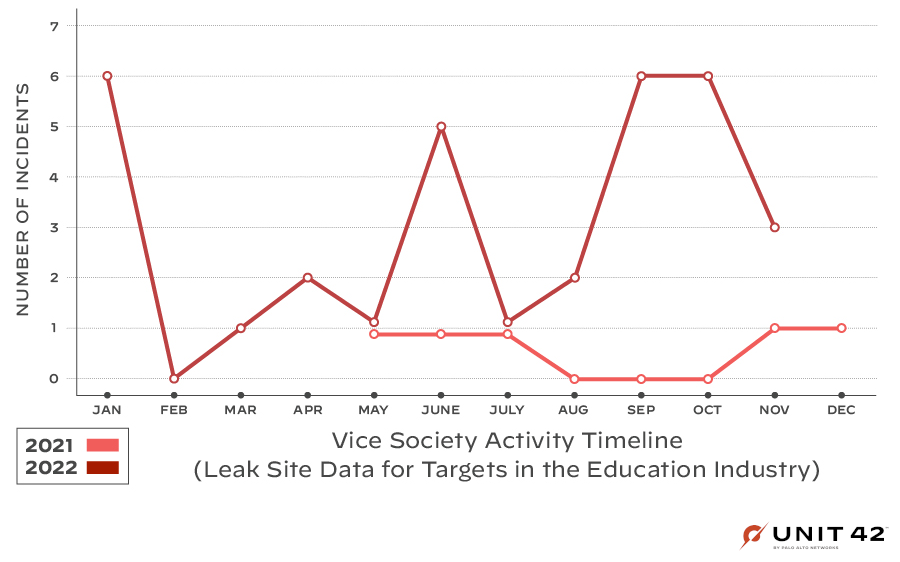
Fast forward to fall 2022, when we saw another wave of Vice Society activity across the education sector, as shown in Figure 2, which prompted a flood of advisories and reports about the group.
The noticeable spikes in spring and fall give us a hint at some of their motivations. As education organizations are the group’s prime target, this could be an indication that they’re timing campaigns to coincide with this sector’s unique calendar year. The school year for most educational institutions in the U.S. typically starts in late August-September and ends in June. They might have been trying to time their attacks in 2022 with the transitions of the beginning and end of the school year.
Study of Vice Society’s Victims
Vice Society is notorious for targeting the education sector – K-12 and higher education institutions in particular (as referenced in the recent CISA Advisory). Other targeted sectors include healthcare and nongovernmental organizations (NGOs).
Common targets are small- to medium-size businesses, with no geographical focus apparent at this time. Rather, as noted in a report by SOCRadar, Vice Society focuses on targets of opportunity.
For years, sectors such as education and healthcare have suffered from many challenges in combating ransomware that have made them particularly attractive targets. A lack of budgeting for systems and security solutions has led many organizations to run legacy hardware that isn’t patched against the latest vulnerabilities.
Other challenges that could increase the overall attack surface of these organizations include difficulties in controlling and managing a large number of personal devices brought in by students and staff members. These personal devices introduce inherent risk because they may interact with personal files via cloud services.
