2023-4-4 16:14:13 Author: blog.elcomsoft.com(查看原文) 阅读量:22 收藏
In the previous articles we explained how to connect the first-generation HomePod to a computer, apply the exploit, extract a copy of the file system and decrypt the keychain. Since the HomePod cannot be protected with a passcode and does not allow installing apps, we were wondering what kinds of data the speaker may have and what kinds of passwords its keychain may store.
The keychain
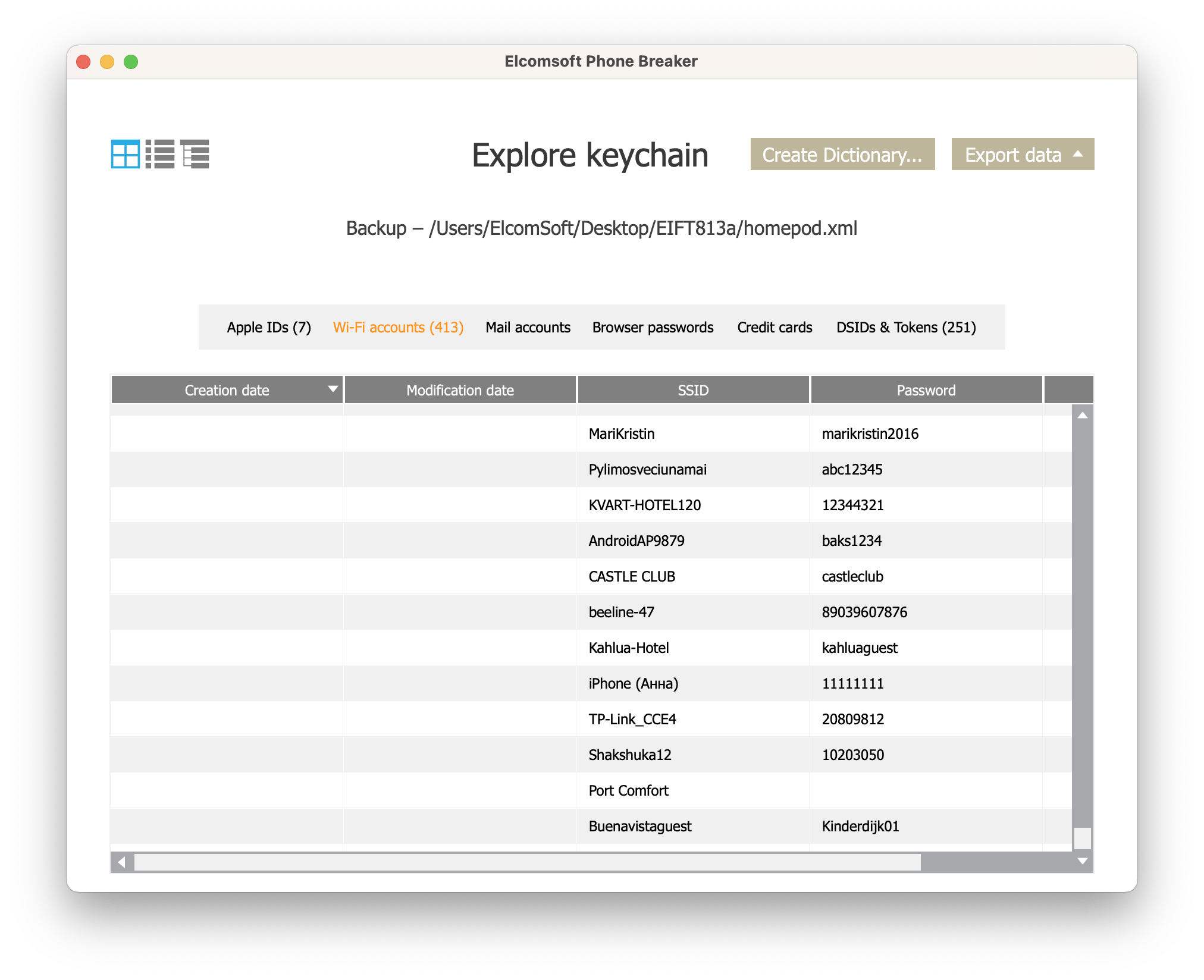
The HomePod contained a copy of the keychain. Once we loaded the file into Elcomsoft Phone Viewer, we were able to see the keychain items available.
