2023-8-3 21:0:5 Author: blog.elcomsoft.com(查看原文) 阅读量:21 收藏
We are excited to announce the release of an open-source software for Orange Pi R1 LTS designed to provide firewall functionality for sideloading, signing, and verifying the extraction agent that delivers robust file system imaging and keychain decryption on a wide range of Apple devices with iOS Forensic Toolkit. This development aims to address the growing security challenge faced by forensic experts when sideloading the extraction agent using regular and developer Apple accounts.
Important: older developer accounts created before June 6, 2021, are exempt from the verification process. If you are using one of these accounts, you will not need a firewall to run the extraction agent.
TL&DR
Our research and development team has introduced an open-source project called EIFTPI (github/eiftpi) . This project has brought forth a custom firewall (or more accurately termed “proxy”) designed specifically for the Orange Pi R1 Plus LTS device. This mini-router boasts several features that make it a better fit for this specific purpose then the more all-around Raspberry Pi 4, including two Ethernet ports, both of which are utilized by our software; lower price and wide accessibility.
Why do you need a firewall for iOS forensics? To perform a low-level extraction of iOS and iPadOS devices with iOS Forensic Toolkit, the extraction agent needs to be sideloaded onto the device being analyzed. Each sideloaded app, including the extraction agent, must be signed by Apple with a unique digital signature specific to the device. When installing (or launching for the first time) a sideloaded app on an iPhone or iPad, users are prompted to verify the digital signature, requiring the device to establish contact with an Apple server. However, connecting the device to the internet poses the risks of unwanted synchronization or remote blocking or erasing its content, especially if it is part of an evidence base.
Previously, we recommended a solution that involved enrolling the Apple ID used for signing the sideloaded app into the Apple Developer program, which in turn allowed for the validation of the digital signature without the need for the device to contact an online server. Unfortunately, due to recent updates on Apple’s side, digital signatures associated with new developer accounts must now undergo verification with an Apple server. Consequently, this reintroduces the potential risks that were previously exclusive to non-developer accounts. Considering these changes, we have developed several solutions to minimize risks by limiting the device’s connection solely to the server required for certificate verification. These solutions are:
- A script for macOS that acts as an effective firewall
- An open-source firmware implementing a functional firewall on a Raspberry Pi 4
- An open-source firmware implementing a functional firewall on an Orange Pi R1 Plus LTS
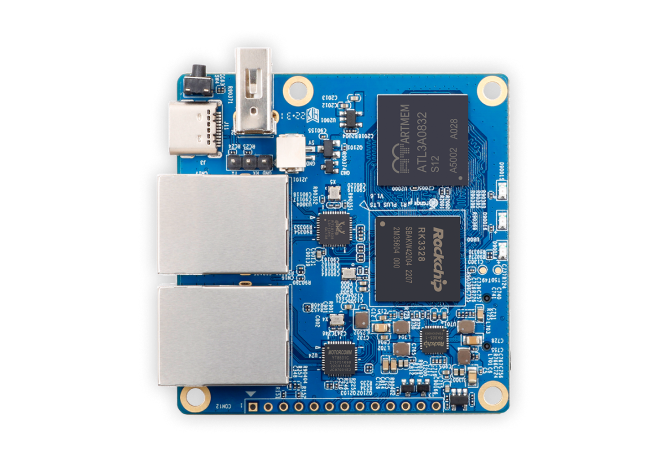
The Orange Pi R1 Plus LTS router
Orange Pi R1 Plus LTS is an open-source single-board computer with Dual Gigabit Ethernet ports. It is highly compact with a dimension of 56X57mm. According to the manufacturer, it can run OpenWRT, Ubuntu, and Debian. It uses the Rockchip RK3328 SoC featuring a quad-core ARM Cortex-A53 64-Bit processor, 1GB LPDDR3 SDRAM, microSD card slot, and, most importantly, two physical Ethernet ports. The device uses a Type-C port as its power connector, and can be easily powered by connecting it to the Type-C port of your Mac or MacBook.
Advantages of the Orange Pi R1 Pus LTS
Compared to a Raspberry Pi 4, for which we have also developed a functional firewall, the Orange Pi R1 Plus LTS is cheaper (around $35 at the time of this writing), and has two dedicated Ethernet ports, both of which are utilized by our project. Essentially, this means that you won’t need an extra USB to Ethernet adapter as you would in the case of the Raspberry Pi 4. In a word, the Orange Pi R1 Plus LTS is a sligthly easier to use firewall/proxy than the Raspberry Pi 4, but the Raspberry Pi 4 is a more powerful general device. We would like to list the following advantages of the Orange Pi R1 Plus LTS:
- Wide Accessibility: The Orange Pi R1 Plus LTS device is easily obtainable, both with and without the metal case, ensuring users can quickly procure the necessary hardware for their forensic needs. The EIFTPI firmware is readily available on GitHub, making it accessible to a broad community of forensic professionals and enthusiasts.