Although these sectors might have dedicated IT or security teams that run traditional security solutions such as an intrusion detection system (IDS) or intrusion prevention system (IPS), ransomware threat actors are leveraging living off the land techniques that can effectively circumvent traditional signature-based detection mechanisms. These tactics require an extended detection and response (XDR) platform for more robust behavioral monitoring within a network.
The education and healthcare sectors also experience the common challenge of finding staff who are adequately trained to handle the ongoing threat of ransomware. And lastly, many of these organizations are charged with protecting some of the most sensitive and valuable personally identifiable information (PII) of any business sector.
Geographical Impact
Vice Society is primarily opportunistic, and its targets have included organizations across the globe. The group has infected organizations based in all regions, as shown in Figures 3 and 4, with the largest numbers in the U.S., followed by the U.K., Spain, France, Brazil, Germany and Italy.
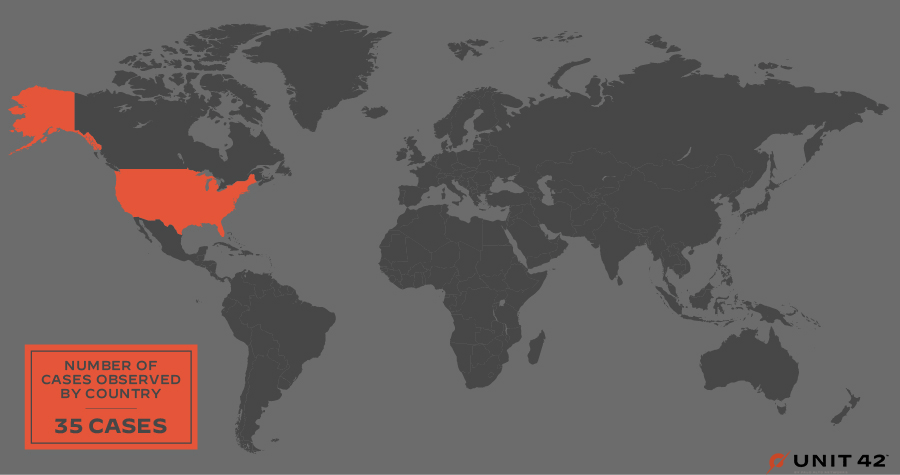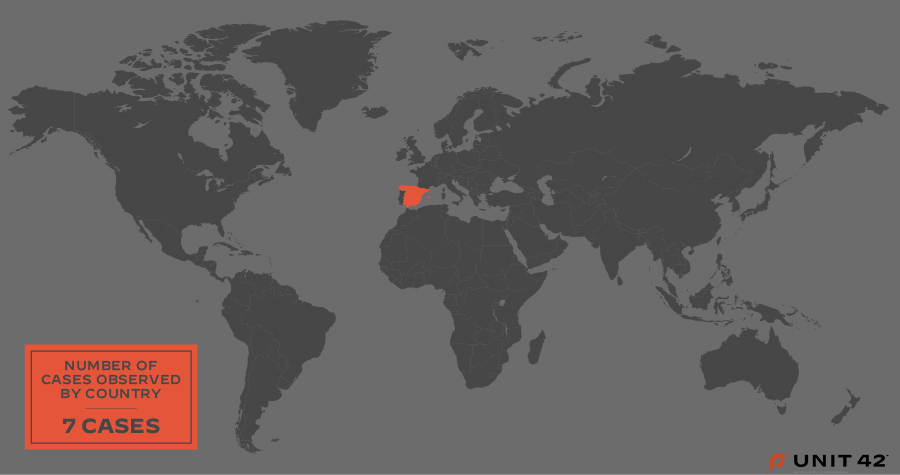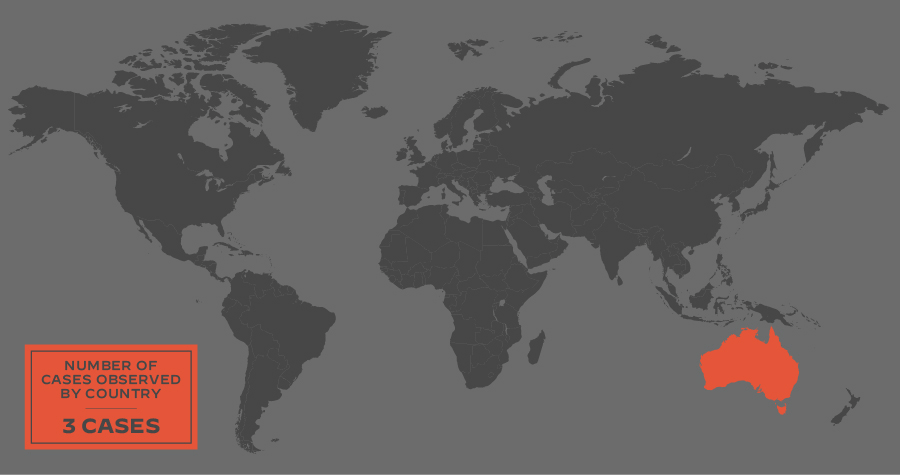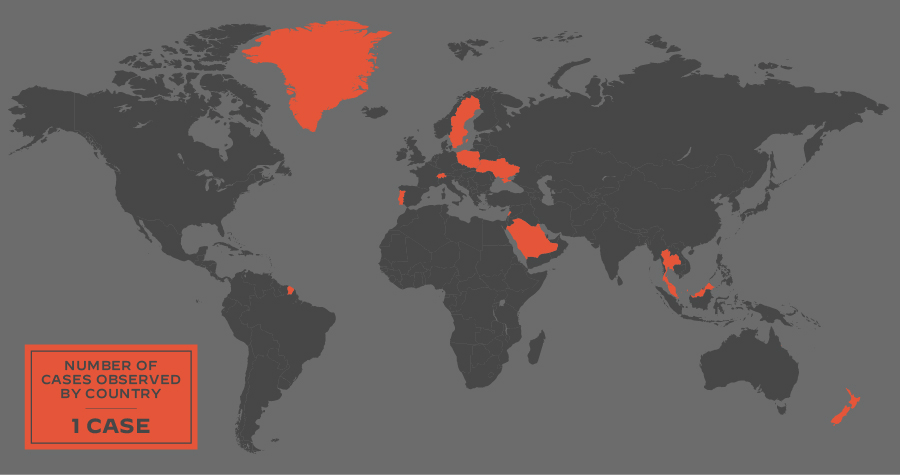
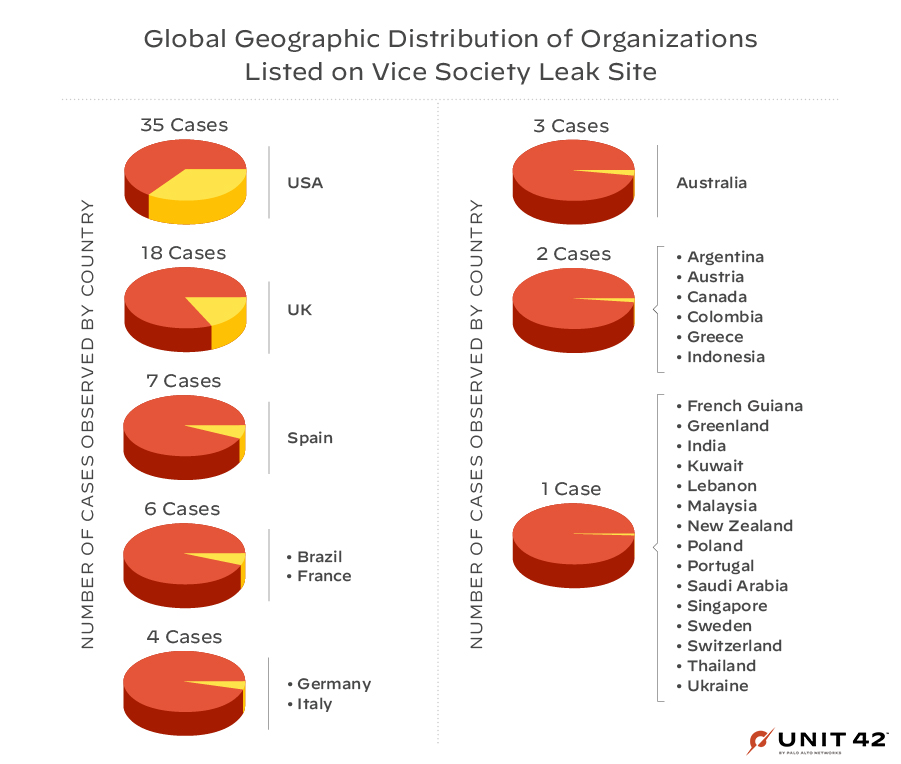
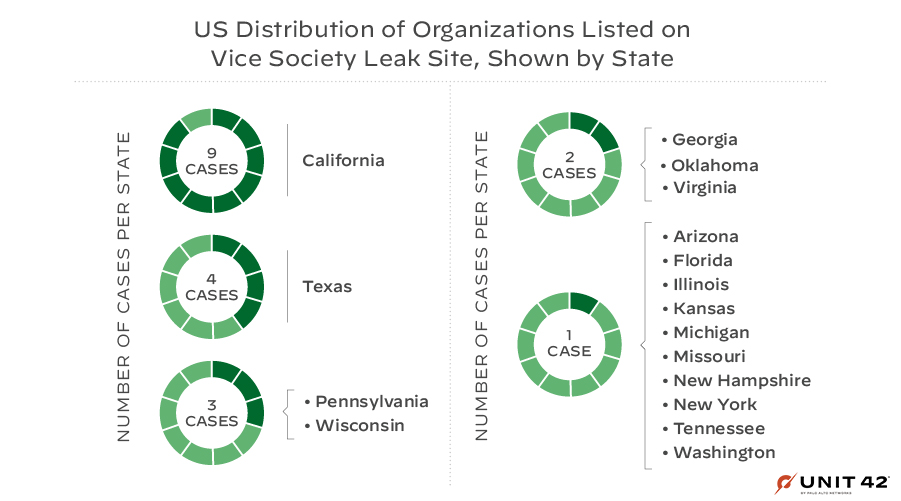
The CISA advisory mentions how Vice Society has disproportionately targeted educational institutions in the United States. Looking at leak site data in more detail, the group appears to be targeting more educational organizations based in California, as shown in Figure 5.
