2023-7-25 21:14:55 Author: www.sentinelone.com(查看原文) 阅读量:23 收藏
Earlier this month, security researcher iamdeadlyz reported on multiple fake blockchain games being used to infect both Windows and macOS targets with infostealers, capable of emptying crypto wallets and stealing stored password and browser data.
In the case of macOS, the infostealer turned out to be a new malware written in Rust, dubbed “realst”. Building on this previous analysis, we identified and analyzed 59 malicious Mach-O samples of realst malware. Among those, we discovered some samples are already targeting Apple’s forthcoming OS release, macOS 14 Sonoma.
In this post, we describe the malware in detail to help threat hunters and security teams identify and detect compromises by Realst Infostealer.

Realst Distribution
Realst Infostealer is distributed via malicious websites advertising fake blockchain games with names such as Brawl Earth, WildWorld, Dawnland, Destruction, Evolion, Pearl, Olymp of Reptiles, and SaintLegend. The campaign appears to have links to the earlier PearlLand infostealer. Each version of the fake blockchain game is hosted on its own website complete with associated Twitter and Discord accounts.
As reported by iamdeadlyz, threat actors have been observed approaching potential victims through direct messages on social media.
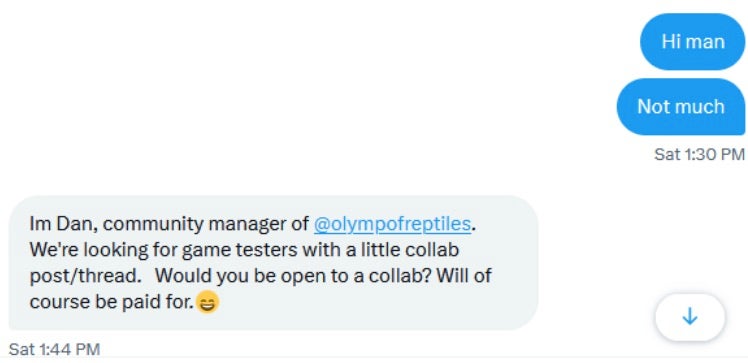
