The updated iOS Forensic Toolkit 8.11 brings keychain decryption support to devices running iOS/iPadOS versions up to and including the 15.5 by using the extraction agent. The tool supports recent models that can run iOS 15 , which includes devices based on the Apple A12 through A15 Bionic, as well as Apple Silicon based devices built on the M1 SoC.
What’s it all about?
The ultimate goal of a forensic expert is extracting as much data from the device as possible, and the keychain is a true gold mine. While advanced logical extraction is the simplest to use and the most compatible method that supports all devices and all versions of iOS, a low-level approach yields a much better return. In particular, low-level extraction provides access to encryption keys stored in the keychain. These encryption keys can be used to access encrypted chat histories saved by secure instant messaging apps such as Signal, Wickr, Threema, and SnapChat. Naturally, the keychain contains information required to decrypt encrypted Notes saved by the native Apple app.
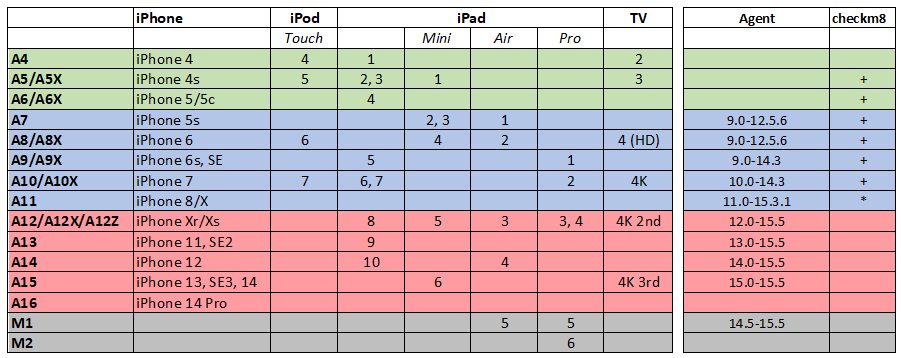
This time around we are targeting the newer generation of Apple devices that are built with the Apple A12 through A15 Bionic and Apple Silicone (M1) SoC. For older devices such as the iPhone 8/X, we still only support the file system and keychain extraction for iOS 15.3.1 and below, but this is not necessarily bad news as the entire iPhone 8/X generation running all versions of iOS 15.x is covered by checkm8 extraction.
For those newer devices we employ a custom developed extraction agent. The extraction agent is a small app that uses kernel-level exploits to escalate privileges, escape the sandbox and access the content of the device in the low level. It may sound simple, but in fact it is not: a kernel exploit alone is not enough to gain access to the file system, let alone decrypt the keychain. The new build of iOS Forensic Toolkit bumps iOS version support to allow keychain decryption for the all versions of iOS for which the file system extraction is supported, which is currently up to and including iOS 15.5.
What’s inside?
The keychain contains the most essential evidence, which includes passwords to web sites, Wi-Fi access points and mail accounts, passwords to cloud services/accounts, credit card numbers and a lot of encryption keys such as those protecting encrypted conversations in secure instant messaging apps.
Our agent-based extraction method is truly unique. We invented the approach for iOS devices, and we support the widest range of Apple devices and OS versions, including M1-based models. Our agent-based extraction solution is the only one on the market that capable to decrypt the keychain from OS versions up to and including iOS 15.5. For the full list of compatible device models and system versions please refer to the following chart:
REFERENCES:
![]()
Elcomsoft iOS Forensic Toolkit
Extract critical evidence from Apple iOS devices in real time. Gain access to phone secrets including passwords and encryption keys, and decrypt the file system image with or without the original passcode. Physical and logical acquisition options for all 64-bit devices running all versions of iOS.
Elcomsoft iOS Forensic Toolkit official web page & downloads »
如有侵权请联系:admin#unsafe.sh