2023-8-2 21:38:33 Author: lab.wallarm.com(查看原文) 阅读量:30 收藏
Introduction
In a recent advisory, the Cybersecurity and Infrastructure Security Agency (CISA) warned vendors, designers, developers, and end-user organizations of web applications about the dangers posed by Insecure Direct Object Reference (IDOR) vulnerabilities, now commonly referred to as BOLA (Broken Object Level Authorization) in the OWASP API Security Top 10 project and elsewhere. This vulnerability poses a serious threat by granting attackers access to sensitive data they shouldn’t be able to see, by simply manipulating a numeric value in a URL or API call. This blog post aims to shed light on BOLA (IDOR) vulnerabilities, explore their risks, and provide insights into effective mitigation strategies.
Understanding BOLA (IDOR) Vulnerabilities
BOLA (IDOR) is a type of security vulnerability that occurs when an application’s access control mechanisms are not properly implemented. In a well-designed web application, users should only have access to resources they are authorized to view or manipulate. However, in the case of BOLA (IDOR) vulnerabilities, attackers can bypass these access controls and gain access to sensitive information or perform actions that they are not allowed to perform.
The vulnerability typically arises when developers use unvalidated or insufficiently validated parameters, such as user-supplied input, as references to internal objects (e.g., database records, files, or resources). As a result, attackers can manipulate these parameters to point to unauthorized objects and access data that should be protected.
Real-World Impact of BOLA (IDOR) Vulnerabilities
The consequences of BOLA (IDOR) vulnerabilities can be severe. Attackers can exploit these flaws to access sensitive user data, manipulate account details, view private information, modify orders or transactions, and even escalate their privileges within the system. These unauthorized actions can lead to data breaches, financial losses, reputational damage, and legal liabilities for the affected organizations.
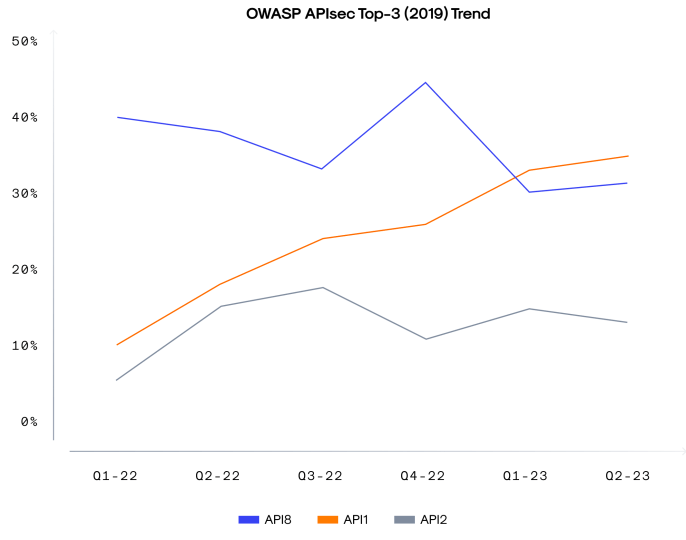
It’s worth noting that BOLA (API1 in both the old 2019 and the new 2023 OWASP APIsec Top-10 lists) is now the no. 1 vulnerability category we’re tracking in our quarterly API ThreatStats™ reports, surpassing API8:2019 (Injections) for the first time. Read our latest report here or the blog post here.
The Importance of Proactive Security Measures
Considering the potential impact of BOLA (IDOR) vulnerabilities, it’s crucial that organizations take proactive steps to secure their web applications. Here are some essential security measures that can help mitigate the risk of BOLA (IDOR):
- Implement Robust Access Controls: Ensure that access controls are enforced at every level of the application. Use role-based access control (RBAC) or attribute-based access control (ABAC) mechanisms to restrict user permissions to authorized resources.
- Input Validation and Sanitization: Thoroughly validate and sanitize all user-supplied input to prevent attackers from injecting malicious data and exploiting BOLA (IDOR) vulnerabilities.
- Secure Coding Practices: Train developers in secure coding practices to avoid common mistakes that could lead to BOLA (IDOR) vulnerabilities. Perform code reviews and security testing during the development process.
- Regular Security Testing: Conduct regular security assessments, such as penetration testing and vulnerability scanning, to identify and remediate potential BOLA (IDOR) vulnerabilities.
- Stay Informed about Emerging Threats: Keep track of the latest security advisories and stay informed about recent data breaches caused by BOLA (IDOR) vulnerabilities. Learning from real-world incidents can help prevent similar occurrences in your applications.
Timing
The timing and nature of this advisory are noteworthy as it provides explicit AppSec-focused guidance. This level of specificity is unusual for ACSC/CISA/NSA advisories. One plausible reason for this proactive measure could be the Optus breach in 2022, where a significant portion of the Australian population’s data was stolen due to poor API security and the presence of a BOLA (IDOR) vulnerability.
It also comes hot on the heels of the recent discovery less than two weeks ago of an IDOR vulnerability in Microsoft Teams which allows external tenants to introduce malware.
Conclusion
BOLA (IDOR) vulnerabilities remain a significant threat to web applications, and their potential impact on sensitive data should not be underestimated. By understanding the risks associated with BOLA (IDOR) and adopting proactive security measures, organizations can better protect their web applications and the data they handle. Collaboration between development, security and operations professionals is essential to create a robust security posture that can withstand evolving cyber threats.
Let’s take this advisory from CISA as a wake-up call and work together to bolster our web application security. By doing so, we can safeguard sensitive data, protect our users, and build trust in the burgeoning digital ecosystem.
如有侵权请联系:admin#unsafe.sh
