2023-3-10 22:0:22 Author: www.sentinelone.com(查看原文) 阅读量:16 收藏
The Good
Prolific ransomware gang, DoppelPaymer (aka Grief), took a major hit this week as a number of their core members were arrested in Germany and Ukraine. In a joint operation conducted by Europol, the FBI, and the Dutch police force, two individuals have been taken into custody following multiple raids in both countries. IT experts and investigators are currently examining all seized electronic devices for forensic evidence and crypto tracing. In their statement, Europol stated that data from the resulting analysis is expected to trigger investigations in related cases.

Russian-linked DoppelPaymer has cost enterprises millions over the years. Operating as a Ransomware-as-a-Service (RaaS), they often leverage Emotet and Drydex malware variants to launch high profile, double extortion attacks focused on healthcare, government, and education sectors. In 2020, the gang crashed the operational systems of a hospital in Düsseldorf, causing critical delays in emergency treatments. The resulting death of one patient is often referred to as the first possible case of indirect casualty due to cyberattack. Past victims of the gang include SpaceX, NASA, Kia Motors, Compal, and Foxconn.
The DoppelPaymer sting operation is ongoing and authorities have issued arrest warrants for three more principal members who are still at large. Three suspects, Igor Olegovich Turashev, Irina Zemlyanikina, and Igor Garshin, are all wanted on charges including extortion, computer sabotage, spying, data encryption, and the administration of DoppelPaymer’s IT infrastructure, internal chats, and leak sites.
This operation is the latest in a global effort to crackdown on prominent ransomware syndicates. While collaboration between international authorities make impactful progress on dismantling cybercriminal networks, police urge organizations to continue reporting attacks immediately and implementing proactive measures against ever-rising ransomware attacks.
The Bad
IceFire ransomware operators have launched a new dedicated encryptor to actively target Linux systems. Reported this week by SentinelLabs, the ransomware gang recently targeted several media and entertainment enterprises across the world, encrypting their systems with the novel malware variant.
In this recent string of breaches, IceFire was observed exploiting a deserialization vulnerability tracked as CVE-2022-47986 (CVSS score 9.8) within IBM’s Aspera Faspex product (4.42 Patch Level 1) to deploy ransomware payloads. IceFire operators leveraged this flaw to execute arbitrary code on the infected system by sending a specially crafted obsolete API call. Upon execution, the IceFire ransomware works by encrypting files and adding the iFire extension to the name before deleting itself and removing the binary to wipe its own tracks.
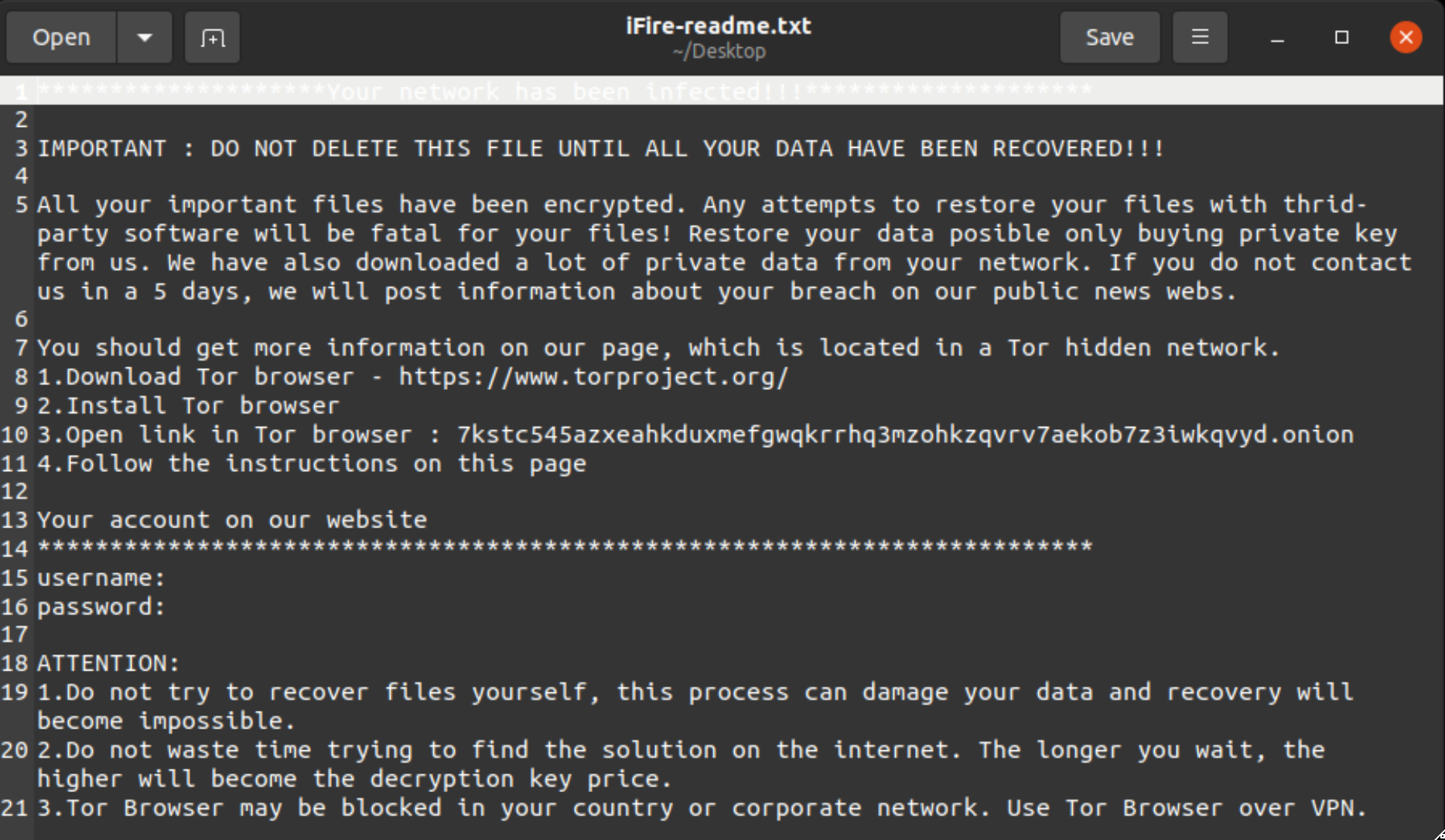
