2023-8-2 15:59:48 Author: blog.elcomsoft.com(查看原文) 阅读量:40 收藏
When it comes to iOS data acquisition, Elcomsoft iOS Forensic Toolkit is the top choice for forensic experts. Its cutting-edge features and unmatched capabilities have made it the go-to software for investigating iOS devices. In a recent update, we expanded the capabilities of the low-level extraction agent to support full file system extraction and keychain decryption on Apple’s newest devices running iOS 16.5. This achievement represents a breakthrough, as the delay between Apple’s iOS updates and our forensic software release has significantly reduced.
Introduction
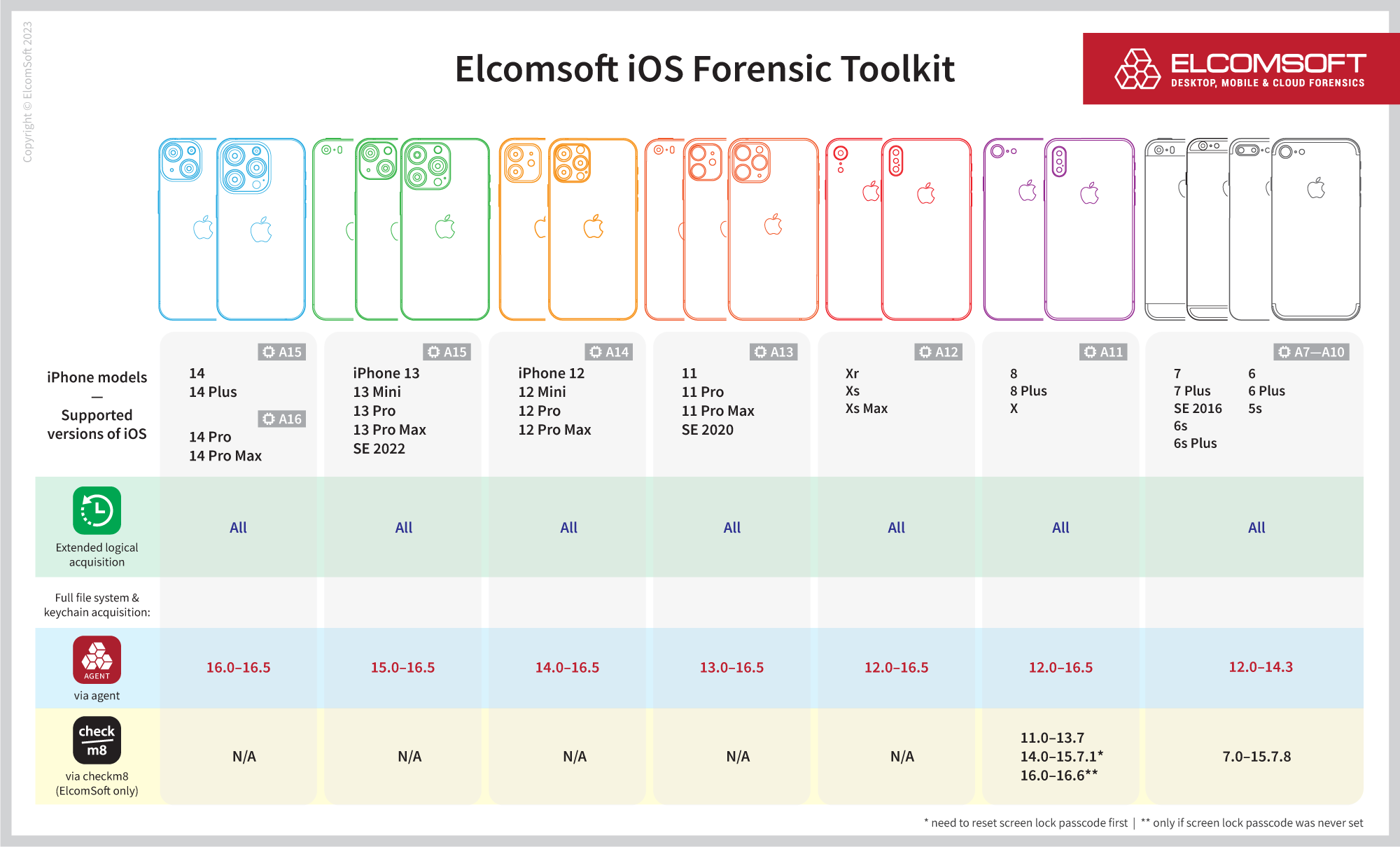
Agent-based extraction is an advanced “consent extraction” method used to obtain the complete file system and keychain data from modern iOS and iPadOS devices, namely iPhones and iPads. “Consent extraction” is a term meaning that it can only be used when the device passcode is known or not set. Although agent extraction may not be considered completely “forensically sound” like the acquisition method based on the bootloader exploit, it stands as the sole available technique for the latest Apple devices equipped with A12-A16 Bionic and M1/M2 SoC, and even remains the only working extraction technique for A11 devices (iPhone 8/8 Plus/iPhone X) running iOS 16, for which bootloader-based methods fail. By employing agent-based extraction, investigators can retrieve the maximum amount of data, making it a valuable source of forensic evidence.
The Low-Level Extraction Agent
The low-level extraction agent is what sets iOS Forensic Toolkit apart. We have already established ourselves as pioneers in checkm8 extractions, extended support to various Apple devices, and introduced low-level extraction support for Apple M1 and M2 chip-based iPad models. Previously, our tool could extract the full file system image and decrypt the keychain from supported devices running iOS releases up to and including iOS 16.4; for some devices, the latest supported version of iOS was even older. Now, with full file system extraction and keychain decryption support for the same range of devices, we expanded OS version support all the way up to iOS 16.5 for devices based on Apple A11 Bionic and newer chips, up to and including the M1 and M2.
