2023-6-19 23:15:17 Author: lab.wallarm.com(查看原文) 阅读量:34 收藏
This post delves into a very impactful JWT Authentication Bypass vulnerability (CVE-2023-30845) found in ESP-v2, an open-source service proxy that provides API management capabilities using Google Service Infrastructure. This vulnerability allows malicious API clients to bypass JWT authentication through crafty manipulation of the X-HTTP-Method-Override header under specific circumstances.
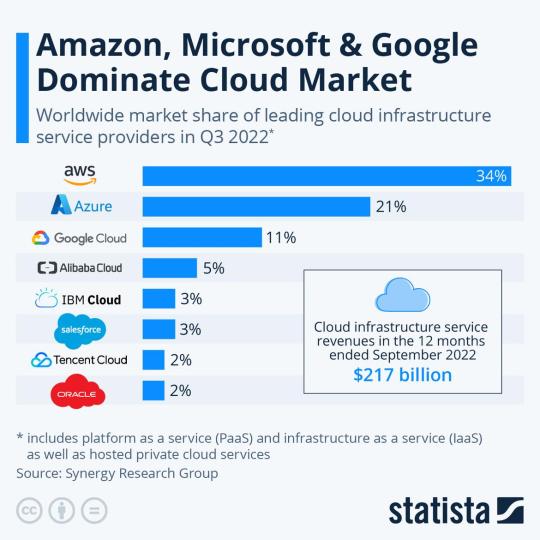
The importance of this issue is highlighted by the significant market share commanded by the Google Cloud Platform (GCP), reported at 11% of the global cloud market in Q3-2022 and growing. The potential impact of this vulnerability thus extends to a considerable number of businesses worldwide that rely on GCP’s services, underscoring the pivotal role of security in software development and the need for swift mitigation actions.
Consequently, the timely resolution of the issue by updating to ESP-v2 v2.43.0 reinforces the importance of proactive security strategies in a rapidly evolving API-driven software and services environment. We argue that organizations need a continuous, anticipatory approach to cybersecurity, and cite this particular vulnerability as an illustration of how even seemingly minor oversights can potentially have widespread ramifications, given the ubiquity and global usage of such platforms.
Technical Exploit Review
We’re going to dissect the CVE-2023-30845 vulnerability, which allows malicious API clients to bypass JSON Web Token (JWT) authentication under certain cases, based on the original advisory published on 2023-Apr-26. This issue was reported by Panagiotis Vasilikos (panagiotisvasilikos) and remediated by Teju Nareddy (nareddyt).
Background
Before delving into the details, let’s understand the basics involved in this exploit.
X-HTTP-Method-Override: This header allows a client to override the HTTP method used in the request. It’s often employed when some HTTP methods are unavailable due to restrictions imposed by firewalls or other intermediaries. For instance, a client can use this header to send a PUT request over a POST, as demonstrated in the code snippet below:
curl --request POST \
--header "X-HTTP-Method-Override: PUT" \
--header "Content-Type: application/json" \
--data '{"username":"xyz"}' \
https://my-endpoint.com/api
JWT Authentication: JWT is a compact, URL-safe means of representing claims to be transferred between two parties. In our case, Google’s ESP-v2 uses JWT authentication for securing API endpoints. When properly implemented, only authenticated users can access these endpoints.
The Vulnerability
This exploit abuses a weakness in how ESP-v2 treats the X-HTTP-Method-Override header in order to bypass JWT authentication. This can happen if:
- The requested HTTP method is not in the API service definition (OpenAPI spec or gRPC google.api.http proto annotations).
- The specified X-HTTP-Method-Override is a valid HTTP method in the API service definition.
For instance, if your API service only accepts POST requests with valid JWT tokens, a malicious client can bypass the authentication by sending a PUT request with the X-HTTP-Method-Override header set to POST.
This is demonstrated in the following attack example:
curl --request PUT \
--header "X-HTTP-Method-Override: POST" \
--header "Content-Type: application/json" \
--data '{"payload":"compromised"}' \
https://url-to-espv2.comAs a result, the malicious client successfully bypasses the authentication, leading to a potential security breach.
How to Remediate
The fix for this issue was implemented in version 2.43.0 of ESP-v2. If you’re using an affected version (from v2.20.0 to v2.42.0), it’s recommended you upgrade to v2.43.0 or higher as soon as possible.
The fixed version still supports the X-HTTP-Method-Override header, but it correctly verifies the JWT authentication, mitigating the vulnerability.
Impact and Severity
GitHub, the CVE Numbering Authority (CNA) in this case, and the National Institute of Standards and Technology (NIST) National Vulnerability Database (NVD) differ in their severity assessment of CVE-2023-30845; here’s how they compare:
| GitHub | NIST NVD | |
| Base Score | 8.2 High | 9.8 Critical |
| Vector | CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:L/A:N | CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H |
| Attack Vector (AV) | Network (accessible over the network) | Network (accessible over the network) |
| Attack Complexity (AC) | Low | Low |
| Privileges Required (PR) | None | None |
| User Interaction (UI) | None | None |
| Scope (S) | Unchanged | Unchanged |
| (potential loss of) Confidentiality (C) | High | High |
| (potential loss of) Integrity (I) | Low | High |
| (potential loss of) Availability (A) | None | High |
Credit
This vulnerability was reported by GitHub user panagiotisvasilikos and remediated by nareddyt.
For the original post and more details, please visit the official security advisory.
The JWT Authentication Bypass Exploit
This high-to-critical severity vulnerability involving JWT authentication bypass via the X-HTTP-Method-Override header highlights an important aspect of API security – that threat actors are continuously exploring new ways to exploit the system. This exploit leverages a custom header manipulation, allowing malicious users to bypass JWT authentication under specific conditions.
This is a stark reminder that we need to remain ever vigilant to the unconventional and the unexpected approaches, in addition to traditional ones, as these can also lead to potential breaches.
Future Predictions
In closing, a couple of thoughts for defenders – and builders – to consider in light of this novel and potentially impactful type of API vulnerability.
Cloud Services, Custom Headers, and JWT Cloud Services
As cloud services continue to grow and evolve, they will not only provide numerous benefits but will also pose many unique security challenges. As more organizations migrate to the cloud, we expect an increase in security incidents related to misconfigurations, data exposures, and inadequate access controls. The added complexity that multi-cloud environments introduce will require an even more comprehensive and integrated security approach.
As demonstrated by this JWT exploit, custom headers can be manipulated to bypass security protocols. Moving forward, we recommend increased scrutiny of these elements within the API infrastructure. More stringent rules around their use and stronger validation mechanisms will be necessary to protect against future exploits.
JWT Issues
Despite their widespread use, JWTs are not immune to security issues. Weak key management, insufficient token validation, and flaws in token expiration handling are just a few potential vulnerabilities. JWT security is likely to continue being a hot topic in the coming years, as threat actors exploit these issues and organizations rush to patch their systems.
如有侵权请联系:admin#unsafe.sh
