2023-8-15 20:58:21 Author: www.sentinelone.com(查看原文) 阅读量:17 收藏
SentinelOne recently announced the launch of the new Singularity™ Cloud Data Security product line to help customers gain visibility and provide protection for their cloud data, storage, downstream applications, and users from risks associated with unscanned files. Threat Protection for NetApp provides protection for NetApp arrays, and Threat Detection for Amazon S3, which will be highlighted here, provides protection for S3 buckets. Both services provide powerful, low-latency security for cloud storage in a highly efficient and simple user experience.

Why Does Amazon S3 Require Protection?
Amazon S3 is one of the most commonly used AWS services. Due to its flexible, scalable, and available nature, it is possible to store and access nearly any object type from anywhere. With this flexibility, there are a variety of use cases for the service, but in today’s environments, we see Amazon S3 being used more by applications than by humans looking for storage. S3 buckets being used by applications house critical application data for apps themselves but also sensitive data. Uptime and performance are mission critical.
Earlier this year, Amazon S3 turned 17 years old, and AWS shared that it currently holds more than 280 trillion objects and has an average of over 100 million requests per second. As part of the shared responsibility model, AWS ensures that the infrastructure itself is secure, and even ensures data integrity within S3. However, the security of what is in the bucket and its potential spread to downstream applications or workflows is the responsibility of the customer.
Many Amazon S3 users and security teams think of configuration management as the primary security challenge, and this used to be a bigger issue with buckets with sensitive data accidentally made public. AWS, though, has implemented new measures to encourage proper configuration. To combat this data loss risk, many organizations use a Cloud Security Posture Management (CSPM) solution to scan for potential misconfigurations, which is an important element of a defense-in-depth strategy. However, CSPM alone is not enough to prevent S3 from being an attack surface.
The sheer volume of data stored in S3, most of it unscanned and accessible to downstream applications and workflows (including user endpoints), poses a security risk to organizations in terms of malware, ransomware, remote access trojans (RATs), supply chain attacks, and more. Without additional protection, an organization’s S3 buckets can become an accidental staging area for malware.
Threat Detection for Amazon S3
With Threat Detection for Amazon S3, organizations can decrease risk and increase visibility when it comes to the objects in their buckets. Reducing risk is important and so is meeting compliance requirements including data sovereignty. The solution was designed to meet the business, security, and cloud architecture needs of customers, focusing on the following features:
- AI-Driven Threat Detection – Powerful, AI-driven threat detection goes beyond traditional signature-based approaches, which are easily evaded, and protects the organization from threats faster.
- Automation, Flexibility, and Scalability – Scan new files added to buckets automatically. Inventory and protect buckets, including new buckets automatically as they are created, based on configurable policy based approaches.
- High Performance, Low Overhead – Easily deploy into cloud-native architectures using CloudFormation Templates with low ongoing overhead and minimal additional compute costs. Files are scanned quickly, keeping applications running smoothly.
- Compliance-Ready – Scanning completed in customer cloud; no sensitive data or files leave the organization’s cloud environment.
- Centralized Management Experience – Delivered in a simple, unified management experience within the SentinelOne console, where customers can also manage the protection of cloud workloads, endpoints, and identity.
Existing solutions in the market have left many customers frustrated due to poor security performance such as a signature-only approach and a lack of visibility into the resources and their protection status. Other challenges include sluggish scanning or unnatural deployment patterns that slow applications down, or require time consuming re-architecture.
Easy Deployment & Ongoing Security Without Maintenance
Getting Started
Threat Detection for Amazon S3 is centrally managed in the SentinelOne management console. To get started, onboard an AWS account or organization and create a Stackset to deploy and create an ARN role for SentinelOne to access your cloud environment.
