Author: Knownsec 404 Team
中文版:https://paper.seebug.org/2053/
1.Abstract
In the process of network attack, C2 server, loader server and even the hackers' "working machine" may start the Web server for data transmission.
Based on the historical data of ZoomEye cyberspace search engine [1], we found that 6.53% of the 9,247 Cobalt Strike [2] control servers have provided directory browsing and file download services, involving malicious samples, exploitation scripts, scan results and other files. According to the existing data, we can find more hackers' "working machine" by high frequency mapping of important network segments.
In the process of research, we also found that there was a behavior of traversing and downloading all the files of hackers' "working machine", and concluded that there were already many "hunters" on the Internet by searching hackers' "working machine" to steal its attack tools and work results.
2.Overview
When hackers control other people's computers to steal files, they will also become the target of others' attacks. For example, a hacker might download a scanning tool that someone else has embedded with a malicious Trojan and then run it on a computer that is controlled by a "hunter" behind it.
In this article, we will start by searching the Web server that the hacker opens, by using the ZoomEye cyberspace search engine, become the "hunter" behind the hacker.
During the attack, hackers encounter various environments. To ensure the success of the attack, hackers use common methods to deliver malicious samples.For example, start the Web server, and then download it through the curl and wget commands that come with most systems. While the hacker is testing samples and sending back data, the data can also be transferred by starting a temporary Web server.
Some programming languages, such as Python, come with similar features. We can start an http server with a single command: python3 -m http.server and access it in a browser like this:
While this facilitates the transfer of data, it gives others the opportunity to take advantage. If others find the "working machine" used by the hacker, they can gain access to his attack tools, learn how he attacks, or even directly access the data he steals.
3.Using ZoomEye to Find Hackers' Working Machine
Let's explore how to use ZoomEye to find that hackers' "working machine".
In addition to the feature string in the title of the web page, we also need to specify the hackers "working machine" in the most frequent keyword features, in order to accurately find the hackers' "working machine" on the ZoomEye.
