Event viewer is a component of Microsoft Windows that displays information related to application, security, system and setup events. Even though that Event Viewer is used mainly for troubleshooting windows errors by administrators could be also used as a form a persistence during red team operations. Microsoft in order to assist administrators to retrieve direct information for a particular event ID over the web has embedded a functionality which is called Event Log Online Help.
The Event Log Online Help redirects the users to a Microsoft URL and is controlled from the following registry location.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Event ViewerThree registry keys could be modified if local administrator access has been achieved in order to execute arbitrary payloads once the Event Log Online Help is clicked by the user. These keys can be found below:
- MicrosoftRedirectionProgram
- MicrosoftRedirectionProgramCommandLineParameters
- MicrosoftRedirectionURL
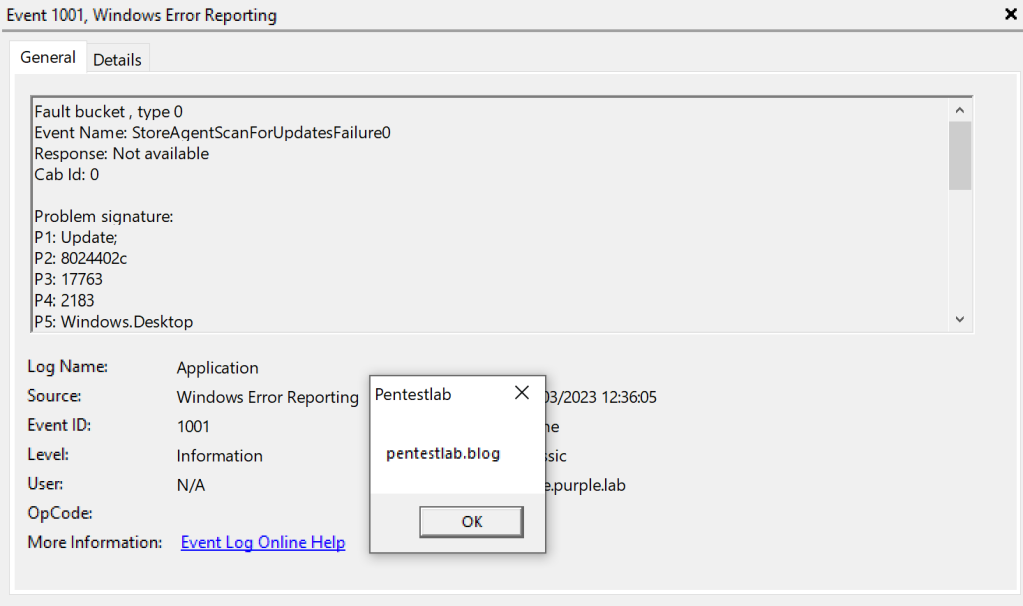
A very trivial proof of concept is to trigger a message box.
#include <windows.h>
#pragma comment (lib, "user32.lib")
int WINAPI WinMain(HINSTANCE hInstance, HINSTANCE hPrevInstance, LPSTR lpCmdLine, int nCmdShow) {
MessageBox(NULL, "pentestlab.blog", "Pentestlab", MB_OK);
return 0;
}
The code above could be compiled using MinGW in order to generate an executable.
x86_64-w64-mingw32-g++ -O2 messagebox.cpp -o messagebox.exe -I/usr/share/mingw-w64/include/ -s -ffunction-sections -fdata-sections -Wno-write-strings
-fno-exceptions -fmerge-all-constants -static-libstdc++ -static-libgcc -fpermissiveThe registry key “MicrosoftRedirectionProgram” could be modified to contain the location of the compiled executable. Clicking the Event Log Online Help will display the message box indicating that code has been executed.

In similar manner “msfvenom” could be used to generated a payload.

Modification of the registry key below to map to the location on the disk of the previously generated payload will execute the payload.

When the Event Log Online Help is clicked a connection will be established.

The second registry key “MicrosoftRedirectionProgramCommandLineParameters” allows the user modify the data value in order to execute commands. A very common living off the land binary such as “regsvr32” can be utilized to execute a fileless payload.

Once the Event Log Online Help is clicked the command will be executed and a communication channel will established.

The last registry key is the “MicrosoftRedirectionURL” which by default it points out to a Microsoft location. The registry value could be changed to point either to a malicious URL or to a payload which is dropped on the disk.

In all of the above scenarios the following condition will be created:
- Parent Process (mmc.exe) –> Child Process (Payload)

EDR’s should flag when mmc tries to spawn non trusted processes. Furthermore, monitoring of the above registry keys for changes could create a detection opportunity. As access to Windows graphical interface is required and considering the fact that the average user would not typically open event viewer and click on the Windows Event Log Online Help it is unlikely that this technique will gain popularity. However, in an assumed breach or malicious insider scenarios it could be used as a trivial method to maintain an active connection over a C2 channel.