2022-3-6 04:36:0 Author: www.boredhackerblog.info(查看原文) 阅读量:6 收藏
Introduction:
Just a quick analysis of malware sent via discord...
I got the malicious file from someone who received the file via Discord from a trusted account (which was compromised...)
Analysis:
Hash: 4f709e1c6951bbd65d03a9f44961e0ae
Original filename:Fruit_of_the_ace_v3.11.99.exe
The file looked like nodejs binary
pdb string: C:\Users\runneradmin\AppData\Local\Temp\pkg.3d5278e5642d39a96bc8ed09\node\out\Release\node.pdb
I started by analyzing the file locally but didn't get anywhere quickly so I moved to hatching triage for analysis.
Results: https://tria.ge/220220-wnqp3sbeh6
Here's the process list:
The executable drops and starts temp.ps1, which contains code to hide the window.
Once the window is hidden, it seems to download and execute MachineMania.exe which is a python executable file made with pyinstaller. Argument provided to the machinemania.exe during executing is a discord webhook.
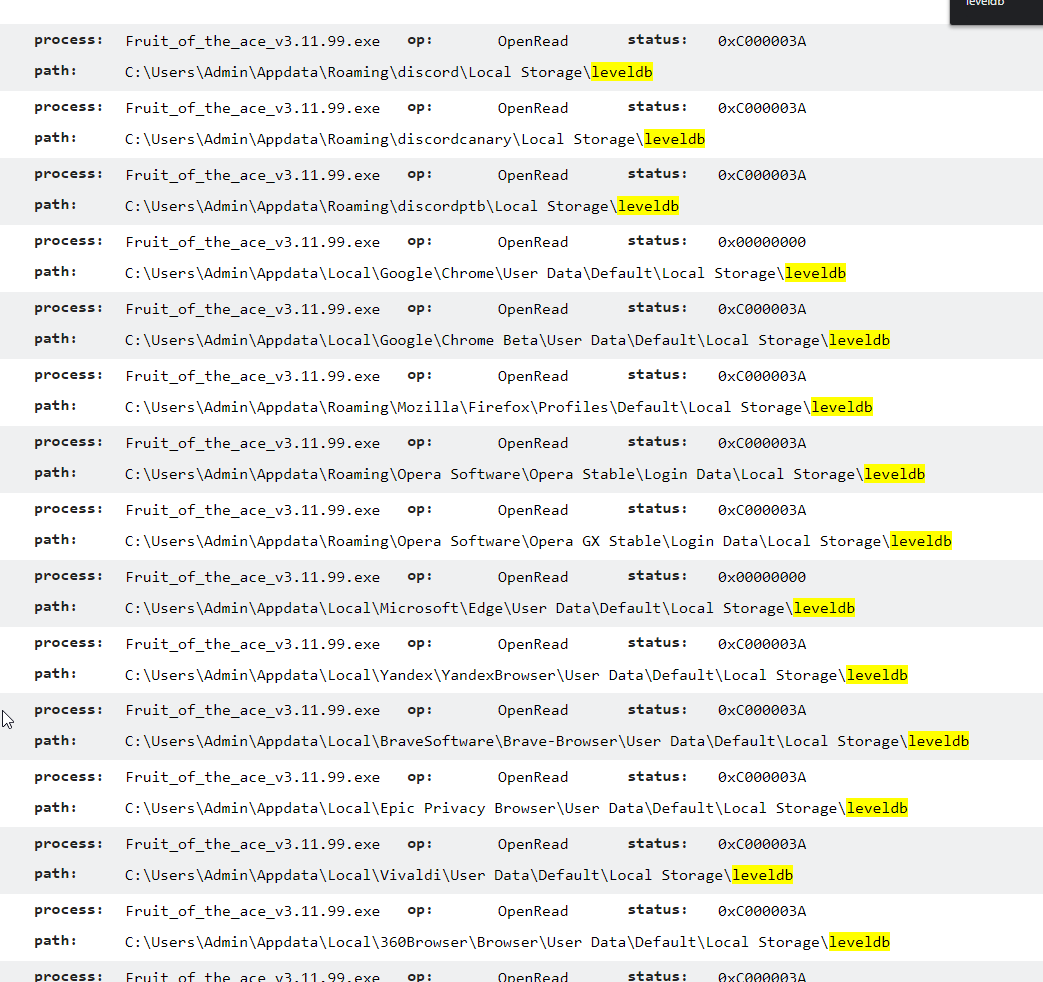
Looking through Triage and file access I see the following:
It appears to be looking for applications listed above but I'm not sure if it actually does anything if the apps are installed.
Network traffic kinda looks like this:
It looks like there is a connection to OneDrive. I was pretty sure that's where the MachineMania.exe was being downloaded from but I didn't see much in the pcap or Triage output.