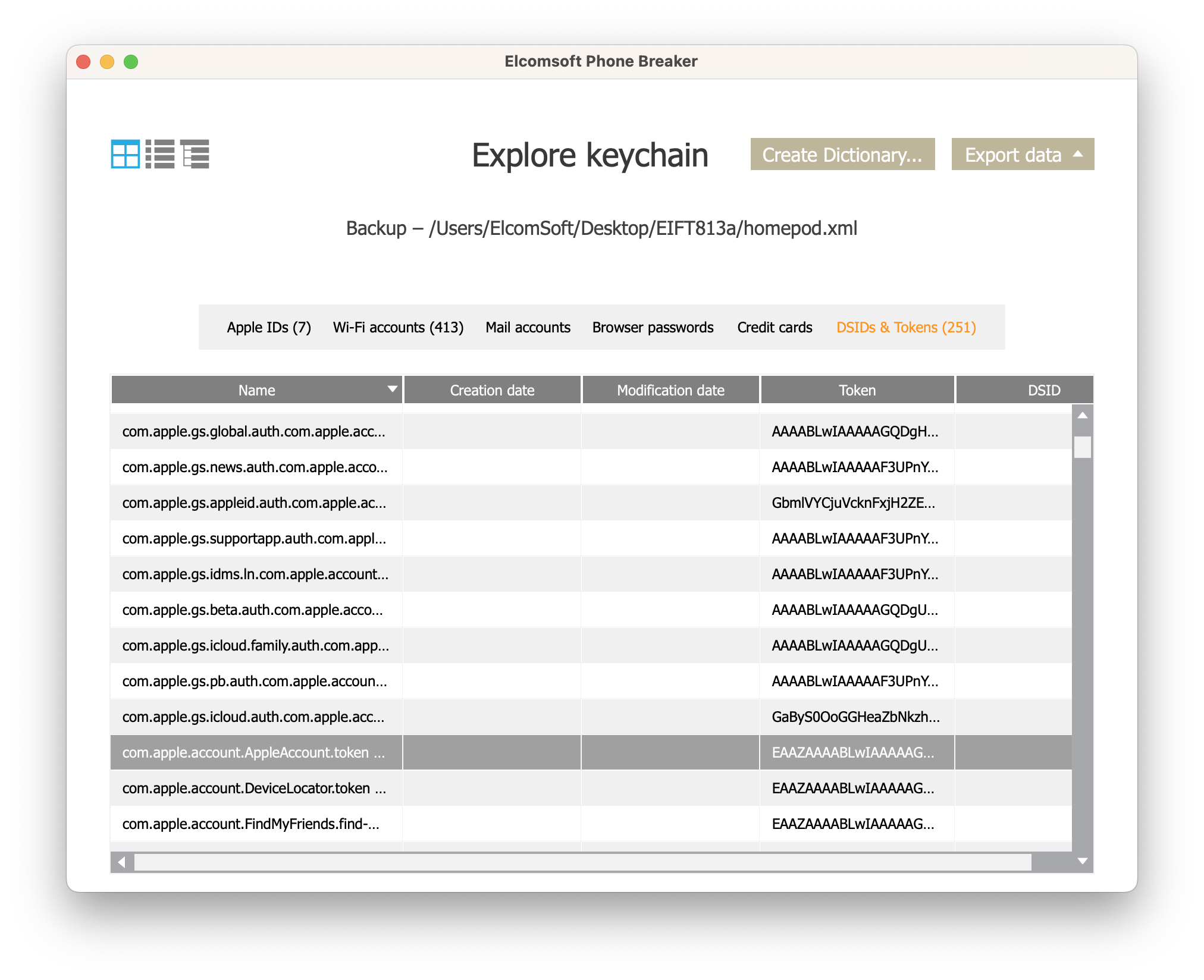
What we saw was a long list of Wi-Fi passwords, which contained passwords to pretty much all Wi-Fi access points stored in the iPhone on the same Apple ID. We also found a list of tokens including an Apple account token. We have not looked into this any further.
The file system image
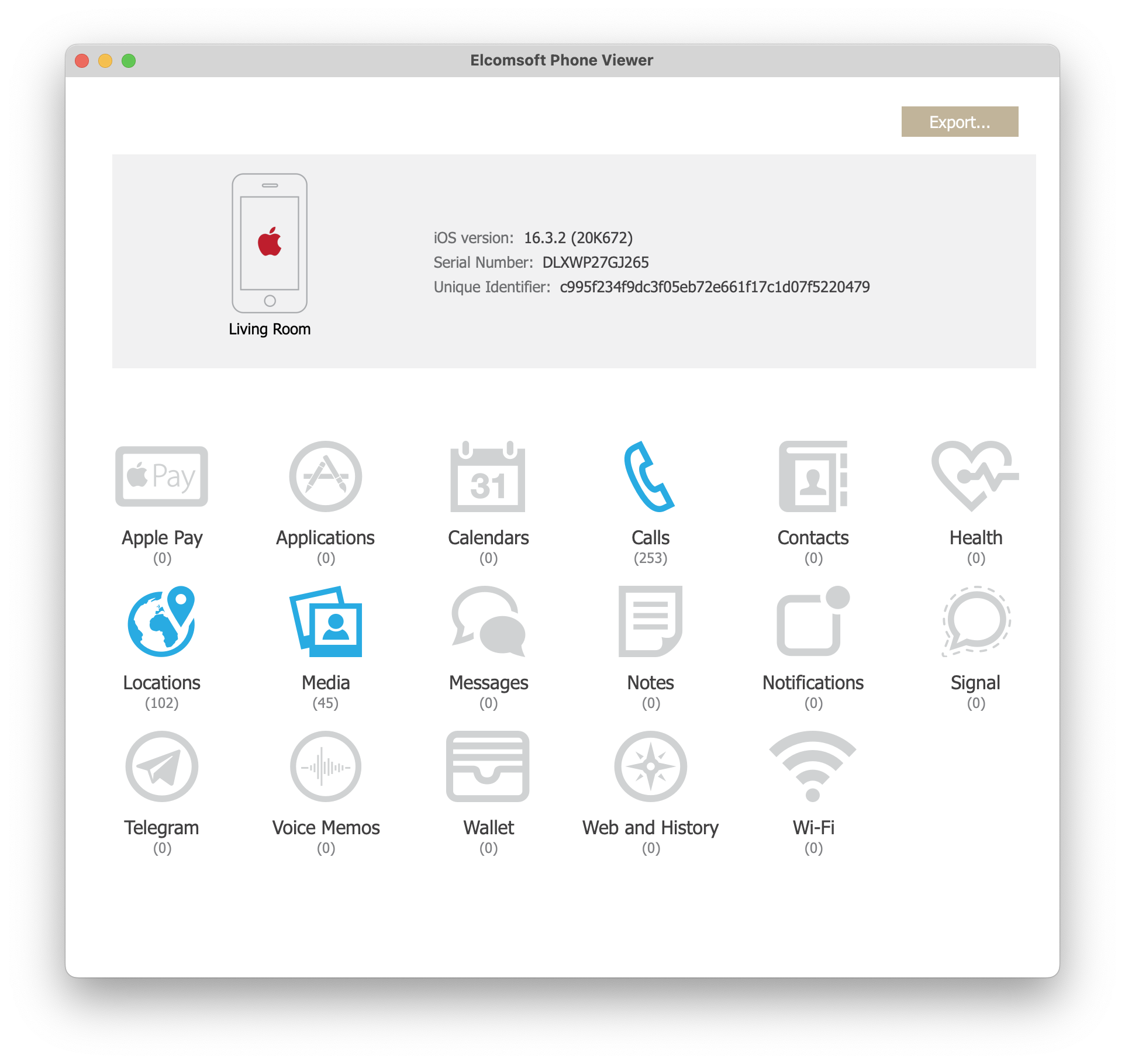
The size of the file system image extracted from the HomePod (user