2023-1-6 22:0:57 Author: www.sentinelone.com(查看原文) 阅读量:23 收藏
The Good
It’s been a busy start to the new year for privacy regulators, who have hit both Meta (aka Facebook) and Apple with new fines.
Apple has been given an $8 million penalty by France’s CNIL for failing to obtain consent from iOS 14.6 users relating to identifiers used to present targeted ads. Meta, which had just received a fine of $170 million from the CNIL a few weeks ago, now faces a further whopping $410 million (€390 million) fine from Ireland’s Data Protection Commission (DPC).

The DPC fined Meta Ireland €210 million for breaches of the GDPR relating to its Facebook service and €180 million for breaches in relation to Instagram. Both relate to complaints that users were forced to consent to personalized ads in order to use the offered services.
In better news for Meta and users of the company’s WhatsApp instant messaging service, this week saw WhatsApp roll out support for proxy servers. This allows users to connect to each other and maintain end-to-end encrypted chats even if authorities block WhatsApp’s own servers, as Iranian authorities did back in September in the wake of civil unrest.
The Bad
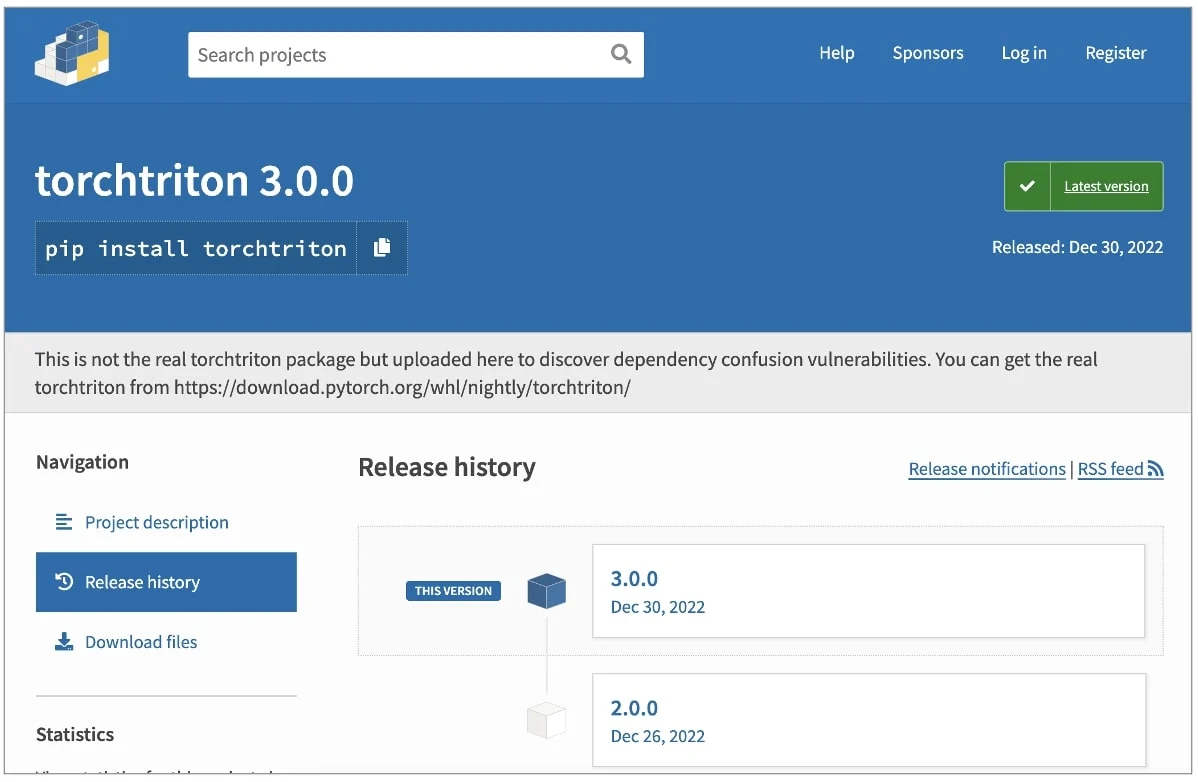
No sooner had we noted that supply chain attacks via public code repositories were likely to be an increasingly common feature of the 2023 threat landscape than a threat actor ran a dependency confusion attack against the PyTorch package on PyPI.
Dependency confusion attacks are different from the more common typosquatting attacks that we’ve seen used against shared repos recently like CrateDepression and pymafka. The technique takes advantage of the fact that some packages have dependencies that are hosted on private servers. However, by default, package managers that handle a client’s request for dependencies search the public code registry first for instances of the dependency. That means if the dependency package’s name is available on the public registry, an attacker can upload a malicious package to the registry and essentially intercept the dependency request from the client when users build it on their local machines.