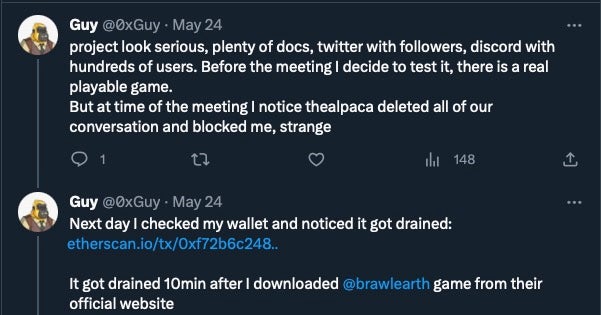
Individuals who fell for the lures soon found that they had become victims of theft.
Realst Malicious Installers
Some versions of the malware are distributed by a .pkg installer containing a malicious Mach-O and three related scripts.
The Python script game.py is a cross-platform Firefox infostealer. No actual game is contained here or elsewhere.
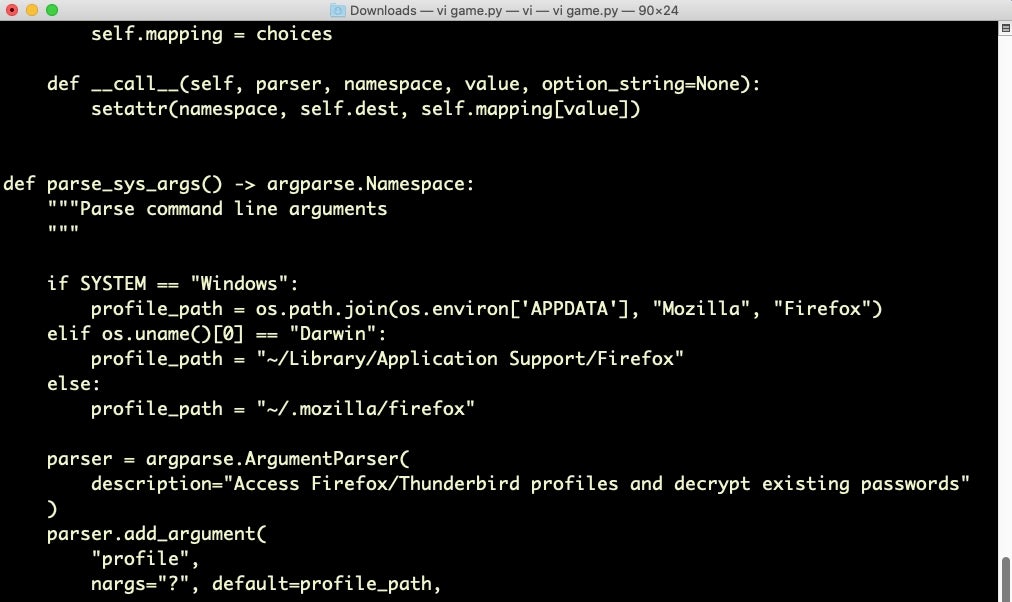
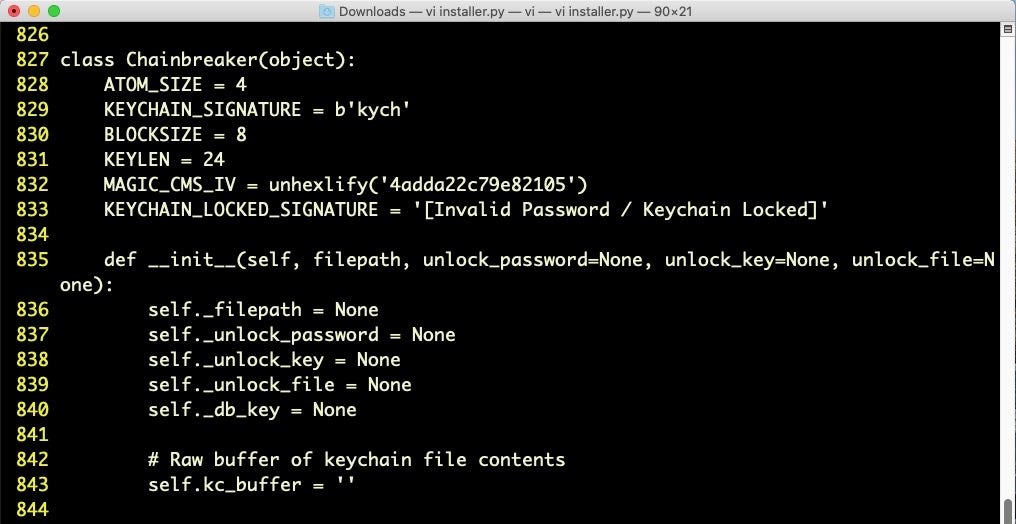
The installer.py script is in fact a copy of chainbreaker, an open-source project for extracting passwords, keys and certificates from a macOS keychain database. Given the user’s password scraped earlier in the execution chain, chainbreaker will retrieve plaintext versions of the user’s internet account and other stored passwords.
Surprisingly, the uninstall.sh script is simply a barebones uninstall script with no malicious behavior.
Other versions of realst stealer are distributed as applications via .dmg disk images. In some cases the developer has packaged the malware in Electron apps; in others, native macOS application bundles are used. The previous research provides an in-depth description of these.
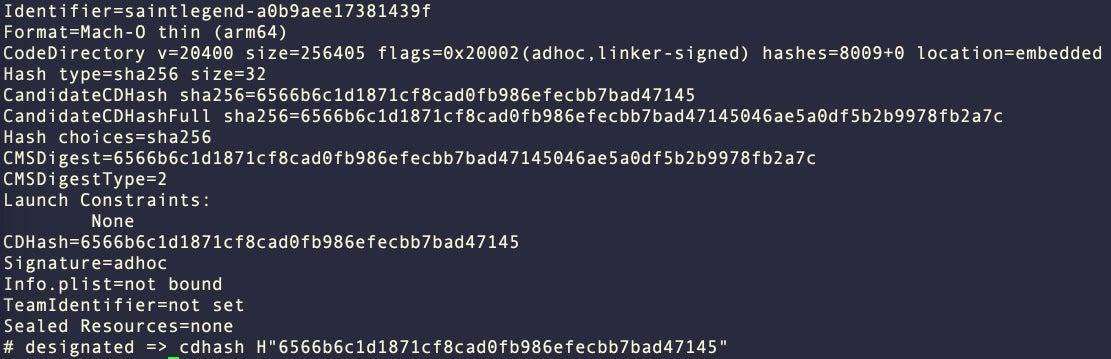
Some samples were codesigned with Apple Developer ID (Team Identifier: C46287MB25), which has since been revoked.