I went back to debugger and found the exact OneDrive link in the memory which is hosting MachineMania.exe
Looking at MachineMania.exe:
Hash: 725918a6ae94e864908946ebb5e98dee
This is pyinstaller file.
I analyzed that file in Triage but I replaced discord webhook with webhook.site webhook
https://tria.ge/220220-ycs26scgdr/behavioral1
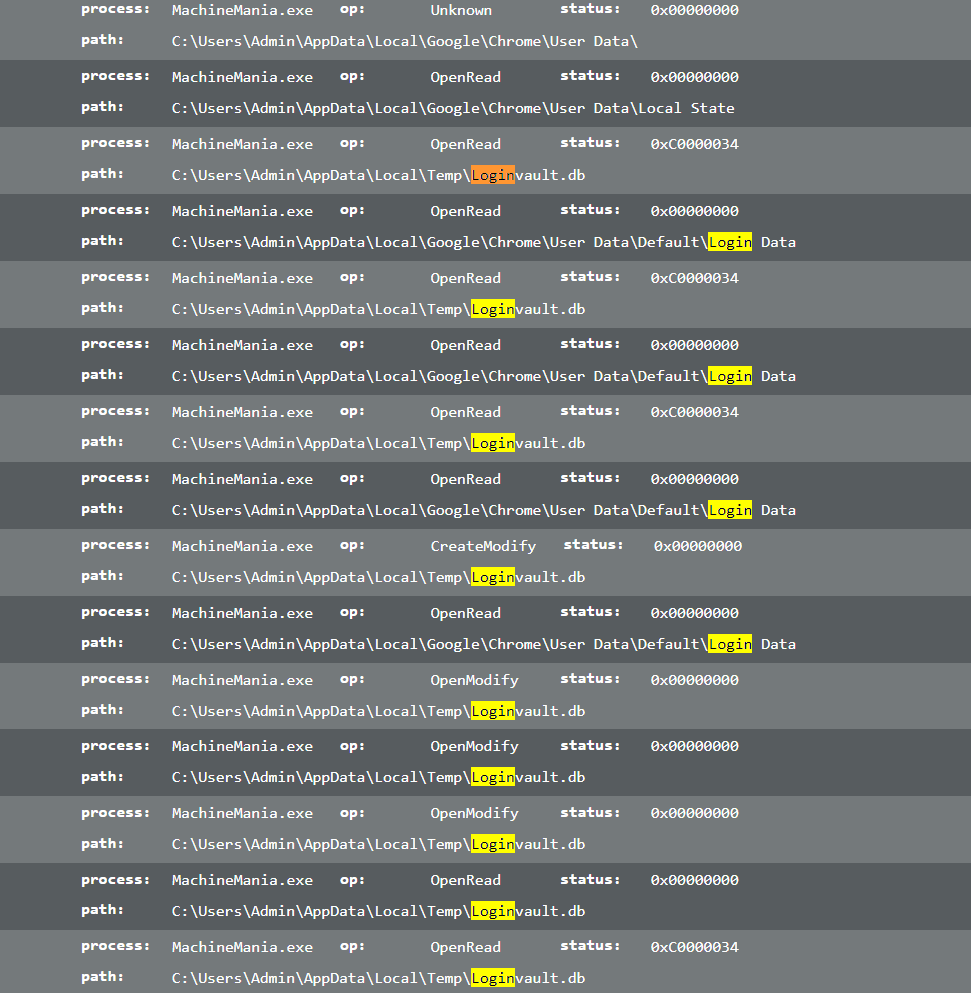
File interaction looks a bit different in analysis of this file. Unlike the original file, this file only looks at Chrome folder.
The webhook requests look kinda like this:
It appears to be only looking at Chrome.
To further analyze the file, I started to decompile the pyinstaller file to see what it has inside of it.
I used this to extract the files: https://github.com/extremecoders-re/pyinstxtractor
I found the following files to be interesting
discordwebhook content looks like it's just doing POST request.
I wasn't able to get anything out of chrome.pyc file but it appears to be backed with pyarmor.
Additionally, while doing some analysis of the original file in debugger I also saw this:
I'm not really sure about what other capabilities the original file has. There is probably more but I mostly looked at the dropped pyinstaller/machinemania.exe file. I'm not sure about how nodejs code can be packed as executable.
Conclusion
Based on limited and quick analysis, it looks like compromised account will share the exe file.
original exe file will download and execute file from onedrive
onedrive file will steal data and send it to discord via webhook.
to me, the onedrive file only seems to be stealing chrome saved passwords and nothing else.
Similar sample: https://twitter.com/GlitchyPSI/status/1439674473515569154
Check the Execution Parents. There are a lot of node binaries and filenames usually look like names of games.
如有侵权请联系:admin#unsafe.sh