Here are some sample search statements:
Vulnerability EXP attack tools are often stored on the "working machine"
(title:"Index of /" title:"Directory List" title:"Directory listing for /") +"exp"
log4j exploit tools are often stored on the "working machine"
(title:"Index of /" title:"Directory List" title:"Directory listing for /") +"log4j"
CobaltStrike is frequently deployed on the "working machine"
(title:"Index of /" title:"Directory List" title:"Directory listing for /") +"cobaltstrike"
(title:"Index of /" title:"Directory List" title:"Directory listing for /") +"cobalt strike"
Metasploit is often deployed on the "working machine"
(title:"Index of /" title:"Directory List" title:"Directory listing for /") +"Metasploit"
Vulnerability exploitation tools containing the CVE number are often stored on the "working machine"
(title:"Index of /" title:"Directory List" title:"Directory listing for /") +"cve"
The payload is often stored on the "working machine"
(title:"Index of /" title:"Directory List" title:"Directory listing for /") +"payload"
calc.exe is often stored on the "working machine" for Trojan horse bundling tests
(title:"Index of /" title:"Directory List" title:"Directory listing for /") +"calc.exe"3.1 Example: A hacker uploads a scanning tool for malicious scanning
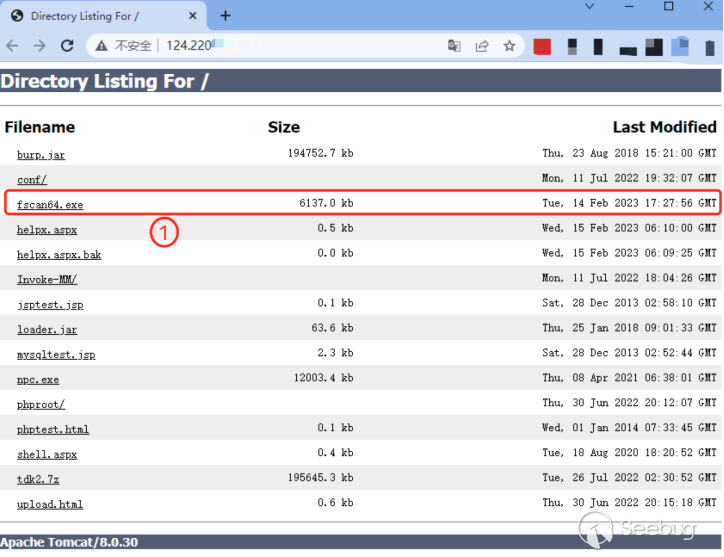
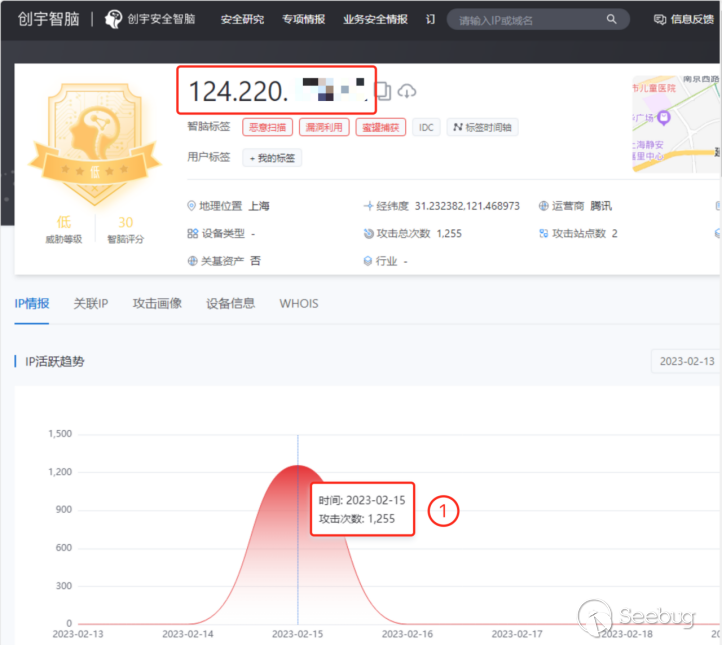
The server with IP address 124.200.*.* added a tool named fscan64.exe on February 14, 2023. On the following day (February 15, 2023),Knownsec Security Intelligence [3] captured 1255 attack requests initiated by this IP address and marked this IP address as a malicious IP address.
3.2 Example: Malicious files used by hackers for delivery are marked as malicious
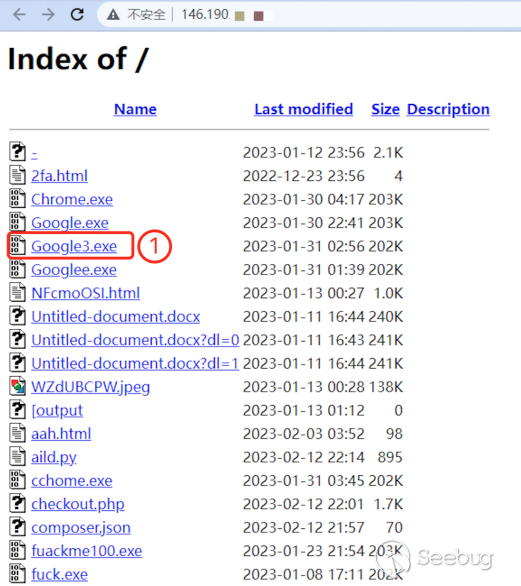
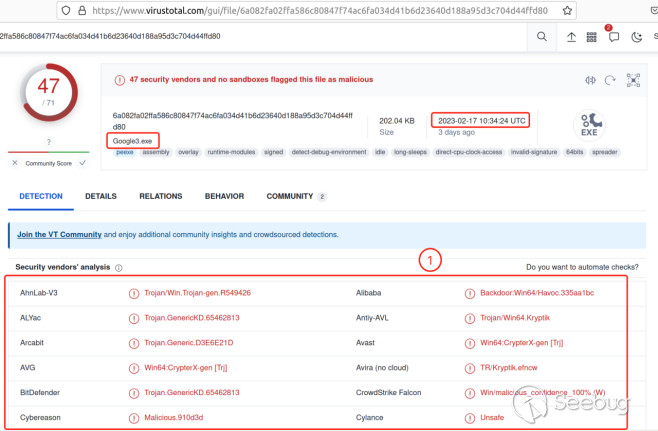
The hacker stored multiple decoy files on the "working machine" for the victim to click on. We randomly select a file "Google3.exe", which appears on the "working machine" on January 31, 2023; It was then uploaded to the Virustotal platform for verification, showing that the file had been identified as malicious on February 17, 2023.
3.3 Example: We can obtain attack tools used by hackers
On the hacker "working machine", we can obtain attack tools used by hackers, such as CVE vulnerability exploitation tool, Web Trojan tool, Payload code, and decoy file.