partition only) was some 3.81 GB. Once we loaded the image into Elcomsoft Phone Viewer, we’ve seen some data in the following categories: Calls, Locations, and Media.
Calls
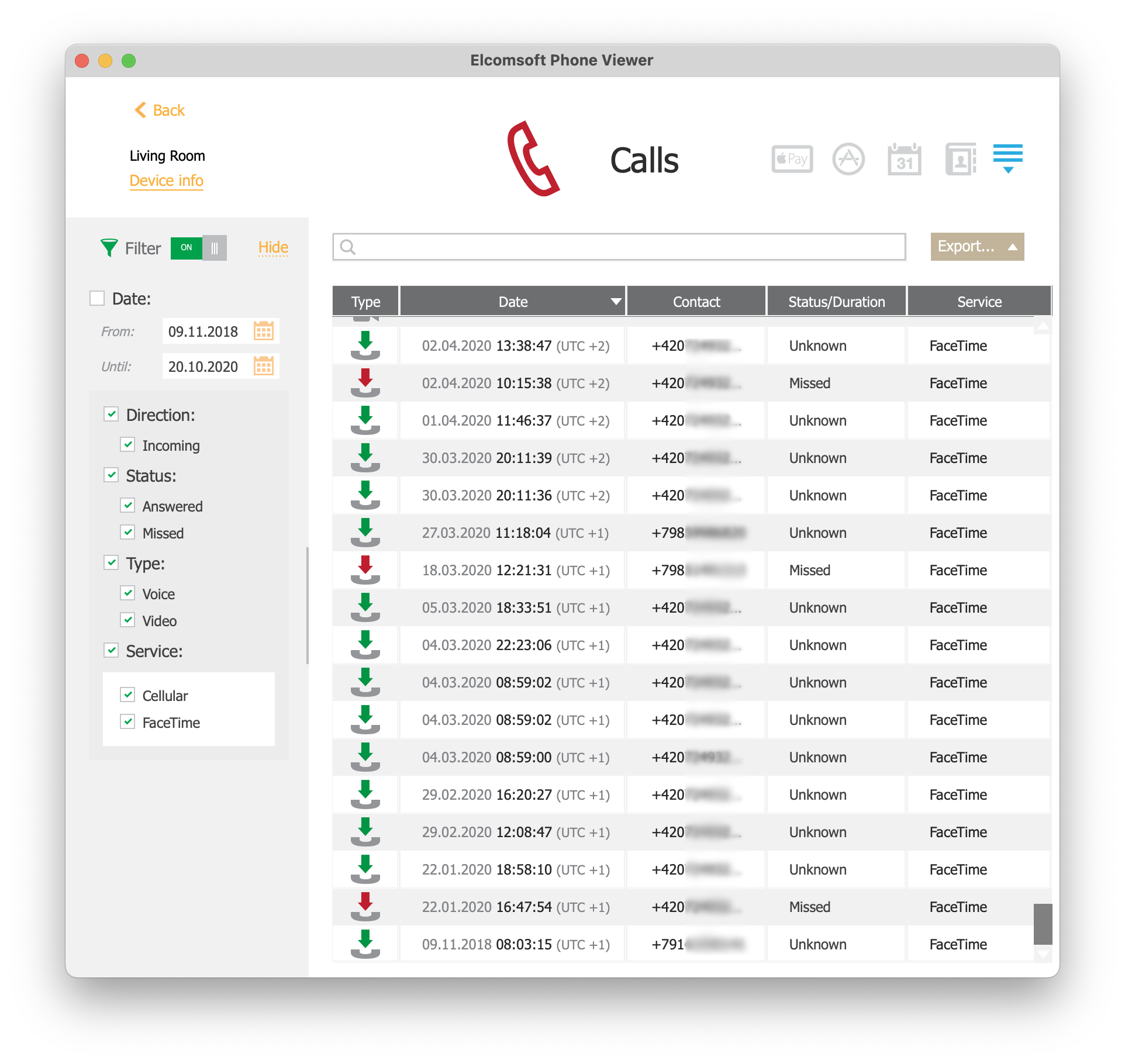
Back in 2016, we discovered that Apple silently synchronizes call logs with iCloud. Back then, we tried to understand how the syncing works and whether one can disable call sync. At a certain point, the syncing