Impacted Industry Verticals
Although Vice Society has been in the headlines for targeting educational organizations, they also extort victims in many other industry verticals, as shown in Figure 6, including those supplying critical infrastructure, such as healthcare, government entities and manufacturing.
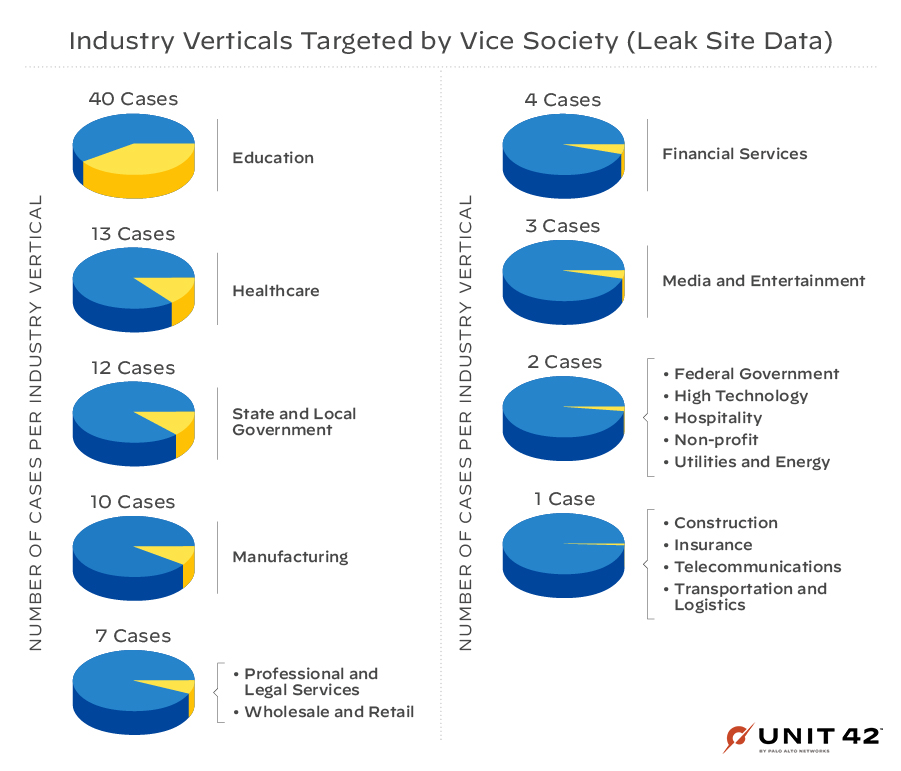
Leak Site Metric Comparisons
According to analysis of ransomware leak sites, Unit 42 has identified Vice Society as being in the top 10 of the most impactful ransomware gangs of 2022. We estimate that, since it started operations in 2021, Vice Society has impacted more than 100 organizations in total. More than 90 of the total published leak site infections occurred in the year 2022 alone.
Leak site data suggests that Vice Society has had the highest impact on education organizations this year, with at least 33 educational institutions having been listed on the group’s dedicated ransomware leak site. This impact is closely followed by ransomware families such as LockBit 2.0 and 3.0, as shown in Figure 7.
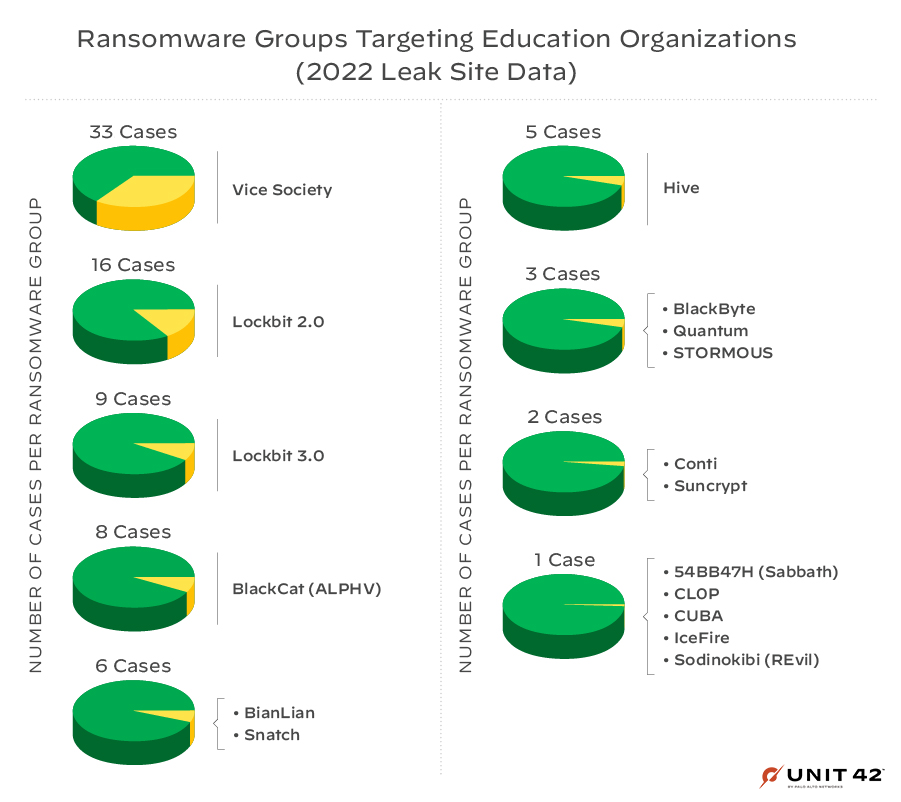
Unit 42 Incident Response Data on Vice Society
Since Vice Society’s inception in 2021, Unit 42 has performed incident response (IR) engagements with clients who have been impacted by Vice Society. Let’s look at some of the data from these incidents.
