2023-8-18 13:39:12 Author: blog.qualys.com(查看原文) 阅读量:12 收藏
Qualys Blog Series – 2023 TotalCloud Security Insights by the Threat Research Unit
The 2023 TotalCloud Security Insights report from the Qualys Threat Research Unit (TRU) provides research insights, best practices, and detailed recommendations organized by five separate Risk Facts. The insights will enable organizations using cloud technologies to better understand these risks and how they can be better prepared to face the challenges in today’s threat landscape.
Read the previous blog in this series: External-facing vulnerabilities are low-hanging fruit for attackers.
The existence of weaponized vulnerabilities is like handing anyone a key to your cloud. With these tools, an attacker already knows how to enter and move within your cloud. To understand the potent threat of weaponized vulnerabilities, let us consider today’s clear-and-present danger of Log4Shell.
Impact on Cloud Security by Log4Shell
The Log4Shell vulnerability exploits the functionality of Log4j, an open-source logging framework widely used in Java applications. Log4Shell allows attackers to execute arbitrary Java code or leak sensitive information by manipulating specific string substitution expressions when logging a string. The prevalence of this vulnerability in cloud environments is due to several factors.
Why Log4Shell Is Still Dangerous
First, the ubiquity of Log4j broadens the vulnerability’s potential impact by affecting many cloud services. It can also be exploited through often-logged HTTP requests. Attackers place a malicious string in the HTTP request URL or in commonly logged HTTP headers making cloud services highly vulnerable that handle high volumes of HTTP requests.
Beyond these direct factors, characteristics of cloud environments also raise their vulnerability. Due to the rapid development and deployment, these environments become challenging to secure comprehensively. They are easily accessible to potential attackers because of public exposure and extensive use of open-source software, such as Log4j.
The multi-tenancy nature of many cloud environments, where multiple users share the same infrastructure, can further compound security risks. Legacy applications and systems may not have been designed with cloud security in mind and can introduce additional vulnerabilities. These environments are attractive for automated exploit scripts that rapidly scan for unpatched, exposed systems. Inadequate security knowledge and training also can lead to system misconfigurations or oversights, thereby increasing the system’s vulnerability to such exploits.
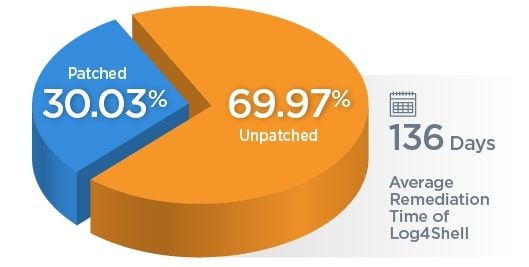
Just 30% of Log4Shell Is Successfully Patched
Log4Shell was first detected in December 2021 and continues to plague enterprises globally. We have detected one million Log4Shell vulnerabilities, with a mere 30% successfully fixed. Due to complexity, remediating Log4Shell vulnerabilities takes, on average, 136.36 days (about four and a half months).
Critical Insights from Risk Fact 3
Weaponized vulnerabilities globally offer attackers a key to your cloud. They are proven tools for exploitation and must be at the top of the list for remediation. As the #1 weaponized vulnerability, Log4Shell continues to plague organizations globally.
We recommend that your teams prioritize two actions to reduce this clear-and-present risk.
Firstly, identify Log4Shell instances in your organization’s cloud. Next, remediate critical Log4Shell vulnerabilities ASAP. Based on the numbers, failure to achieve these two actions considerably raises the chance of a cloud breach.
To learn more about the five cloud security Risk Facts and detailed recommendations, download your copy of Qualys 2023 TotalCloud Security Insights.
Get the full Qualys 2023 TotalCloud Security Insights and learn about all five Cloud Risk Facts now.
如有侵权请联系:admin#unsafe.sh
