Introduction
In recent weeks, Perception Point researchers have closely been tracking and studying a Brazilian cyber threat group they call “GeoMetrix.” This group is responsible for running various phishing campaigns, mainly targeting individuals in Brazil and Spain. They are also likely profiting off of their phishing tools by selling them to other bad actors. In this blog, we review the key aspects of GeoMetrix’s tactics and operations.
Phishing Campaigns Overview
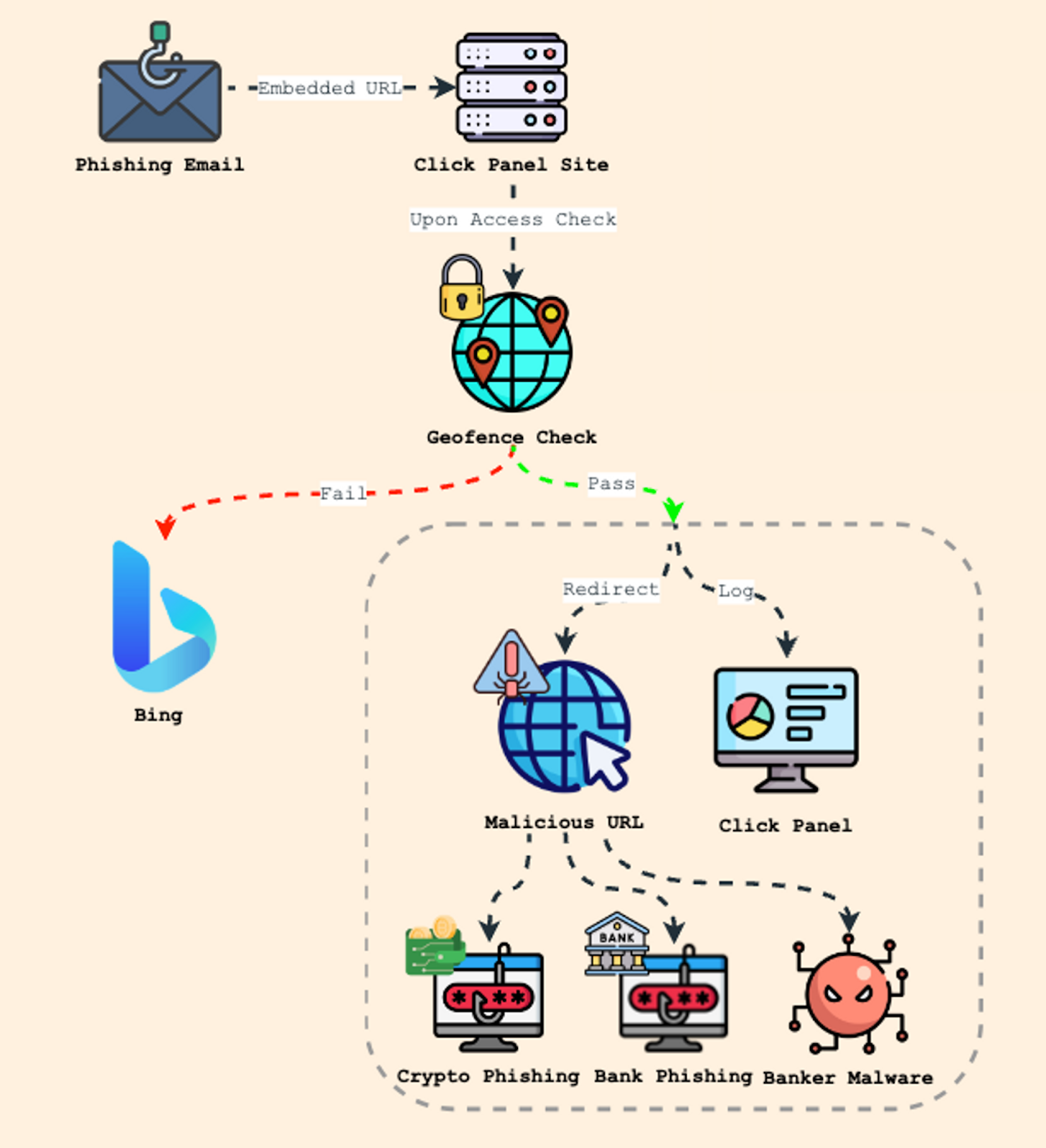
Over the course of July 2023, Perception Point researchers observed an increase in phishing email campaigns crafted in Portuguese and Spanish. These emails are designed to impersonate legitimate Spanish and Brazilian banking institutions. The ultimate goal is to trick unsuspecting users into clicking an embedded link contained within the email:
Once the user clicks on this subtly inserted URL, they are redirected to the threat actor’s control panel site. The site then proceeds to conduct a geolocation scan of the user. If the user’s location aligns with the threat actor’s targeted geography, critical user data – IP address, physical location, and email address – is logged into the attacker’s ‘click panel.’
