2023-1-18 16:0:45 Author: securelist.com(查看原文) 阅读量:18 收藏
Kaspersky detects an average of 400,000 malicious files every day. These add up to 144 million annually. The threat landscape is constantly updated through new malware and spyware, advanced phishing methods, and new social engineering techniques. The media routinely report incidents and leaks of data that end up publicly accessible on the dark web. Hacker attacks constantly hurt individuals, corporations, and entire countries, and not just financially. In certain cases, cyberattacks may threaten human lives, for example if they target critical infrastructure.
Last year, the cybersecurity of corporations and government agencies was more significant than ever before, and will become even more so in 2023. As part of the Kaspersky Security Bulletin, the DFI (Digital Footprint Intelligence) and DFIR (Digital Forensics and Incident Response) teams have come up with an overview of threats that will be relevant to the segment in question.
More personal data leaks; corporate email at risk
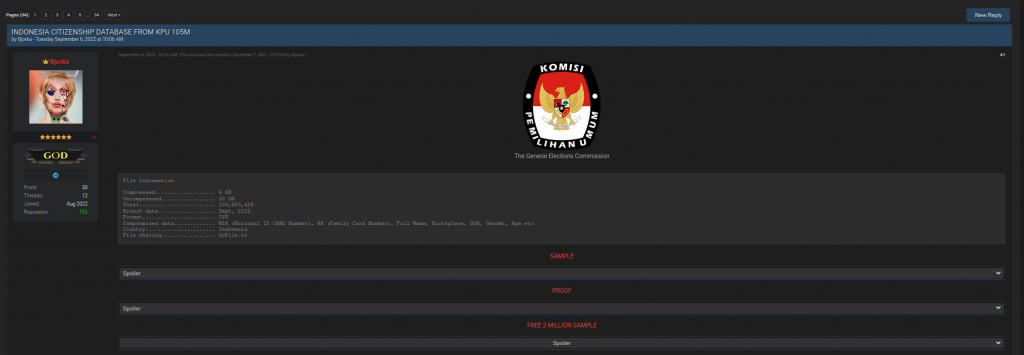
The trend for personal data leaks grew rapidly in 2022 and will continue into 2023. Last year saw, a number of high-profile cases, such as Medibank, Uber, and WhatsApp. The leaks affected various organizations and amounts of data. For example, last September, an attacker offered for sale a database containing 105 million records with information about Indonesian citizens. The compromised data included full name, place and date of birth, gender, as well as national identification number. The perpetrator valued the data, seemingly taken from the General Elections Commission of Indonesia, at US$5,000 and put it up for sale on the dark web.
