You will learn the differences between WPA and WPA2 encryption, including why hardware updates were necessary for WPA2, and the differences in the final MPDU of both encryptions.

Hello world! I was always curious about the "exact" difference between WPA and WPA-2 while learning wireless security. It turns out that it is related to both the encryption algorithm and the process of generating encryption keys. Let's go over this in detail.
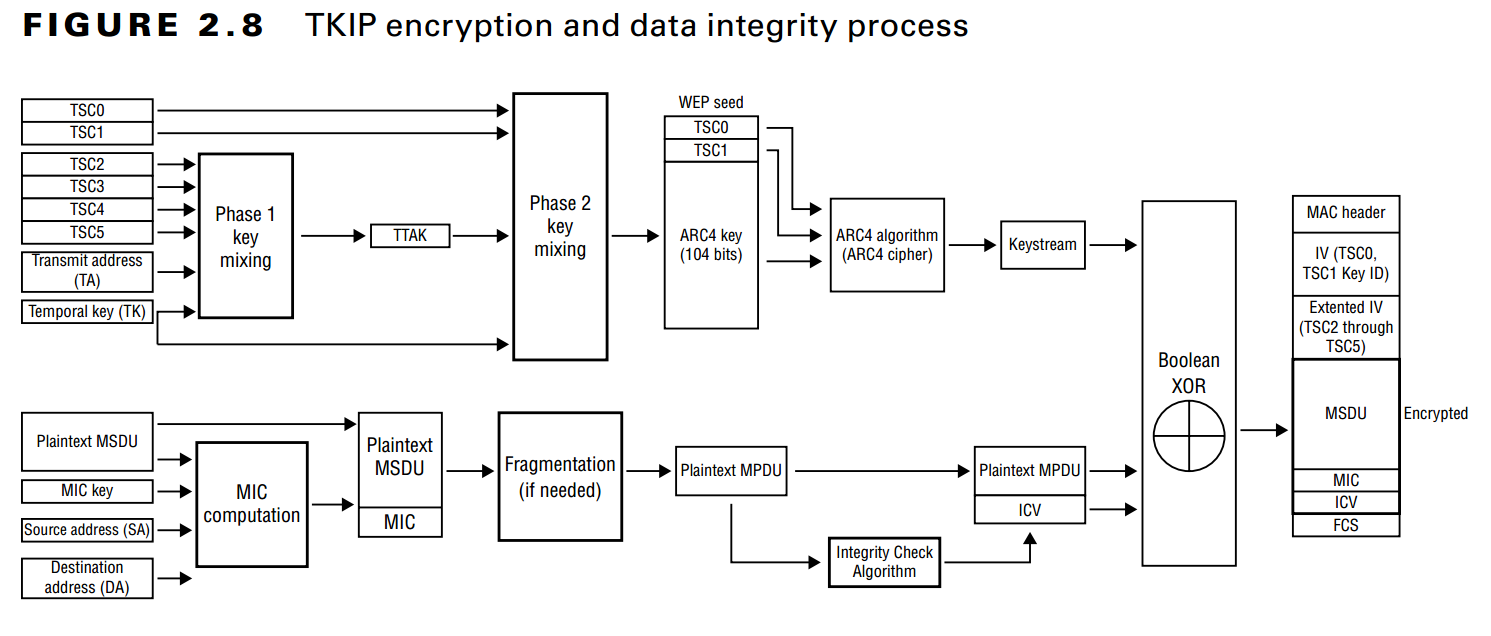
Temporal Key Integrity Protocol (TKIP or TKIP/RC4) was introduced in 2002 to upgrade the security of WEP-based hardware without any downtime, just by downloading and installing the firmware from the vendor's website the users can configure and use the WPA encryption. It keeps the basic architecture and operation of WEP but adds safeguards around the vulnerable points like generating dynamic keys to encrypt each packet instead of relying on the IV and static key. This is done by increasing the size of IV from 24 bit to 48 bits and a technique called key mixing.
