The program will aim to help partners deliver stellar services and customer experiences.
2023-2-6 19:23:43 Author: perception-point.io(查看原文) 阅读量:28 收藏
In this blog we cover a new underground Clipper malware that allows attacks to replace a victim’s crypto wallet with their own.
Clipper malware is a type of malware that specifically targets cryptocurrency wallets. It replaces wallet addresses with the attacker’s own address, effectively diverting funds to the attacker. The danger of Clipper malware lies in its ability to intercept and manipulate sensitive information, such as wallet addresses, through various hooking techniques.
In this blog we review Paradies Clipper malware, which is uncommon in the wild due to its developer’s low popularity, but still interesting from a cyber research perspective.
Threat Intel
Let’s start from the beginning, at the source of the malware: a sales thread in the nulled.to forum. There, anyone can access the Clipper panel site, register, and buy a subscription.
Figure 1: The Clipper panel site
Static Info
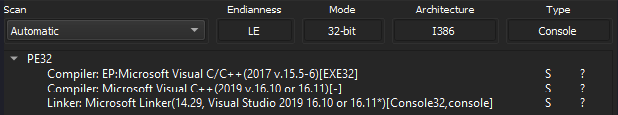
To determine the basics about this malware, we opened a sample in DiE, a malware analysis tool. From there, we could see that the sample was written in C/C++ and that it is a PE32 file.
Figure 2: Malware written in C/C++ as a PE32 file
Looking at the strings of the sample, we noticed that the developer hasn’t invested time in obfuscating the strings. This enabled us to find what could be the C2 (and the compilation path on the developer’s computer):
Figure 3: Possible C2 and compilation path
We could also understand a lot by looking at the imports, no dynamic API resolution necessary:
Figure 4: The imports
Analysis
Opening up the malware binary in IDA, a disassembler tool, we found a long main function. The function first checks for a mutex handle with the value: 7CmLQX. If it exists, the program will understand that it is already executed and will terminate itself.
Figure 5: Mutex handle function
Persistence
The program then retrieves the path to the user’s AppDataLocal folder and combines it with the persistence executable name: Update.exe.
From there, the program compares the persistence path to the current path of the executable (it retrieves the path using GetModuleFileNameA). If the executable is not running from the persistence path (C:\Users\user\AppData\Local\Update.exe), it will skip the main functionality code and create persistence:
Figure 6: Creating persistence
Figure 6: Creating persistence
The program creates a registry key with the name Update under the path HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run with the value pointing to the persistence path.
Figures 7 & 8: Creating a registry path
Figures 7 & 8: Creating a registry path
Next, the binary concatenates a CMD command and executes it. The command copies the executable to the desired persistence path, deletes the executable, and executes it again from the persistent path.
Figure 9: Linking and executing the executable
The final concatenated command is as follows:
start cmd /Q /C " ping localhost -n 1 && copy
"C:\Users\igal\Desktop\Paradies2.bin"
"C:\Users\igal\AppData\Local\Update.exe" && attrib +r +h +a
"C:\Users\igal\AppData\Local\Update.exe" && icacls
"C:\Users\igal\AppData\Local\Update.exe" /deny "everyone":(WD,AD,WEA,WA) && del
"C:\Users\igal\Desktop\Paradies2.bin" && cmd /C "start
"C:\Users\igal\AppData\Local\Update.exe" && exit" && && exit "
This command uses the attrib command with several flags:
- +r – sets the file as read-only.
- +h – sets the file as hidden.
- +a – flags the file as available for archiving when using the BACKUP or XCOPY commands.
The command uses the icacls command with several flags:
- /deny “everyone” – denies specified user access rights.
- WD – write data/add file.
- AD – append data/add subdirectory.
- WEA – write extended attributes.
- WA – write attributes.
Figures 10 & 11: Command features
Once the persistence is made and the binary restarts we can dive into the Clipper functionality.
Main Functionality
The program starts off by creating the Mutex that the program initially tried to retrieve. The program then sleeps for a minute.
Figure 12: The program creates the Mutex and then sleeps
Before the Clipper begins the clipping function it creates the first connection to the Paradies server.
The first POST request that the Clipper makes contains the following fields:
- username – the computer username (by using the GetUserNameA).
- ip – the computer IP.
- country – the country associated with the computer IP.
- city – the city associated with the computer IP.
- date – the initial infection date (followed up with the format DD-MM-YYYY).
- time – the initial infection time.
- last date & last time – the last active ping received from the infected computer.
- mwv – Clipper version.
- assigned – the associated ID of the builder in the web panel.
- worker – affiliate ID.
Figures 13 & 14: The first POST request
In order to find the IP and the associated country/city, the program sends out three GET requests:
- https://myexternalip.com/raw with the user agent: hitman
- https://ipapi.co/{IP}/country with the user agent: hitman69
- https://ipapi.co/{IP}/city with the user agent: hitman1337
The first request to myexternalip.com retrieves the IP of the computer. The second and third requests to ipapi.co retrieve the country/city of the given IP.