seemingly stopped, or was controlled by the “Allow Calls on Other Devices” feature. The HomePod we analyzed contained information about some 253 calls, all dating back to 2020.
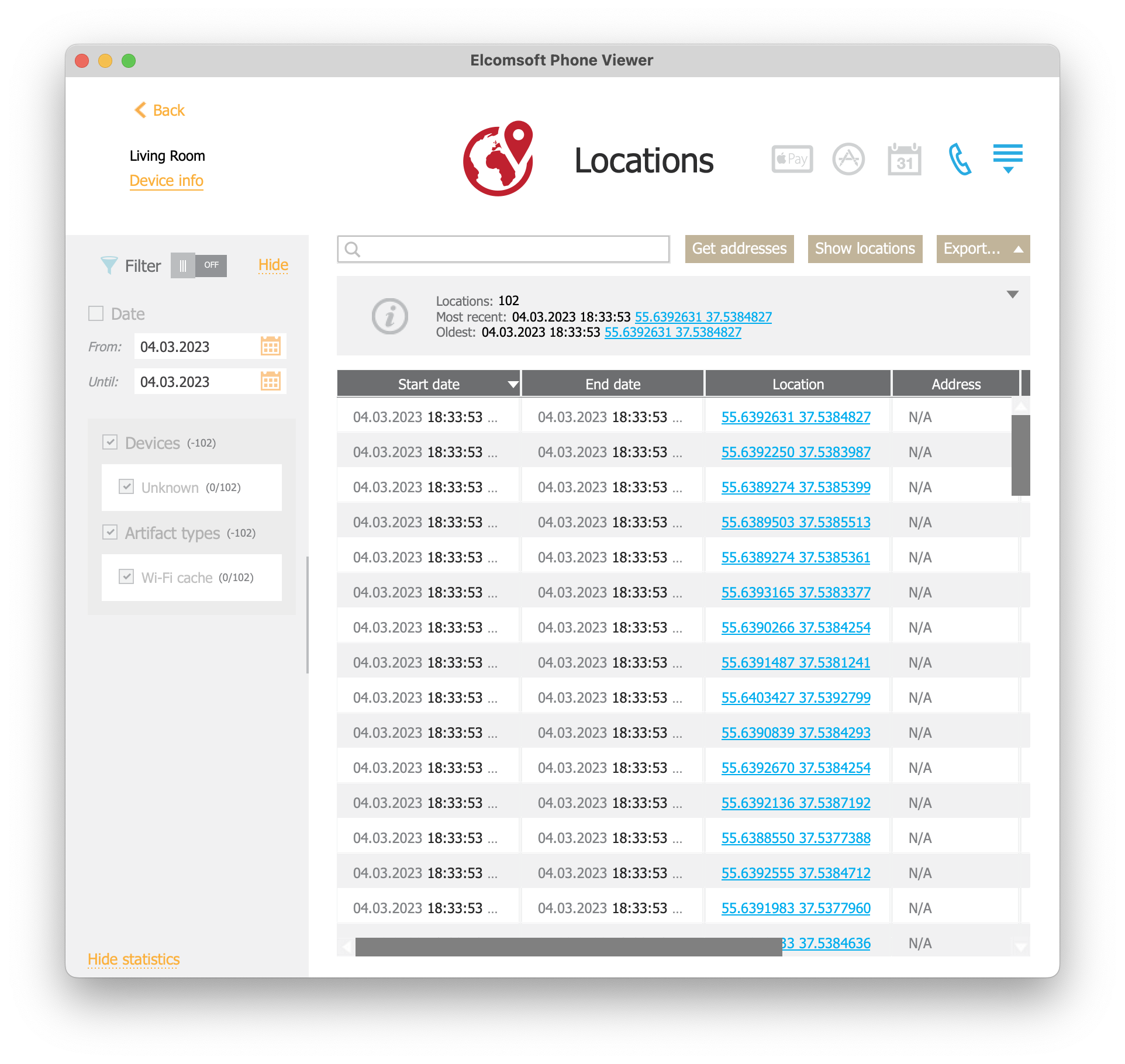
Locations
There were some 102 location reports stored in the HomePod. It seems that these locations were determined with a Wi-Fi reverse lookup. Since the HomePod was stationary, all records point to the home location.