Previously, the WEP secret key was static, and IV was random with limited key space; now, IV's key space has been increased (actually square), and the secret key is dynamic as well. As you can see, the transmitter address and sequence counter are used to calculate the secret key and the IV, which means that the same key used by two different devices will be different. This image is taken from Chapter 3 of CWSP Study Guide book.
Note: The MIC is pre-calculated and passed to fragmentation function which forwards it to the MPDU.
💡
The TKIP Sequence Counter (TSC) is utilized in the key stream generation process and serves to defend against replay attacks. The 48-bit sequence counter is divided into 6 parts (8 bits each) resulting in TSC0 \( \cdots \) TSC5. This fragmented TSC is then utilized in the second phase of key mixing to generate the WEP seed (encryption key).
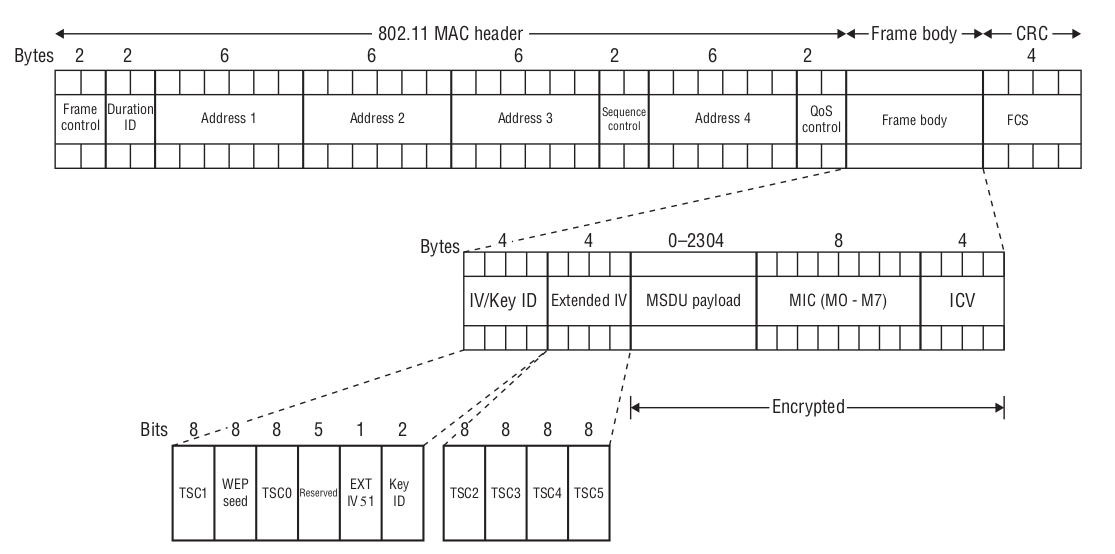
After the completion of all the operations, the MPDU will look like following image, taken from Chapter 3 of CWSP Study Guide.
TKIP is no longer supported as an encryption method for 802.11n or 802.11ac data standards. Here's an example of what I mean: this screenshot of hotspot configuration in my phone, and there is no WPA option to configure in hotspot security.
However, because the underlying encryption algorithm is RC4 we needed a stronger one to ensure that it cannot be easily exploited. Later in 2004, AES algorithm was introduced into the realm of WiFi, which required hardware changes but had a similar flow to WPA, so the task group called it WPA2. This encryption is commonly referred to as Counter Mode CBC-MAC Protocol (CCMP) and it also has RFC-3610 for this. CCMP combines CTR to provide data confidentiality and CBC‐MAC for authentication and integrity.
Again, this image is taken from the Chapter 3 of CWSP Study Guide.