- Cost-Effectiveness: In comparison to some other specialized forensic hardware options, including the Raspberry Pi 4, the Orange Pi R1 Plus LTS is an affordable choice. This affordability extends to its components, as it comes with two Ethernet ports, eliminating the need for an additional adapter. This cost-effectiveness makes it a preferred option for those on a tight budget or smaller forensic teams.
- Enhanced Connectivity: The Orange Pi R1 Plus LTS features two Ethernet ports – one is labeled “LAN” on the case (if you have the one; this port is located closer to the USB-C port) and the other is labeled as “WAN” (at the right of it).In our implementation, these ports serve distinct purposes. The LAN port connects the device to the internet, while the WAN port is dedicated to connecting iPhones and iPads through the use of appropriate adapters (such as USB-C to Ethernet or Lightning to Ethernet).
Setup requirements
To set up the EIFTPI firewall for iOS forensic purposes, users will need the following:
- A microSD card
- A Type-C power supply for the Orange Pi R1 Plus LTS device (you may use a Type-C cable to power the device off a Mac or MacBook USB Type-C port)
- An adapter for Ethernet connectivity on iPhones/iPads (USB-C to Ethernet or Lightning to Ethernet)
- Two Ethernet patch cords – one to connect the device to a regular router (using the LAN port) and another to connect the iPhone/iPad to the Orange Pi R1 Plus LTS (using the WAN port)
Setting up an Orange Pi R1 Plus LTS as a functional firewall
The EIFTPI image is designed to work as a proxy for wired iOS internet connections, enabling safe agent signing with restricted communication to specific servers. This manual will guide you through the setup process.
First, download the firmware image from GitHub – Elcomsoft/eiftpi. There is a single unified image currently supporting several devices including Raspberry Pi 3B, Raspberry Pi 3B+, Raspberry Pi 4, Orage Pi 5, and Orange Pi R1 Plus LTS.
The simplest way to use it is:
- Flash image in microSD card (at least 4GB)
- Insert card into the Pi and power on the Orange Pi R1 Plus LTS device
- Connect iPhone with Lightning to Ethernet adapter to the WAN port of the Orange Pi R1 Plus LTS
- Connect the Orange Pi R1 Plus LTS to Internet through the LAN port of the Orange Pi R1 Plus LTS
Important: On the Orange Pi R1 Plus LTS, the downlink (i.e. the connection to the iPhone) is the port next to the USB-C port labeled “WAN”. The other port (the one closer to the GPIO pins) labeled “LAN” is uplink. Just note that there are no LAN/WAN labels on the board itself, but only on the box.
That’s it! You have successfully installed the firmware on Orange Pi R1 Plus LTS. Connect the Orange Pi R1 Plus LTS device to the internet and then connect your iPhone to the Orange Pi R1 Plus LTS using a cable. We recommend connecting a test iPhone first to ensure that Internet access is limited. The test iPhone should only have access to ppq.apple.com and humb.apple.com. Additionally, www.elcomsoft.com should be accessible (you can use it for testing the connection), while www.apple.com (or any other address except those listed above) should not be accessible.
If you prefer building your own image or using Wi-Fi instead of the built-in Ethernet port (which we generally do not recommend), visit GitHub – Elcomsoft/eiftpi for additional instructions.
Conclusion
As we have shared our open-source software for Orange Pi R1 Plus LTS with firewall functionality, we aim to secure the sideloading of the extraction agent in the iOS ecosystem. The limitations of checkm8 and the complex nature of developer accounts have necessitated new approaches to ensure data security. By embracing open-source solutions and providing alternatives, we strive to empower forensic experts and enhance the effectiveness of the extraction agent in safeguarding valuable information.
REFERENCES:
![]()
Elcomsoft iOS Forensic Toolkit
Extract critical evidence from Apple iOS devices in real time. Gain access to phone secrets including passwords and encryption keys, and decrypt the file system image with or without the original passcode. Physical and logical acquisition options for all 64-bit devices running all versions of iOS.
Elcomsoft iOS Forensic Toolkit official web page & downloads »
如有侵权请联系:admin#unsafe.sh