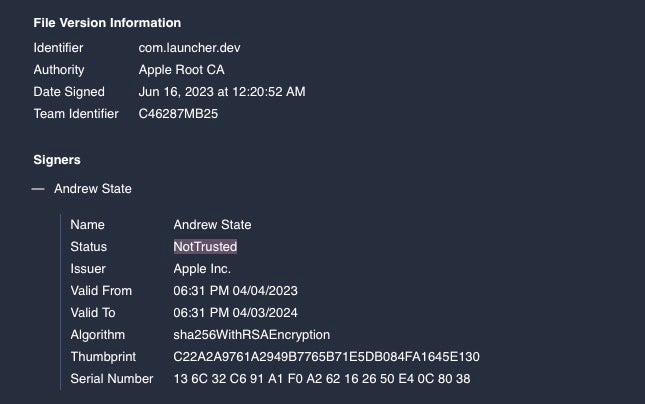
Other samples are ad-hoc codesigned and will continue to launch, as such signatures cannot be revoked remotely.
Dynamic Analysis of Realst Variants
Behaviorally, realst samples look fairly similar across variants and are readily detectable in much the same way as other macOS infostealers. Although they at times use different API calls and have some variant dependencies, from a telemetry point of view the key to all these infostealers is the access and exfiltration of browser data, crypto wallets, and keychain databases.
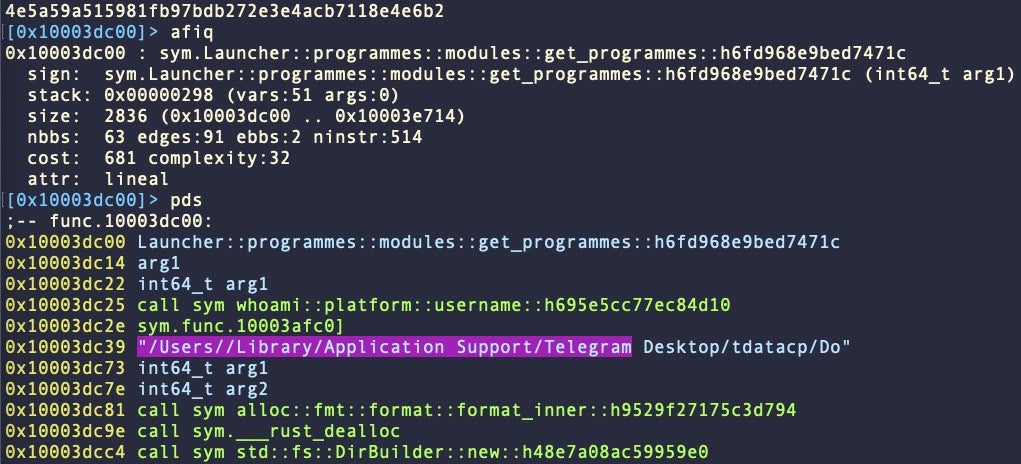
Targeted browsers include Firefox, Chrome, Opera, Brave and Vivaldi. Safari was not targeted in any of the samples we analyzed. We also note that the malware targets the Telegram application.
The samples we analyzed reach out to one of two hardcoded URLs to exfiltrate stolen data:
http://167[.]172[.]103[.]83:8080/opened http://77[.]91[.]84[.]110:5000/send_analytics
Most variants (see below for further details) attempt to grab the user’s password via osascript and AppleScript spoofing and perform rudimentary checking that the host device is not a virtual machine via sysctl -n hw.model. We explore these differences in detail in the static analysis section below.
Collected data is dropped in a folder simply named “data”. This may appear in one of several locations depending on the version of the malware: in the user’s home folder, in the working directory of the malware , or in a folder named after the parent game, e.g.,
~/data/ ~/data.zip ~/Downloads/brawl/data/ ~/Downloads/brawl/data.zip
If the malware was able to access screen capture permission, a screenshot of the Desktop is also taken and deposited in the same location.
~/screenshot.jpeg ~/Downloads/brawl/screenshot.jpeg
Static Analyses of Realst Variants
Our analysis identified 16 variants across 59 samples, which we divide into four major families: A, B, C and D. The division is somewhat arbitrary: There are a number of overlaps that would allow us to draw the lines differently (for example, the use or lack of pycryptodome, or the targeting of macOS Sonoma). We chose the following taxonomy based on string artifacts that should aid threat hunters in better identification and detection.
Realst Variant Family A
Of the 59 Mach-O samples we analyzed, 26 fall into Variant A. This variant has a number of sub variants (we noted ten), but they all share one defining characteristic which isn’t found in Variants B, C and D: The inclusion of whole strings related to AppleScript spoofing.
Example SHA1: 144665cb2e5d65c88579aa4391cebbc116842536 0x752f16:: osascript 0x752f21: display dialog 0x752fb7: with hidden answer 0x7511dc: keychain-db 0x751238: dump-generic-passwords 0x1c75e13: FireFoxDecryptor 0x19444a1: hw.model
Family A variants use AppleScript spoofing in much the same way that we have seen earlier macOS stealers use to grab the user’s admin password in plaintext. This technique involves popping a password request dialog box with the “hidden answer” option. This prevents the user seeing the characters they type by replacing them with bullet points, similar to a real password dialog. The important difference being, however, that in this case the password is only obscured from the user themselves. The password is captured and logged in clear text by the AppleScript dialog box.