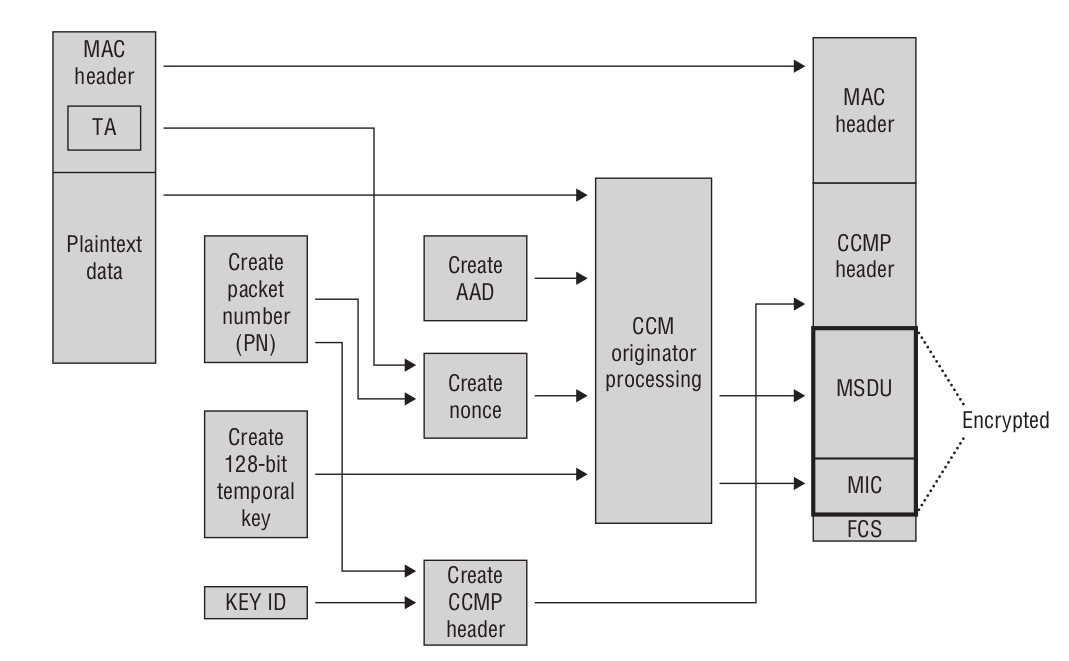
Note: The MIC is calculated along with encryption by the CCM function.
It is a block cipher, which means that the data is divided into specific blocks and then passed to the encryption or decryption functions rather than as a whole message. It uses a 128-bit key and a 128-bit block size, but some highly classified data should be encrypted with 192 or 256-bit keys.
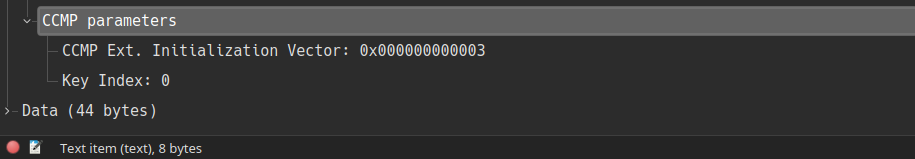
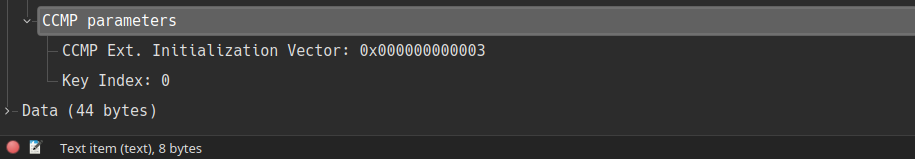
In the CCMP header, this 48-bit packet number (PN) is what wireshark decodes as CCMP Extended Initialisation Vector, which is of course incremented as the packets flow through the network. Also, because this counter is implemented locally, if the transmitter used counter \(X\), it does not follow that the receiver will use this and transmit the response with \(X+1\).