Media
We have not found any user-created media files on the HomePod. Some preinstalled sounds (such as white noise) and a number of system images were discovered.
Additional evidence
Mattia Epifani performed a quick analysis of the file system image, and reports the following findings.
- Wi-Fi network:
/private/var/preferences/com.apple.wifi.known-networks.plist - Wi-Fi network geolocation:
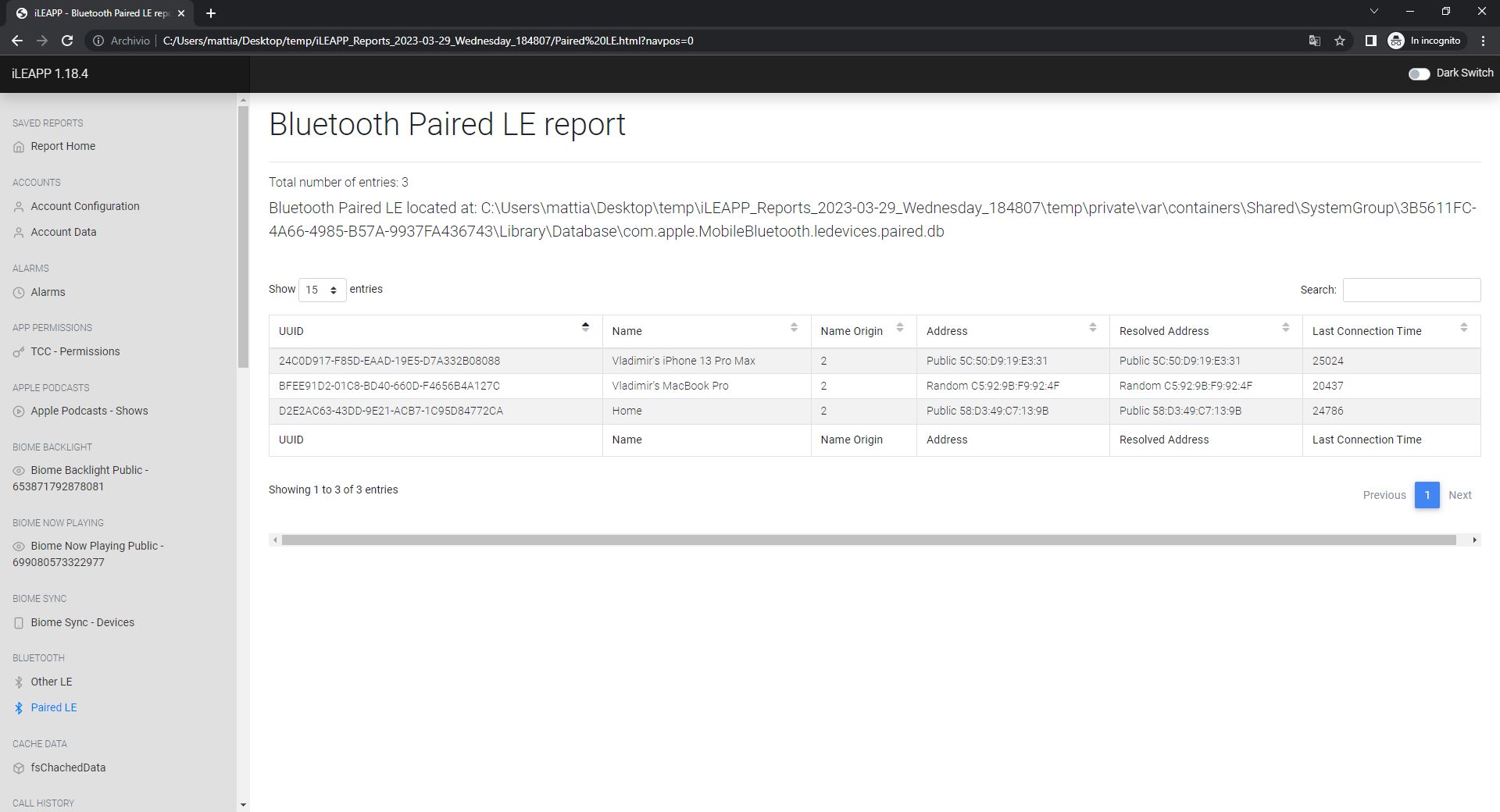
/private/var/root/Library/Caches/locationd/cache_encryptedB.db - Paired and Seen Bluetooth devices (huge list):
/private/var/containers/Shared/SystemGroup/<GUID>/Library/Database/com.apple.MobileBluetooth.ledevices.other.db
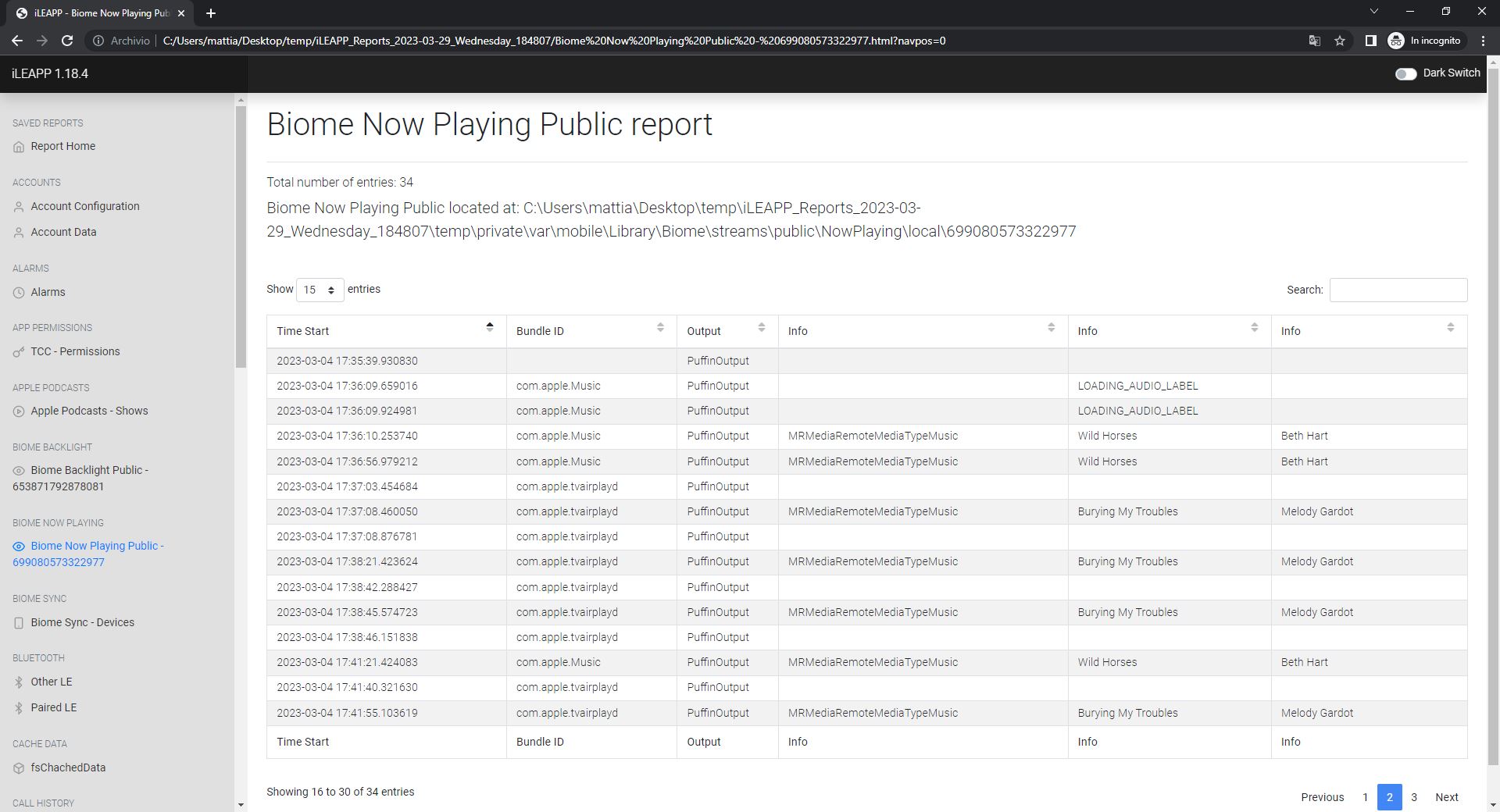
/private/var/containers/Shared/SystemGroup/<GUID>/Library/Database/com.apple.MobileBluetooth.ledevices.paired.db - KnowledgeC, containing info about Display On/Off and NowPlaying (with timestamp and media/song name)
