2023-4-24 23:3:16 Author: www.thezdi.com(查看原文) 阅读量:88 收藏
Last week, the Zero Day Initiative (ZDI) threat-hunting team observed new exploit attempts coming from our telemetry system in Eastern Europe indicating that the Mirai botnet has updated its arsenal to include CVE-2023-1389, also known as ZDI-CAN-19557/ZDI-23-451. This bug in the TP-Link Archer AX21 Wi-Fi router was originally disclosed to ZDI during the Pwn2Own Toronto event, where it was used by Team Viettel in their LAN-side entry against the TP-Link device and by Qrious Security in their WAN-side entry.
Both teams’ entries were successful at the contest, and the vulnerabilities were disclosed to the vendor. Interestingly, the bug was also used by the Tenable team in their unsuccessful Pwn2Own attempt against the device. They, too, disclosed the bug to TP-Link, but their public report did not show that the bug could be exploited on the WAN interface. TP-Link released a firmware update in March that “Fixed some security issues” – including this and other CVEs. It was after this fix was made public that exploit attempts using this CVE were detected in the wild.
Vulnerability Details
The bug itself is an unauthenticated command injection vulnerability in the locale API available via the web management interface. This endpoint allows a user to specify the form we want to call by specifying the query string form along with an operation, which is usually read or write. In this instance, we are interested in the write operation on the country form, which is handled by the set_country function. This function will call merge_config_by_country that concatenates the specified country field into a command string. This command string will be executed using the popen function. There is no sanitization of the country field, so an attacker can achieve command injection at this point.
This functionality is exposed on the LAN side of the router, as evidenced by both Team Viettel and Tenable targeting this functionality at the contest. However, the team from Qrious Security was able to exploit this vulnerability on the WAN interface of the router. They discovered a race condition issue related to iptable handling on the TP-Link’s WAN-side processing that would briefly expose this functionality on the WAN-side. This allowed them to chain the race condition weakness with the locale API command injection to gain code execution at the contest. According to TP-Link, both issues were resolved in the patch released on March 17.
Active Exploitation Details
Starting on April 11th, we began seeing notifications from our telemetry system that a threat actor had started to publicly exploit this vulnerability. You can see an example of the attack here:
Most of the initial activity was seen attacking devices in Eastern Europe, but we are now observing detections in other locations around the globe.
Mirai Payloads
In this version of Mirai, the attackers utilize CVE-2023-1389 to make an HTTP request to the Mirai command and control (C2) servers to download and execute a series of binary payloads. These binary payloads are intended for various system architectures. This is one such request:
The binary payloads are downloaded and then executed using brute-force methodology to find the appropriate payload for the target system architecture.
Once the appropriate binary is found and the payload is installed, the host becomes fully infected and establishes a connection with the Mirai C2. Here’s a network trace showing this connection:
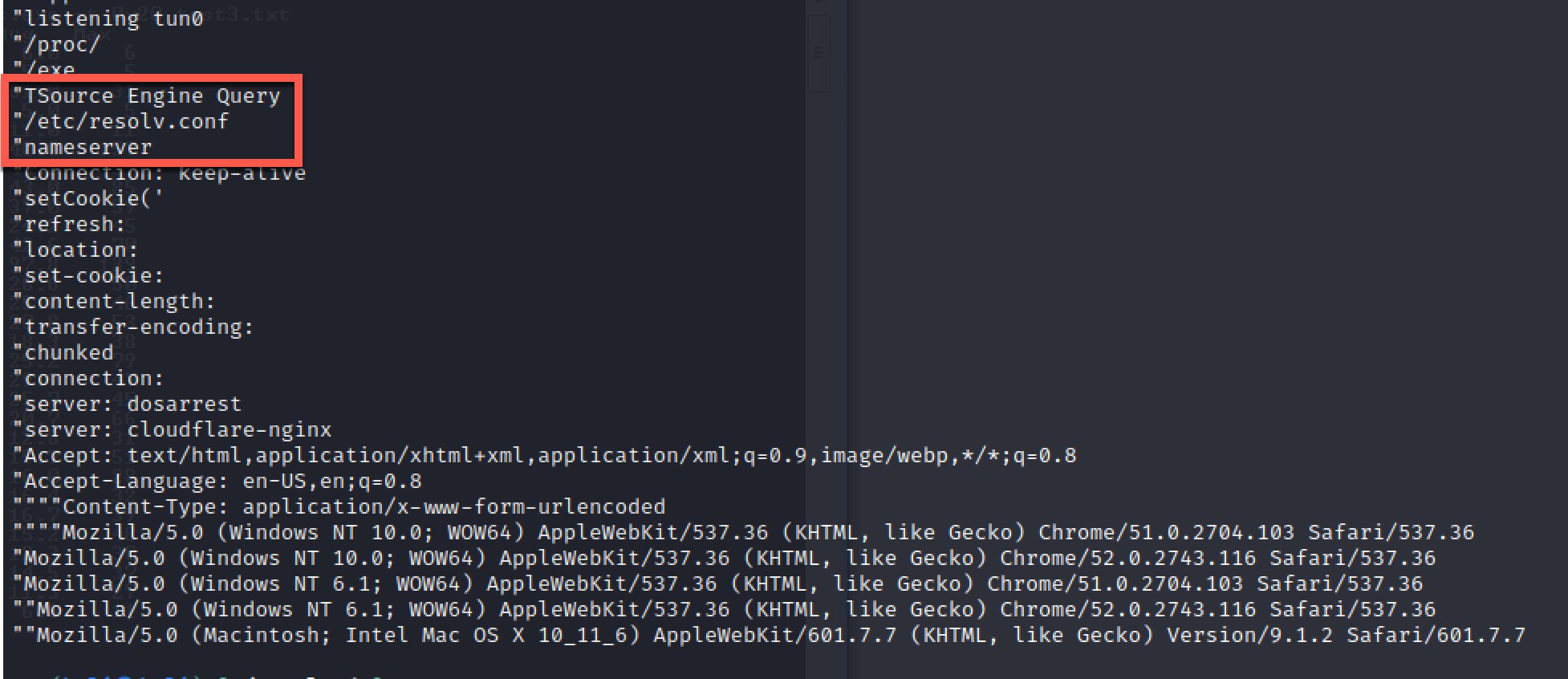
While analyzing some of the payloads, we determined that the threat actors are encrypting strings using 0x00 and 0x22 as XOR keys. Unencrypting these strings revealed some of the capabilities and configuration details that correspond with known Mirai indicators.