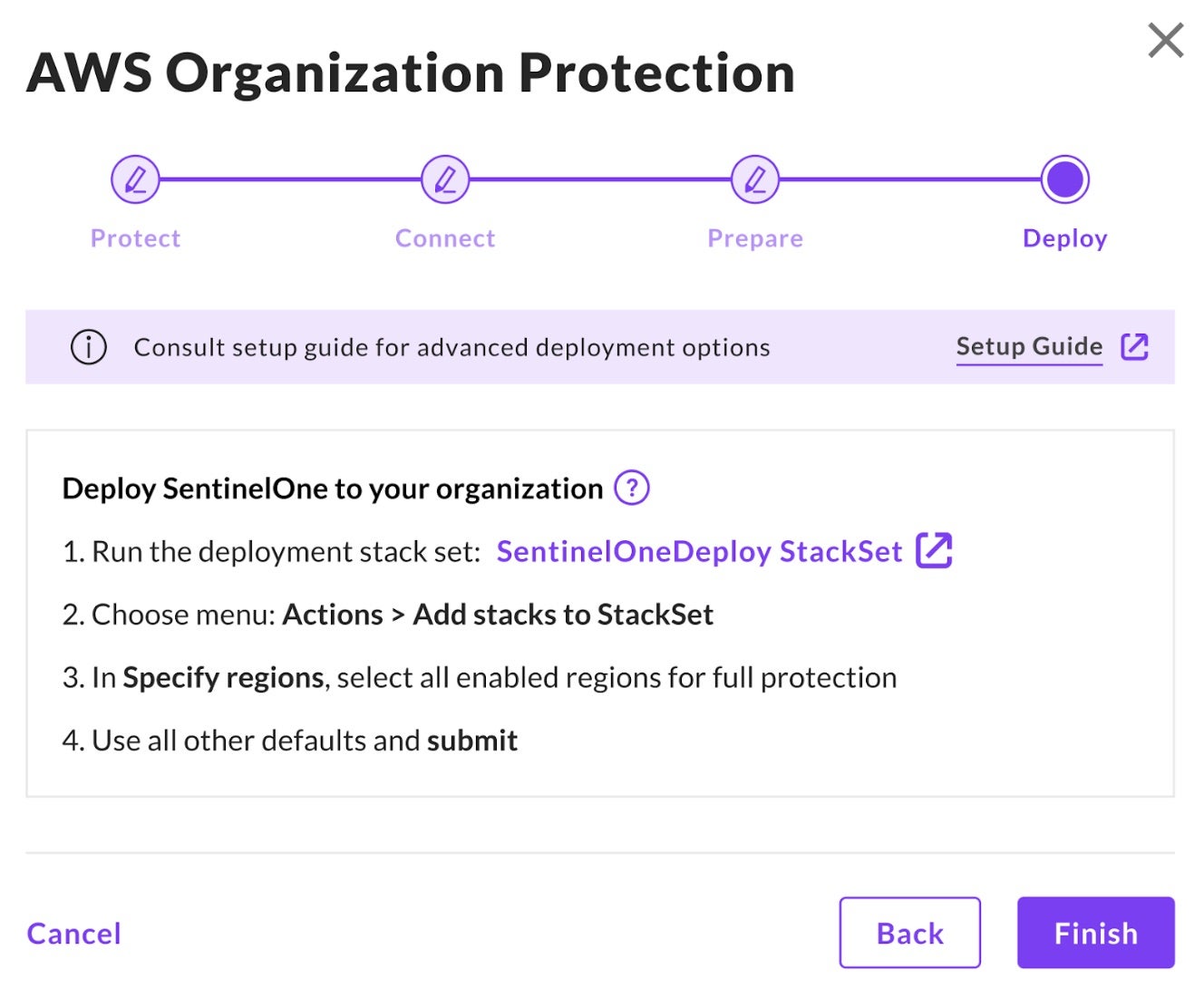
The next step is to select the relevant CloudTrail that will be used by SentinelOne to analyze your cloud environment data and provide an inventory of your S3 buckets. Once done, users will receive multiple CloudFormation templates to be deployed, one for each region that the account’s S3 buckets reside in. Once deployed, the admin can then configure the policy to select which buckets will be protected for malware or fully scanned. Admins can also invoke an ad-hoc scanning of a bucket.
Scanning and Policy Configuration
In a true “set it and forget it” approach, scanning of S3 buckets is triggered by configuring a cloud policy that will automatically scan every file added to the indicated bucket according to a predefined rule. For example, all buckets tagged as production should be automatically scanned and monitored for new files.