Dwell Time
In Unit 42 IR cases regarding Vice Society, we observed dwell times as high as six days. This represents the time elapsed between the date of initial compromise and the date of initial discovery.
Ransom Demands
When tracking ransomware group operations, Unit 42 takes note of the initial and final ransom demands made by each ransomware group. This allows us to better understand how aggressive a particular ransomware gang’s demands might be for particular industry verticals, and to get a general view into the rate at which a particular actor might drive their demands down after negotiations take place.
Our observations of ransom demands by Vice Society across IR cases include:
- Initial demands by this actor could exceed $1 million.
- Final demands after negotiations were as high as $460,000.
- The difference between initial demands and final demands could be significant. We saw decreases as large as 60%.
Vice Society Technical Details
Leak Site Synopsis
Over the past year, Vice Society has operated sites on the Tor network using the following .onion address:
vsociethok6sbprvevl4dlwbqrzyhxcxaqpvcqt5belwvsuxaxsutyad[.]onion
On Oct. 20, the primary .onion address became inactive, while the following site mirror was still active: ssq4zimieeanazkzc5ld4v5hdibi2nzwzdibfh5n5w4pw5mcik76lzyd[.]onion
Recently, the header for the group’s blog site bears a striking resemblance to the logo of a popular video game titled “Grand Theft Auto: Vice City” (shown in Figure 8).
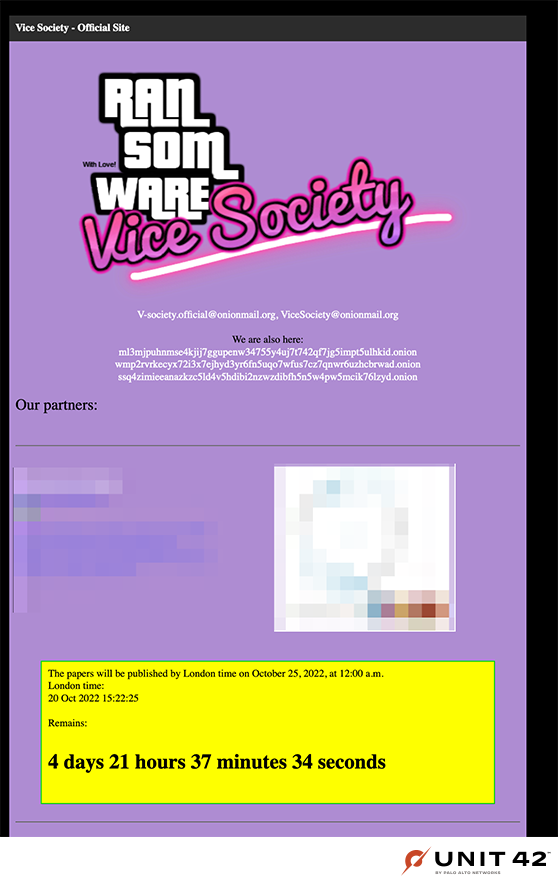
On Oct. 25, the original .onion address became active again. It was updated to include additional blog sections. As of early November, the “Our Blog” page showcased one article that highlights the group's notoriety, as shown in Figure 9.
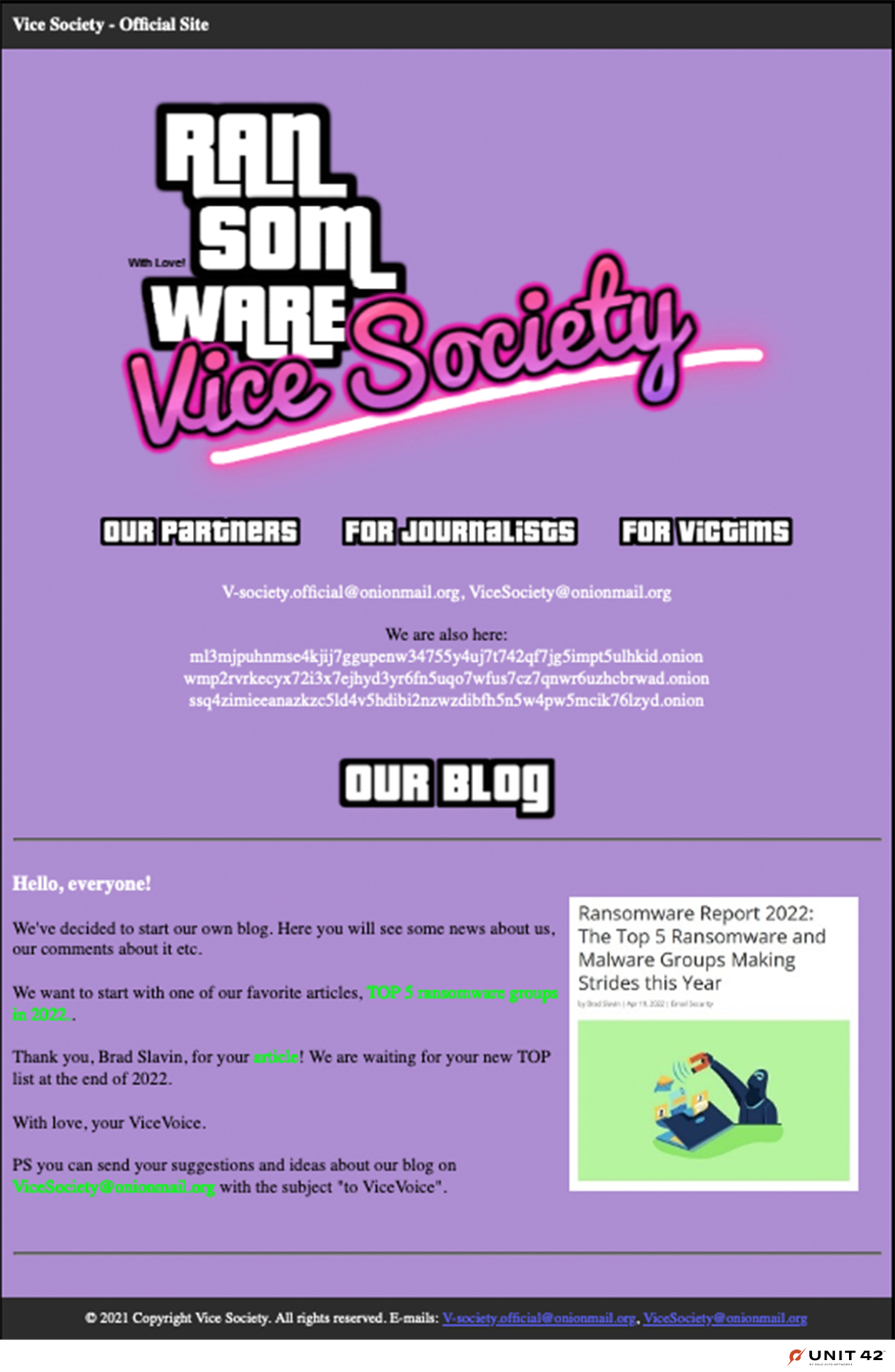
The new “Our Partners” page takes the place of the main page from the previous incarnation of the leak site, including links to view leaked victim data.
