Views: 62
HardCIDR is a Linux Bash script to discover the netblocks, or ranges, (in CIDR notation) owned by the target organization during the intelligence gathering phase of a penetration test.
This information is maintained by the five Regional Internet Registries (RIRs):
- ARIN (North America)
- RIPE (Europe/Asia/Middle East)
- APNIC (Asia/Pacific)
- LACNIC (Latin America)
- AfriNIC (Africa)
In addition to netblocks and IP addresses, Autonomous System Numbers (ASNs) are also of interest. ASNs are used as part of the Border Gateway Protocol (BGP) for uniquely identifying each network on the Internet. Target organizations may have their own ASNs due to the size of their network or as a result of redundant service paths from peered service providers. These ASNs will reveal additional netblocks owned by the organization.
Usage of HardCIDR – Network CIDR and Range Discovery Tool
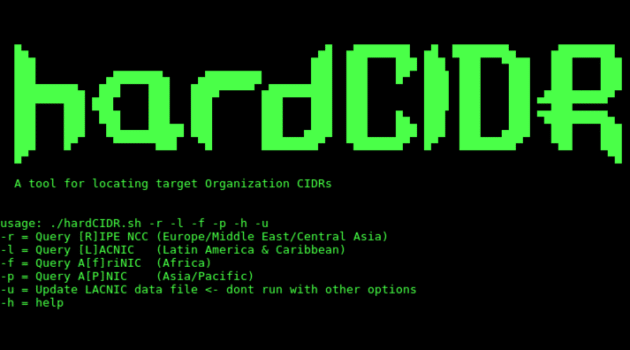
The script with no specified options will query ARIN and a pool of BGP route servers. The route server is selected at random at runtime. The -h option lists the help:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 |
█▄ ▄█ ▄████████ ▄█ ████████▄ ▄████████ ███ ███ ███ ███ ███ ███ ▀███ ███ ███ ███ ▄███████▄ ▄████████ ███ ███ █▀ ███▌ ███ ███ ███ ███ █████████▄ ███ ███ ████▀▀▀▀▀ ▄█████████ ███ ███▌ ███ ███ ▄███▄▄▄▄██▀ ███▀▀▀▀███ ███ ███ ███ ███ ███ ███ ███▌ ███ ███ ▀▀███▀▀▀▀▀ ███ ███ ███ ███ ███ ███ ███ ███ █▄ ███ ███ ███ ▀█████████▄ ███ ███ ██▄▄▄▄█████ ███ ███ ▄███ ███ ███ ███ ███ ▄███ ███ ███ ███ █▀ ▀▀▀▀▀▀███ ▀█ ████████▀ ▀███████▀ █▀ ████████▀ ▀██ ███ █▀ ▀█ A tool for locating target Organization netblocks Written by: Jason Ashton, TrustedSec Website: https://www.trustedsec.com Twitter: @ninewires usage: ./${sname} -r -l -f -p -h -u -r = Query [R]IPE NCC (Europe/Middle East/Central Asia) -l = Query [L]ACNIC (Latin America & Caribbean) -f = Query A[f]riNIC (Africa) -p = Query A[P]NIC (Asia/Pacific) -u = Update LACNIC data file <- dont run with other options -h = help |
The options may be used in any combination, all, or none. Unfortunately, none of the “other” RIRs note the actual CIDR notation of the range, so ipcalc is used to perform this function. If it is not installed on your system, the script will install it for you.
At the prompts, enter the organization name, the email domain, and whether country codes are used as part of the email. If answered Y to country codes, you will be prompted as to whether they precede the domain name or are appended to the TLD. A directory will be created for the output files in /tmp/. If the directory is found to exist, you will be prompted to overwrite it. If answered N, a timestamp will be appended to the directory name.
You can download HardCIDR here:
Or read more here.https://github.com/trustedsec/hardcidr