Configuring policy or rules is done in the SentinelOne management console. Policies can filter resources based on any AWS metadata such as tags, regions, “name contains”, OU, org, etc. There are a variety of policy based options available. For example, organizations could choose to apply scanning to new files, and quarantining of all suspected malicious files to all “production” tagged buckets, or to all buckets in a specific region due to compliance requirements. By using a tag-based approach, users save time by automating the policy application vs. applying policies to each bucket by name.
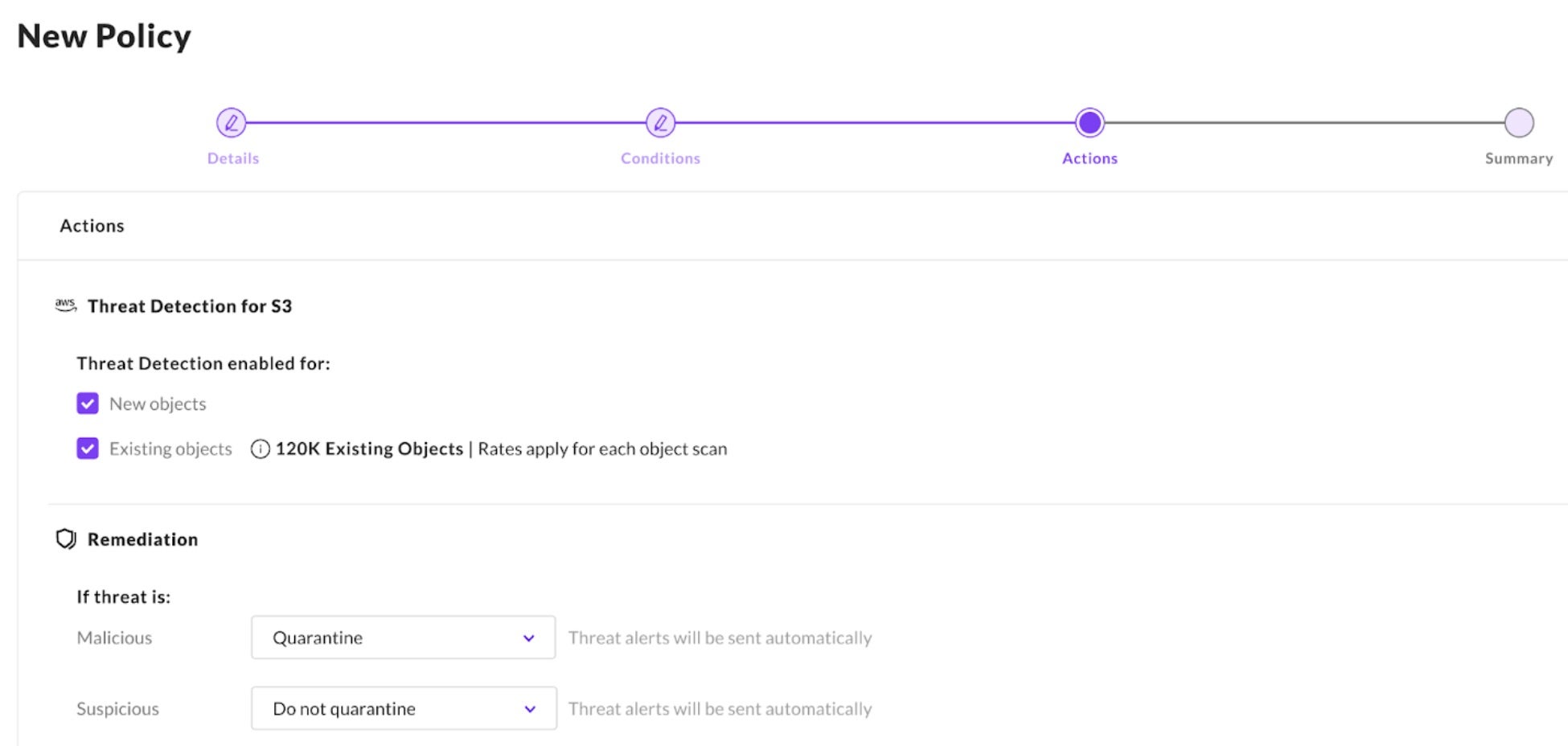
These options are configured at the policy level. When a suspicious or malicious file is identified in a bucket with a “Quarantine” policy enabled, the service will encrypt the file and move it to a customer-defined quarantine bucket. The file is also removed from the original bucket. If the policy is set not to quarantine, the service will tag the malicious file and create a threat in the SentinelOne management console.