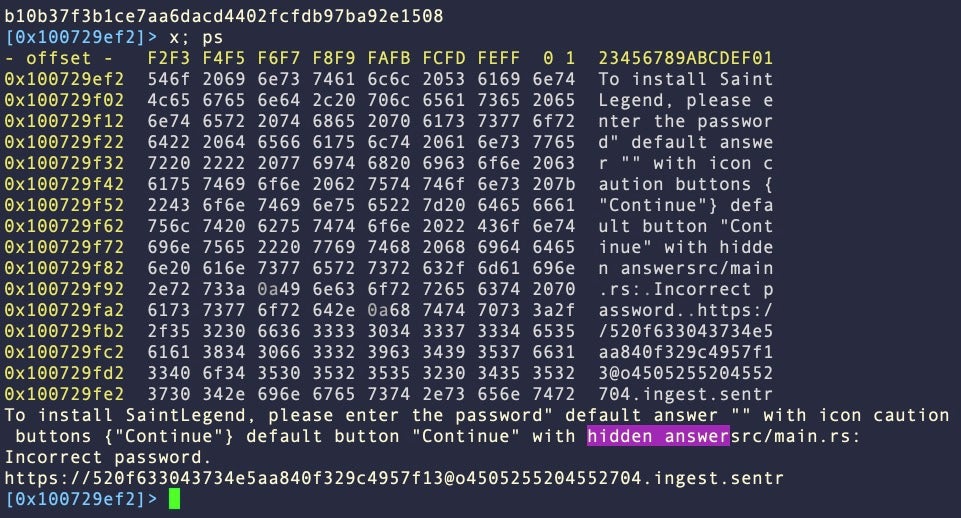
Like other variants, A samples also include full strings related to anti-analysis through VM detection in the form of hw.model. This is used as an argument to the sysctl command to determine the model of the host device. When run on a Virtual Machine, a macOS instance will typically return the name of the VM software as opposed to the model of Mac.
Realst Variant Family B
Family B variants also have static artifacts related to password spoofing, but these samples are distinctive as they break up the strings into smaller units as a means to evade simple static detection. We found 10/59 samples fell into this category.
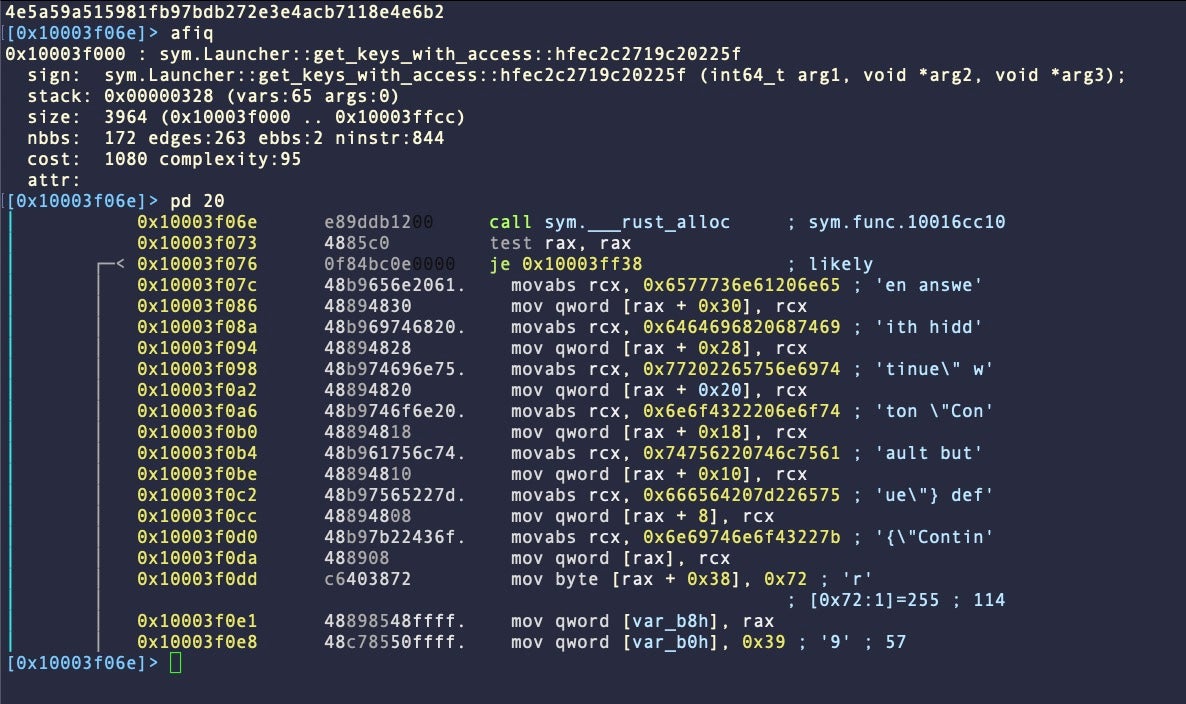
Otherwise, B variants have similar artifacts to Variant A samples.