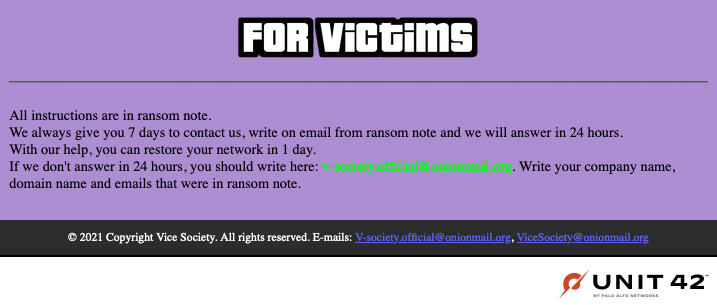
The new “For Victims” page directs victims to the ransom note that is dropped as part of the group’s infection chain. This is followed by additional instructions in case the victim doesn’t respond to one of the contact emails provided in their ransom note. During the extortion process, the attacker typically gives victims seven days to fulfill ransom demands, as shown in Figure 10.
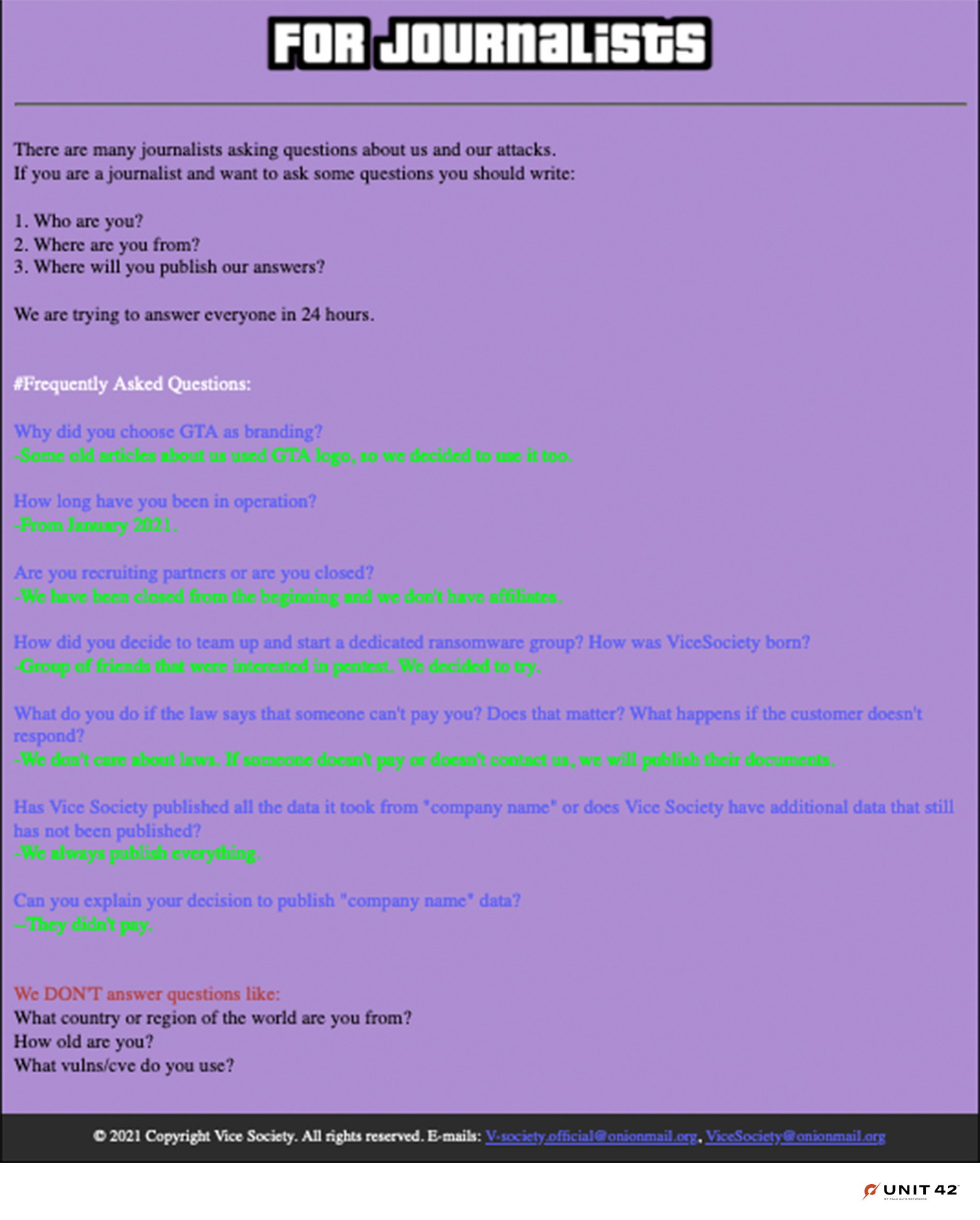
The “For Journalists” page depicts a “Frequently Asked Questions” section to address general questions about the group, as shown in Figure 11.