A post on the dark web that offers Indonesian data for sale and was found with the help of Digital Footprint Intelligence
We often see people use work email addresses to register with third-party sites and services, which can be hacked and exposed to a data leak, putting the security of the company that owns the email at risk. The attack surface in its infrastructure increases with the number of potentially vulnerable objects. When sensitive data becomes publicly accessible, it may invoke the interest of cybercriminals and trigger discussions of potential attacks on the organization on dark web sites (forums, instant messaging channels, onion resources, etc.). In addition, the likelihood of the data being used for phishing and social engineering increases.
Media blackmail: businesses to learn they were hacked from hackers’ public posts with a countdown to publication
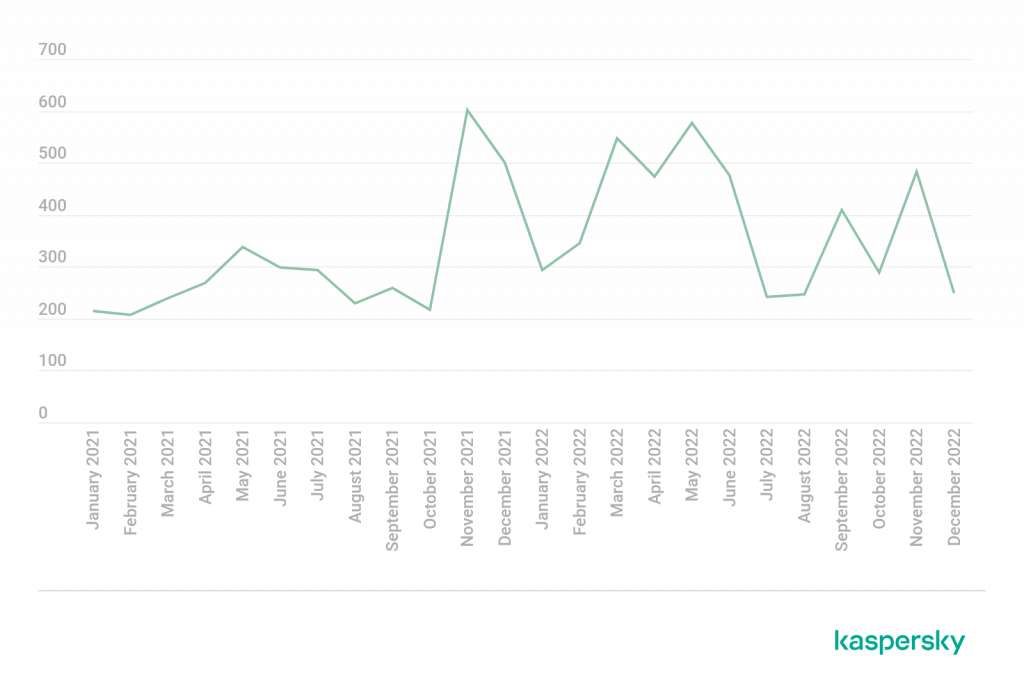
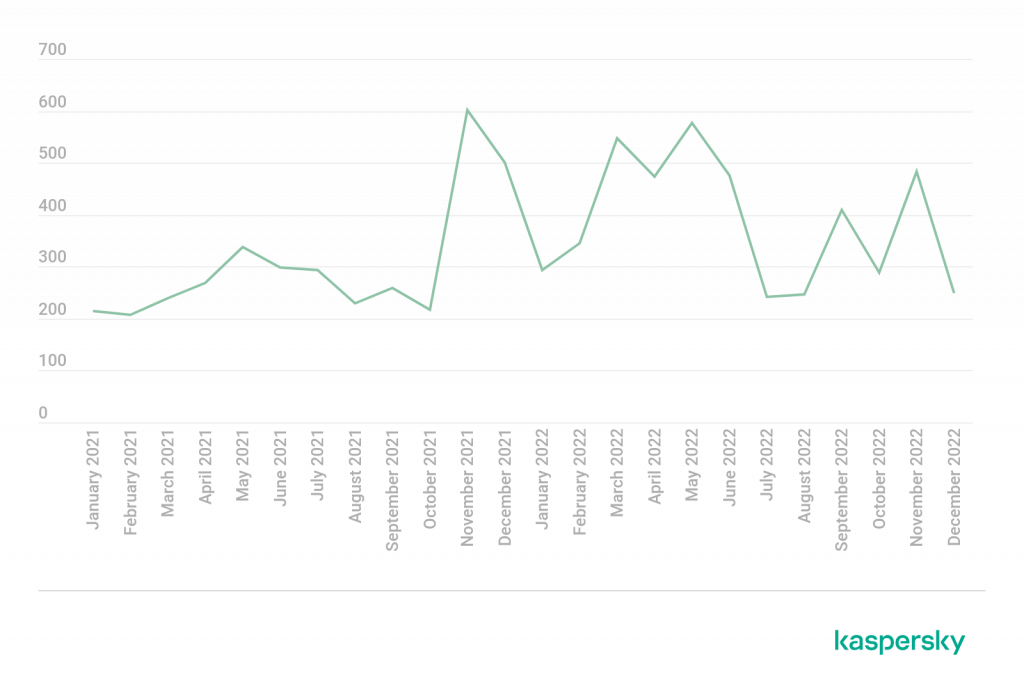
Ransomware operators set up blogs where they post about new successful hacks of businesses and publish the data they stole. The number of posts in those blogs grew in 2022, both in open sources and on the dark web. Whereas we were seeing 200 to 300 posts in each of the first ten months of 2021, the number peaked at more than 500 monthly at the end of 2021 and the first half of 2022[1].
