News broke over the weekend that ransomware gang LockBit had begun targeting Mac users, triggering some concern in the Apple community. But have no fear: Apple security experts have dissected the ransomware, taking a deep dive into what it can and cannot do, and concluded that it is, actually, toothless.
"Yes, it can indeed run on Apple Silicon. That is basically the extent of its impact," said Patrick Wardle (@patrickwardle), known macOS cybersecurity expert and founder of the non-profit, Objective-See. "macOS users have nothing to worry about."
Here's why.
The signature is invalid
Using a utility called codesign, Wardle saw that the payload's signature value is "ad-hoc" compared to an Apple Developer ID. Because the signature is invalid, macOS won't execute it.

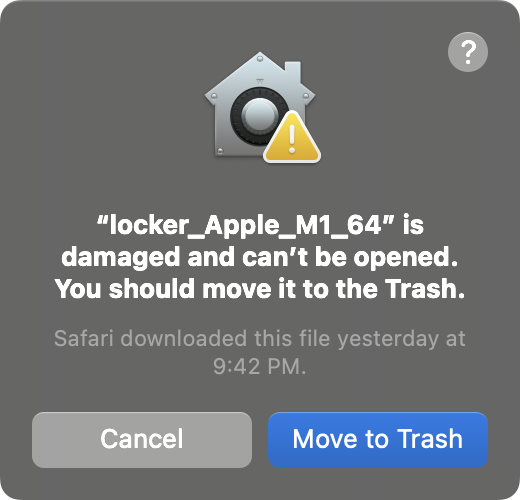
If you're brave enough to run the payload on your macOS, you'll be met with this message, says Wardle. (Source: Objective-See)
The encryptor is likely a test file
Azim Khodjibaev (@AShukuhi), a security researcher at Cisco Talos, floated the theory to BleepingComputer that the encryptors designed for macOS were "meant as a test and were never intended for development in live cyberattacks."
Wardle further confirmed this theory, stating the malware is far from complete. Indicators in the malware's code suggest it's Linux-based but compiled for macOS with basic configuration settings included. The code also shows its developers have yet to consider macOS's TCC (Transparency, Consent, and Control) and SIP (System Integrity Protection), two security features meant to protect user files and folders.
With TCC and SIP present, the ransomware will only be able to encrypt a little, if at all.
The code is buggy and will crash
Laying further credence to the test file theory, Wardle found the macOS payload contains a buffer overflow, which will cause it to crash when executed.

No worries for now!
Apple users can rest easy knowing that this macOS ransomware, as it is now, will hardly impact anyone. However, as Wardle quickly pointed out, this may be different in future releases.
"The fact that a large ransomware gang has apparently set its sights on macOS should give us pause for concern and also catalyze conversations about detecting and preventing this (and future) samples in the first place," he says in his blog.
With LockBit operating as a ransomware-as-a-service (RaaS) outfit, its ambition is to offer a range of ransomware. Currently, we have at least two available offerings: LockBit Black (based on BlackMatter's code) and LockBit Green (based on Conti's code). So expanding to target systems outside its repertoire is not only a logical move but also strategic.
"For most organizations, the main takeaway is Macs are probably safe, for now, but your Windows servers were always the prime target anyway," says Malwarebytes Security Evangelist Mark Stockley. However, Mark warned:
"You're only safe until you're not, and there's no timeline on getting this working. We won't get a warning in advance, we'll just hear (probably from LockBit itself) that an organization with lots of Macs has been turned over. So...what are you going to do if you have lots of Macs in your organization? Wait for the horse to bolt and then shut the door, or shut the door now?"
In an interview with BleepingComputer, LockBit's public-facing representative LockBitSupp says the Mac encryptor is "actively being developed."
LockBit was by far the most dominant ransomware in 2022, and hasn't slowed down in 2023, which is why it's one of the five threats you can't afford to ignore in the Malwarebytes 2023 State of Malware report.
How to avoid ransomware
- Block common forms of entry. Create a plan for patching vulnerabilities in internet-facing systems quickly; disable or harden remote access like RDP and VPNs; use endpoint security software that can detect exploits and malware used to deliver ransomware.
- Detect intrusions. Make it harder for intruders to operate inside your organization by segmenting networks and assigning access rights prudently. Use EDR or MDR to detect unusual activity before an attack occurs.
- Stop malicious encryption. Deploy Endpoint Detection and Response software like Malwarebytes EDR that uses multiple different detection techniques to identify ransomware, and ransomware rollback to restore damaged system files.
- Create offsite, offline backups. Keep backups offsite and offline, beyond the reach of attackers. Test them regularly to make sure you can restore essential business functions swiftly.
- Don’t get attacked twice. Once you've isolated the outbreak and stopped the first attack, you must remove every trace of the attackers, their malware, their tools, and their methods of entry, to avoid being attacked again.
Malwarebytes removes all remnants of ransomware and prevents you from getting reinfected. Want to learn more about how we can help protect your business? Get a free trial below.