HelloKitty Usage
At the start of the group’s observed operations in 2021, Vice Society affiliates used the HelloKitty Ransomware variant as a primary payload in their infection chain.
This ransomware family was first observed in December 2020, primarily targeting Windows systems. This variant gets its name from its mutex: HELLOKITTYMutex.
In July 2021, as described in our HelloKitty ATOM, Unit 42 came across a Linux (ELF) sample with the name funny_linux.elf that had a ransom note with contents similar to those of HelloKitty for Windows samples. This Linux sample led to the discovery of additional HelloKitty samples for Linux dating back to October 2020. In March 2021, HelloKitty’s Linux variant was also observed in the wild to target ESXi servers.
Similar to ransomware variants like BlackCat, HelloKitty ransomware typically requires a key to execute, to hinder analysis efforts. In HelloKitty’s case, this key is typically obfuscated with AES 256 encryption. As mentioned in our previous report detailing emerging ransomware families in 2021, HelloKitty features multiple flags that could be set as command line arguments, which are detailed in Table 1 of the linked report.
When the encryption process is complete, encrypted files are typically appended with an extension using the following format: .v-society.<victim ID>.
Zeppelin Usage
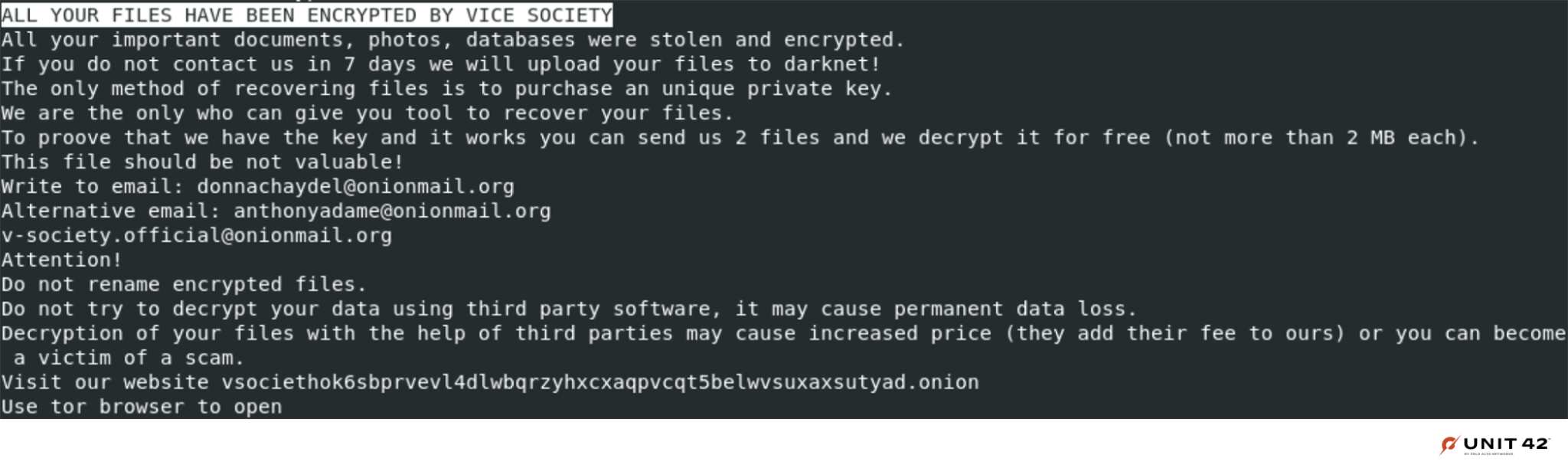
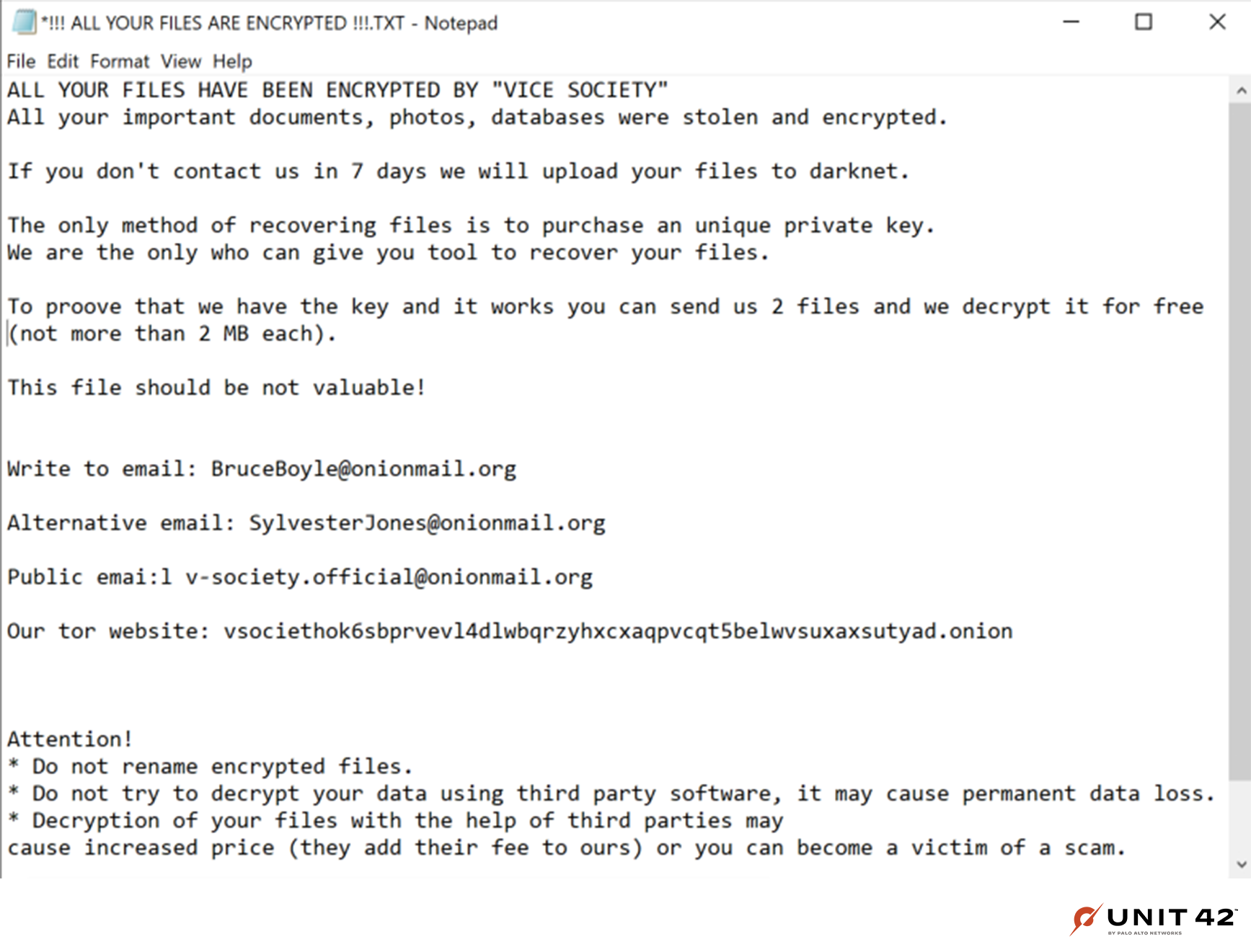
As previously mentioned, the Vice Society group has also been known to adopt other ransomware families such as Zeppelin as a part of their infection chain. Upon execution, the ransomware binary deletes itself and drops a ransom note on the victim machine’s desktop titled !!! ALL YOUR FILES ARE ENCRYPTED !!!.TXT. The contact email address provided by the threat actor vary between samples, but the public [email protected][.]org address and the Tor .onion link remain consistent.
Additional execution details include the following:
- Creating the HKCU\Software\Zeppelin registry key
- Appending an extension with the format A1A-A80-4CD to encrypted files
- Creating a file called README.txt.v-society
- Imphash: 8acb34bed3caa60cae3f08f75d53f727
- Creating a temp file with a .Zeppelin extension using the following format - C:\Users\<User>\AppData\Local\Temp\7D3ED7F1.Zeppelin
Conclusion
School districts with limited cybersecurity capabilities and constrained resources are often the most vulnerable to threat actors. The opportunistic targeting often seen with cybercriminals can put even school districts with robust cybersecurity programs at risk. K-12 institutions may be seen as particularly lucrative targets due to the amount of sensitive student data accessible through school systems or their managed service providers.
Vice Society and its consistent targeting of the education industry vertical, particularly around the September time frame, serves as a warning that this group has shaped their campaigns to take advantage of the school year in the U.S. It’s likely they’ll maintain use of these tactics to impact the cyberthreat landscape moving forward, as long as their activities continue to be lucrative for them.
Educational institutions should continue to implement security best practices and be wary of the ongoing threat of ransomware, especially during the start and end of the school year.
K-12 institutions and universities do have an advantage when it comes to protecting themselves that too few organizations use to its full potential. In a school environment, there are many educators who can help inform trainings for both staff and students to learn what they need to do to maintain security for everyone in the organization.
Vice Society’s use of multiple ransomware payloads across both Windows and Linux hosts shows that they’re continually evolving. They will likely continue leveraging additional ransomware strains in the future, as well as exploiting newly disclosed vulnerabilities.
