SPIP version 4.0.1 was released on Wednesday, December 15 2021, in order to patch a vulnerability in the CMS' SQL engine, which was present up until version 4.0.0. The vulnerability allows any unauthenticated user to get read access to the database, connect as an administrator, and then execute arbitrary code on the server.
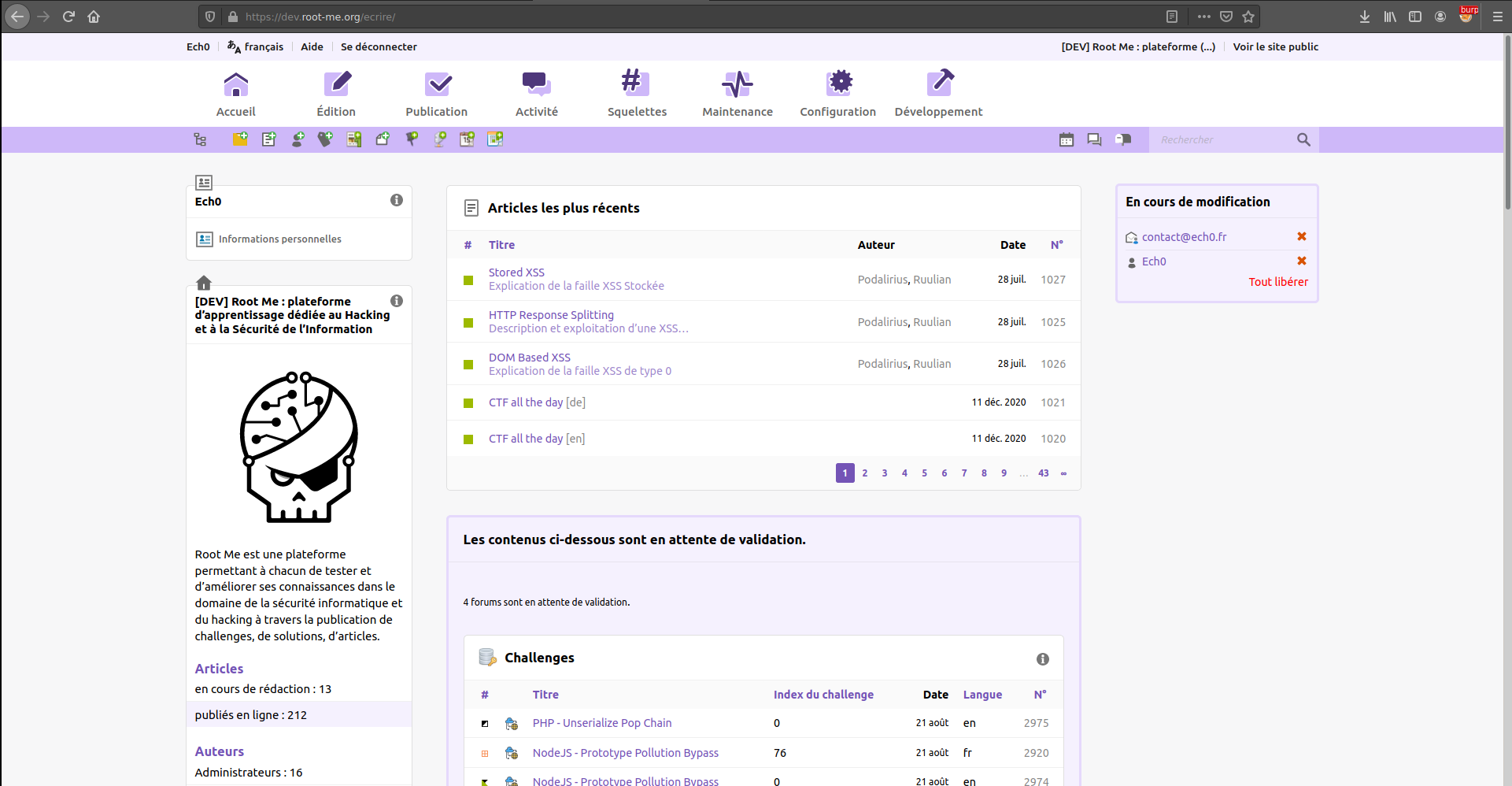
Although not the most used CMS, SPIP has a solid userbase, which includes the hacking challenge website Root-Me. With the agreement of its creator, g0uZ, we hacked into one of the administrator's account and got complete access to the back-office of Root-Me !
Now, you are probably expecting a write-up of the vulnerability. We have something much better.
We created a new challenge on Root-Me that contains a very simple SPIP website, with version 4.0.0. Find the vulnerability, get an SQL injection, and execute code on the server to get the flag !
However, hurry ! In a few months, we will disclose the vulnerability details, and all the fun of finding it will be gone.
The challenge is here: Root-Me, for real.
A million thanks to g0uZ for letting us hack into the website, and build a challenge out of it.
Solved the challenge ? Interested in offensive security ? Contact us !
Ambionics is an entity of Lexfo, and we're hiring! To learn more about job opportunities, do not hesitate to contact us at [email protected]. We're a french-speaking company, so we expect candidates to be fluent in our beautiful language.