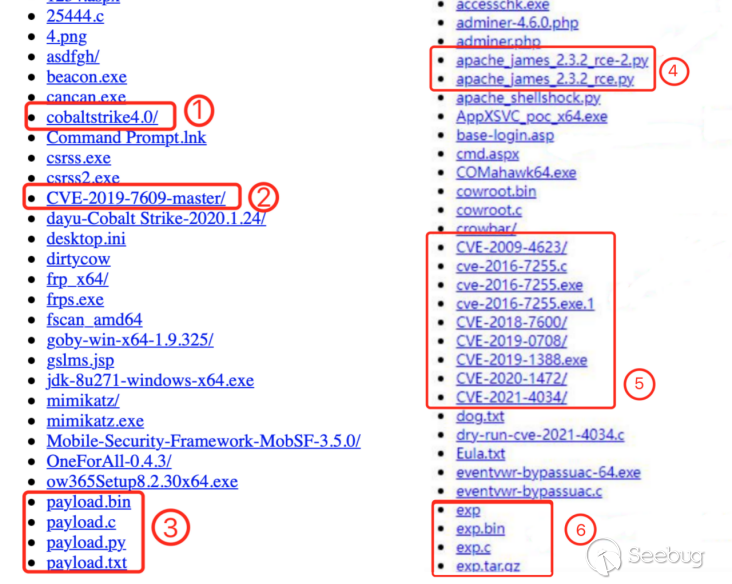
②CVE-2019-7609 Kibana remote code execution vulnerability exploitation tool
③Payload code
④Apache James Server 2.3.2 remote code execution vulnerability exploitation tools
⑤Multiple CVE vulnerability exploitation tools
⑥EXP tools
3.4 Example: We can get the results of the hacker's work
On the hacker's "working machine", we can obtain the hacker's work results, such as website scanning results, stolen victim Cookie data, stolen victim keyboard record data, stolen victim's computer files and so on.
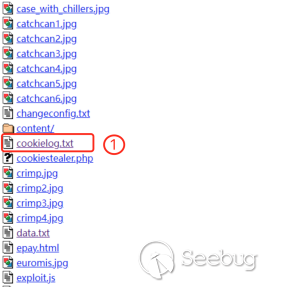
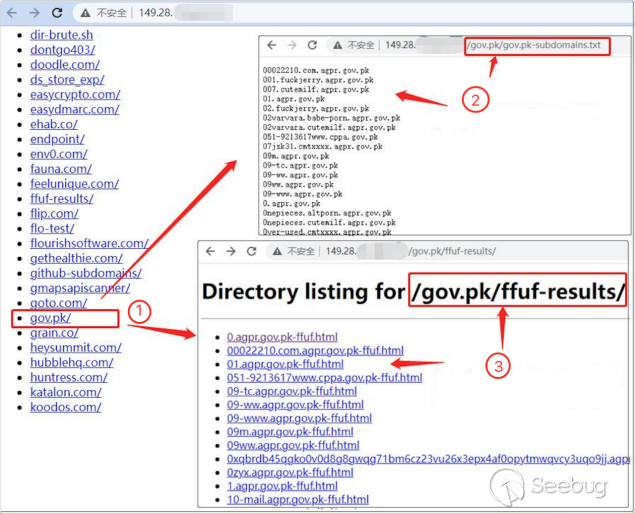
②The subdomain name extension result of gov.pk
③For each subdomain, the FFUF tool was used to conduct the results of Web Fuzz
4.Mapping important network segments
4.1 Web directory browsing open on Cobalt Strike controllers
A total of 9,247 IP addresses have been flagged as Cobalt Strike controllers between January 1, 2020 and February 16, 2023, according to ZoomEye Cyberspace search engine. Among them, 604 IP addresses have been used to provide directory browsing and file downloading services, accounting for 6.53%. According to the detected file names and other information, most of the files are related to hacking attacks.This shows that some hackers on the Internet have "working machines" that others can take advantage of.
4.2 High frequency mapping important network segments
From the IP addresses that have been identified as Cobalt Strike control terminals, we selected 30 B-segment IP addresses with the largest number of Cobalt Strike controller for a small scale test, and conducted high-frequency mapping for 72 hours on 3 ports (8000, 8080, 8888) of these 30 B-segment IP addresses. Check whether it provides directory browsing and file downloading services, and whether it is a hacker's "working machine".
The result is that within 72 hours, of the 1.96 million IP addresses in 30 B segments, we mapped 176 IP addresses that provided directory browsing and file downloading services, 13 of which were hackers' "working machines". We then analyzed the opening and closing time of the HTTP service. Among the 176 IP addresses, 70 were closed after the temporary opening of the HTTP service.
Therefore, we can infer that more hackers' "machines" can be found by high-frequency mapping of important network segments than by querying through a cyberspace search engine.
5.Searching for the "hunters" already on the Internet
In this way, as the "hunter" behind the hacker, he can directly obtain the attack tools and work results on the hacker's "working machine". We speculated that such hunters already exist on the Internet, and we tried to find them.
