
2023-1-4 16:8:52 Author: blog.nviso.eu(查看原文) 阅读量:27 收藏
Introduction
Last year, I published an article on mapping detection to the MITRE ATT&CK framework using DeTT&CT. In the article, we introduced DeTT&CT and explored its features and usage. If you missed it, you can find the article here.
Although, after writing that article, I encountered some challenges. For instance, I considered using DeTT&CT in a production environment but there were hundreds of existing detection rules to consider, and it would have been a tedious process to manually create the necessary YAML file for building a detection coverage layer. As a result, I decided not to use DeTT&CT and instead focused on increasing detection in other ways.
Fortunately, a new tool called Dettectinator has recently been released. Its purpose is to address these kinds of issues and make it easier to automate detection coverage.
In this article, we will explore Dettectinator, its features, and walk through the steps to automate the detection coverage for Sentinel Analytics rules and Elastic detection rules.
What is dettectinator
Dettectinator is a tool developed by Martijn Veken and Ruben Boumen of Sirius Security that enables the automation of DeTT&CT data source and technique administration YAML files needed to create visibility and detection layers in the ATT&CK Navigator. This tool can be integrated as a Python library within your security operations center (SOC) automation tools or used via the command line.
To use the Python library, install it with “pip install dettectinator” and import one of the following classes into your code:
- DettectDataSourcesAdministration
- DettectTechniquesAdministration
These classes allow you to programmatically edit DeTT&CT YAML files, including creating new data source and techniques administration files and modifying existing ones.
from dettectinator import DettectDataSourcesAdministration
from dettectinator import DettectTechniquesAdministration
# Open an existing YAML file:
dettect_ds = DettectDataSourcesAdministration('data_sources.yaml')
# Or create a new YAML file:
dettect_ds = DettectDataSourcesAdministration()
# Open an existing YAML file:
dettect = DettectTechniquesAdministration('techniques.yaml')
# Or create a new YAML file:
dettect = DettectTechniquesAdministration()
To run as a CLI tool:
$ python dettectinator.py
Please specify a valid data import plugin using the "-p" argument:
- DatasourceCsv
- DatasourceDefenderEndpoints
- DatasourceExcel
- DatasourceWindowsSecurityAuditing
- DatasourceWindowsSysmon
- TechniqueCsv
- TechniqueDefenderAlerts
- TechniqueDefenderIdentityRules
- TechniqueElasticSecurityRules
- TechniqueExcel
- TechniqueSentinelAlertRules
- TechniqueSigmaRules
- TechniqueSplunkConfigSearches
- TechniqueSuricataRules
- TechniqueSuricataRulesSummarized
- TechniqueTaniumSignals
$ python3 dettectinator.py -p TechniqueElasticSecurityRules -h
Plugin "TechniqueElasticSecurityRules" has been found.
usage: dettectinator.py [-h] [-c CONFIG] -p PLUGIN -a APPLICABLE_TO [-d {enterprise,ics,mobile}] [-i INPUT_FILE] [-o OUTPUT_FILE] [-n NAME] [-s STIX_LOCATION] [-ch] [-cl] [-ri RE_INCLUDE] [-re RE_EXCLUDE]
[-l LOCATION_PREFIX] [-clp] --host HOST --user USER --password PASSWORD [--filter FILTER]Dettectinator provides a range of plugins for various detection systems and data source platforms, and you can even create custom plugins to suit your specific workflow. Some of the available plugins for detection include:
- Microsoft Sentinel: Analytics Rules (API)
- Microsoft Defender: Alerts (API)
- Microsoft Defender for Identity: Detection Rules (loaded from MS Github)
- Tanium: Signals (API)
- Elastic Security: Rules (API)
- Suricata: rules (file)
- Suricata: rules summarized (file)
- Sigma: rules (folder with YAML files)
- Splunk: saved searches config (file)
- CSV: any csv with detections and ATT&CK technique ID’s (file)
- Excel: any Excel file with detections and ATT&CK technique ID’s (file)
Plugins for data sources include:
- Defender for Endpoints: tables available in Advanced Hunting (based on OSSEM)
- Windows Sysmon: event logging based on Sysmon (based on OSSEM and your Sysmon config file)
- Sentinel Window Security Auditing: event logging (based on OSSEM and EventID’s found in your logging)
- CSV: any csv with ATT&CK data sources and products (file)
- Excel: any Excel file with ATT&CK data sources and products (file)
It’s easy to create your own Dettectinator plugins or edit the ones provided to cover additional scenarios. An instruction on how to create your own plugins can be found here.
Dettectinator can be seamlessly integrated into your detection engineering workflow, as illustrated in the picture below. Steps 1 and 3 can be automated using version control system (VCS) pipelines or scheduling. The analyst can enhance the techniques identified by Dettectinator by assigning appropriate scores, resulting in an enriched YAML file that can be used in future runs of the tool.

How to use dettectinator
To illustrate how to use Dettectinator from a production environment, we will walk through the steps to build your coverage from Elastic Security detection rules and Microsoft Sentinel analytics rules.
Let’s start with Elastic Security. As shown in the picture below, we enabled the built-in detection rules from Elastic which represent 724 rules in total.

