Finding bogus content and unexpected links for prescription drugs on your WordPress website can be a frustrating experience. But don’t blame your site: it just got caught up in a bad crowd of black hat SEO spammers and fell victim to a pharma hack.
Pharma spam occurs when bad actors inject a website with keywords for pharmaceutical products. Their end goal is to use an innocent site’s good reputation to lure traffic to a scam. In fact, in 2022 over 40% of SiteCheck’s SEO spam detections were related to pharma spam injections — indicating just how prevalent these infections are.
If you’ve recently encountered redirects to online pharmacies or spam keywords in your website’s search results, you may have been infected with pharma spam. In this post, we’ll explain what the pharma hack is, outline the symptoms you should look out for, and how to find and remove pharmaceutical spam on your WordPress website.
Contents:
- What is a pharma hack?
- Why pharma spam?
- How to know if your site is infected
- How to clean up a pharma hack
- Removing WordPress malware warnings
What is a pharma hack?
A pharma hack is an SEO spam infection that exploits vulnerable WordPress sites, hijacking the website and injecting pages with keywords for pharmaceutical products like Xanax, Levitra, Cialis or Viagra. These pages are indexed by major search engines like Google and Bing, helping to rank the attackers’ spam.
Pharmaceutical spam can be an absolute nightmare for website admins. In these attacks, bad actors leverage a website’s resources and SEO, piggybacking off the site’s own rankings and often redirecting site visitors to spammy websites and content.
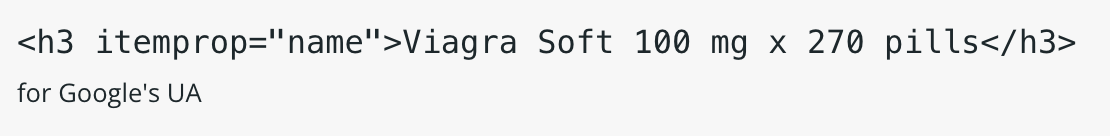
Unfortunately, pharmaceutical spam and redirects often lead to blocklisting which in turn can result in decreased organic traffic, loss of reputation, and fewer sales. And if your web host detects malware, there’s a risk that your site may be suspended.
So, you’ll want to address a pharma hack as soon as possible to mitigate risk for your visitors, reputation, and revenue.
Why pharma spam?
Pharmaceutical prices are much higher in the U.S. than other countries, and many of these spammers are exploiting the fact that they can resell medication they buy locally to Americans at a much lower price than obtaining it through legal options.
Spammers also target drugs that are still under U.S. patent law. The patents prevent cheaper generic options from hitting the market, so spammers will expect American customers to be on the lookout for a cheaper option.
However, don’t consider this a reason to give pharma spam sites a shot for saving money. Buying pharmaceuticals online without a doctor’s prescription in the U.S. is still illegal, and there is no guarantee the spammers won’t take your money and run. And while you may be able to obtain the drugs in question there is no guarantee that they are safe to consume, the correct product, or cut with other cheaper drugs or substances.
How to know if your site is infected with pharma spam
Finding out if your WordPress site is infected with a pharma hack may take a few steps, but isn’t an overly complex process.
Here are four steps you can take to pinpoint a pharma hack on your website.
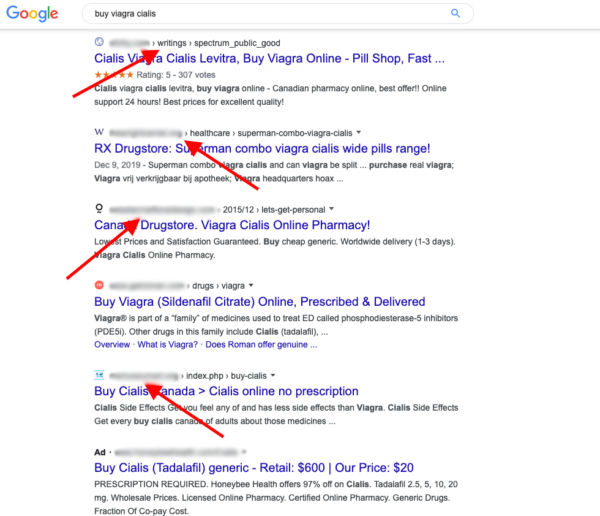
1 – Look for pharmaceutical keywords in search
Just head over to Google and search your site for pharmaceutical-related keywords, such as:
- Viagra
- Cialis
- Nexium
- Buy prescription online
- Buy xanax online overnight
- Buy cheap
If you find pages with content about these pharmaceuticals that you didn’t put there, then your site is infected.
But if you’re feeling a bit squeamish or embarrassed about having male enhancement drugs in your search history, we’ve got you covered.