As we do with other ransomware groups, Unit 42 strongly advises organizations that have been impacted by Vice Society to avoid paying a ransom if possible, and to instead consult a trusted IR negotiation team for the best course of action.
Palo Alto Networks customers receive protections against ransomware used by Vice Society from Cortex XDR, as well as from the WildFire cloud-delivered security service for the Next-Generation Firewall.
If you think you may have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America Toll-Free: 866.486.4842 (866.4.UNIT42)
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200
Tactics, Techniques and Procedures (TTPs)
Unit 42 has observed the following TTPs being used by Vice Society in past incident response engagements involving the group. The following table illustrates these TTPs according to the MITRE ATT&CK framework.
| TA0001 Initial Access | |
| T1566 Phishing | Vice Society is known to use phishing to gain initial access to victims’ systems. |
| T1078 Valid Accounts | Compromised valid credentials have been used by Vice Society to gain initial access. |
| T1190 Exploit Public-Facing Applications | Internet-facing applications and systems vulnerabilities can be exploited, such as PrintNightmare (CVE-2021-1675) and (CVE-2021-34527), to gain initial access. |
| TA0002 Execution | |
| T1047 Windows Management Instrumentation (WMI) | Malicious commands are executed via WMI as a means of “living off the land” and avoiding detection. |
| T1053.005 Scheduled Task/Job | Vice Society is known to execute commands via scheduled tasks/jobs. |
| T1059.001 Command and Scripting Interpreter: Powershell | Vice Society utilizes PsExec for execution, persistence and defense evasion. |
| T1059.003 Command and Scripting Interpreter: Command Shell | Batch files are used by Vice Society to deploy the ransomware via PsExec. |
| TA0003 Persistence | |
| T1543.003 Modify System Process | To maintain access to compromised systems, Vice Society leverages Windows operating functions to execute encrypted PowerShell. |
| T1547.001 Registry Run Keys/Startup Folder | Persistence is maintained after boot/reboot via malicious autostart registry keys. |
| T1574.002 DLL Side-Loading | Vice Society utilizes legitimate programs to side-load the group’s own DLL to execute their payload. |
| TA0004 Privilege Escalation | |
| T1068 Exploitation for Privilege Escalation | Software vulnerabilities, such as PrintNightmare (CVE-2021-1675) and (CVE-2021-34527), may be exploited in an attempt to elevate privileges. |
| TA0005 Defense Evasion | |
| T1036 Masquerading | Files dropped in the victim’s environment by Vice Society may have been altered to appear legitimate. |
| T1055 Process Injection | Legitimate processes have been corrupted by Vice Society via code injection, as a means to evade defenses. |
| T1070 Indicator Removal on Host | As with many other ransomware groups, Vice Society attempts to clear system, security and application logs on compromised machines. |
| T1112 Modify Registry | Vice Society attempts to disable Windows Defender by modifying the Registry. |
| T1497 Sandbox Evasion | Vice Society attempts to thwart reverse engineering and/or dynamic analysis via various sandbox evasion techniques. |
| T1562.001 Impair Defenses: Disable or Modify Tools | Attempts to disable or modify endpoint security, such as Microsoft Defender, on compromised devices. |
| TA0006 Credential Access | |
| T1003 OS Credential Dumping | Vice Society is known to utilize ntds.dit and comsvcs.dll to extract credentials. |
| T1003.001 OS Credential Dumping: LSASS Memory | Vice Society utilizes comsvcs.dll to dump credentials from Local Security Authority Subsystem Service. |
| T1003.003 OS Credential Dumping: NTDS | Vice Society attempts to “live off the land” by utilizing ntds.dit and ntdsutil.exe to dump Active Directory Database in an effort to obtain credentials. |
| TA0007 Discovery | |
| T1046 Network Service Discovery | Vice Society has been seen using the recon tool called Advanced Port Scanner to identify running services and local network infrastructure. |