Once the scanning service is done, it reports the findings into the SentinelOne Singularity™ console incidents page. If a file needs to be unquarantined, a user with appropriate privileges can unquarantine with one click, and also add an exclusion to the file for future scans.
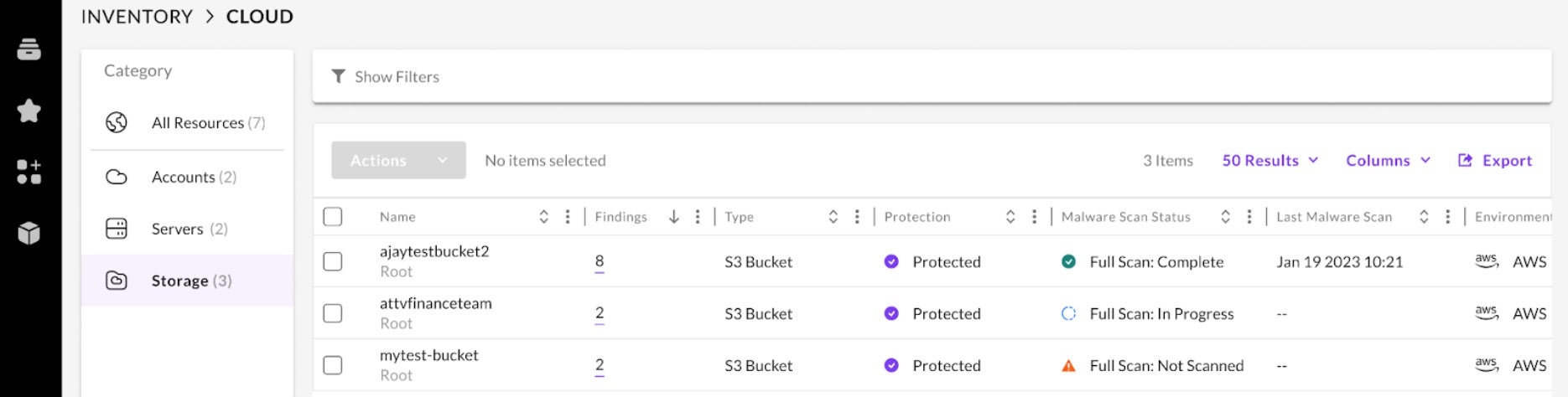
Autoscaling & High Volume Scanning
Whether you are scanning a high-volume of files entering your S3 bucket or performing an on-demand scan, this solution has a built-in, auto-scaling feature to ensure files are being scanned for malware as quickly as possible while minimizing cost.
The actual files never leave the organization’s AWS accounts. This service sends metrics, metadata, and logs from your AWS accounts to Singularity™ Cloud. Once a malicious file is detected, the file name, path, and the relevant user ID that uploaded the file are sent to the Singularity™ Cloud console for display. This ensures all compliance and data sovereignty requirements are met with respect to hosting your data in your environment.
Scanning Existing Files
After deploying the solution and configuring the policy definition, the appropriate policy will be applied to the buckets in the inventory: new file scanning, existing file scanning, both, or no scanning. An ad hoc scan on existing files can easily be initiated on demand from the Singularity console.
Simple, Powerful Security For Simple Storage Service
Configuration scanning is not enough – danger resides in the data itself, being passed downstream. The popularity and flexibility of Amazon S3 leads to a potentially broad attack surface for many organizations that have not begun scanning and securing the data residing in their buckets. Regardless of cloud maturity or S3 use cases, organizations now have a simple and scalable solution to protect their data, their users, and their businesses with Threat Detection for Amazon S3.
Simple deployment, powerful AI-driven threat detection and response with in-line and in-bucket scanning will enable customers to protect their Amazon S3 buckets, critical business applications, and users from malware, ransomware, remote access trojans (RATs) and more.
To learn more about Threat Detection for Amazon S3, read the solutions brief, request a demo, or contact us today.
如有侵权请联系:admin#unsafe.sh