Application whitelisting is a very effective protection mechanism, but it can be difficult to manage and deploy at scale, and is not commonly deployed by larger organizations.
What is application whitelisting?
Whitelisting is a way of creating an inventory of secure software applications that may run on an organization’s network. Whereas blacklists block specific application sets, whitelists specify which programs are allowed—with the objective of preventing harmful files and malicious software from running on a company’s infrastructure.
How application whitelisting works?
Implementation of application whitelisting begins with building a list of approved applications. The whitelist can be built into the host operating system (OS), or it can be provided by a third-party vendor. The simplest form of whitelisting allows the system administrators to specify file attributes associated with whitelisted applications, such as file name, file path and file size.
If the software determines that the application is allowed, process creation completes and the code will execute. On the other hand, if the application is not allowed, the process is terminated, and an error message may be displayed.
Types of application whitelisting
There are multiple types of application whitelisting, such as:
- File size
- File path
- File name
- File hash
- Digital signature
Application whitelisting solutions
Microsoft provides multiple such solutions:
- Software Restriction Policies (SRP)
- AppLocker
- Windows Defender Application Control (WDAC)
Additionally, there are 3rd party tools available for application whitelisting.
Application whitelisting rules
On this blog the focus will be on AppLocker. AppLocker has three primary rules categories that can be combined:
- File paths rules
- File hash rules
- Digital signature rules
AppLocker can be found from within the Group Policy Management at Local Computer Policy -> Computer Configuration -> Windows Settings -> Security Settings -> Application Control Policies.

By taking a look over the Configure rule enforcement we can see there are 4 options that can be enabled.

Let’s break each option down:
- Executable rules – Enforces the rules for executable files (.exe)
- Windows Installer rules – Enforces the rules for windows installer files (.msi)
- Script rules – Enforces the rules for PowerShell, JScript, VB and older file formats (.cmd, .bat)
- Package app rules – Enforces the rules for packages that can be installed through Microsoft Store
To create an application whitelisting configure the Executable Rules located on the left pane and add a few rules.

Enforce the newly created rules:

Enumerating AppLocker policies
AppLocker policies can be enumerated using the registry query functionality, as show below:

All the rules created can be listed afterward, by querying one of the chosen registries

Furthermore, each rule can be then queried and the permissions can be observed.

Bypassing leveraging trusted folders
Update the GPO, and try copying a well-known .exe file to another path than the ones allowed. It can be noticed that it’s not possible to run it.

Accesschk from Sysinternals Suite can be used to find folders that are writable and can be leveraged. It should be noted that the output is way longer than what is presented below.

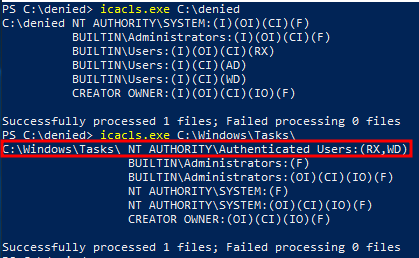
Furthermore, icacls can be used to determine if we also have execute rights within the targeted folder.
Below is presented icacls output of a folder where binary execution is not allowed, and where one has execution granted.

By moving the binary to the tested folder, we can execute our binary.

Bypassing using DLLs
From the initial setup there was no option of blocking out DLLs, resulting in another way of bypassing the application whitelisting. It should be noted that the DLL is located on the user desktop, where a rule enforcing the block of binaries exists.

The AppLocker configuration can be further tweaked to restrict the usage of DLLs by enabling DLL rule collection from within the AppLocker properties.

By switching back to the Enforcement tab a new option regarding DLL can be observed.

Allowing or denying running DLLs can be done through creating rules. After creating the rules, if the DLL is ran again, it won’t execute.

Bypassing using third parties
Third party tools or software can be used to bypass the AppLocker policy.
However, this is conditional, as it requires the system to have installed these tools on it. An example would be using python or perl.

Final thoughts
In conclusion, bypassing application whitelisting can be a daunting task, but it is not impossible. By understanding how application whitelisting works, attackers can identify weaknesses and devise strategies to evade the controls. However, organizations can take steps to protect their systems from such attacks.
Finally, it’s essential to keep in mind that bypassing application whitelisting is not a new technique, and attackers are always looking for new ways to evade security controls.
如有侵权请联系:admin#unsafe.sh