Following this, the user is further redirected to a malicious URL. This malicious URL conceals one of the following payloads:
- A downloader for banking malware, such as Mekotio, Grandoreiro, or Ousaban.
- A phishing site imitating a LATAM-based bank.
- A fraudulent Trust Wallet phishing site.
The diagram below showcases the execution flow of the campaign:
Panel Overview & Geofence Check
In the course of our in-depth analysis, we identified ten active click panels, each sharing a common structure:
- Login page presented in Portuguese
- Control panel encompassing the following fields:
- Click date
- IP address
- Country
- Region
- City
- Device type
- Host
- Status
- Reset buttons
The geofencing mechanism involves three essential checks:
- User-Agent Check: The server retrieves the user-agent data and cross-references it with a blocklist. (Refer to Appendix 1)
- Hostname Check: Provided the user-agent check is passed, the server then retrieves the user’s host data using the PHP function “gethostbyaddr.” This host data is also compared to a blocklist. (Refer to Appendix 2)
- Geolocation Check: As a final step, assuming the host check is successfully passed, the server sends the user’s IP address to an IP Geolocation API service. The ‘country’ field retrieved from this service is compared to an allowlist.
If the user successfully passes all three checks, their data will be logged on the click panel, and they will be redirected to the malicious URL. If any check fails, the user will be redirected to a benign search engine, like Bing.
Impact of Campaigns
As highlighted earlier, our investigation led to the discovery of ten different click panels, each featuring a ‘success click’ counter (“Liberados”). By aggregating the number of ‘success clicks’ across all panels, we found that the number of infected users has exceeded a staggering 15,000 victims.
Spotlight Campaign – Banco Do Brasil
In our investigation, one campaign stood out in particular, impersonating Banco do Brasil. The email in this campaign was well-crafted, alerting the recipient about a large amount of digital coins due to expire the next day and suggesting that they use them immediately.
This seemingly harmless email led victims to a cleverly designed phishing site, closely resembling Banco do Brasil’s login page.
On the left of this page, users are asked for a key and password. Submitting these details begins a series of phishing steps aimed at stealing personal banking information. But what is perhaps more interesting is the right side of the page, featuring something called a “BB Code.”
The “BB Code” is a feature from Banco do Brasil designed to make money transfers easier and safer. It works by scanning a QR code with any banking app and confirming the transaction on the user’s phone. This then transfers the money to the desired recipient.
The cybercriminals behind the phishing campaign have exploited this feature, using it to trick victims into transferring money directly to them. By making the process seem easy and secure, they have identified a convincing way to steal money from unsuspecting victims.
The Potential Commercial Side of GeoMetrix
Given the array of evidence gathered during our investigation, we are led to speculate that GeoMetrix may be profiting from one of the following business models:
- Phishing-as-a-Service (PhaaS): It is conceivable that GeoMetrix could be offering a service in which customers are charged per successful click, a model reminiscent of Malware-as-a-Service (MaaS), in which providers typically charge per infection. Our conjecture stems from observed repetitive patterns, which have helped identify this potential threat.
- Phishing kit sales: Another possible income source for GeoMetrix could be selling ready-to-use phishing kits. These kits would typically include essentials such as a phishing panel, domain, and a spam target list.
