Update: With JEB 5.6, several restrictions are lifted to make the Assistant available for Java decompiled output generated by dexdec (it is currently limited to C output generated by gendec).
Starting from JEB 5.2, you may use the experimental “JEB Assistant” to infer names for decompiled methods and method parameters.
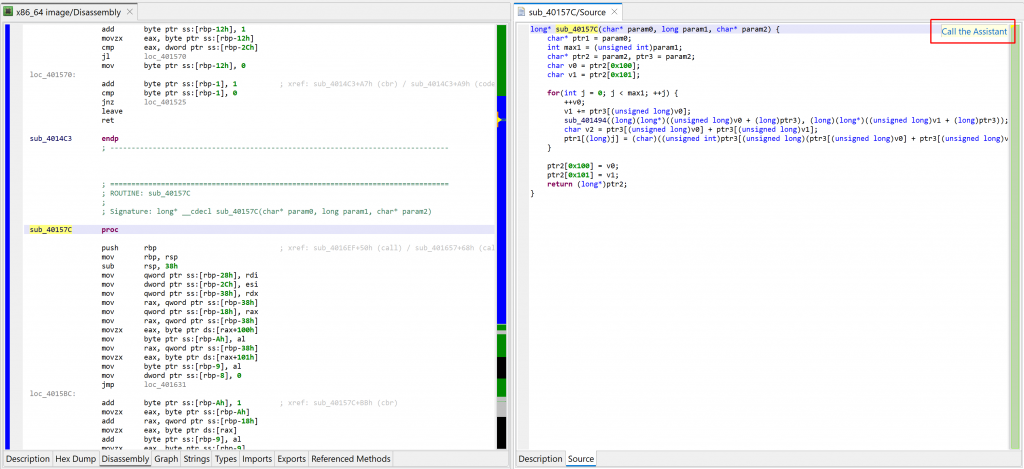
Below is a decompiled aarch64 routine found in the BPFDoor malware. A raw decompilation does not produce any useful name (the default routine name is sub_40157C).
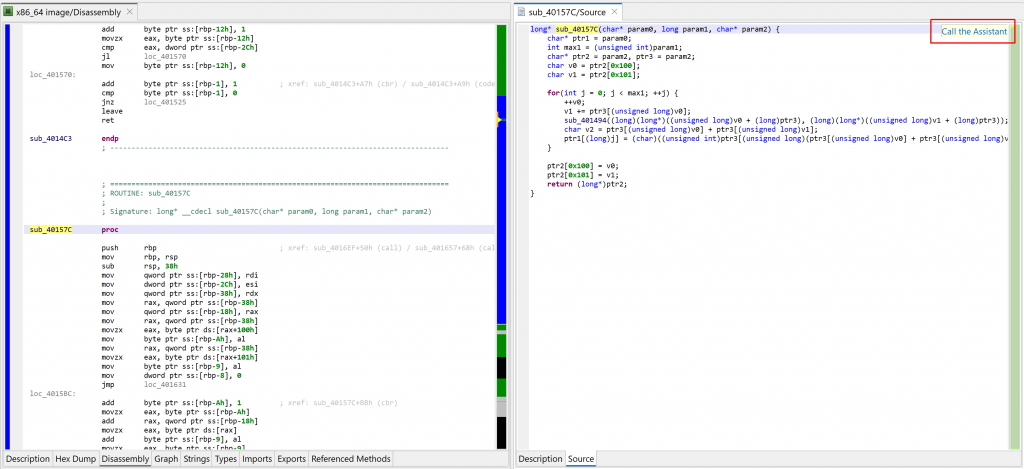
You may click the “Call the Assistant” button (also available via the Action menu, Request Assistant handler, or the back-tick keyboard shortcut) to query the assistant via JEB.IO. At the time of writing, a JEB.IO account is not required to access the assistant.
