
2018-02-15 08:32:43 Author: medium.com(查看原文) 阅读量:392 收藏
TL;DR
As a proof of concept, I wrote script which abuses social media in order to send commands to infected machines, i.e bots. It uses platforms like Twitter, Instagram, Youtube and results are sent to Telegram. Additionally, it can be used as a legitimate tool for remotely administrating your computer.
INTRODUCTION
When I was looking for inspiration and challenge, I stumbled upon article from ESET describing how Turla Group (more about them here) took advantage of Instagram and posted there address to theirs command and control server. “Malicious payload” was hidden in comment on one of the Britney Spears’ photos. They checked every comment, computed hash and if there was a match, then run regex against chosen comment. End goal was to obtain link to bit.ly (popular tool for shortening links). Probably, they were just testing new methods for delivering payloads and c&c addresses and whether it can be deployed on bigger scale. I think it’s hard to manage massive botnet in this way, it’s more useful in stealthy and covert operations. Additionally, it generates traffic only to social media platforms and we know how hard it can be to block these sites.

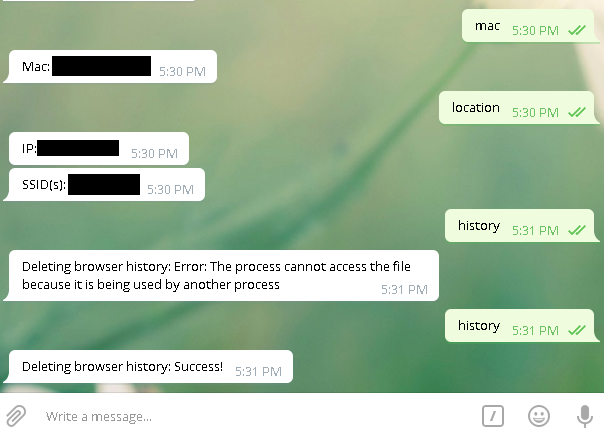
Interested in this, I was wondering if there is a way to control computer just with help of Twitter or other popular websites for exchanging photos or videos. It turned out that it’s easy and it’s quite fun. My proof of concept, for example, allows you to remotely delete your history browser with just one tweet containing #history hashtag. To show how it can be used in nefarious way, I weaponized it a little by adding module responsible for obtaining MAC address and location based on ipify.org and last connected SSID’s.
I wanted to keep it simple so available commands are: history, location, mac and update, which I will describe later.
Every module was wrote with API and have hardcoded keys. I believe you can achieve similar results with requests module or BeautifulSoup.
As it’s only proof of concept, it was wrote and tested just on one machine and there is no identification numbers, heartbeats and other things, which are used on typical botnets.
TELEGRAM
It’s the most simple, trivial and easy to implement way for accessing your machine remotely, you just send a message to Telegram bot and proper module is called. Telecrypt ransomware was using this technique but only for receiving messages (computer’s name, infection id and key seed) from infected computers. In my case, Telegram listens in specified timeout for new commands and then calls adequate function. Worth to mention is that you have to check only new messages and make sure that previous commands won’t be executed again and again. We can achieve that with offset parameter, Codementor made good tutorial about Python and Telegram.
def getMessage(self, offset):
if offset:
update = self.bot.getUpdates(offset=offset)
else:
update = self.bot.getUpdates()
update_json = json.loads(update[2])
return update_json
There is quite cool trick to get location without reaching internet, you can check for names of last networks that he or she was connected to. As everybody already knows, SSIDs are kept in registry in
SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkList\Profiles\. When we have this values, we can check of them in wigle.net, which has map of 400 million wifi networks. If SSID(s) won’t be accessible we are sure that user has no admin rights.