Figure 15: Requests to ipapi.co
The program then constantly sends out pings to the web panel, letting the attacker know that the program is still alive. The POST request simply contains the following fields:
- lastdate
- lasttime
- IP
Figure 16: The second POST request
The program then uses the next API calls to operate the clipboarding functionality:
- OpenClipboard
- GetClipboardData
- CloseClipboard
- EmptyClipboard
- SetClipboardData
Once the program retrieves the data from the clipboard (using GetClipboardData) it tries to compare the data to crypto wallet regex patterns and, if the regex matches, the program replaces the wallet in the clipboard with the attacker’s wallet (using SetClipboardData).
Figure 17: Replacing the clipboard wallet
After the clipboard is switched, the program sends a POST request to the Paradies server, informing the attacker that the clipboard was changed. This includes the replaced wallet and to which wallet it was replaced. This request includes the below fields:
- ip
- previous
- replaced
- mwv
- date
- time
- Assigned
Figure 18: Request to Paradies server
Summary
Paradies Clipper is a simple C++ malware with a dedicated mission. It aims to stay alive on the victim’s computer and monitor the clipboard data, in order to carry out the simple task of making money at the expense of the victim.
For more information about how to prevent malware, check out this blog.
IOCs
Sha256:
Paradies Clipper – 4df448d36e3409ecd712702ef66dba779d81961ae364243ccc0e2e5a6cb39334
Crypto wallets:
- Bitcoin – bc1qxudtrupckfmc204z70x8p9xu7409nsrgvekm0h
- Bitcoin – 1C7HpJnRNaUNY8F7inQXyxmJ9aQsczZAML
- Litecoin – ltc1q259z50fwemrpjvjmkn5rl2m4h8jckm32rlhvem
- Etherium – 0x301e8c4Dffaeb682b67bdfB5d340F36EFE2Cf877
- Dogecoin – DE4hgzmrtaXVhTWRuzLpnyhbgRGikjBVvg
- Ripple – rfvgDUeRUaDfGwPxnSj9aed4nroJgQcyDQ
- Dash – Xh1ff4HdtbUtC2DW8vk3Dhwa5VSJ2pxSMG
- Neo – LQ4Gwqr38zBR5JdyoxcUDu38r63T5mUi4Y
- Monero – 41oqjME2WP2C88P3BW4oEgUGjMaXQwGqgirYJWCDYwAQahMXWKYNLF4XVodVkNQnF
Yara rule
import "pe"
rule win_paradies
{
meta:
author = "igal lytzki"
malware_family = "Paradies Clipper"
date = "18/01/2023"
version = "1.0"
sha256 = "4df448d36e3409ecd712702ef66dba779d81961ae364243ccc0e2e5a6cb39334"
strings:
$cryptoWallet1 = /(bc1)[a-zA-HJ-NP-Z0-9]{25,39}/
$cryptoWallet2 = /0x[a-fA-F0-9]{40}/
$cryptoWallet3 = /r[0-9a-zA-Z]{24,34}/
$cryptoWallet4 = /D{1}[5-9A-HJ-NP-U]{1}[1-9A-HJ-NP-Za-km-z]{32}/
$cryptoWallet5 = /[L][a-km-zA-HJ-NP-Z1-9]{26,33}/
$cryptoWallet6 = /ltc1[a-z0-9]{39,59}/
$cryptoWallet7 = /4[0-9AB][1-9A-HJ-NP-Za-km-z]{93}/
$cryptoWallet8 = /X[1-9A-HJ-NP-Za-km-z]{33}/
$userAgent = "hitman" ascii wide
condition:
uint16(0) == 0x5a4d
and 3 of ($cryptoWallet*)
and #userAgent > 2
and pe.imports("User32.dll" ,"GetClipboardData")
and pe.imports("User32.dll" ,"SetClipboardData")
}
Ready to Try
Perception Point?
Costs are rising across most companies today. A new study, however, is finding that the costs of protecting against cyber events are also soaring.
Combating cyberattacks has proven to be costly, with organizations shelling out $1,197 per employee annually to deal with email service-, cloud app- or service-, and web browser-related cyber incidents, excluding expenses related to compliance fines, mitigation costs, and business losses, VentureBeat reports.
Global businesses are paying thousands each year to meet the expanding threats against email, browsers, and emerging cloud-based channels in the enterprise
Perception Point announced the publication of a report, “The Rise of Cyber Threats Against Email, Browsers and Emerging Cloud-Based Channels“, which evaluates the responses of security and IT decision-makers at large enterprises and reveals numerous significant findings about today’s enterprise threat landscape.
Perception Point, a leading provider of advanced threat prevention across digital channels, announced the publication of a new report, ‘The Rise of Cyber Threats Against Email, Browsers and Emerging Cloud-Based Channels’.
如有侵权请联系:admin#unsafe.sh