Example SHA1: 2d89ffbadddd62483bc2be33e296ce4e6036c45b 0x6940a0: display dialog 0x6b08f3: keychain-db 0x6b094f: dump-generic-passwords 0x6b52cb: hw.model 0x9b8b69: FireFoxDecryptor
Realst Variant Family C
Family C also attempts to hide the strings for AppleScript spoofing by breaking up the strings in the same way as Variant B. However, Variant C is distinctive in that it introduces a reference to chainbreaker within the Mach-O binary itself. 7/59 samples fell into this category.
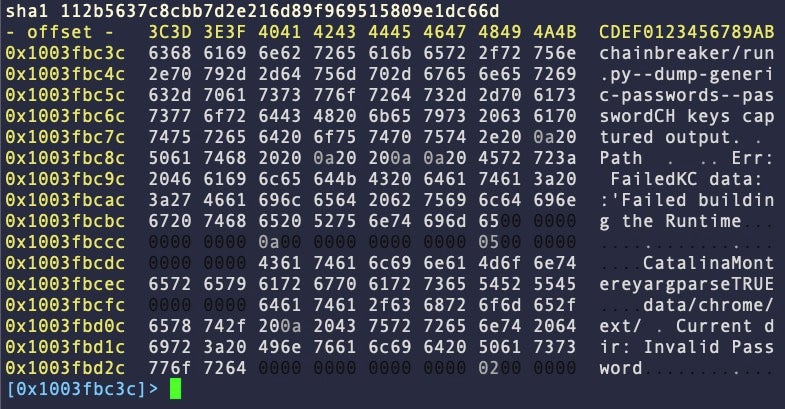
SHA1: 112b5637c8cbb7d2e216d89f969515809e1dc66d 0x3fbc10: keychain-db 0x3fbc3c: chainbreaker 0x3fbc51: dump-generic-passwords 0x628e4f: FireFoxDecryptor 0x402552: hw.model
Realst Variant Family D
In Family D, which accounted for 16/59 samples, there are no static artifacts for osascript spoofing. Password scraping is handled by a prompt in the Terminal window via the get_keys_with_access function. Once the password is acquired it is immediately passed to sym.realst::utils::get_kc_keys, which then attempts to dump passwords from the Keychain.
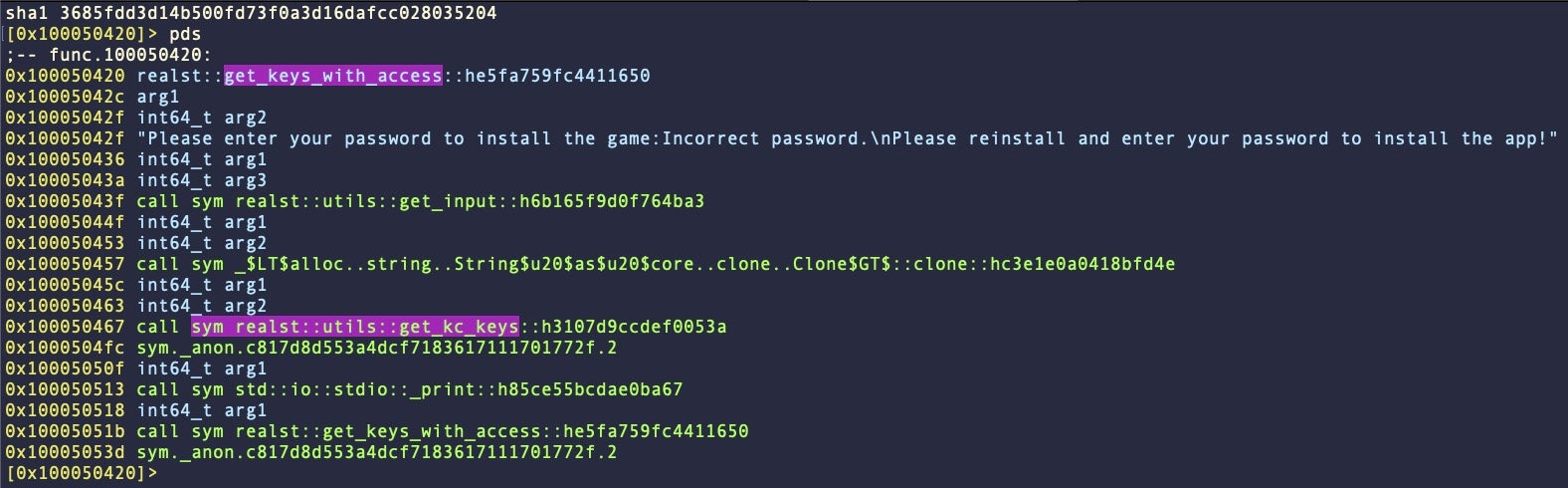
In some versions, the malware also uses the scraped password to elevate privileges with the sudo command and install the Python pycryptodome package.
