Views: 61
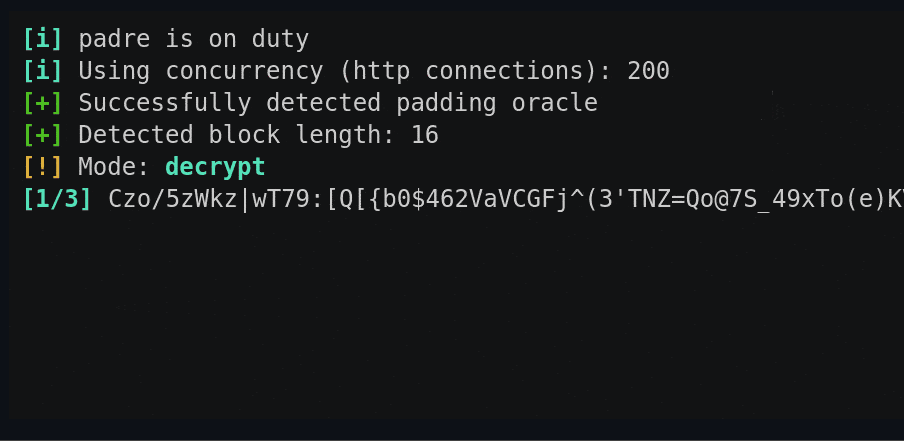
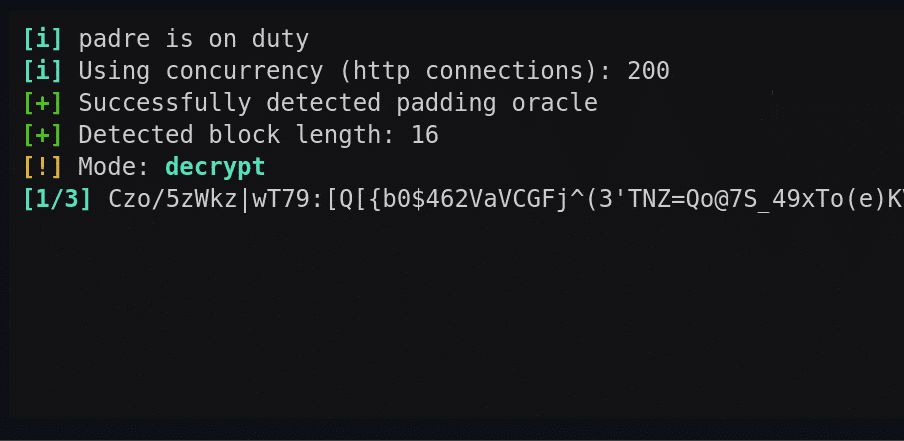
padre is an advanced exploiter and Padding Oracle attack tool that can be deployed against CBC mode encryption.
In many cryptographic systems, especially those that use block cyphers (like AES), data must be divided into blocks of a specific size. If the data doesn’t fit neatly into this block size, it must be “padded” with extra bits to fill out the remaining space. This padding must be done in a specific way so it can be identified and removed when the data is decrypted.
So in this attack type, we don’t know the key – but we do have access to a system that does know the key (the oracle) and we can leverage information from that system to decrypt the block.
Features:
- blazing fast, concurrent implementation
- decryption of tokens
- encryption of arbitrary data
- automatic fingerprinting of padding oracles
- automatic detection of cipher block length
- HINTS! if failure occurs during operations, padre will hint you about what can be tweaked to succeed
- supports tokens in GET/POST parameters, Cookies
- flexible specification of encoding rules (base64, hex, etc.)
Usage for padre – Padding Oracle Attack Tool
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 |
Usage: padre [OPTIONS] [INPUT] INPUT: In decrypt mode: encrypted data In encrypt mode: the plaintext to be encrypted If not passed, will read from STDIN NOTE: binary data is always encoded in HTTP. Tweak encoding rules if needed (see options: -e, -r) OPTIONS: -u *required* target URL, use $ character to define token placeholder (if present in URL) -enc Encrypt mode -err Regex pattern, HTTP response bodies will be matched against this to detect padding oracle. Omit to perform automatic fingerprinting -e Encoding to apply to binary data. Supported values: b64 (standard base64) *default* lhex (lowercase hex) -r Additional replacements to apply after encoding binary data. Use odd-length strings, consiting of pairs of characters <OLD><NEW>. Example: If server uses base64, but replaces '/' with '!', '+' with '-', '=' with '~', then use -r "/!+-=~" -cookie Cookie value to be set in HTTP requests. Use $ character to mark token placeholder. -post String data to perform POST requests. Use $ character to mark token placeholder. -ct Content-Type for POST requests. If not specified, Content-Type will be determined automatically. -b Block length used in cipher (use 16 for AES). Omit to perform automatic detection. Supported values: 8 16 *default* 32 -p Number of parallel HTTP connections established to target server [1-256] 30 *default* -proxy HTTP proxy. e.g. use -proxy "http://localhost:8080" for Burp or ZAP |
Impact of padding Oracles
- disclosing encrypted session information
- bypassing authentication
- providing fake tokens that the server will trust
- generally, a broad extension of attack surface
You can download padre here:
Or read more here.