2 – Use a website scanner
Sucuri’s free SiteCheck tool can scan your site for all kinds of malware including pharmaceutical spam, and will tell you if your site has been blacklisted from the attack.
Simply enter a domain name into the search bar and a website scan will be performed at the client level.
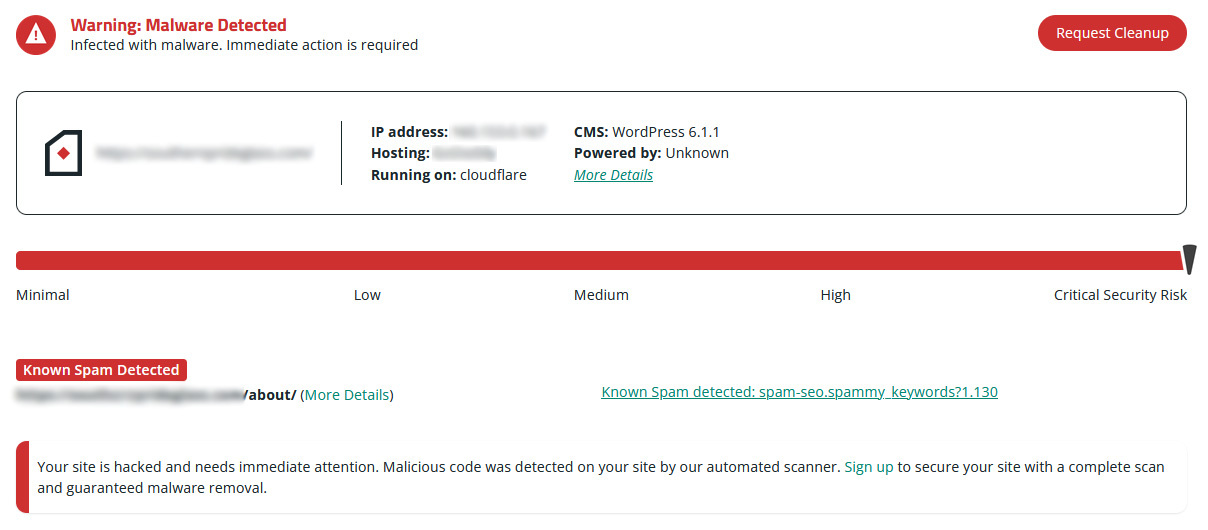
If any SEO spam is detected, you’ll be notified on the results page. Make sure to note any payloads or locations from the SiteCheck report.
Getting a hand with infections is easy – click Request Cleanup to sign up for malware cleanup services and get help from our remediation team.
Important caveat: Remote scans like SiteCheck aren’t able to access the server, which could be hiding malicious PHP, backdoors and phishing that aren’t visible on the client side. Consider running a thorough website scan at the server level to identify all malicious code on your site.
3 – Check your WordPress core files
Next, you’ll want to check your core WordPress file integrity. Because most core WordPress files should not be modified, you’ll want to make sure the attackers did not make any changes to files in the wp-admin, wp-includes, and root folders.
The easiest way to check is by installing the Sucuri plugin from the WordPress repository. It can quickly check your file integrity and compare it against the original source files. If no files have been modified, your core files are clean – but you’re still not out of the woods yet.
4 – Check WordPress for recently modified files
After confirming your core files, you will also want to check for any other recently modified files in your website’s environment, including plugins or themes. These modified files could be part of the attack or a backdoor for the hackers to come back and reinfect your site.
The good news is that there are a couple of methods for checking recently modified files. The Sucuri WordPress plugin’s file integrity monitoring can find and restore modified files. This makes the process much easier for novices.
But if you want to do it yourself without the plugin, you’ll need to log into your server using an FTP client or SSH terminal.
If using SSH, you can list all files modified in the last 15 days using this command:
$ find ./ -type f -mtime -15
If using SFTP, sort by the last modified date column for all files on the server. With either method, make sure to take note of any recently modified files.
It’s worth noting that in some cases bad actors are known to fake the modified/changed times — so you can’t always rely on this step to identify all indicators of compromise.
How to clean up a pharma hack
Now that you know where your pharma hack is, you can start cleaning.
Keep in mind that manually removing “malicious” software can be detrimental to your website’s health. For example, the removal of an injection into an existing legitimate file can cause formatting problems that prevent proper execution of the file’s code.
Do not perform any of these steps without a backup. If you’re feeling uneasy about the process, it may be best to call in a professional to assist.
Also, note that not all pharma hacks are created equal. WordPress pharma hacks can be tricky to remove at times. For example, back in 2016 our remediation team ran into what was described as an “undeletable pharma ‘doorway.’ While the doorway wasn’t literally “undeletable,” it certainly put up a fight against our malware removal professionals.