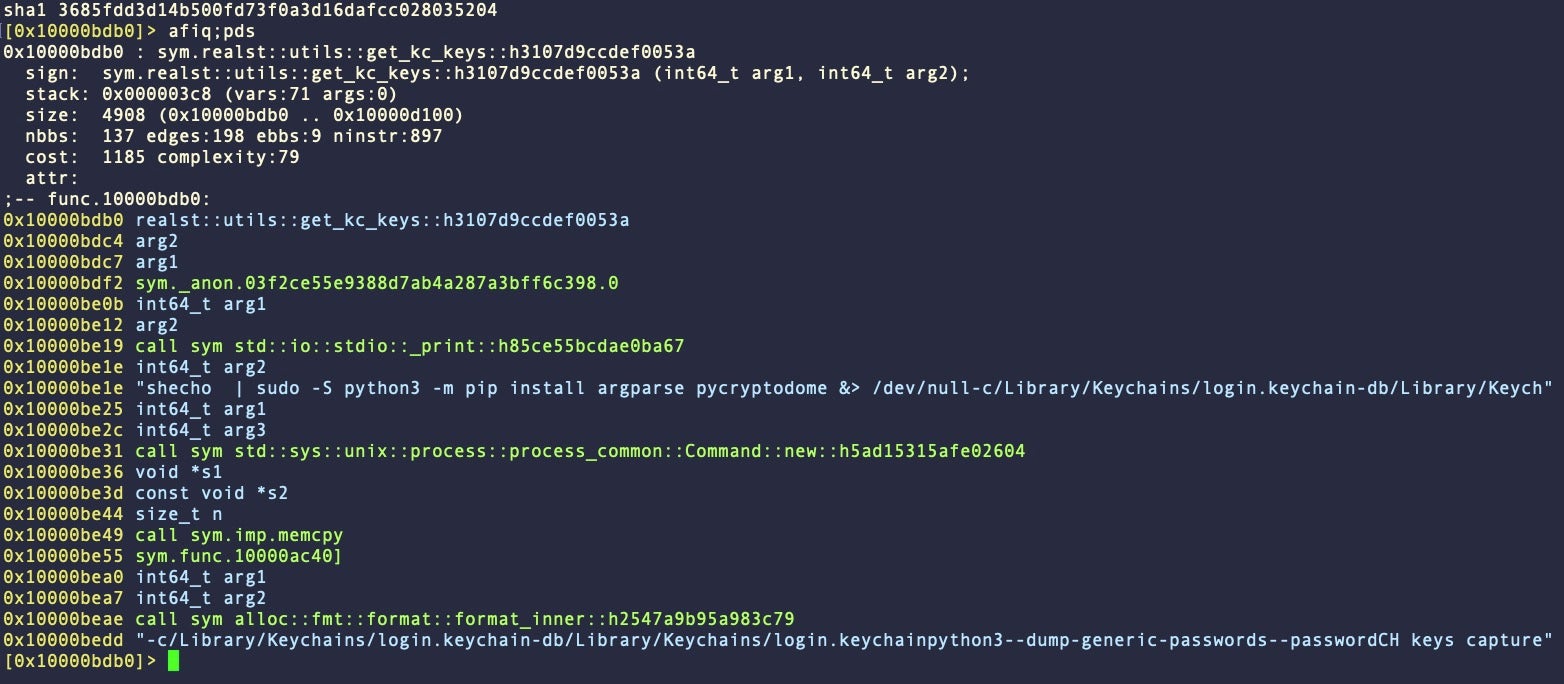
The use of pycryptodome is itself inconsistent across samples and families, appearing in around half of the entire collection.