| T1482 Domain Trust Discovery | Vice Society has been seen using the attack path reconnaissance tool Bloodhound during the initial stages of their attack before ransomware is deployed. |
| TA00008 Lateral Movement | |
| T1021 Remote Services | RDP is used by the group for lateral movement. |
| T1021.002 Remote Services: SMB/Windows Admin Shares | SMB shares have been used by Vice Society for lateral movement. |
| T1080 Taint Shared Content | Network drives and other shared storage locations are used by Vice Society to deliver payloads. |
| T1570 Lateral Tool Transfer | Lateral tool transfers have been used to move tools and files from one compromised system to another, including SMB and RDP. |
| TA0010 Exfiltration | |
| T1020 Automated Exfiltration | PowerShell scripts are used to exfiltrate data to external C2 servers. |
| T1041 Exfiltration over C2 Channel | Tools such as PowerShell and PsExec are used to exfiltrate data directly to C2 servers. |
| T1048 Exfiltration Over Alternative Protocol | Vice Society has used SMB in attempts to exfiltrate data. |
| T1567.002 Exfiltration Over Web Service: Exfiltration to Cloud Storage | Cloud storage and transfer services such as Mega.nz, Anonfiles.com, File.io, and Sendspace have been used by Vice Society to exfiltrate victim data. |
| TA0011 Command and Control | |
| T1219 Remote Access Software | Tools such as SystemBC and proprietary backdoors are known to be used by Vice Society. |
| TA0040 Impact | |
| T1486 Data Encrypted for Impact | Vice Society is known for its extortion tactics, encrypting devices and demanding a ransom. |
| T1531 Account Access Removal | Vice Society is known to change passwords of compromised victim accounts and privileged users, such as email and administrator accounts. |
Indicators of Compromise (IoCs)
HelloKitty Elf samples featuring Vice Society ransom note header:
- 643a3121166cd1ee5fc6848f099be7c7c24d36f5922f58052802b91f032a5f0f
- 754f2022b72da704eb8636610c6d2ffcbdae9e8740555030a07c8c147387a537
- 78efe6f5a34ba7579cfd8fc551274029920a9086cb713e859f60f97f591a7b04
- 16a0054a277d8c26beb97850ac3e86dd0736ae6661db912b8782b4eb08cfd36e
Zeppelin ransomware with the Vice Society ransom note header:
- 4a4be110d587421ad50d2b1a38b108fa05f314631066a2e96a1c85cc05814080
- 307877881957a297e41d75c84e9a965f1cd07ac9d026314dcaff55c4da23d03e
- faa79c796c27b11c4f007023e50509662eac4bca99a71b26a9122c260abfb3c6
- dd89d939c941a53d6188232288a3bd73ba9baf0b4ca6bf6ccca697d9ee42533f
- 4440763b18d75a0f9de30b1c4c2aeb3f827bc4f5ea9dd1a2aebe7e5b23cfdf94
- 24efa10a2b51c5fd6e45da6babd4e797d9cae399be98941f950abf7b5e9a4cd7
- bafd3434f3ba5bb9685e239762281d4c7504de7e0cfd9d6394e4a85b4882ff5d
- aa7e2d63fc991990958dfb795a0aed254149f185f403231eaebe35147f4b5ebe
- 001938ed01bfde6b100927ff8199c65d1bff30381b80b846f2e3fe5a0d2df21d
- Ab440c4391ea3a01bebbb651c80c27847b58ac928b32d73ed3b19a0b17dd7e75
Contact information:
- [email protected][.]org
- [email protected][.]org
- [email protected][.]org
- [email protected][.]org
- [email protected][.]org
- [email protected][.]org
- [email protected][.]org
- [email protected][.]org
- [email protected][.]org
- [email protected][.]org
- [email protected][.]org
- [email protected][.]org
- [email protected][.]org
- [email protected][.]org
Domains:
- vsociethok6sbprvevl4dlwbqrzyhxcxaqpvcqt5belwvsuxaxsutyad[.]onion
- Qu5dci2k25x2imgki2dbhcwegqqsqsrjj5d3ugcc5kpsgbtj2psaedqd[.]onion
- Wavbeudogz6byhnardd2lkp2jafims3j7tj6k6qnywchn2csngvtffqd[.]onion
- gunyhng6pabzcurl7ipx2pbmjxpvqnu6mxf2h3vdeenam34inj4ndryd[.]onion
Additional Resources
Threat Brief: Windows Print Spooler RCE Vulnerability (CVE-2021-34527 AKA PrintNightmare)
Emerging Ransomware Groups: AvosLocker, Hive, HelloKitty, LockBit 2.0
Threat Assessment: Zeppelin Ransomware
#StopRansomware: Vice Society | CISA
Dark Web Profile: Vice Society - SOCRadar® Cyber Intelligence Inc.
Michael Gillespie Twitter post
Unit 42 ATOM: HelloKitty
UNC2447 SOMBRAT and FIVEHANDS Ransomware: A Sophisticated Financial Threat | Mandiant
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
如有侵权请联系:admin#unsafe.sh