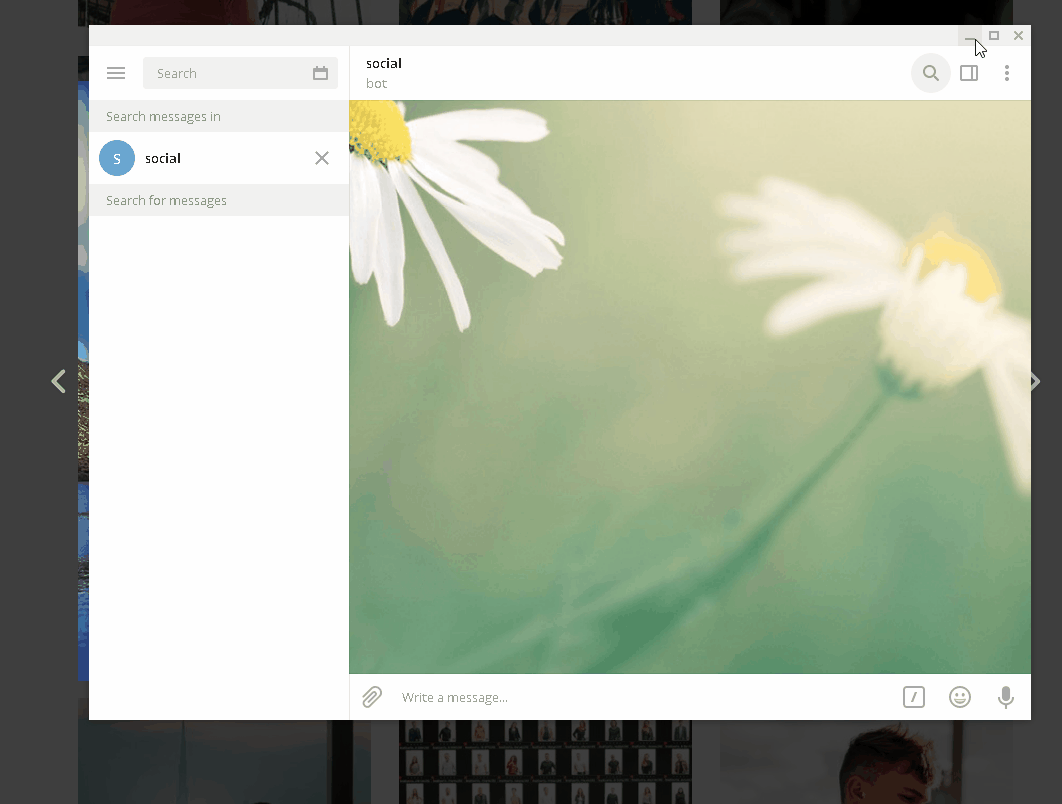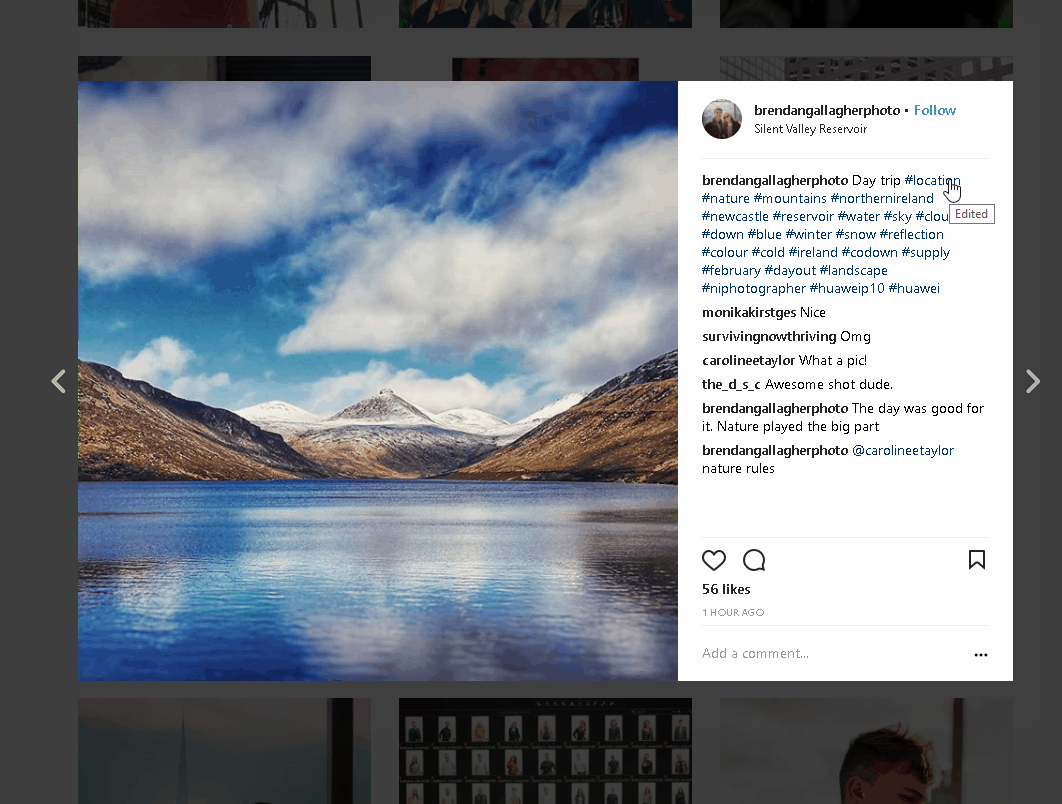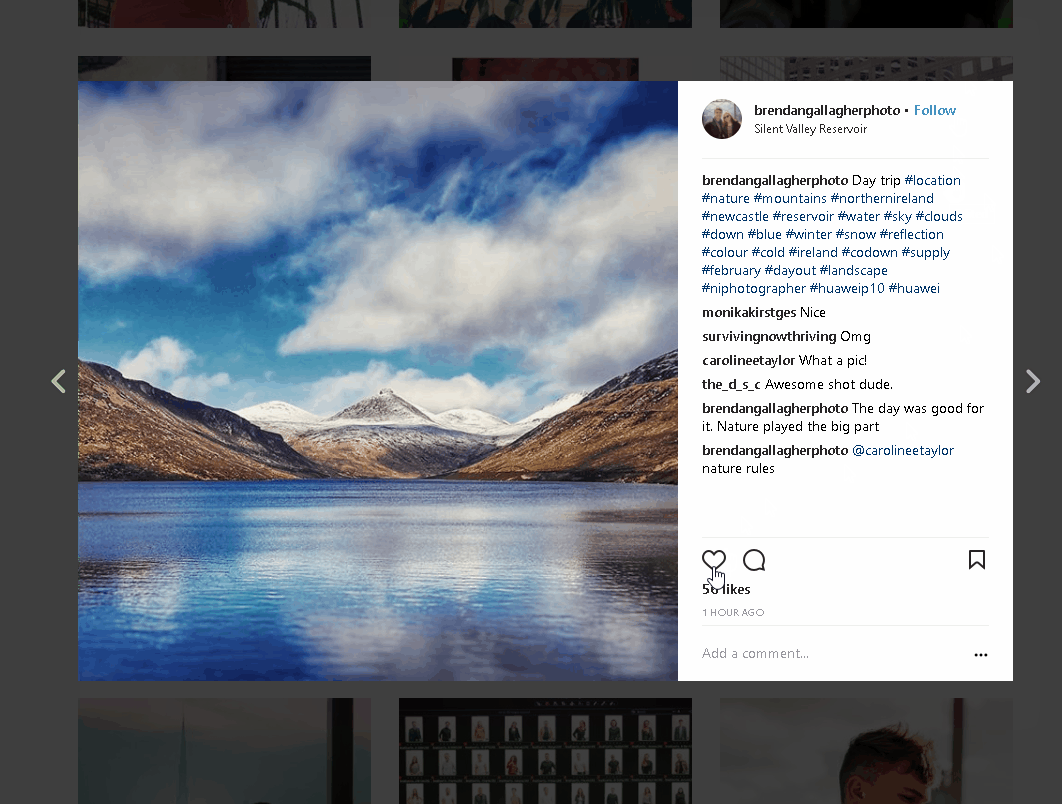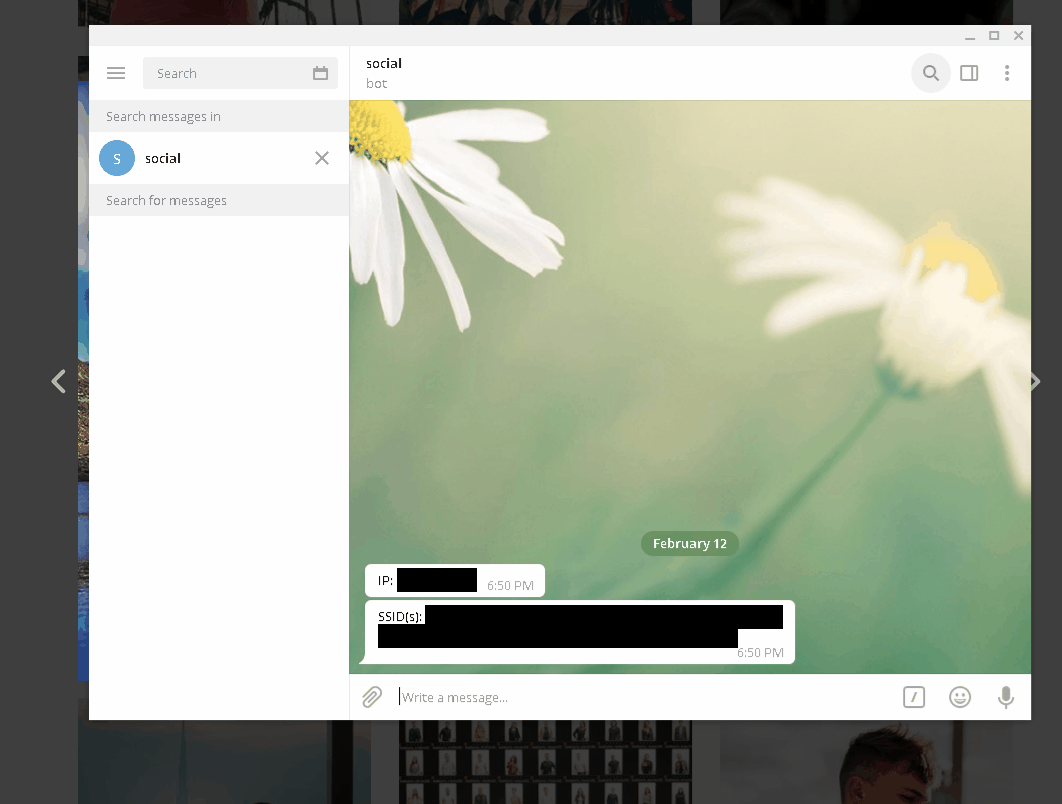
Next technique is based on Instagram, module is called when you like photo with description (hashtags also count) including one of the available commands. It’s really stealthy because it’s impossible to monitor who likes what in real time,besides that you can ‘delete’ your like after command will be executed. It does not matter what kind of photo you liked but it must include specified command in description. For this module I used Instagram API for python. In this case, you must pass your credentials instead of API keys.