- MediaLibrary (usual file and info)
- Account (usual file and info about iCloud account)
- Synced Preferences
/private/var/mobile/Library/SyncedPreferences/com.apple.kvs/com.apple.KeyValueService-Production.sqlite
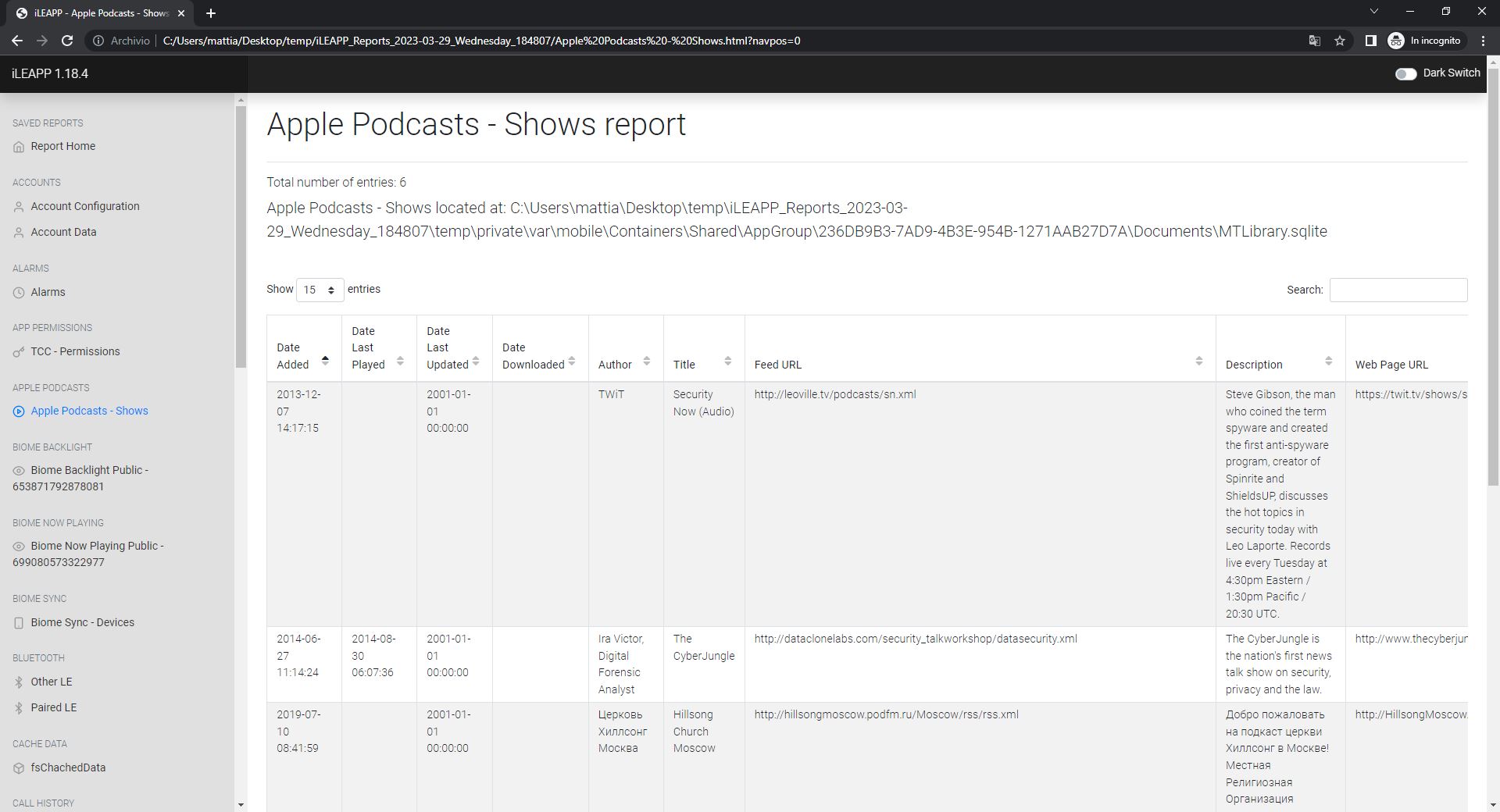
this seems really interesting as it contains metadata of some of your messages/email with addresses. - Apple Podcast data
\private\var\mobile\Containers\Shared\AppGroup\<GUID>\Documents\MTLibrary.sqlite - Biome data (Backlight and NowPlaying, similar to knowledgeC)
- Call History from 2020
- Alarms set on the device
- Mobile Activation Logs
- Mobile Installation Log
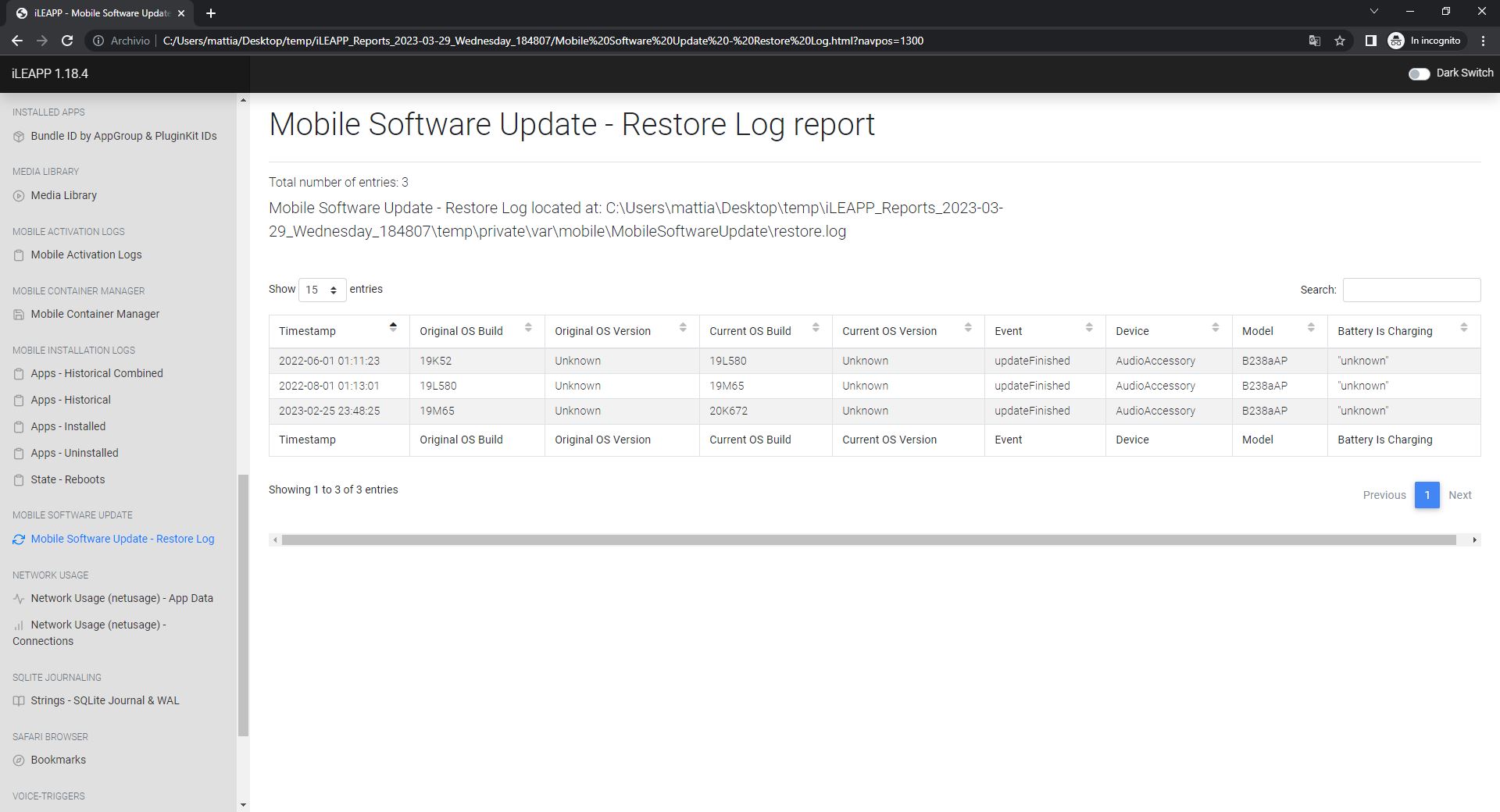
- OS Software Update History
- PowerLogs with recent activities (Data Usage, Applcation Usage)
