2023-7-19 21:12:18 Author: lab.wallarm.com(查看原文) 阅读量:15 收藏
Our Q2-2023 API ThreatStats™ report is out. It provides API builders, defenders, breakers, and decision-makers with a comprehensive look at the API security vulnerabilities, threats and exploits reported this past quarter. This report provides everyone involved in API development, security and strategy with actionable intelligence to strengthen their API security posture.
Download the report to learn how you may be able to improve your API protections. At a high level, we see the API threat landscape evolving rapidly:
- Growing: 514% rise in detected API attacks YoY (Q2-2023 vs. Q2-2022).
- Shifting: 40% of all web attacks were API-related in Q2-2023, compared to 18% in Q2-2022.
- Diversity: 60% rise in unique API attacks QoQ (Q2-2023 vs. Q1-2023).
- Complexity: 6X increase in malicious requests per API attack sequence YoY.
- Pervasive: impacting every corner of the digital world, from NVIDIA and Google to Reddit and Samsung Mobile.
Long-time readers will notice we’re doing something different this time, with more focus on the most significant issues uncovered. This includes:
- Follow the Money. We’ve expanded our coverage to include, for the first time, analysis of bug bounty rewards.
- API Security Razzies. We’ve homed in on the most impactful vulnerabilities and exploits of the quarter.
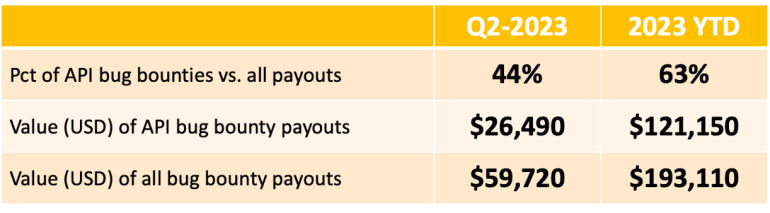
It’s no surprise that we see a continued increase in API vulnerabilities and exploits so far this year. This is borne out by the finding that 63% of all HackerOne bug bounty rewards paid so far this year were for API security problems, with a total of $26,490 being paid out in just the last quarter. Since bounty payments typically lag by 2-3 months, we anticipate an even greater surge in these payments for vulnerabilities reported in Q2.

API Security Razzies: Most Impactful API Vulns & Exploits
As always, we’ve analyzed all published CVEs, security bulletins, and bug bounty reports to bring you the most insightful perspectives on API security. From this analysis, we’ve are selected the most impactful results for Q2-2023 in the following categories:

What’s perhaps most interesting in this past quarter’s findings is how widespread the impacts of API vulnerabilities are. It’s not just public-facing APIs – it’s also partner and internal APIs. And it’s not just software – it’s also firmware and hardware, and even AI infrastructure. The impact is so broad-based that no corner of the enterprise and customer digital world is untouched.
In-Depth Webinar
To learn more, we invite you to attend our upcoming webinar on Thursday, July 27. In this live interactive event, Ivan Novikov, CEO & co-founder of Wallarm and noted security researcher, will take a deep-dive into the latest API vulnerability and exploit data, and discuss the implications to your organizational risk and your cyberdefenses.
Are You Prepared for Ever-Rising API Attacks?
A Deep Dive into the Wallarm Q2-2023 API ThreatStats™ Report
Thursday, July 27, 2023
11:00 PT / 14:00 ET
Final Thought
A year ago, we cited a 2022 Gartner prediction that API abuses would move to the most frequent attack vector. In that same report, they predicted that by 2023, 90% of web-enabled applications will have more surface area for attack in the form of exposed APIs rather than the UI.1
Today, mid-way through 2023, we suggest we’re well on the way to confirming this prediction. Indeed, we project that next quarter we will see API attacks exceed the number of non-API web attacks for the first time ever. Forewarned is forearmed.
Download our latest API ThreatStats™ report to learn where and how your APIs may be at risk.
1 Gartner, Magic Quadrant for Application Security Testing (ID G00733839)
如有侵权请联系:admin#unsafe.sh