Changes in the number of ransomware blog posts in 2021–2022, worldwide
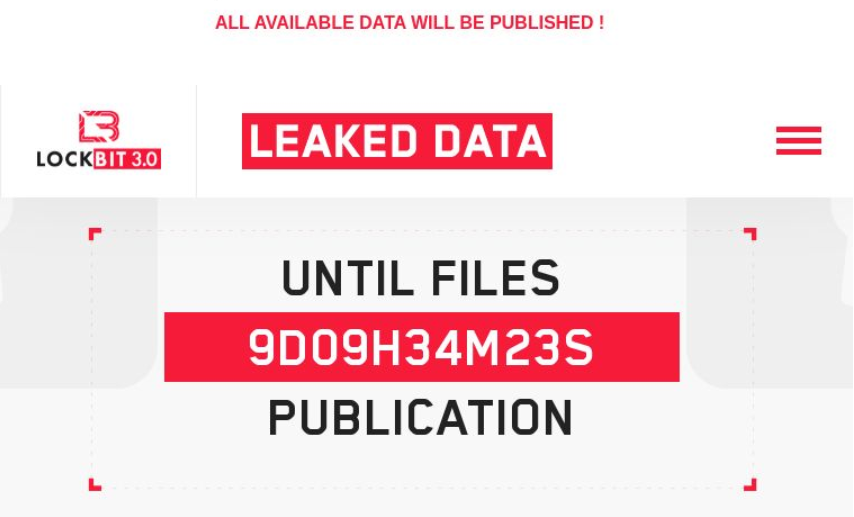
Extortionists used to try to settle matters with victim businesses in private, without attracting the attention of the broader public. Cybercriminals used to strive to keep a low profile until they got what they wanted, while the hack victims preferred to avoid reputational damage or any other consequences of the attack. These days, hackers post about the security breach in their blogs instead of contacting the victim, set a countdown timer to the publication of the leaked data, and wait for the victim’s reaction. This pattern helps cybercriminals win regardless of whether the victim pays up or not. Data is often auctioned, with the closing bid sometimes exceeding the demanded ransom.
Example: a post about the hack of the Australian company Medibank, found with the help of Digital Footprint Intelligence
We expect that in 2023, cybercriminals will try to reach out to victim businesses ever less often, while the number of blog posts and mentions of victims’ names in the news will increase.
Example of a countdown to the publication of leaked data as seen in the LockBit ransomware blog
Enjoying the fun part: cybercriminals to post fake hack reports more often
These days, hardly a day goes by without a new leak being reported. The number of fake reports grows along with that. We believe that in 2023, cybercriminals will more frequently allege, that they have hacked a company, as an ego trip and a rep boost. A leak report that appears in public sources can be used as a media manipulation tool and hurt the target business regardless of whether the hack happened or not. It is key to identify these messages in a timely manner and initiate a response process similar to that for information security incidents. This includes monitoring of dark and deep web sites for leak or compromise reports.
Cloud technology and compromised data sourced on the dark web to become popular attack vectors
The major attack vectors, such as vulnerabilities in publicly used applications, compromised credentials, and emailed malicious links and attachments, will be joined by activities and tools relating to cloud and virtualization technology. Businesses increasingly transfer their information infrastructures to the cloud, often using partner services for that. They place little focus on information security when migrating to the cloud: this is not even a task they assign to the virtualization service provider. An incident catches the company with insufficient data for investigation, as the cloud provider neither gathers nor logs system events. This essentially makes investigating the incident a difficult task.
Cybercriminals will tap dark web sites more often in 2023 to purchase access to previously compromised organizations. Our investigations have revealed a clear trend: the number of attacks utilizing pre-compromised accounts posted on dark web sites is on the rise. What is dangerous about that trend is that the preliminary phase of the attack, that is the account being compromised, can go unnoticed. The victim company will not learn about the attack until it is faced with major damage, such as their services suffering interruptions or ransomware encrypting their data.
Digitalization brings increased cybersecurity risks with it. If a corporation is to secure the loyalty of its customers and partners, it must ensure business continuity and robust protection of its critical assets, corporate data and the entire IT infrastructure to counter growing threats. Large businesses and government organizations often employ multilevel security, but even that is not a guarantee against compromise. Therefore, timely, adequate incident response and investigation are essential to both remedying the consequences and fixing the root cause, as well as to preventing similar incidents from happening again.
The malware-as-a-service model will continue to gain popularity in 2023, with blackmailer teams among others. Cybercriminals try to optimize their work efforts by scaling their operations and outsourcing certain activities just as a legitimate business would. For instance, LockBit — you can read about its evolution here — has been expanding its services like a software development company. The cybercriminals recently went so far as to announce a bug bounty program. Malware-as-a-service (MaaS) is lowering the entry threshold for wannabe cybercriminals: anyone can launch a ransomware attack by renting a fitting malware tool.
Meanwhile, the number of popular and well-known ransomware tools will decline, and attacks will grow in similarity. Companies might view this as a positive: a great number of ransomware tools will utilize similar MaaS techniques and tactics, so a smaller number of these will need to be considered for SOC response. That said, attackers’ tools will grow in complexity, rendering automated systems insufficient as a means of complete security.
The year 2023 will be a complicated one from an information security perspective, because the threat landscape is evolving rapidly. This sets a pace for businesses, which are forced to adapt. On the brighter side, researchers have the advanced tools to curb the growing threats.
These were our predictions for the year 2023. A year from now, we shall see which ones materialized and which ones did not.
[1] The statistics contain data on sites that are covered by the Digital Footprint Intelligence monitoring system
如有侵权请联系:admin#unsafe.sh