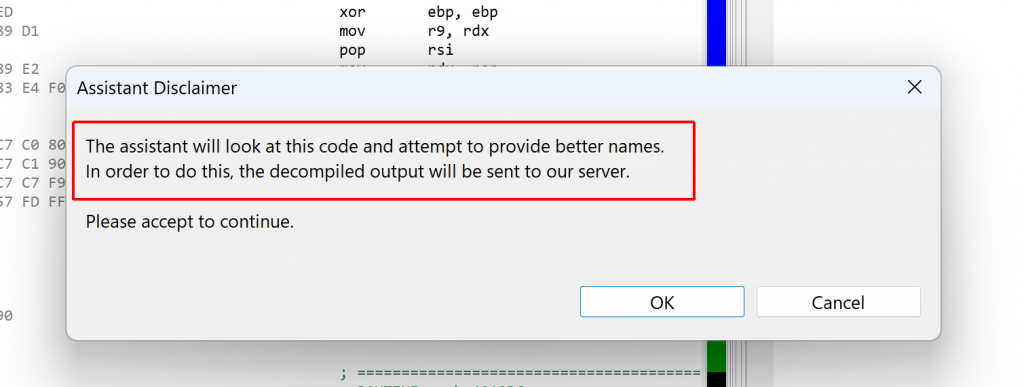
Upon first request, a disclaimer will be shown, letting you know that the decompiled code must be sent to our server:
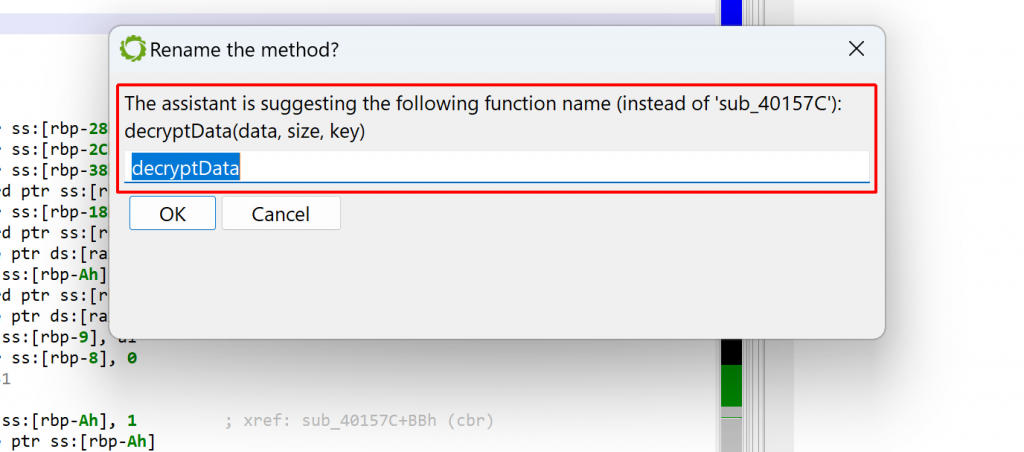
The assistant may return a better name for the method and its parameters. Sometimes, the names may be incorrect, yet provide some insight into what the method is doing. Other times, they may be entirely out of scope! It is always better to take the provided results as hints, rather than absolute truths.
In the case of our mysterious method, the assistant did provide valuable information: decryptData(data, size, key). Indeed, the method is a decryption function — more specifically, rc4 with a pre-computed sbox. The parameter names are (almost) correct.
You may decide to apply the suggested method name directly. The suggested parameter names are not applied automatically.
This feature is experimental. Currently, several limitations apply:
- The assistant is limited to decompiled native routines. It will not work for dex/dalvik decompilations.
- The assistant will refuse to work on overly long routines (whose decompilation exceeds several thousand characters).
- The assistant is not available via the JEB API and requests are rate-limited (at most one every 5 seconds).
On the plus side, a JEB.IO account is not required at this time to use the assistant! Anybody can use it to (sometimes) gain insight into obscure decompilations. We hope it will help you in your reverse-engineering efforts. Please let us know your feedback through the usual channels (email, Slack, etc.).
Until next time 🙂 — Nicolas.