SHA1: d436de35164a045e3c0f7b51cf41fcefedf7e77d 0x3fbc10: keychain-db 0x3fbc47: dump-generic-passwords 0x402542: hw.model 0x628de2: FireFoxDecryptor
Realst Infostealer Prepares for macOS 14 Sonoma
About a third of the samples we identified contain strings targeting macOS 14 Sonoma. These string artifacts appear in around half of Variant A samples, and all of Variant B samples. None of Variants C or D were found to contain Sonoma strings.
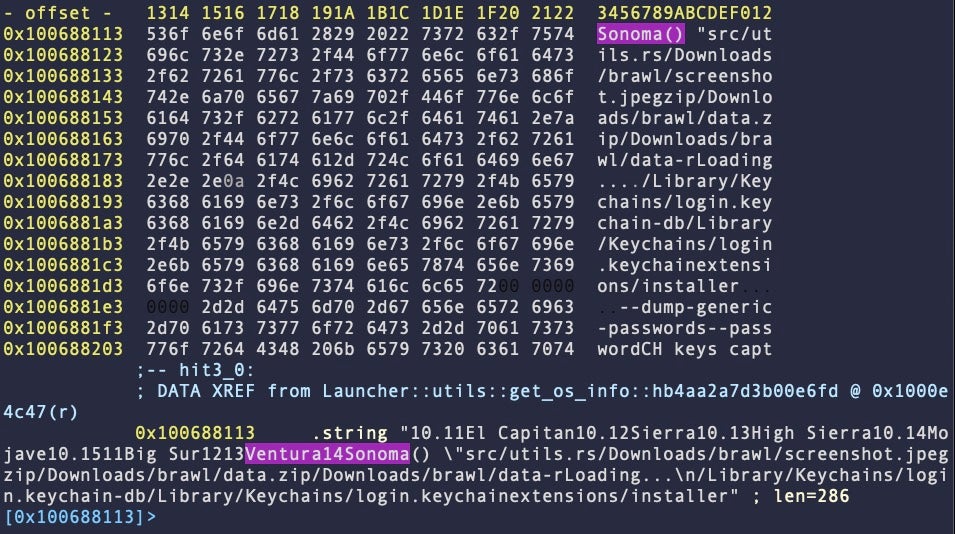
It is not clear at this point how differences between Sonoma and Ventura would affect execution of the malware – a question it seems the malware authors are themselves seeking to determine.
SentinelOne Protects Against Realst Infostealer
All known variants of Realst macOS infostealer are detected and, where the ‘Prevent’ site policy is enabled, prevented from execution by the SentinelOne agent. Apple’s malware blocking service “XProtect” does not appear to prevent execution of this malware at the time of writing.
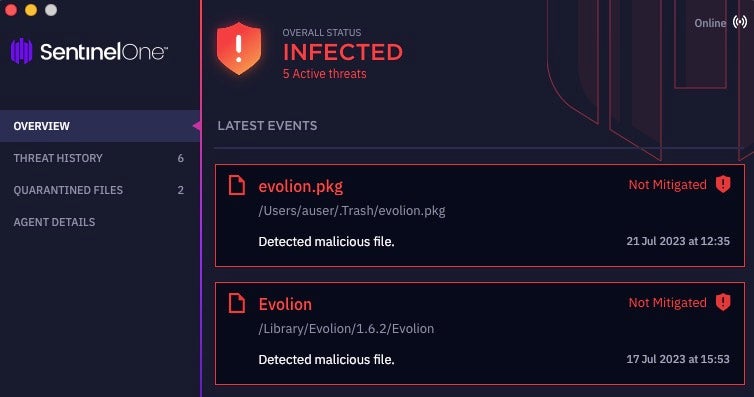
Organizations not protected by SentinelOne may use the comprehensive indicators provided in this post to aid threat hunting and detection.
Conclusion
The number of Realst samples and their variation shows that the threat actor has invested serious effort in order to target macOS users for data and crypto wallet theft. Multiple fake game sites complete with Discord servers and associated Twitter accounts have been created to present the illusion of genuine products and convince users to try them out. As soon as the victim launches these fake games and provides the “installer” with a password, their data, passwords and crypto wallets are stolen.
Given the current popular interest in blockchain games, which promise users the reward of making money while gaming, users and security teams are urged to treat solicitations to download and run such games with extreme caution.