But if you have your backups and you’re ready to get your website back in shape yourself, let’s get started! We’re always here to help if you encounter any issues.
Cleaning WordPress files and databases
If you did find a pharma hack infection in your core files, you can fix it manually. Just make sure to not overwrite your wp-config.php file or wp-content folder.
First, identify any recently changed files. Confirm if the changes were legitimate with the user who made them. Restore any modified core files with copies from the official WordPress repository.
For any custom or premium files that are not in the official repository, open them in a text editor. Remove any suspicious code and then test to verify that the site is still operational after changes.
After cleaning the files, you’ll want to clean your database tables. Keep in mind that your WordPress plugins also use these tables.
Be very cautious, as these steps can break your website if not properly followed. Make sure to have a backup, test any changes, and get help if you are worried about causing any damage.
To clean pharma spam from an infected database:
- Log into your database administration panel (e.g PHPMyAdmin).
- Search the existing database tables for any suspicious content related to the pharma hack.
- Open the table with the suspicious content and manually remove it.
- Test the changes to verify everything is still working.
- If you used any database access tools like Search-Replace-DB or Adminer, make sure to remove those as well.
Unfortunately pharma spam injections in the _posts table can be tedious to manually remove. The injection may use existing post text for its hyperlink text, so it’s important to avoid inadvertently removing legitimate text during the removal process.
This also further highlights the necessity of a full backup (files AND database) prior to making any modifications.
Finding and removing website backdoors
Now your website should be clean… but let’s keep it that way with a few more steps.
Log in to your site as an admin. Audit your site’s users and see if there are any you don’t recognize. This should include checking whether the user’s email address was modified by the attacker. If there are any suspicious users, delete them. These were likely created by the hackers for use as a backdoor.
Speaking of reinfection, hackers don’t leave just one backdoor option to get back into a compromised environment.
If you miss any backdoors on your WordPress site, you’ll get reinfected and have to start this all over again. That’s why this step is imperative to your website’s health.
Hackers try all kinds of techniques to keep backdoors undetected. One popular method is to embed them into files with the same name as core files but located in the wrong directories.
Attackers can also inject backdoors into common files and directories. Backdoors often contain one or more of the following PHP functions:
- base64
- str_rot13
- gzuncompress
- eval
- exec
- system
- assert
- stripslashes
- preg_replace (with /e/)
- move_uploaded_file
But, much like database tables, these functions are also used legitimately by plugins. As a result, you’ll want to make sure to make backups and test everything to avoid breaking your website.
Removing WordPress malware warnings and blocklisting
Once your website is clean and back to normal, you’ll want to let any blacklisting authorities like Google or Bing know. Because blacklisted websites can lose up to 95% of organic traffic, not doing this can cause damage to your site’s reputation and revenue.
You’ll need to contact any of the blacklisting authorities with some general information on your cleanup process. Blacklisting authorities include Google Search Console, McAfee SiteAdvisor, and Yandex Webmaster.
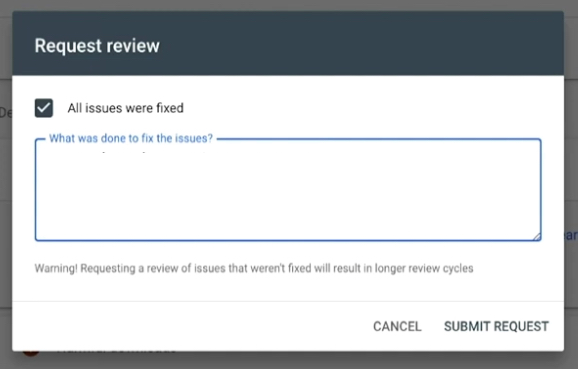
To request a review with Google:
- Navigate to Google Search Console.
- Click on Security Issues.
- Select Request a Review.
- Describe the steps you took to fix the problem.
- Click Submit Request.
You’ll want to provide a thorough description of the steps you took to remove the issue.
For example:
“I located and removed the malicious JavaScript injection that was injecting pharma spam and redirecting users to pharmaceutical websites. I then updated my plugins and website software and changed my passwords.”
It can take days — or even weeks — for your entire site to be recrawled. You’ll need to exercise a bit of patience here. And be sure that the issue is completely resolved before you submit your site for review. If it’s not, resubmitting again could result in a longer wait.
For Sucuri Website Security Platform users, we can submit blacklist review requests on your behalf.
Conclusion
Bad actors are always looking for new websites to infect with SEO spam, backdoors, and credit card skimmers. As a result, anyone with a website needs to keep security top of mind.
With the increased amount of attacks, it’s understandable to feel overwhelmed.
You don’t have to go at it alone. Sucuri can help you keep your website safe from pharma hacks. Our web application firewall (WAF) and platform plans can protect your WordPress sites from pharma hacks and other malware.