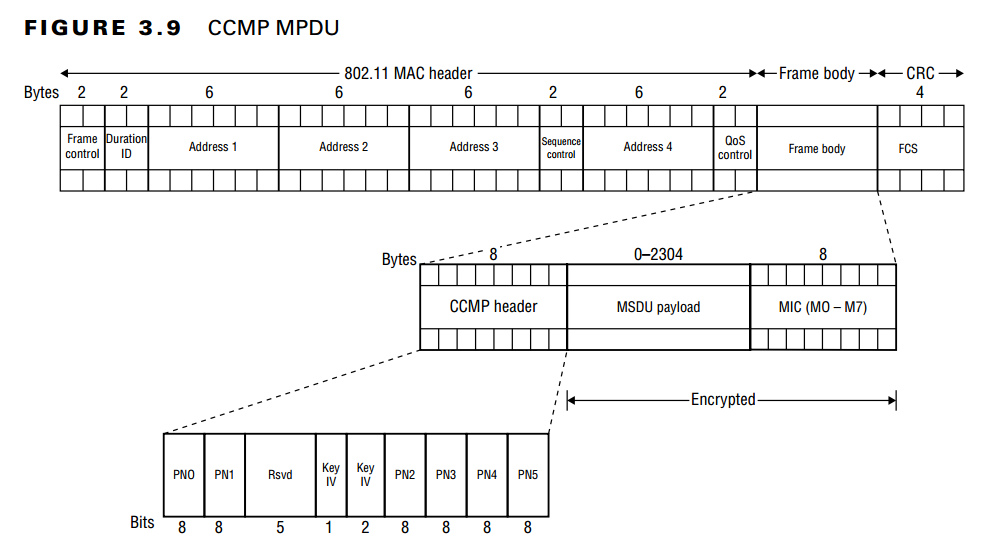
After completing encryption process, the final MPDU will look like the following image, taken from Chapter 3 of CWSP Study Guide.
The RSN I mentioned earlier is the protocol that defines how dynamic keys are generated and exchanged between two parties; it has nothing to do with the encryption used. This decision is left up to the communicating parties, who can select whichever option they prefer.
Since TKIP, a more robust checksum algorithm is employed into the protocol, we call it Message Integrity Code / Check (MIC). It is computed using destination and source address, key and the plain text MSDU payload. Although this process is more complex and may result in slower transmission speeds compared to WEP, it is considered a preferable option due to its stronger security measures.
💡
In order to prevent needless failures, receivers should check the FCS, ICV, and TSC of all MPDUs before verifying the MIC. Additionally, checking the TSC before the MIC makes DoS attacks more difficult.
Since the MIC checksum by itself is not the strongest, TKIP uses it in conjunction with the ICV checksum, as you may have noticed in the TKIP MPDU above. However, CCMP it is more secure than TKIP which makes it more computationally intensive, so the developers decided to go with MIC instead of adding adding additional overhead by computing the ICV.. For this reason, you will only find MIC in the CCMP MPDU above.
Finally, I'd like to say that WPA and WPA2 are not the best, but they are stronger than Pre-RSN. For instance, the Beck-Tews attack can insert forged frames, retrieve the MIC key from an encrypted short packet's plain text, and recover the short packet's encryption key. If you're curious, you can try tkiptun-ng.
- https://web.archive.org/web/20071022160131/http://www.hsc.fr/ressources/articles/hakin9_wifi/hakin9_wifi_EN.pdf
- https://www.researchgate.net/figure/Key-mixing-and-data-encryption-in-TKIP_fig1_2997996
- https://mrncciew.com/2014/09/13/cwsp-tkip-encryption-method/
- https://en.wikipedia.org/wiki/CCMP_(cryptography)
- https://www.geeksforgeeks.org/block-cipher-modes-of-operation/
- https://mrncciew.com/2014/08/19/cwsp-ccmp-encryption-method/
- https://security.stackexchange.com/questions/87523/how-is-tsc-tkip-sequence-counter-calculated-in-wpa
- https://www.rfc-editor.org/rfc/rfc3610
- https://documents.uow.edu.au/~jennie/WEB/WEB05/Michael.pdf
- http://etutorials.org/Networking/802.11+security.+wi-fi+protected+access+and+802.11i/Part+II+The+Design+of+Wi-Fi+Security/Chapter+11.+TKIP/Message+Integrity+Michael/
- https://www.aircrack-ng.org/doku.php?id=tkiptun-ng
- http://lnkiy.in/security-analysis-of-message-integrity-code (fallback https://documents.uow.edu.au/~jennie/WEB/WEB05/Michael.pdf)