An individual, who subsequently claimed to be a ‘researcher’, uploaded a malicious public version of the privately-hosted torchtriton package used by PyTorch. Users that built PyTorch between December 25th and December 30th received the fake torchtriton dependency. The malware was almost identical to the legitimate torchtriton save for the addition of a malicious binary at ./triton/runtime/triton and code to ensure that it was executed. The triton executable collects and exfiltrates a variety of sensitive data from the victim’s machine to a remote URL including:
- Nameservers from
/etc/resolv.conf - Hostname from
gethostname() - Current username
- Current working directory
- Environment variables
/etc/hosts/etc/passwd- First 1,000 files in
$HOME $HOME/.gitconfig$HOME/.ssh/
The malicious package has since been removed and replaced with a stub to prevent further attempts at exploiting the same trick. However, dependency confusion attacks are possible wherever private packages do not claim the same namespace in the public repository. Aside from PyPI, packages hosted on NPM and YARL are also known to be vulnerable to dependency confusion attacks.
It’s estimated that there were around 2300 malicious downloads during the time the malware was hosted on PyPI and PyTorch users are urged to uninstall and download the latest version if they think they might be affected. It is also recommended that credentials or keys stored in any of the locations noted above be rotated or reset.
The Ugly
In a different kind of dependency attack, DLL sideloading reared its ugly head again this week with news that threat actors are abusing Microsoft’s Windows Problem Reporting tool, WerFault.exe, to deploy Pupy RAT.
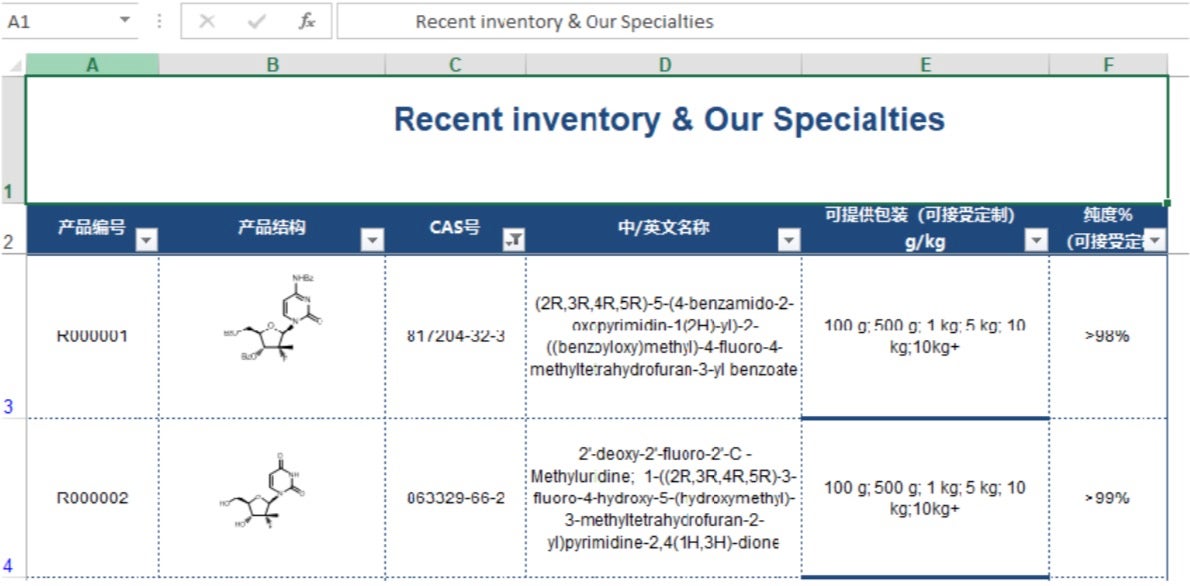
Victims receive an email with a malicious attachment. When double-clicked, the attachment mounts an ISO file containing a legitimate copy of WerFault.exe and a malicious version of a dependency, faultrep.dll. When users click the shortcut LNK file “recent inventory& our specialties.lnk” located in the mounted drive, it launches WerFault.exe, which in turn looks for and loads the DLL dependency located in the same directory.
The doctored DLL presents the user with a decoy XLS spreadsheet while in the background it loads an encrypted Pupy RAT payload into memory.
Pupy is an open-source, cross-platform attack framework with payloads that work on Windows, Linux, Android and macOS. Its capabilities include the ability to open a backdoor, execute arbitrary code and execute further payloads.
It is not immediately clear who is behind the campaign, but based on the XLS lure targets appear to be Chinese-speaking users. Sideloading DLLs via legitimate Microsoft software continues to be an issue defenders need to take seriously: Last year, Microsoft security tool Windows Defender was found being used to sideload Cobalt Strike during LockBit ransomware incidents.
如有侵权请联系:admin#unsafe.sh