Investigators can now access crucial evidence in the latest Apple devices running relatively recent versions of iOS, including the contents of apps’ sandboxes, system data, and important online account passwords, shedding light on users’ digital activities. In addition to passwords, the keychain stores crucial keys required to unlock protected chat histories from messaging applications like Signal.
The current support matrix includes iOS 16.5 and beyond, and our development team is actively working to support upcoming iOS versions. Elcomsoft iOS Forensic Toolkit remains at the forefront of iOS forensic tools, continuously evolving to meet the demands of the ever-changing landscape.
A Major Achievement makes for a Breakthrough in Mobile Forensics
Apple is known for its dedication to security and regularly patches iOS with timely security fixes. Their commitment to protecting user data means they release OS updates promptly and frequently, making it challenging for forensic vendors to keep up and develop software that can effectively extract evidence from devices with known passcode running these latest iOS versions. However, despite these difficulties, our forensic team achieved a significant milestone this time, reducing the time gap between the release of iOS 16.5 and our forensic software update to approximately 2.5 months. This achievement may seem minor to some, but within the forensic industry, it represents a major breakthrough and highlights our unwavering commitment to staying at the forefront of iOS data acquisition. Our constant effort to bridge the gap between iOS updates and forensic capabilities ensures that investigators have the most advanced tools at their disposal to conduct thorough and effective digital investigations.
A Word on Apple A11 Chips
Devices equipped with A11 Bionic chips, such as the iPhone 8, 8 Plus, and iPhone X, were initially considered susceptible to checkm8, a powerful bootloader-level exploit that was thought to be unpatchable. However, with the release of iOS 16, Apple implemented a new SEP hardening patch, effectively shutting down checkm8’s access to user data if a screen lock passcode had ever been used on the device. We’ve already discussed it in iOS 16: SEP Hardening, New Security Measures and Their Forensic Implications. This update rendered the exploit useless for accessing data on A11 iPhones running iOS 16.