SentinelLabs researchers explained that, in comparison to Windows, attackers have more difficulty deploying ransomware within Linux servers, especially at scale. To overcome this, attackers are increasingly turning to exploiting vulnerabilities within applications. Shodan, at the time of this publication, currently shows 158 Aspera Faspex servers exposed online mostly in the United States and China.
The shift from targeting Windows to Linux systems is a strategic one that is gaining traction across the greater cyberthreat landscape. Ransomware groups such as Cl0p, Hive, LockBit, HelloKitty, BlackMatter, RansomEXX, and AvosLocker have also made this move, seemingly to match global enterprises who have transitioned to Linux-powered virtual machines in the past few years. Researchers at SentinelLabs note that the recent evolution for IceFire is a clear indication that this trend will continue to grow in popularity throughout the rest of 2023.
The Ugly
A security advisory published by Fortinet this week disclosed a critical buffer underflow vulnerability impacting the company’s FortiOS and FortiProxy products. Tracked as CVE-2023-25610 (CVSS score 9.3), the vulnerability allows an unauthenticated attacker to execute arbitrary code or launch a denial of service (DoS) attack on the GUI of vulnerable devices.
🚨Attention! Fortinet has released security patches for 15 new flaws, including a critical #vulnerability (CVE-2023-25610) affecting FortiOS and FortiProxy that could allow attackers to take control of affected systems.
Details: https://t.co/HqSHkSNKpS#infosec #cybersecurity
— Swati Khandelwal (@Swati_THN) March 9, 2023
This type of vulnerability is the result of programs trying to read more data from a memory buffer than what is available. In this scenario, the program must access adjacent memory locations that may lead to crashes and data loss. Buffer underflow vulnerabilities are most often leveraged by attackers for remote code execution (RCE) and DoS attacks. Fortinet strongly urges its users to deploy the security updates immediately. As a temporary workaround, users may also choose to disable access to the HTTP/HTTPS administrative interface or limit the IP addresses that have access to the interface.
Though Fortinet notes that it is not aware of any instance of exploitation of CVE-2023-25610 in the wild, this flaw closely follows on the heels of two other critical RCE flaws that impacted the company’s FortiNAC and FortiWeb products. Just four days after fixes were published for the pair of RCE flaws, a working proof-of-concept was made public resulting in immediate exploitation in the wild. Security teams are reminded that opportunistic attackers continuously sweep for vulnerabilities that allow them to gain initial access with as little work as possible. Critical-level vulnerabilities, particularly those that do not require authentication, are highly attractive to attackers and should be patched as a priority.
如有侵权请联系:admin#unsafe.sh