Conclusion
GeoMetrix appears to be more than a mere threat actor. There is a strong possibility that it serves as a platform that enables others to conduct malicious activities, including phishing and malware distribution. This underlines the ever-increasing complexity of the cyber threat landscape and emphasizes the need for enhanced cyber defenses. As we deal with these multidimensional threats, we must continually update our knowledge, improve our defenses, and remain alert to new tactics.
For more information on how to protect your organization against cyber threats, request a demo today.
IOC’s
- IP’s:
- 226.120.168[.]184
- 202.34.109[.]208
- 86.203.178[.]68
- 124.245.72[.]148
- 1.161.178[.]68
- 145.166.205[.]92
- 240.91.74[.]97
- 85.27.205[.]92
- URLs:
- cliente.appoupelainternet[.]com
- recoverymetacustom.z29.web.core.windows[.]net
- recovercustomertrust.z29.web.core.windows[.]net
- brbrasilonline[.]online
- centersjwpoll[.]com
- resgateseguro-seg[.]com
- clientesegurodesco[.]com
- seg-primeparavoce[.]com
Appendixes
Appendix 1 – User-Agent Blocklist
“Googlebot”,”Googlebot-Mobile”,”Googlebot-Image”,”Googlebot-News”,”Googlebot-Video”,”AdsBot-Google([^-]”,”$)”,”AdsBot-Google-Mobile”,”Feedfetcher-Google”,”Mediapartners-Google”,”Mediapartners (Googlebot)”,”APIs-Google”,”bingbot”,”Slurp”,”[wW]get”,”LinkedInBot”,”Python-urllib”,”python-requests”,”libwww-perl”,”httpunit”,”nutch”,”Go-http-client”,”phpcrawl”,”msnbot”,”jyxobot”,”FAST-WebCrawler”,”FAST Enterprise Crawler”,”BIGLOTRON”,”Teoma”,”convera”,”seekbot”,”Gigabot”,”Gigablast”,”exabot”,”ia_archiver”,”GingerCrawler”,”webmon “,”HTTrack”,”grub.org”,”UsineNouvelleCrawler”,”antibot”,”netresearchserver”,”speedy”,”fluffy”,”findlink”,”msrbot”,”panscient”,”yacybot”,”AISearchBot”,”ips-agent”,”tagoobot”,”MJ12bot”,”woriobot”,”yanga”,”buzzbot”,”mlbot”,”YandexBot”,”YandexImages”,”YandexAccessibilityBot”,”YandexMobileBot”,”purebot”,”Linguee Bot”,”CyberPatrol”,”voilabot”,”Baiduspider”,”citeseerxbot”,”spbot”,”twengabot”,”postrank”,”TurnitinBot”,”scribdbot”,”page2rss”,”sitebot”,”linkdex”,”Adidxbot”,”ezooms”,”dotbot”,”Mail.RU_Bot”,”discobot”,”heritrix”,”findthatfile”,”europarchive.org”,”NerdByNature.Bot”,”sistrix crawler”,”Ahrefs(Bot”,”SiteAudit)”,”fuelbot”,”CrunchBot”,”IndeedBot”,”mappydata”,”woobot”,”ZoominfoBot”,”PrivacyAwareBot”,”Multiviewbot”,”SWIMGBot”,”Grobbot”,”eright”,”Apercite”,”semanticbot”,”Aboundex”,”domaincrawler”,”wbsearchbot”,”summify”,”CCBot”,”edisterbot”,”seznambot”,”ec2linkfinder”,”gslfbot”,”aiHitBot”,”intelium_bot”,”facebookexternalhit”,”Yeti”,”RetrevoPageAnalyzer”,”lb-spider”,”Sogou”,”lssbot”,”careerbot”,”wotbox”,”wocbot”,”ichiro”,”DuckDuckBot”,”lssrocketcrawler”,”drupact”,”webcompanycrawler”,”acoonbot”,”openindexspider”,”gnam