Let’s reiterate: a bootloader-level extraction of A11-based iPhones running iOS 16 will fail if a passcode was ever used on the iPhone since the initial setup, making checkm8 extractions pointless for these devices if they run iOS 16.
Previously, other extraction methods for A11 Bionic devices proved to be challenging, as many existing OS-level exploits did not work on these chips, limiting forensic specialists to partial file system extraction for iOS 15.4 – 16.1.2, without access to the keychain. Fortunately, an updated agent-based extraction method is now available, leveraging a new OS-level exploit. This breakthrough now allows to perform full file system extraction and decrypt the keychain on A11 devices running all versions of iOS 15 and 16 up to and including iOS 16.5. With this advancement, investigators can now access critical data and evidence from a wider range of devices, enhancing their capabilities in the realm of digital forensics.
Wait A Minute!
When attempting data extraction using this new method, it is crucial to exercise patience. After restart the device, it is recommended to wait for at least a minute, preferably 2 to 3 minutes, before proceeding with the extraction process. This waiting period is essential to allow the device to stabilize and for background processes to settle. Note that the number of apps installed on the device can impact the kernel’s activity during this period, so an even longer waiting period may be required for successful extraction.
Additionally, make sure to place the device in airplane mode and additionally disable Wi-Fi and Bluetooth toggles before you begin the extraction. This not only eliminates the risk of remote lockout, but also helps minimize unwanted activity on the device, ensuring a more stable environment for the extraction process.
In real life, successful extractions might not be achieved on the first attempt. In our lab, one device took five attempts before the extraction succeeded, while several others required only two tries. Devices with limited data or minimal applications generally completed the process without issues on the first run.
How We Tested It
We extensively tested the update on a wide range of devices to ensure its reliability and compatibility. We hope that several more devices and iOS versions will be added to our testing list based on valuable feedback from our clients. This is the current list of devices/iOS versions/SoC we tested the update on:
- iPhone 8 & iPhone X, iOS 15.4, 15.6, 15.7.1, 16.0, 16.1, 16.2, 16.3, 16.4, 16.4.1, 16.5 // A11
- iPhone Xs Max, iOS 16.4.1 // A12
- iPhone 11, iOS 16.5 // A13
- iPhone SE (2nd generation), iOS 16.4.1 (а) // A13
- iPad Air (4th generation), iOS 16.5 // A14
- iPhone 13 Pro, iOS 16.5 // A15
- iPhone 13 Pro Max, iOS 16.4.1 // A15
- iPhone 13 Mini, iOS 16.4.1 // A15
- iPhone 13 Mini, iOS 16.5 // A15
- iPhone SE (3rd generation), iOS 16.5 // A15
- iPad Air (5th generation), iOS 16.4.1 // M1
Note: The exploit may not always work on the first attempt and could occasionally result in the device rebooting. In such cases, we recommend trying again, but it’s crucial to wait for at least a minute after the reboot to allow the system’s core components to stabilize. Furthermore, to increase security during the process, we advise using airplane mode, which can minimize external interference during the data extraction process.
Conclusion
Elcomsoft iOS Forensic Toolkit stands unrivaled in iOS data acquisition. With its powerful extraction capabilities, support for the latest iPhone and iPad models, and keychain decryption, it empowers forensic investigators with comprehensive access to valuable information. The recent addition of iOS 16.5 support, along with our commitment to future updates, solidifies EIFT as the most advanced iOS acquisition software available, unlocking new possibilities for your forensic investigations.
REFERENCES:
![]()
Elcomsoft iOS Forensic Toolkit
Extract critical evidence from Apple iOS devices in real time. Gain access to phone secrets including passwords and encryption keys, and decrypt the file system image with or without the original passcode. Physical and logical acquisition options for all 64-bit devices running all versions of iOS.
Elcomsoft iOS Forensic Toolkit official web page & downloads »
如有侵权请联系:admin#unsafe.sh