This project was created to play with different IOCs caused by Imageload events.
It leverages ETW to monitor for ImageLoad events and walks the callstack to identify some possible IOCs, such as:
- R(W)X page in callstack
- Stomped module in callstack
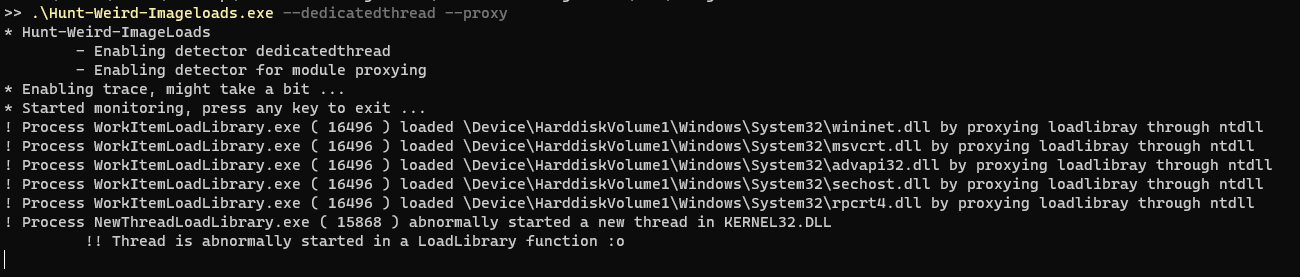
- Module proxying ( ntdll -> kernel32!LoadLibrary ) as described here or here
- New thread dedicated to load a library
There are two sample programs for module proxying and dedicated threads in this repository.
Conclusion
In my tests, I had a lot of false positives monitoring for private or module stomped pages in the callstack and this is probably not a valid IOC.
However, it seems that both, module proxying and dedicated threads are quite abnormal, but see yourself.
Usage
--all activates all alerts
--rx alerts on private rx regions in callstack
--rwx alerts on private rwx regions in callstack
--stomped alerts on stomped modules in callstack
--proxy alerts on abnormal calls to kernel32!loadlibrary from ntdll
--dedicatedthread alerts on thread with baseaddr on loadlibrary*