gnam spider”,”web-archive-net.com.bot”,”backlinkcrawler”,”coccoc”,”integromedb”,”content crawler spider”,”toplistbot”,”it2media-domain-crawler”,”ip-web-crawler.com”,”siteexplorer.info”,”elisabot”,”proximic”,”changedetection”,”arabot”,”WeSEE:Search”,”niki-bot”,”CrystalSemanticsBot”,”rogerbot”,”360Spider”,”psbot”,”InterfaxScanBot”,”CC Metadata Scaper”,”g00g1e.net”,”GrapeshotCrawler”,”urlappendbot”,”brainobot”,”fr-crawler”,”binlar”,”SimpleCrawler”,”Twitterbot”,”cXensebot”,”smtbot”,”bnf.fr_bot”,”A6-Indexer”,”ADmantX”,”Facebot”,”OrangeBot”,”memorybot”,”AdvBot”,”MegaIndex”,”SemanticScholarBot”,”ltx71″,”nerdybot”,”xovibot”,”BUbiNG”,”Qwantify”,”archive.org_bot”,”Applebot”,”TweetmemeBot”,”crawler4j”,”findxbot”,”S[eE][mM]rushBot”,”yoozBot”,”lipperhey”,”Y!J”,”Domain Re-Animator Bot”,”AddThis”,”Screaming Frog SEO Spider”,”MetaURI”,”Scrapy”,”Livelap[bB]ot”,”OpenHoseBot”,”CapsuleChecker”,”[email protected]”,”IstellaBot”,”DeuSu”,”betaBot”,”Cliqzbot”,”MojeekBot”,”netEstate NE Crawler”,”SafeSearch microdata crawler”,”Gluten Free Crawler”,”Sonic”,”Sysomos”,”Trove”,”deadlinkchecker”,”Slack-ImgProxy”,”Embedly”,”RankActiveLinkBot”,”iskanie”,”SafeDNSBot”,”SkypeUriPreview”,”Veoozbot”,”Slackbot”,”redditbot”,”datagnionbot”,”Google-Adwords-Instant”,”adbeat_bot”,”WhatsApp”,”contxbot”,”pinterest.com.bot”,”electricmonk”,”GarlikCrawler”,”BingPreview”,”vebidoobot”,”FemtosearchBot”,”Yahoo Link Preview”,”MetaJobBot”,”DomainStatsBot”,”mindUpBot”,”Daum”,”Jugendschutzprogramm-Crawler”,”Xenu Link Sleuth”,”Pcore-HTTP”,”moatbot”,”KosmioBot”,”pingdom”,”AppInsights”,”PhantomJS”,”Gowikibot”,”PiplBot”,”Discordbot”,”TelegramBot”,”Jetslide”,”newsharecounts”,”James BOT”,”Bark[rR]owler”,”TinEye”,”SocialRankIOBot”,”trendictionbot”,”Ocarinabot”,”epicbot”,”Primalbot”,”DuckDuckGo-Favicons-Bot”,”GnowitNewsbot”,”Leikibot”,”LinkArchiver”,”YaK”,”PaperLiBot”,”Digg Deeper”,”dcrawl”,”Snacktory”,”AndersPinkBot”,”Fyrebot”,”EveryoneSocialBot”,”Mediatoolkitbot”,”Luminator-robots”,”ExtLinksBot”,”SurveyBot”,”NING”,”okhttp”,”Nuzzel”,”omgili”,”PocketParser”,”YisouSpider”,”um-LN”,”ToutiaoSpider”,”MuckRack”,”Jamie’s Spider”,”AHC”,”NetcraftSurveyAgent”,”Laserlikebot”,”^Apache-HttpClient”,”AppEngine-Google”,”Jetty”,”Upflow”,”Thinklab”,”Traackr.com”,”Twurly”,”Mastodon”,”http_get”,”DnyzBot”,”botify”,”007ac9 Crawler”,”BehloolBot”,”BrandVerity”,”check_http”,”BDCbot”,”ZumBot”,”EZID”,”ICC-Crawler”,”ArchiveBot”,”^LCC “,”filterdb.iss.netcrawler”,”BLP_bbot”,”BomboraBot”,”Buck”,”Companybook-Crawler”,”Genieo”,”magpie-crawler”,”MeltwaterNews”,”Moreover”,”newspaper”,”ScoutJet”,”(^”,” )sentry”,”StorygizeBot”,”UptimeRobot”,”OutclicksBot”,”seoscanners”,”Hatena”,”Google Web Preview”,”MauiBot”,”AlphaBot”,”SBL-BOT”,”IAS crawler”,”adscanner”,”Netvibes”,”acapbot”,”Baidu-YunGuanCe”,”bitlybot”,”blogmuraBot”,”Bot.AraTurka.com”,”bot-pge.chlooe.com”,”BoxcarBot”,”BTWebClient”,”ContextAd Bot”,”Digincore bot”,”Disqus”,”Feedly”,”Fetch”,”Fever”,”Flamingo_SearchEngine”,”FlipboardProxy”,”g2reader-bot”,”G2 Web Services”,”imrbot”,”K7MLWCBot”,”Kemvibot”,”Landau-Media-Spider”,”linkapediabot”,”vkShare”,”Siteimprove.com”,”BLEXBot”,”DareBoost”,”ZuperlistBot”,”Miniflux”,”Feedspot”,”Diffbot”,”SEOkicks”,”tracemyfile”,”Nimbostratus-Bot”,”zgrab”,”PR-CY.RU”,”AdsTxtCrawler”,”Datafeedwatch”,”Zabbix”,”TangibleeBot”,”google-xrawler”,”axios”,”Amazon CloudFront”,”Pulsepoint”,”CloudFlare-AlwaysOnline”,”Google-Structured-Data-Testing-Tool”,”WordupInfoSearch”,”WebDataStats”,”HttpUrlConnection”,”Seekport Crawler”,”ZoomBot”,”VelenPublicWebCrawler”,”MoodleBot”,”jpg-newsbot”,”outbrain”,”W3C_Validator”,”Validator.nu”,”W3C-checklink”,”W3C-mobileOK”,”W3C_I18n-Checker”,”FeedValidator”,”W3C_CSS_Validator”,”W3C_Unicorn”,”Google-PhysicalWeb”,”Blackboard”,”ICBot”,”BazQux”,”Twingly”,”Rivva”,”Experibot”,”awesomecrawler”,”Dataprovider.com”,”GroupHigh”,”theoldreader.com”,”AnyEvent”,”Uptimebot.org”,”Nmap Scripting Engine”,”2ip.ru”,”Clickagy”,”Caliperbot”,”MBCrawler”,”online-webceo-bot”,”B2B Bot”,”AddSearchBot”,”Google Favicon”,”HubSpot”,”Chrome-Lighthouse”,”HeadlessChrome”,”CheckMarkNetwork”,”www.uptime.com”,”Streamline3Bot”,”serpstatbot”,”MixnodeCache”,”^curl”,”SimpleScraper”,”RSSingBot”,”Jooblebot”,”fedoraplanet”,”Friendica”,”NextCloud”,”Tiny Tiny RSS”,”RegionStuttgartBot”,”Bytespider”,”Datanyze”,”Google-Site-Verification”
Appendix 2 – Hostname Blocklist
“.tor.”,”123planosdesaude”,”VAULTVPN”,”activescan”,”alpha2″,”amazon”,”ancombraterney”,”anti-phishing”,”antipishing”,”antispam”,”antivirus”,”avast”,”bancopastor”,”bancopopular”,”banesto”,”bankofamerica”,”barracuda”,”bb.com.br”,”bitdefender”,”bradesco”,”cajamadrid”,”chicago “,”cia.gov”,”clamav”,”clamwin”,”cleandir”,”colocrossing”,”coloup”,”consumer”,”copel”,”customer”,”datapacket”,”delitosinformaticos”,”detector”,”dimenoc”,”dnblead”,”donategrid”,”dufrio”,”easysol”,”ebay.com”,”eset”,”eveocloud”,”f-secure”,”fasano”,”fbi.gov”,”fraudwatchinternational”,”free-av”,”gfihispana”,”greenmountainaccess”,”grisoft”,”hands”,”hauri-la”,”hispasec”,”instantcheckmain”,”itau”,”iwgroup”,”kapersky”,”laarnes”,”letti”,”linode”,”mailcontrol”,”mailstream”,”mallshill”,”marimex”,”mcafee”,”mgconecta”,”microsoft.com”,”midphase”,”monitor”,”movistar”,”msn.com”,”nephosdns”,”netcraft.com”,”nod32″,”norton”,”offerzz1″,”onlinedc”,”opendns”,”owned-networks”,”panda.com”,”pandasoftware”,”paypal”,”phish”,”pish”,”prcdn”,”protectedgroup”,”quadranet”,”rodobens.com.br”,”rsa.com”,”rsghosting”,”sajonaramail”,”santander”,”scaleway”,”scotiabank”,”security”,”seguridad”,”sescsp”,”sophos”,”spamfirewall2″,”spfbl”,”symantec”,”thinins”,”trendmicro”,”trustwave”,”unicaja”,”utfpr.edu.br”,”verisign”,”veritas”,”viabcp”,”vnunet”,”vodafone”,”vultr”,”wbinfo”,”webandseo “,”zonealarm”,”.tor.”,”123planosdesaude”,”VAULTVPN”,”activescan”,”alpha2″,”amazon”,”ancombraterney”,”anti-phishing”,”antipishing”,”antispam”,”antivirus”,”avast”,”bancopastor”,”bancopopular”,”banesto”,”bankofamerica”,”barracuda”,”bb.com.br”,”bitdefender”,”bradesco”,”cajamadrid”,”chicago “,”cia.gov”,”clamav”,”clamwin”,”cleandir”,”colocrossing”,”coloup”,”consumer”,”copel”,”customer”,”datapacket”,”delitosinformaticos”,”detector”,”dimenoc”,”dnblead”,”donategrid”,”dufrio”,”easysol”,”ebay.com”,”eset”,”eveocloud”,”f-secure”,”fasano”,”fbi.gov”,”fraudwatchinternational”,”free-av”,”gfihispana”,”google”,”greenmountainaccess”,”grisoft”,”hands”,”hauri-la”,”hispasec”,”instantcheckmain”,”itau”,”iwgroup”,”kapersky”,”laarnes”,”letti”,”linode”,”mailcontrol”,”mailstream”,”mallshill”,”marimex”,”mcafee”,”mgconecta”,”microsoft.com”,”midphase”,”monitor”,”movistar”,”msn.com”,”nephosdns”,”netcraft.com”,”nod32″,”norton”,”offerzz1″,”onlinedc”,”opendns”,”owned-networks”,”panda.com”,”pandasoftware”,”paypal”,”phish”,”pish”,”prcdn”,”protectedgroup”,”quadranet”,”rodobens.com.br”,”rsa.com”,”rsghosting”,”sajonaramail”,”santander”,”scaleway”,”scotiabank”,”security”,”seguridad”,”sescsp”,”sophos”,”spamfirewall2″,”spfbl”,”symantec”,”thinins”,”trendmicro”,”trustwave”,”unicaja”,”utfpr.edu.br”,”verisign”,”veritas”,”viabcp”,”vnunet”,”vodafone”,”vultr”,”wbinfo”,”webandseo “,”zonealarm”,”vcarefilter”,”dovaleseguros”,”dedini”,”penso”,”unimedfortaleza”,”alfa”,”kiaautovale”,”mail.ale”,”barracuda.penso”,”mx.lubeck”,”datacoper”,”tcu.gov.br”,”gdh.tbi”,”dbz.ce”,”lubeck”,”citroenpremiere”,”eucatex”,”carburgo”,”fieam”,”uniparcarbocloro”,”sysbrasil”,”braspor”,”relay.eb.mil.br”,”elojasbecker”,”ferragensnegrao”,”grupogmaes”,”eb”,”luzsp”,”midiaon”,”gegnet”,”lojasbesni”
如有侵权请联系:admin#unsafe.sh