Indicators of Compromise
Communications
77.91.84[.]110
167.172.103[.]83
Team Identifier
C46287MB25
Bundle Identifier
com.launcher.dev
Observed MITRE TTPs
T1033 System Owner/User Discovery (whoami)
T1059 Command and Scripting Interpreter (osascript)
T1070.004 File Deletion (rmdir)
T1082 System Information Discovery (sw_vers)
T1083 File and Directory Discovery (dirname, basename)
T1553 Bypass or Subvert Trust Controls (xattr)
T1620 Reflective Code Loading (execv, fork)
T1562 Disable or Modify Tools (sleep, waitpid)
T1639.001 Exfiltration Over Unencrypted Non-C2 Protocol (tcp, http)
Mach-O Files SHA1
Family Variant A1
44aa30ca902a22520b52789b81add44e15e74a50
713cdae1bc6c68c06d3b9cc18171b5de43957f98
859e5b3d534c8282d168ebe40c127576dc0b9c70
8d60062ad8a29b4e88c7b9ec3b649aa30476001f
A2
963f55a93523c001fdec52ff33ff232e020135e5
A3
89e1cfc0fa65e4369279b78a26837e6259d4800c
A4
144665cb2e5d65c88579aa4391cebbc116842536
56a0b37302829d5fb116d8aa5700dcc3af00dc34
5da136f267dc70447d420b28dee729d32fdf437f
6cb07664ef882f7cb98f017b0fbdffe4946e9161
b10b37f3b1ce7aa6dacd4402fcfdb97ba92e1508
b898723602c96ecd04176bd13e6c21dbea82e6de
faf6b11a137bf7ae0ffcab411b02e0c0905260b6
A5
091f960fe4317696fb30abc3b36d2c8a7eef4b65
0eeb66a08ca067f168779be8b22da25f90fe4f51
88880772b0f8723020e0feb2bb179dc71e482072
A6
6ee0d99e3a56a72c60f3da790268286cd1e7a3ab
A7
60a747b3e8a25b885ccd16945ba1a238a66e4439
8054b51a51c8c8f21fe4c51322ef36a9fa02b570
b8ac89eed011c0a4e5f4973acbee888323ec80f0
efccafe8cf2a7d63f82c69882195a565fbd60720
A8
39060bb82061c5d426d4a7bad66e07888b05b354
b1aac3888403f4597d9cf14b505f572b2fe7d485
d890822af137df48a91f4ba47a27272dcacc9920
A9
630b23a57d2d8e6d8e25c346173191af6273c3ab
A10
087b3bf372928279d547fb6bb0ab656717fa8c4b
Family Variant B1
0a2a853251fe28333761cc6f9c4518807354dd27
13bdb3823b8555d846f17bdf381f9568b9a81d26
29a7eefff22156a72577ed920eaf9b903e9f164a
2d89ffbadddd62483bc2be33e296ce4e6036c45b
4e5a59a515981fb97bdb272e3e4acb7118e4e6b2
9719fd9415d438722f94877c55c9495708c64fee
c205d4ba044f2d69500f10a46c31aaf068e32c44
c716a02e3bc8603fcf0bb8d63fc4f7e3afab471d
dadfbd13b7bd0e9b6d87ebae30bc48c2eeae0eb3
B2
09e8672af5e18ce99ad8ae608cdc0fa229f121f0
Family Variant C1
112b5637c8cbb7d2e216d89f969515809e1dc66d
C2
154909cdd261130b0ed6d603d4727cb9f15ddc36
247c50d19e7ad18f466558f9c1785ef29962ab7c
32f06e3e9d8899f5224f3d5538724d132bda0921
68dc1f80064f6c261e587cdbb2f01677c8f2e14a
8b4cdd02330cf25f4e1d338b91ffd1c1dd87021a
ce42d202446cc6b316f668a072c17df87dcd495c
Family Variant D1
2f61ddd391d23a6665fa326629e004cb380c4f85
38ae4fa8f4fec9ab98c0003c455016464b62acce
65c175f5fad31ea1c938a96a9cdc9987413fd1f2
80483c5c95ed92da6f086e9497cd08cf7d3b7658
c4296e1a67545e50f44c3776adb674ea1d4d4c0e
d436de35164a045e3c0f7b51cf41fcefedf7e77d
f097123a1999a656a368114abbd848b68d523ee0
D2
158cf7a0c89544ce1c3294453be2a8c8ced9c9b0
294392bcf166953c552443fe95ba1e8f15487f74
294bfc9b97092904bb5e216531b184e38fb2c11f
3685fdd3d14b500fd73f0a3d16dafcc028035204
4053e0ecf5f59b6f7afc06750551d77e131ebd2d
410e4e24f6f6c4f29c8a75723f84bf60ff96c2d5
ada7a47b7fecb142ff532c6e0f01a89bcb47afc9
bfac1b17ad79719c4602a2142435f02c529ec4ab
db9fe7ba9ff8771d28a2fa504d84059faab6be5b
如有侵权请联系:admin#unsafe.sh