Things with Twitter are straightforward and similar to previous concept. In order to run a command, you need to retweet or make a tweet contains keywords: location, history, mac or update. Limitation here is that Tweepy can retrieve only first 150 characters of the Tweet, so your payload must be at the beginning. Same as with Instagram, you can delete your message immediately after command will be executed. I found only two documented cases, when malicious actor was abusing Twitter for sending his payloads. Messages contained links to bit.ly, which next redirected to infostealer malware but everything were base64 encoded. It’s easy to find out what’s going on when you see tweets with weird string of characters. In Youtube case, I will show how to retrieve this kind of links in more discrete way.
This module allows you to (re)tweet whatever you want, but your (re)tweet must include one of the commands to be executed. When you feel like you are dying, you can delete your browser history with one tweet.
def deleteBrowserHistory(self):
firefox = os.path.join("C:", os.sep, "Users", os.getenv('username'), "AppData", "Roaming", "Mozilla", "Firefox",
"Profiles") # get path to firefox
list_profiles = os.listdir(firefox) # list directoryfor i in list_profiles: # for every founded profile
sqlite_path = "C:\Users\\" + os.getenv(
'username') + "\AppData\Roaming\Mozilla\Firefox\Profiles\\" + i + "\places.sqlite" # get pathtry:
os.remove(sqlite_path) # try to remove history - places.sqlite file
return "Success!"
except WindowsError as e:
return "Error: " + e.strerror # File can be used by another process

If there are so many (Russian?) bots on Twitter, it would be interesting to use them for controlling botnet, though.
Youtube
With ‘update’ module we can retrieve address of CnC server like in Turla group example, but if I were one of theirs member, I would choose Youtube to place my comments. We are still on the ‘hide in plain sight’ path, so the best place to hide our “payload” is among other bots. Weird shit going on Youtube right now, this video (you are watching on your own responsibility) has 8 millions views in four months and comments are insane, mostly created by bots or kids. If you take a look at the comments on this video, you will see how it’s messed up and how easy is to hide anything there.
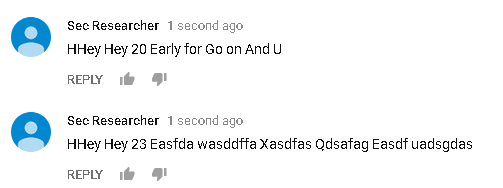

You can check that link: bit.ly/2EwXQEu or second one bit.ly/2EfGoAU. First leads to my blog and second to random page on Infogalactic.
For simplicity I didn’t use any hashing algorithm like Russians but you can implement it on your own. I check if comment starts with specified phrase, letter or symbol. I choose lame beginning “HHey Hey”, first “H” was added for unique, however it can be anything.
def getKeyword(self, comment):
keyword = ""
if comment.startswith(self.COMMENT_START): # if comment starts with COMMENT_START variable defined at the top
new_string = comment[len(COMMENT_START) + 1:]
for i in new_string.split(" "): # make list from remaining words
keyword += i[0] # create keyword from first letter of every word in new_string.split()return keyword
If first condition is met, then script gets first letter of remaining words from the rest of comment. Connected into one, give address to bit.ly. This technique allows you to pass various addresses, chat id for Telegram’s bot (in case of ban) or commands directly.
Conclusion
As you could see, it’s very easy to abuse Instagram, Twitter, Youtube and Telegram to control our administration tool. Additionally, it generates traffic only to trusted servers, which are not blocked in most cases, logs will show behavior like someone was browsing social media sites. However it has limitations such as your account can be banned, comment can be deleted or you have to hardcode API keys (I believe that with some effort someone can manage it).
You can find script here
I am not responsible for what you will do with this, be cautious.
Further reading
如有侵权请联系:admin#unsafe.sh