By loading the image into iLEAPP, one can access a bit more information.
Podcasts:
Biome Now Playing:
Paired Bluetooth devices:
And finally, the iOS update history log:
Conclusion
Our analysis of the first-generation HomePod has revealed that it contains a limited amount of potentially sensitive information. The keychain stored on the device contained a list of Wi-Fi passwords and tokens, while the file system image contained call logs (the last of which originated back in 2020), limited location data, the list of paired and seen Bluetooth devices, and information about media files. Although we did not find any user-created media files on the HomePod, we did discover some metadata and playback history records. Our analysis highlights the importance of analyzing all kinds of electronic devices when collecting digital evidence.
REFERENCES:
![]()
Elcomsoft iOS Forensic Toolkit
Extract critical evidence from Apple iOS devices in real time. Gain access to phone secrets including passwords and encryption keys, and decrypt the file system image with or without the original passcode. Physical and logical acquisition options for all 64-bit devices running all versions of iOS.
Elcomsoft iOS Forensic Toolkit official web page & downloads »
![]()
Elcomsoft Phone Viewer
Elcomsoft Phone Viewer is a fast, lightweight forensic viewer for quickly accessing information extracted from mobile backups. Supporting a variety of platforms and data formats, the tool can display information extracted from local and cloud iOS backups and Microsoft Accounts. Password-protected iTunes backups can be automatically decrypted and analyzed without using third-party tools.
如有侵权请联系:admin#unsafe.sh