2023-7-3 14:30:0 Author: securitycafe.ro(查看原文) 阅读量:35 收藏
1. Overview
In this blog post we will be talking about Command and Control (C&C or C2) Servers and Metasploit’s and Havoc’s role in a C&C Framework. Both can be used as C&C Servers meaning that they can listen for incoming calls from the agents and sends commands to the already compromised systems or devices.
Havoc is a new open source C2 framework that was released in 2022 by 5pider. Researchers say that many threat actors are migrating from paid / cracked versions of Cobalt Strike and Brute Ratel. Being new it still has some bugs, but its functionality surpasses this inconvenient.
Metasploit is another open-source framework created in 2003 by H.D. Moore and was acquired by Rapid7 in 2009 and since then it is one of the most known and wide used frameworks.
Both are post exploitation frameworks that use agents to control the targeted systems and both come with a lot of utilities. Havoc and Metasploit can be used in maintaining persistence on the compromised systems, transfer data, compromise other systems or pivot into other compromised targets with the use of listeners that receive connections from the agents which are located on the compromised hosts.
2. Interface
Havoc has a GUI and doesn’t come with an option to use it with in a Command Line Interface, it is pretty clean as you can see below [ the font can be changed before installing Havoc by modifying the Monaco.setPointSize(9) and Monaco.setPointSize(12) variables in the configuration file under Havoc/Client/Source/Main.cpp ] :

Metasploit comes has both GUI and CLI but I prefer to go for the CLI version as it is simple, reliable and has everything you need.

3. Payload creation and Antivirus detection rates
As the payloads, Metasploit has its own msfvenom tool which is used to generate payloads that can be specific for Metasploit (Meterpreter) or not. Havoc has 3 types of payloads which are generated with Golang and they only work on Windows hosts.
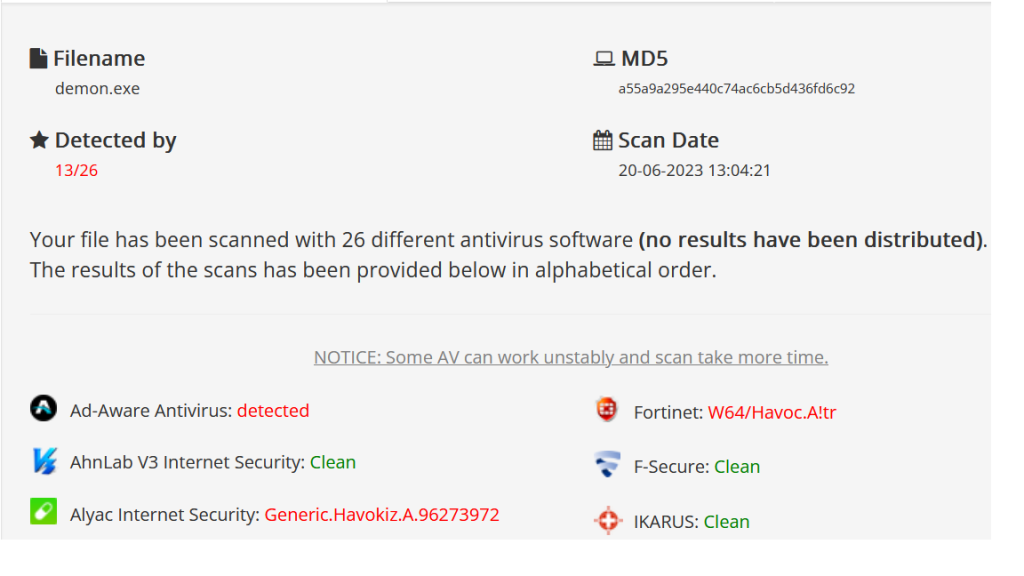
The agent of Havoc called demon has 3 sleep techniques but 2 are worth mentioning because both are encrypted for obfuscation and can reduce the detection rate: Foliage and and Ekko. And as Injection it can be used for x64 or x86 architectures with Native/Syscall or Indirect Syscall. As the format it can be either Windows Exe, Windows Shellcode, DLL and Windows Service Exe. Below you can see the Payload generator and its parameters.

The detection rate of Ekko and Foliage sleep methods with Alloc and Execute set to Native/Syscall or to Win32 had the same detection rate at 13/26 which is not bad.

When it comes to Metasploit, Msfvenom comes with a variety of options and it supports multiple Operating Systems. The more interesting ones are the encrpytion/encoding types: AES256, RC4, XOR. Below you have an example on how to generate a payload that is encrypted with AES256:

Using msfvenom with AES256, RC4 or XOR encryption and meterpreter payload we can see that the detection rate was the same for each and 18/26 Antiviruses discovered it.

4. Scalability
Having the listener up, the agents running. What can we do now?
Here, both Havoc and Metasploit don’t lack the utility, whether you want to extract data, modify, copy or pivot, escalate your privileges and so on. Starting from the basic commands as taking screenshots, listing directories to the more advanced ones on Meterpreter you have the possibility to migrate to another process, do automated privesc etc. and token manipulation/impersonation, dll spawn/injection etc. on Havoc.
So as scalability goes, Havoc has yet to implement a feature. Metasploit can be used to give a single command to many hosts at once. To set the listener to listen for incoming connections you have to use the following command which will make Metasploit to listen as a background process for any incoming connection:
sudo msfconsole -q -x "use exploit/multi/handler; set PAYLOAD <payload>;set LHOST <your IP address>;set LPORT <listening port>;set ExitOnSession false; exploit -j;"

But now let’s say you have way more connections to the Metasploit Server and want to send them the “systeminfo” command. All you need to do is type: sessions -c "systeminfo" -a. This will run the specified command on every agent that is connected to the listener wether it is Windows, Linux or macOS.

But we know the command will only work for Windows instances. What can we do here? Well Metasploit can be customized some more and you can create custom scripts that will send commands based on the Operating System it finds. I won’t go any further on this subject as it is out of the scope on this blog post.
Another critical utility is the working hours utility of Havoc which tells the user to run only between specific hours of the day or to sleep for a determined amount of time (command directly to agent: config workinghours 8:30-17:00) otherwise remaining silent and making no noise. On the other hand, Metasploit has the sleep option (e.g. sleep 20) where you provide the seconds the agent has to sleep and be silent. Those can be crucial in remaining hidden.
5. Conclusion
In the end, whether you choose Havoc or Metasploit as your C2 Server, they both get the job done, both help the user with simple commands and each has a help function whenever you don’t understand one or just want to read more about it. They clearly help in Red Teaming as making it easier to keep track of all the agents and both have common and unique features.
Thank you for reading! Until the next time!
如有侵权请联系:admin#unsafe.sh