Ensure that the Elastic user has the appropriate permissions to manage/read the detection rules. Refer to the Elastic documentation for more information.
In our testing environment, we created a dedicated user and assigned it a custom role (as shown in the highlighted parameters):

With the command below, we will generate the technique administration YAML file which we will use to create the ATT&CK Navigator layer:
$ python3 dettectinator.py -p TechniqueElasticSecurityRules -a Windows -d enterprise -o elasticrules_techniques.yaml –host “<URL>:<Port>” --user <username> --password <password> - -p: specify the plugin
- -a: Systems that the detections are applicable to (comma separated list)
- -d: ATT&CK domain to use {enterprise, ics, mobile} (default = enterprise)
- -o: YAML filename for output
- –host: Elastic Security host
- –user: Elastic Security username
- –password: Elastic Security user’s password

Using the DeTT&CT Editor, we were able to modify the technique administration YAML file. Alternatively, we could use the output to generate a detection ATT&CK Navigator layer through the DeTT&CT Command Line Interface (CLI).
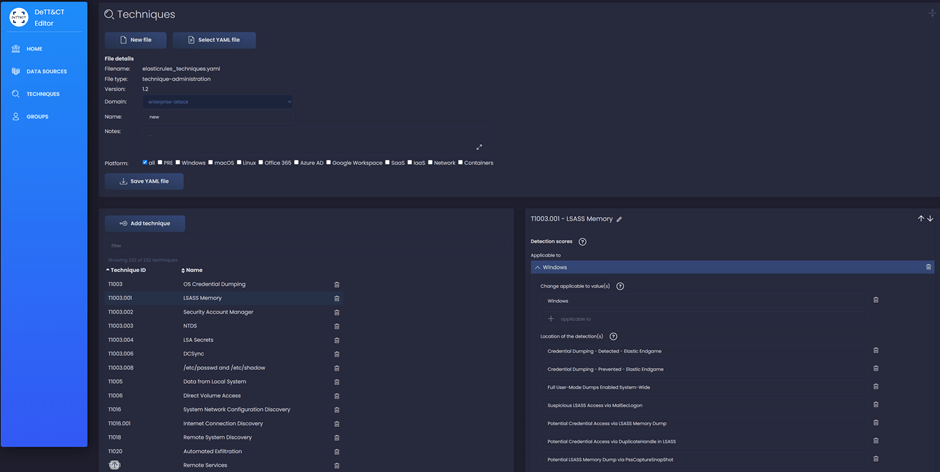
To generate the detection layer, we used the following command:
$ python3 dettect.py d -ft <YAML file generated by dettectinator> -l- d: detection coverage mapping based on techniques
- -ft: path of the technique administration YAML file
- -l: generate a data source layer for the ATT&CK Navigator
The tool dettect.py generated a JSON file that can be opened within ATT&CK Navigator.
In this case, we get a quick overview of the built-in Elastic Security detection rules. All techniques are assigned a default score of ‘1’ by dettectinator. This scoring can be customized using the DeTT&CT Editor.

When hovering over the ATT&CK techniques and sub-techniques, additional information such as related detection rules and comments generated by dettectinator will appear.
Here is an example for the technique Lateral Tool Transfer (T1570):

Now, let’s check the detection coverage from an existing Microsoft Sentinel environment with Analytics rules. In our testing example, we created an “App Registration” in Azure and granted it the following permissions:

Since we are using delegated permissions, we also had to enable “Allow public client flows” in the Authentication settings for the App Registration.
To generate the technique administration YAML for Microsoft Sentinel, we used the following command:
$ python3 dettectinator.py -p TechniqueSentinelAlertRules -a Windows -o sentinel_techniques.yaml --subscription_id <subscription_id> --resource_group <resource group name> --workspace <workspace name> --tenant_id <tenant_id> --app_id <app_id>
Dettectinator generated a JSON file containing information about a single technique. As shown in the picture below, our test Microsoft Sentinel environment contains 5 analytics rules, but only one of them as a technique specified in the metadata. As a result, Dettectinator was able to map the analytic rules to only one technique (T1190).


Conclusion
Dettectinator is a highly efficient tool that can help you optimize your detection engineering processes. By automating certain tasks, it frees up your time and resources to focus on more complex, high-level tasks.
When used in conjunction with DeTT&CT, it provides a real-time overview of your current detection coverage, giving you a clear understanding of your strengths and areas for improvement. Additionally, Dettectinator comes equipped with a range of integrations that are suitable for a variety of environments, making it a versatile and efficient tool.
In addition to its automation capabilities, Dettectinator is also highly customizable. It allows you to tailor its functionality to meet the specific needs of your organization or project.
One of the key benefits of using Dettectinator is its ability to save users a considerable amount of time. It complements DeTT&CT by addressing some of the challenges that users may face, making it an invaluable addition to any detection engineering workflow. In short, if you’re looking to streamline your detection processes and improve your coverage, Dettectinator is an excellent tool to consider.
References
“Dettectinator”, https://github.com/siriussecurity/dettectinator
“Releasing Dettectinator”, https://www.siriussecurity.nl/blog/2022/11/03/releasing-dettectinator
“DeTT&CT : Mapping detection to MITRE ATT&CK”, https://blog.nviso.eu/2022/03/09/dettct-mapping-detection-to-mitre-attck/
“rabobank-cdc/DeTTECT: Detect Tactics, Techniques & Combat Threats”, https://github.com/rabobank-cdc/DeTTECT
“ATT&CK® Navigator“, https://mitre-attack.github.io/attack-navigator/
About the author

Renaud Frère
Renaud is an Incident Response Consultant within the CSIRT team at NVISO with a focus on digital forensics including mobile device forensics. He is also involved in various projects related to Threat Hunting, Detection Engineering and Threat Intelligence. Occasionally, Renaud likes to participate in DFIR CTFs and Netwars.
如有侵权请联系:admin#unsafe.sh