Views: 6,956
APT-Hunter is a threat hunting tool for windows event logs made from the perspective of the purple team mindset to provide detection for APT movements hidden in the sea of windows event logs.
[ad name=”Darknet_Body_468_Links”]
This will help you to decrease the time to uncover suspicious activity and the tool will make good use of the windows event logs collected and make sure to not miss critical events configured to be detected.
The target audience for APT-Hunter is threat hunters, incident response professionals or forensic investigators.
Features of APT-Hunter Threat Hunting Tool
- Provide output with time sketch format to upload it directly and start analyzing the time line
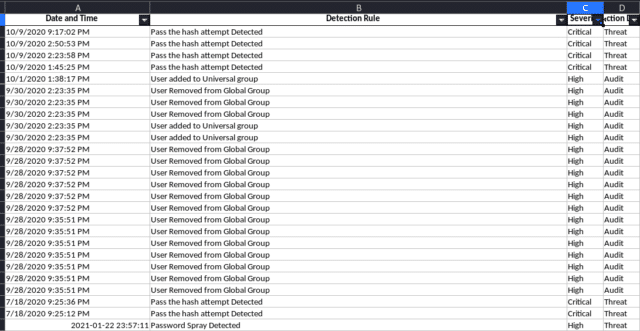
- Events Categorized based Severity to make the filtering easy and focus on what important
- Have A log collection automation script to collect all the required logs to save the time required to export important logs
- Gather and analyze (Sysmon, Security, System, Powershell, Powershell_Operational, ScheduledTask, WinRM, TerminalServices, Windows_Defender)
- This rule tested in many real incidents and provided a great information that reduced the time to detect initial evidence
- Can run on any system thanks to python3, you can do live analysis on the affected system or take the logs offline and analyze them on any system
- Log Parsing and extraction using Regex
- This tool built based on researches published on the internet and testing done by me in order to collect most of the useful use cases in one tool
- Includes more than 60 Use cases along with Security and terminal services logs statistics and more will be added soon . Say good bye to memorizing use cases and SIEM searches
- Now you don’t need to setup instance of SIEM, Log collector solutions to help you parse and extract the required data nor you have to keep looking at sheet with million of events
- Log statistics that will help you uncover the anomaly
- Easy to add new detection rule as the fields clear and syntax easy to use
- Support windows event logs exported as EVTX and CSV
- Analyst can add new malicious executable names directly to list
- Provide output as excel sheet with every Log as work sheet
Using APT-Hunter Threat Hunting Tool
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
# python3 APT-Hunter.py -h usage: APT-Hunter.py [-h] [-p PATH] [-o OUT] [-t {csv,evtx}] -h, --help show this help message and exit -p PATH, --path PATH path to folder containing windows event logs generated by the APT-Hunter-Log-Collector.ps1 -o OUT, --out OUT output file name -t {csv,evtx}, --type {csv,evtx} csv ( logs from get-eventlog or windows event log GUI or logs from Get-WinEvent ) , evtx ( EVTX extension windows event log ) --security SECURITY Path to Security Logs --system SYSTEM Path to System Logs --scheduledtask SCHEDULEDTASK Path to Scheduled Tasks Logs --defender DEFENDER Path to Defender Logs --powershell POWERSHELL Path to Powershell Logs --powershellop POWERSHELLOP Path to Powershell Operational Logs --terminal TERMINAL Path to TerminalServices LocalSessionManager Logs --winrm WINRM Path to Winrm Logs --sysmon SYSMON Path to Sysmon Logs -p : provide path to directory containing the extracted using the powershell log collectors ( windows-log-collector-full-v3-CSV.ps1 , windows-log-collector-full-v3-EVTX.ps1 ) . -o : name of the project which will be used in the generated output sheets -t : the log type if its CSV or EVTX |
You can download APT-Hunter here:
Linux: APT-Hunter-nix.zip
Windows: APT-Hunter_Windows.zip
Source: v1.0-beta.zip
Or read more here.