From the file listed by the HTTP service on port 8000 at IP address 83.136.*.*, we can tell that it is a hacker's "working machine". The file nohup.out is the request log file of the HTTP service.
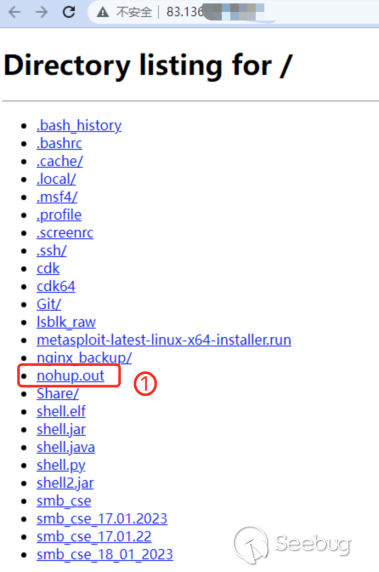
In this file, we find the behavior of IP address 34.140.*.* suspicious. This IP address, on January 30, 2023, traversed and downloaded files from all the folders on the hacker's "working machine." We queried the threat level of IP address 34.140.*.* by using Knownsec Security Intelligence, and found that the IP address had been labeled as a malicious IP address, labeled as "Malicious Scan". And malicious scanning attacks were indeed launched on January 30, 2023.
The IP address 34.140.*.* is not a search engine spider IP, so we infer that it is a "hunter IP". Of course, it could be targeting not just the hacker's "working machine," but any server with a directory browsing vulnerability.
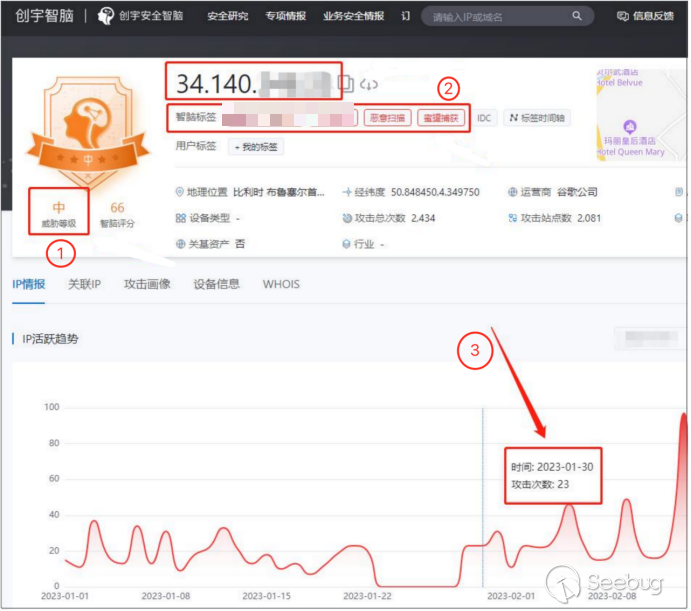
②The IP address has labels such as "Malicious Scan"
③This IP address launched 23 malicious scan attacks on January 30, 2023
In the file "nohup.out", there are three IP addresses with the same behavior as 34.140.*.*. We speculate that they all belong to "hunter IP". Through this example of a hacker "working machine", we have reason to infer that there are many "hunters" on the Internet by searching for hackers "working machines" to steal their attack tools and work results.
6.Conclusion
The hacker may act alone, but the disadvantage is that he has limited technical ability and practical experience, and cannot pay attention to all aspects of the details. It may also be teamwork, with a clear division of labor, and each person is responsible for writing tools, carrying out attacks, analyzing results, etc., but the disadvantage is that each person only pays attention to the work he is responsible for, and no one pays attention to the undefined work or risks. It is for these reasons that we can capture these hackers' "working machines" through ZoomEye cyberspace search engine.
A hacker who is good at attacking is not necessarily good at defending, and may appear as prey in front of a more powerful hunter. To be the hacker behind the attack, or to be the hunter behind the hacker, is an escalation of the confrontation between attack and defense, and is also the charm of mapping cyberspace from the perspective of God.
7.Reference
[1] ZoomEye cyberspace search engine
https://www.zoomeye.org/
[2] Cobalt Strike
https://www.cobaltstrike.com/
[3] Knownsec Security Intelligence
https://gac.yunaq.com/
 本文由 Seebug Paper 发布,如需转载请注明来源。本文地址:https://paper.seebug.org/2054/
本文由 Seebug Paper 发布,如需转载请注明来源。本文地址:https://paper.seebug.org/2054/
如有侵权请联系:admin#unsafe.sh