Part of the plaintext configuration reveals the Mirai bot attack functions, which can be found in Mirai’s source code. For example:
Among the interesting functions is a TSource Engine Query attack functionality. This can be used to launch a Valve Source Engine (VSE) distributed denial-of-service (DDoS) attack against game servers.

The unencrypted strings reveal further configuration details about this Mirai bot. These include specific User-Agent strings and server headers, such as cloudflare-nginx and dosarrest. These allow the bot to imitate legitimate traffic, making it more difficult to separate DDoS traffic from legitimate network traffic.
Indicators of compromise
The following hashes and other data were detected as being used by this exploit:
Initial Downloader888f4a852642ce70197f77e213456ea2b3cfca4a592b94647827ca45adf2a5b8
Payloadsb43a8a56c10ba17ddd6fa9a8ce10ab264c6495b82a38620e9d54d66ec8677b0cb45142a2d59d16991a38ea0a112078a6ce42c9e2ee28a74fb2ce7e1edf15dce3366ddbaa36791cdb99cf7104b0914a258f0c373a94f6cf869f946c7799d5e2c6413e977ae7d359e2ea7fe32db73fa007ee97ee1e9e3c3f0b4163b100b3ec87c22d0c8ab6c71743af8667c7318a6d8e16c144ace8df59a681a0a7d48affc055994cb8c90d1e1b2d725c2c1366700f11584f5697c9ef50d79e00f7dd2008e989a0461f59a84ccb4805c4bbd37093df6e8791cdf1151b2746c46678dfe9f89ac79daed078d3e65b5ff4dd4067ae30da5f3a96c87ec23ec5be44fc85b543c179b7770d404a27c2f511ea7f4adb8aa150f787b2b1ff36c1b67923d6d1c90179033915eca42235a41dbd60615d91d564c91933b9903af2ef3f8356ec4cfff2880a2f193f427eda4d4e18fb192d585fca1490389a1b5f796f88e7ebf3eceec51018ef4daaf446e4e7bfc05a33c8d9e5acf56b1c7e95f2d919b98151ff2db327c333f0894f53eb7fbfa5b68cad3a0850b570cbbcb2d4864e62b5bf0492b54bde2bdbe44b
URLshttp[://]185[.]225[.]74[.]251/armv4lhttp[://]185[.]225[.]74[.]251/armv5lhttp[://]185[.]225[.]74[.]251/armv6lhttp[://]185[.]225[.]74[.]251/armv7lhttp[://]185[.]225[.]74[.]251/mipshttp[://]185[.]225[.]74[.]251/mipselhttp[://]185[.]225[.]74[.]251/sh4http[://]185[.]225[.]74[.]251/x86_64http[://]185[.]225[.]74[.]251/i686http[://]185[.]225[.]74[.]251/i586http[://]185[.]225[.]74[.]251/archttp[://]185[.]225[.]74[.]251/m68khttp[://]185[.]225[.]74[.]251/sparc
Domainzvub[.]us
IP Address185[.]225[.]74[.]251
Conclusion
Seeing this CVE being exploited so quickly after the patch being released is a clear demonstration of the decreasing “time-to-exploit" speed that we continue to see across the industry. That said, this is nothing new for the maintainers of the Mirai botnet, who are known for quickly exploiting IoT devices to maintain their foothold in an enterprise. Looking back at this CVE, it was also interesting to see it being discovered independently by multiple teams in preparation for the Pwn2Own Toronto contest. Each team used different techniques to discover this vulnerability along with distinctive approaches to how they went about exploiting it. We would like to thank all the teams at the Pwn2Own contest for finding and disclosing these critical-class issues. It truly demonstrates the value of the contest, especially in the realm of home and small office devices. Finally, we would like to acknowledge the efforts TP-Link exhibited in developing and deploying a patch. Applying this patch is the only recommended action to address this vulnerability, and we recommend all users of the TP-Link Archer AX21 Wi-Fi router apply it as soon as possible.
Our threat hunting team continues to seek and find exploits being used in the wild, and we’ll publish details on some of these discoveries in the future. Until then, follow the team on Twitter, Mastodon, LinkedIn, or Instagram for the latest in exploit techniques and security patches.
如有侵权请联系:admin#unsafe.sh